Usage management system and usage management method
A management system and management object technology, applied in the transmission system, electronic digital data processing, user identity/authority verification, etc., can solve the problems of inability to authenticate and obtain information, and achieve reliable management, flexible security management, and high convenience Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 approach
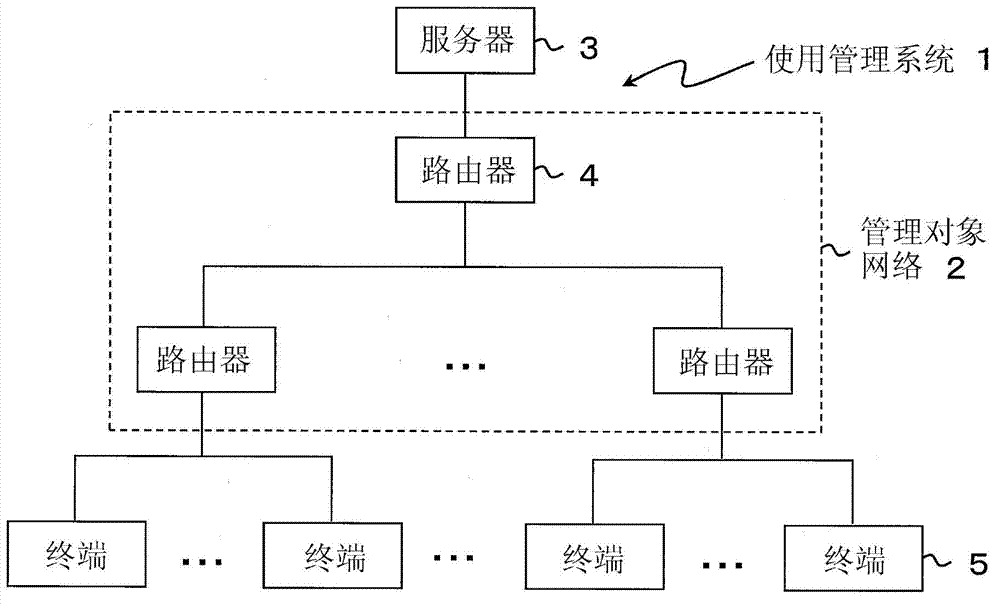
[0069] figure 1 It is an overall configuration diagram of the usage management system 1 of the first embodiment. In the usage management system 1, usage of the terminal 5 (computer) connected to the managed network 2 is managed.
[0070] The managed network 2 is managed by a single management entity such as an enterprise, and is a network closed to external networks such as the Internet. The managed network 2 includes, for example, an in-house LMN (Local Area Network) such as an enterprise, an in-company WMN (Wide Area Network) that connects LMNs installed in multiple sites through dedicated lines or the like.
[0071] Various physical network devices used in the managed network 2 are installed only in places where outsiders cannot use them (for example, if the management subject is a company, then within the company's facilities). Therefore, outsiders cannot connect the terminal 5 to the managed network 2 .
[0072] In addition, in figure 1 Although the router 4 is show...
no. 2 approach
[0137] The second embodiment differs from the first embodiment in the programs installed in the terminal 5 . Hereinafter, the same reference numerals are assigned to the same elements as those in the first embodiment, and overlapping descriptions will be omitted.
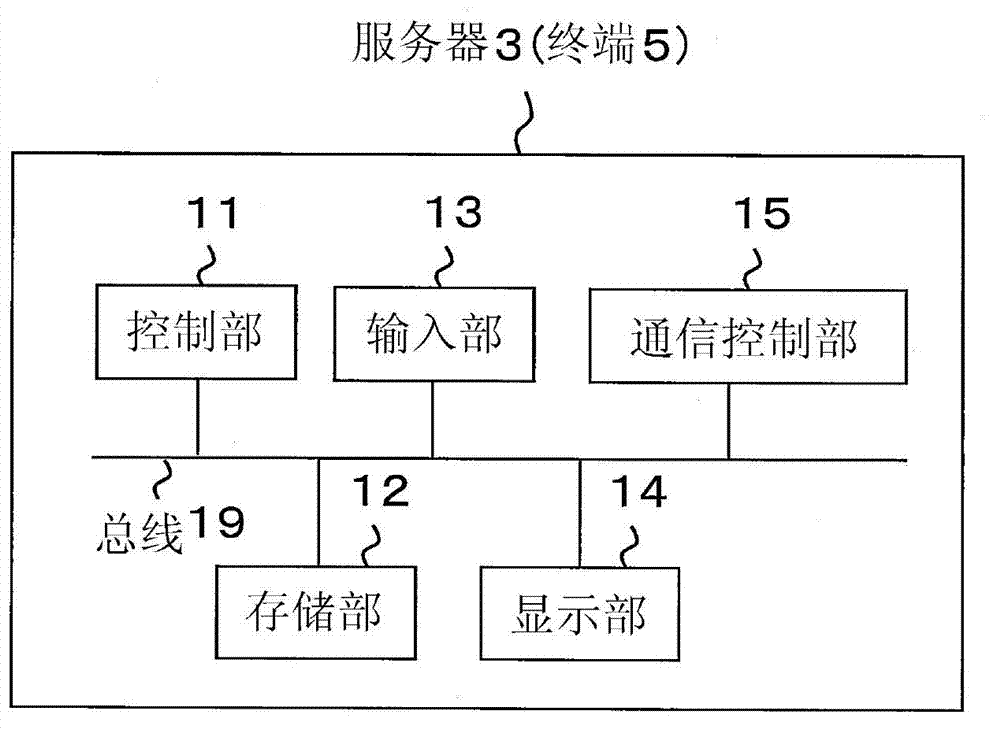
[0138] Figure 7 It is a diagram showing an example of a program stored in the storage unit 12 of the terminal 5 according to the second embodiment.
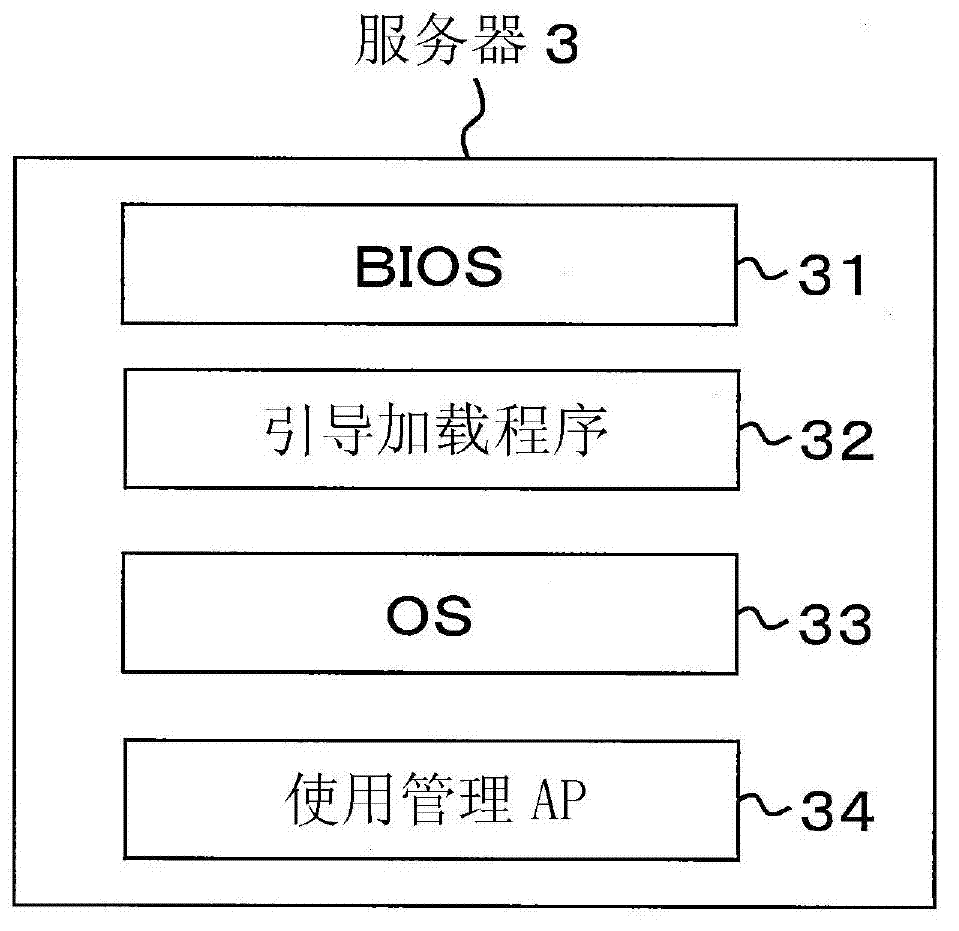
[0139] The storage unit 12 of the terminal 5 stores programs such as a BIOS 51 , a boot loader 52 , an OS 53 , and an inspection MP 57 including an authentication MP 55 and a monitoring MP 56 .
[0140] In the second embodiment, the boot loader 52 of the terminal 5 loads the OS 53 . Then, the inspection MP57 is loaded after the OS53 starts, and the authentication MP55 and the monitoring MP56 which are a part of the inspection MP57 are executed.
[0141] In the second embodiment, the transition to the available state (a state that can be used by the user) means that...
no. 3 approach
[0148] The third embodiment differs from the first embodiment in the hardware configuration of the terminal 5 and the programs installed in the terminal 5 . Hereinafter, the same reference numerals are assigned to the same elements as those in the first embodiment, and overlapping descriptions will be omitted.
[0149] Figure 8 It is an overall configuration diagram of the usage management system 1a of the third embodiment.
[0150] The configuration of the use management system 1a includes a radio wave transmitting device 6, a light emitting device 7, and the like in addition to the server 3 and the terminal 5a connected to the managed network 2.
[0151] The radio wave transmitter 6 transmits a radio wave having a specific frequency indicating that the terminal 5a is permitted to be used, or transmits a radio wave that transmits information indicating that the terminal 5a is permitted to be used. The radio wave transmitting device 6 transmits radio waves having appropriat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com