Hash data storage method and device
A technology of data storage and storage location, applied in the field of communication, can solve the problems of hash conflict, affect the efficiency of resource use, and cannot effectively reduce hash conflicts, so as to improve the use efficiency and reduce hash conflicts.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
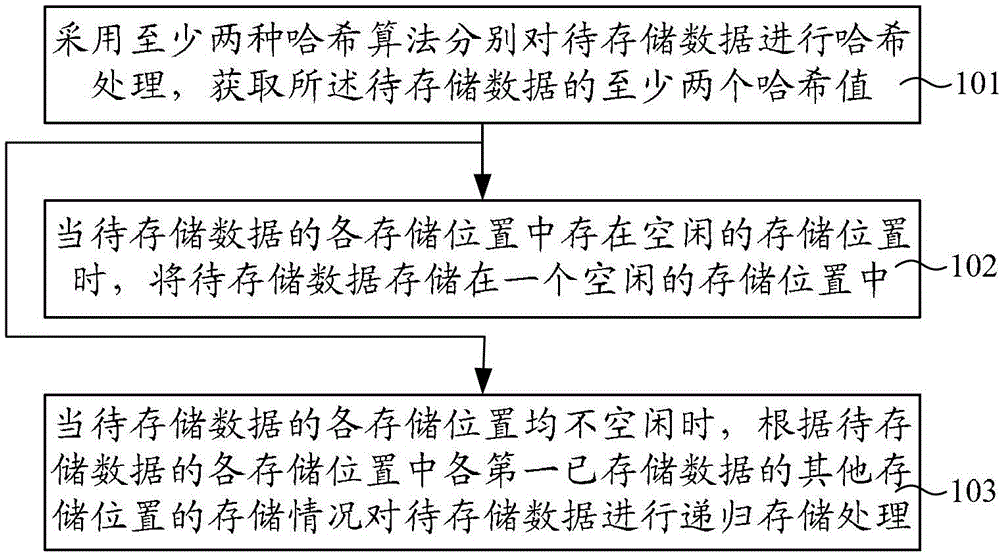
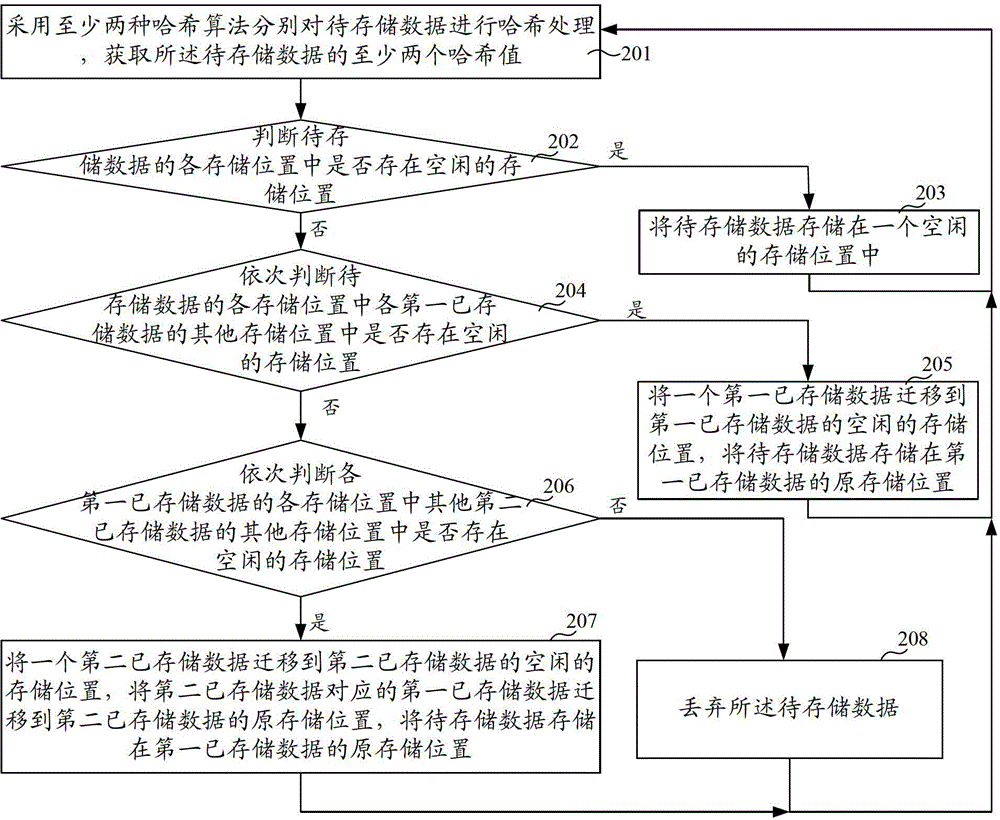
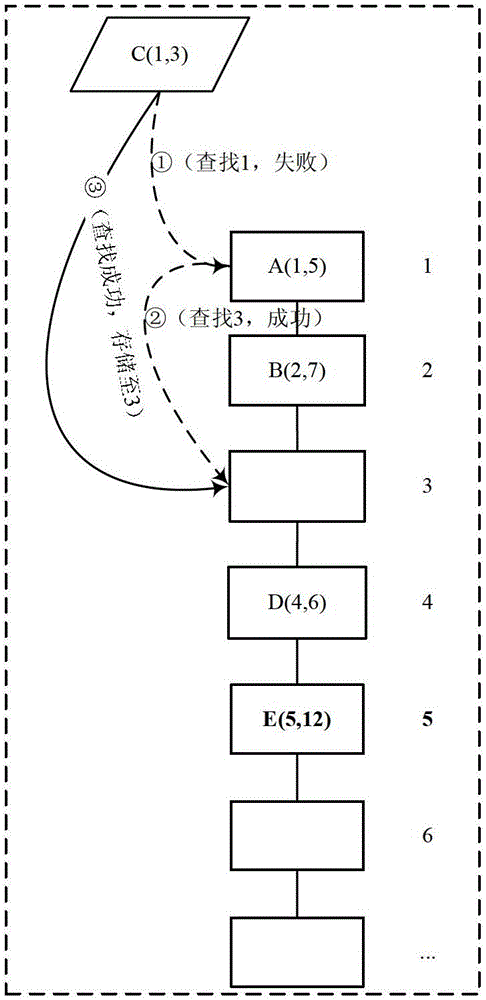
[0021] figure 1 It is a flow chart of Embodiment 1 of the hash data storage method of the present invention, such as figure 1 As shown, this embodiment provides a hash data storage method, which may specifically include the following steps:
[0022] Step 101: Use at least two hash algorithms to perform hash processing on the data to be stored respectively, and obtain at least two hash values of the data to be stored.
[0023] In order to effectively reduce hash collisions in this embodiment, multiple hash algorithms are used to store data. This step is to use at least two hash algorithms to perform hash processing on the stored data respectively. The at least two hash algorithms here can specifically adopt various existing hash algorithms, and use at least two hash algorithms to treat the stored data. Perform hash processing to obtain at least two hash values of the data to be stored, where each hash value corresponds to each hash algorithm. That is, one hash value of t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com