Method for safely upgrading software, communication device and communication system
A technology of software security and equipment, applied in the field of communication, can solve problems such as complex software upgrade process and complex network structure, and achieve the effect of simple process and network and improved security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
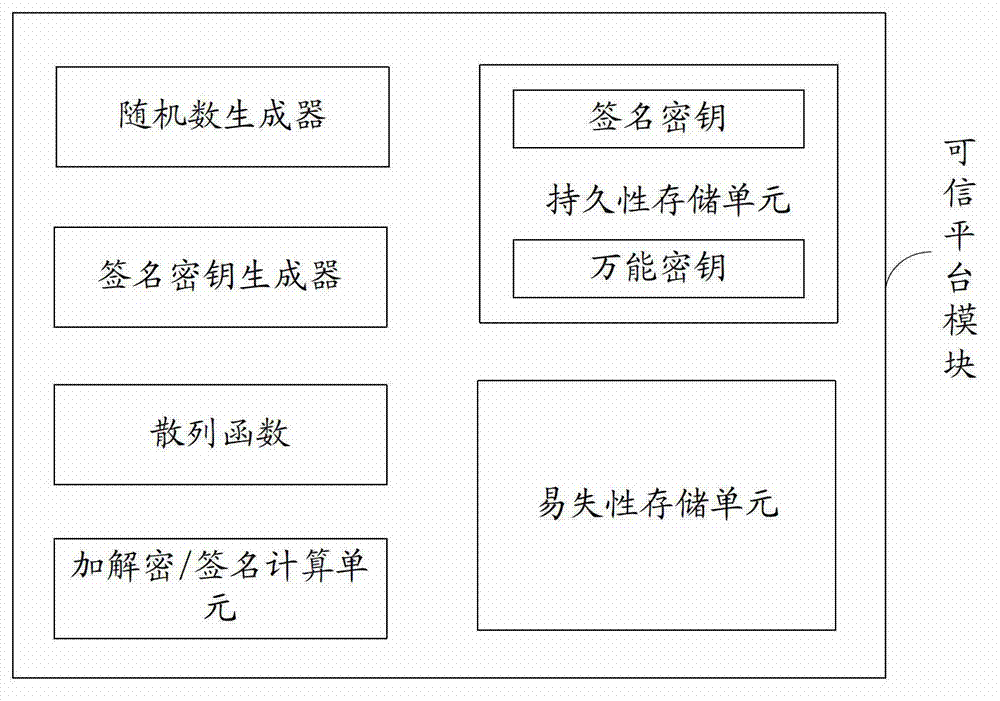
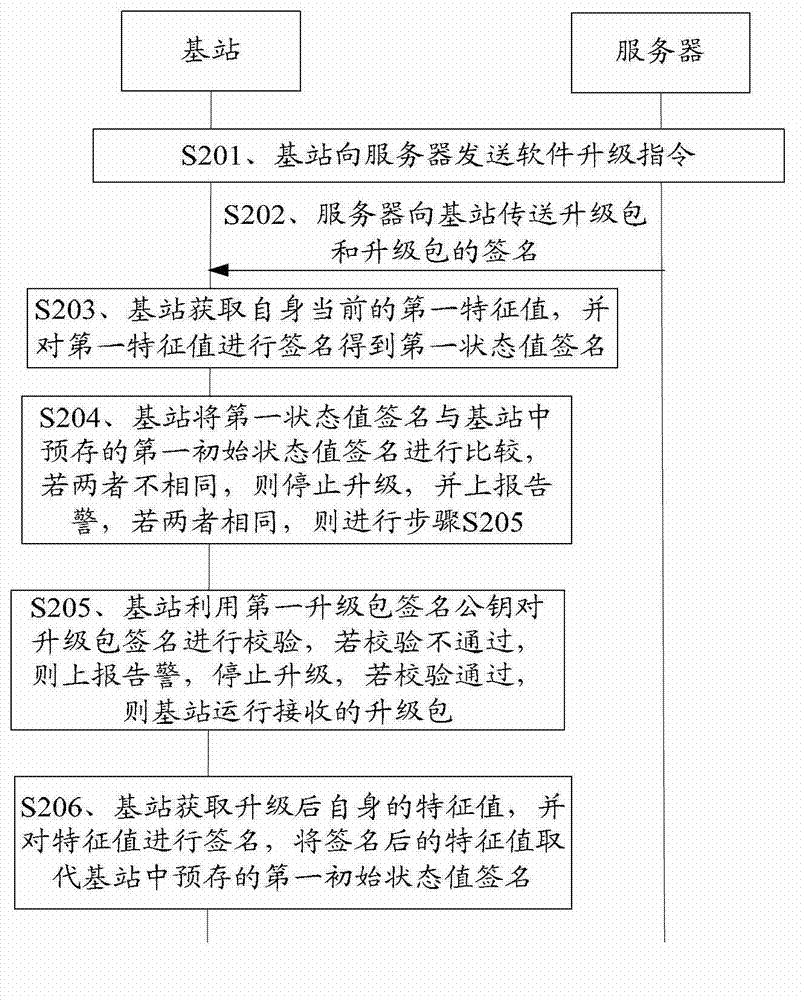
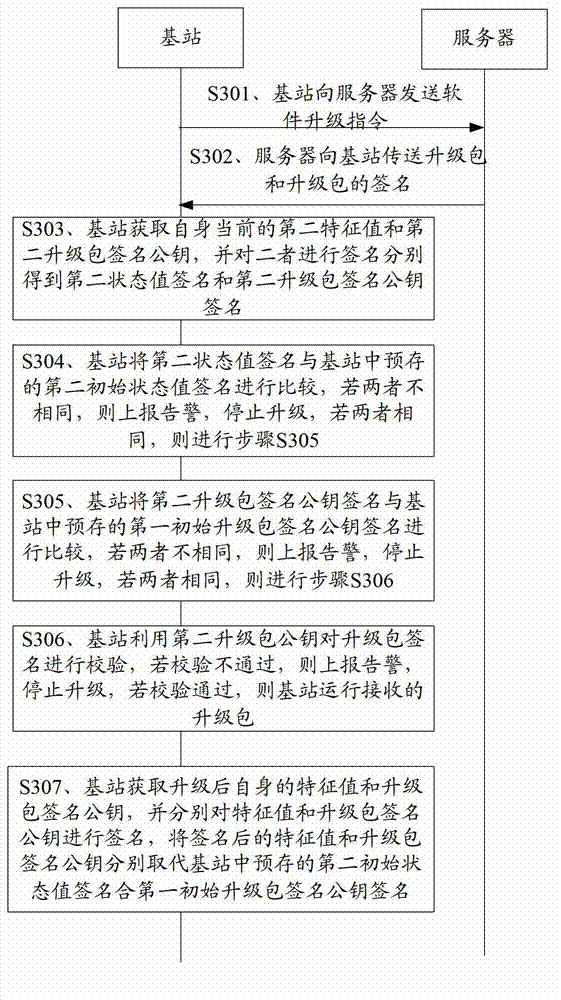
[0032] The embodiment of the present invention provides a method for software security upgrade, because in the method, the upgrade package signature is verified by the device to be upgraded rather than by a third-party verification device, and the device to be upgraded pre-checks the upgrade package before running the upgrade package. The status of itself has been checked, so as to realize the safe upgrade of the software in the equipment to be upgraded more quickly. The embodiment of the present invention also provides a communication device and a communication system, which can also implement fast and safe software upgrades. The following describes the technical solutions in the embodiments of the present invention clearly and completely with reference to the accompanying drawings. Obviously, the described embodiments are only a part of the embodiments of the present invention, rather than all the embodiments. Based on the embodiments of the present invention, all other embod...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com