Data security operating system and method based on authority management and control
A technology of data security and operation method, applied in the field of information security, which can solve the problems of data damage, slow encryption and decryption speed, and impact of reading and writing speed.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
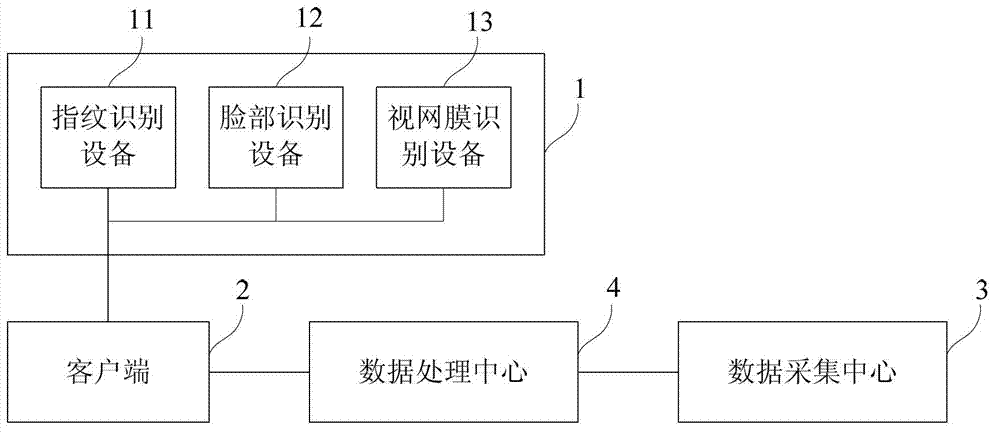
[0043] This embodiment provides a data security operating system based on authority control, such as figure 1 As shown, the data security operating system based on authority control includes: an identity recognition device 1, a client 2, a data collection center 3, and a data processing center 4; the identity recognition device 1 is used to collect and pre-operate users identity feature information; the client 2 is connected to the identity recognition device 1 to upload the user’s identity feature information and the user’s pre-operation information on the data; the data collection center 3 stores the identity features of all users information and its authority; the data processing center 4 is connected to the client 2 and the data acquisition center 3 respectively, and judges whether the user has authority to perform the operation information; if so, the user is allowed to perform the operation through the client information; otherwise, the identity recognition device will r...
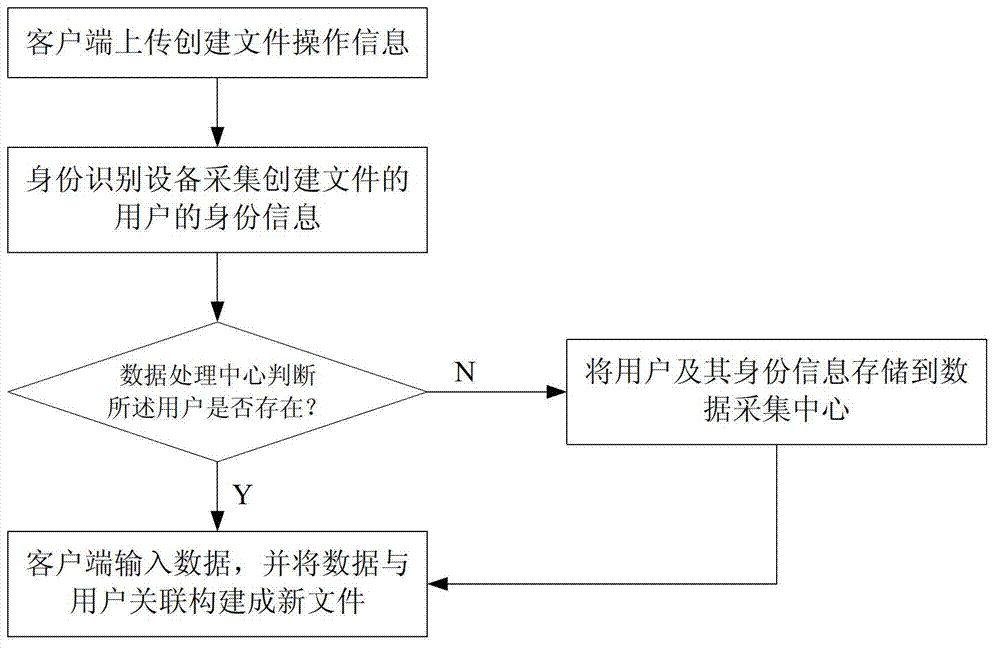
Embodiment 2
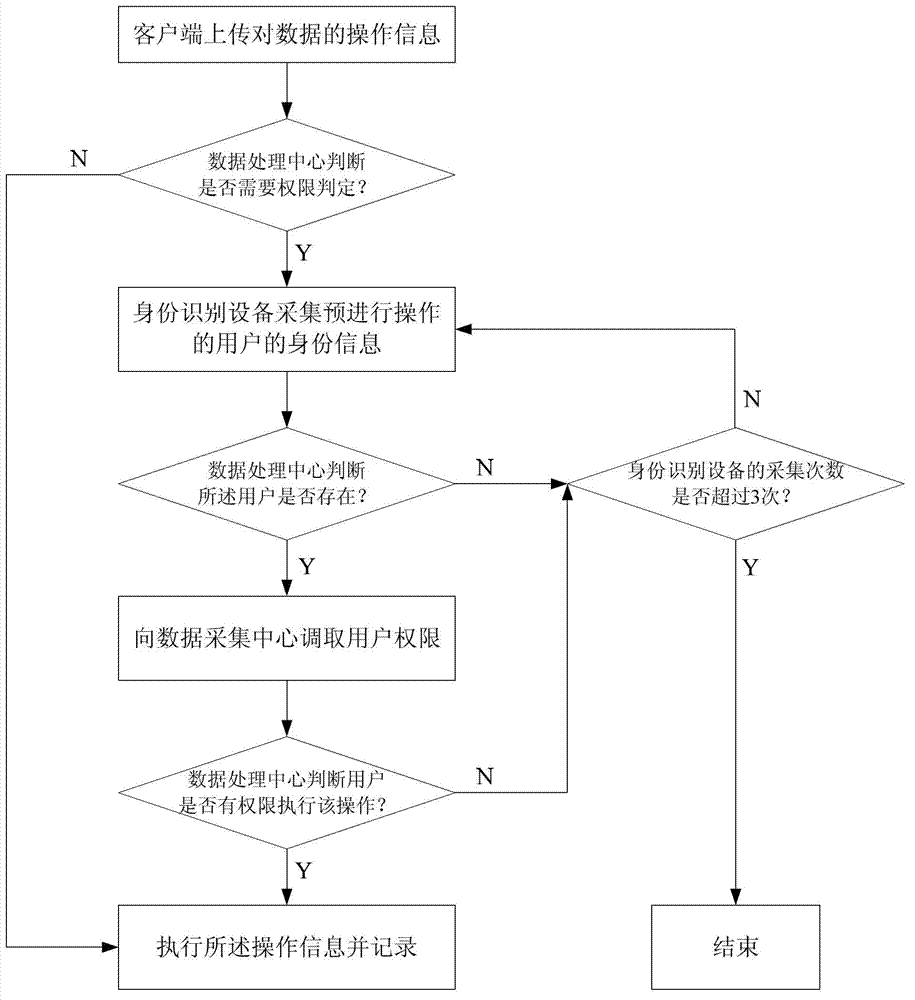
[0048] This embodiment provides a data security operation method based on authority control, such as figure 2 As shown, the data security operation method based on authority control includes:
[0049] S1, the client uploads the operation information performed by the user on the data in advance.
[0050] S2, the data processing center judges whether the operation information needs permission determination; if not, order the client to directly execute the operation information; if necessary, execute step S3. Specifically, the operation information requiring permission determination described in step S2 includes adding, deleting, changing, viewing, taking screenshots, or / and copying files.
[0051] S3. The identity recognition device collects identity feature information of users who pre-operate on the data.
[0052] Further, the step S3 also includes: the data processing center judges whether the identity device has collected the user's identity feature information for the op...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com