Web authentication method and system
An authentication method and an authentication server technology, which are applied in the field of Web authentication methods and systems, and can solve the problems that users' Internet terminals cannot perform Web authentication, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
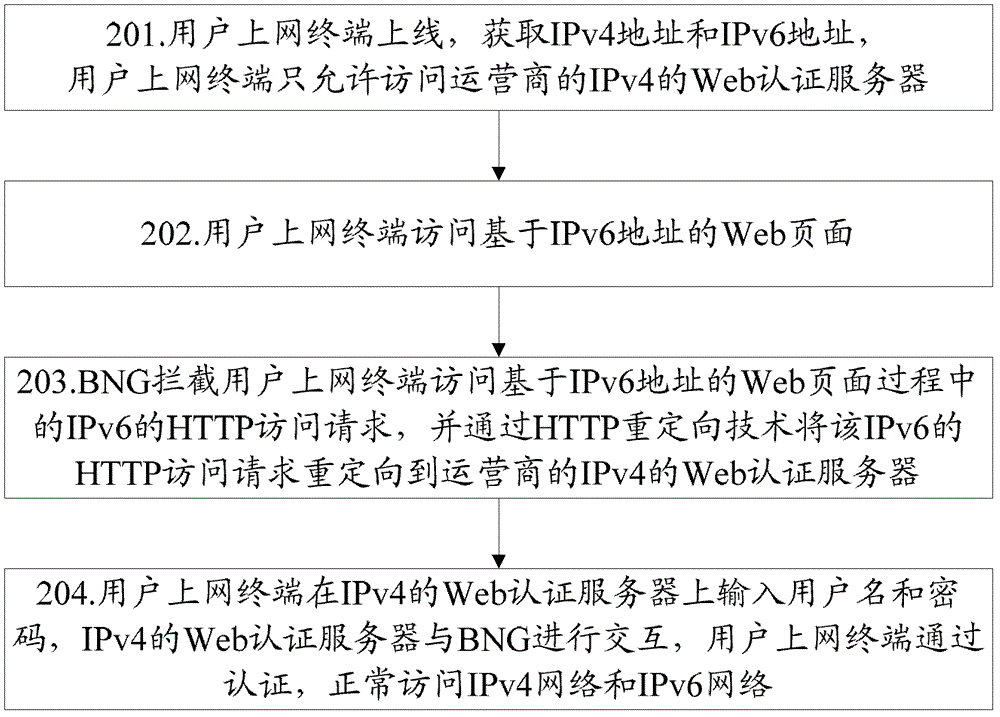
[0078] figure 2 It is a schematic flow diagram of Embodiment 1 of the Web authentication method of the present invention, and it is a specific implementation method of the Web authentication method in the scenario where the user accesses the Internet terminal to obtain an IPv4 address and an IPv6 address, and accesses an IPv6 Web page, such as figure 2 As shown, the method includes the following steps:
[0079] Step 201, the user's online terminal goes online and obtains an IPv4 address and an IPv6 address. At this time, the state of the user's online terminal on the BNG is unauthenticated, and the access authority of the user's online terminal is restricted, and only the IPv4 Web authentication server of the operator is allowed to visit.
[0080] In step 202, the user's Internet access terminal accesses a Web page based on the IPv6 address.
[0081] In step 203, the BNG intercepts the IPv6 HTTP access request in the process of the user's Internet access terminal accessing ...
Embodiment 2
[0084] image 3 It is a schematic flow diagram of the second embodiment of the Web authentication method of the present invention, and it is a specific implementation method of the Web authentication method in the scenario where the user accesses the Internet terminal to obtain an IPv4 address and an IPv6 address, and accesses an IPv4 Web page, such as image 3 As shown, the method includes the following steps:
[0085] Step 301, the user's online terminal goes online and obtains an IPv4 address and an IPv6 address. At this time, the state of the user's online terminal on the BNG is unauthenticated, and the access authority of the user's online terminal is restricted, and only allows access to the operator's IPv4 Web authentication server.
[0086] Step 302, the user's Internet access terminal accesses a Web page based on the IPv4 address.
[0087] In step 303, the BNG intercepts the IPv4 HTTP access request in the process of the user's Internet access terminal accessing the ...
Embodiment 3
[0090] Figure 4 It is a schematic flow chart of Embodiment 3 of the Web authentication method of the present invention, and it is a specific implementation method of the Web authentication method in the scenario where the user's Internet access terminal first obtains an IPv4 address, then performs Web authentication, and finally obtains an IPv6 address, such as Figure 4 As shown, the method includes the following steps:
[0091] Step 401, the user's Internet access terminal goes online and obtains an IPv4 address. At this time, the state of the user's Internet access terminal on the BNG is unauthenticated, and the access authority of the user's Internet access terminal is restricted, only allowing access to the operator's IPv4 Web authentication server.
[0092] Step 402, the user's Internet access terminal accesses a Web page based on the IPv4 address.
[0093] In step 403, the BNG intercepts the IPv4 HTTP access request in the process of the user's Internet access terminal ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com