Comprehensive detection method and system for page tampering
A comprehensive detection and page technology, applied in the field of computer security, can solve the problems of page tampering, false positives and missed negatives, etc., achieve accurate detection results, and reduce false positives and false negatives.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
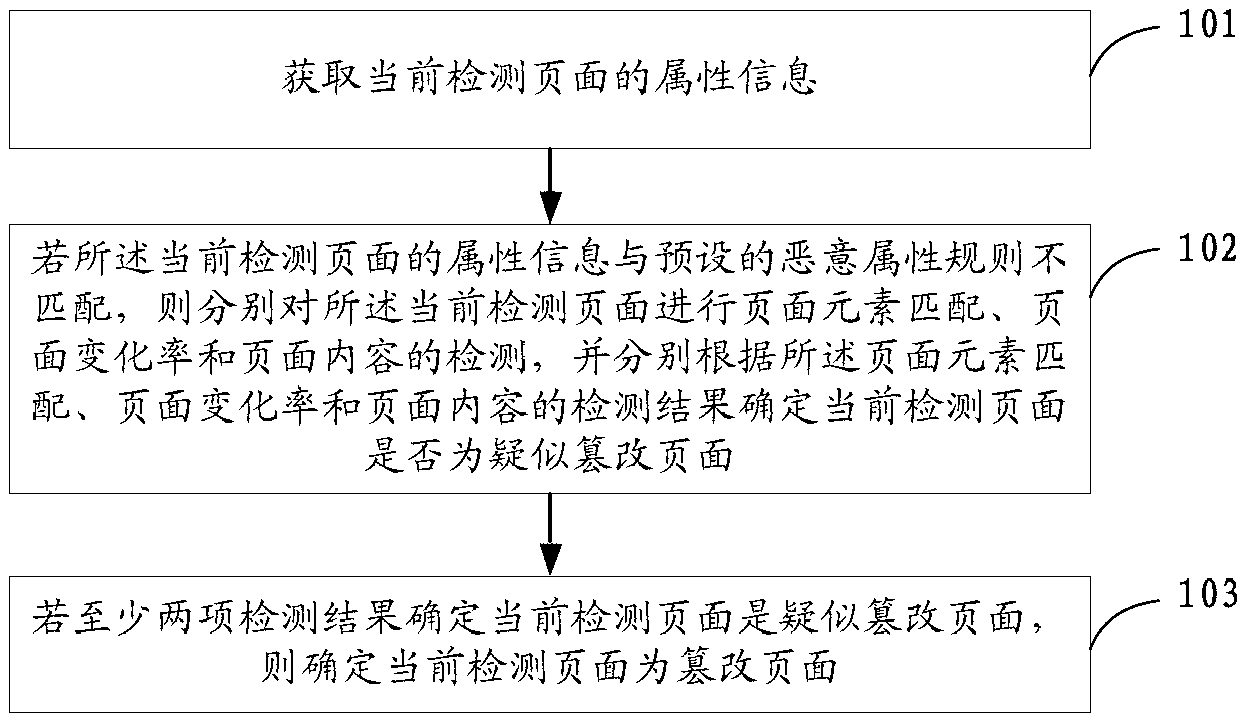
[0016] figure 1 A schematic flowchart of a comprehensive detection method for page tampering provided by Embodiment 1 of the present invention, as shown in figure 1 Described, the comprehensive detection method of described page tampering may comprise the steps:
[0017] Step 101, acquiring attribute information of the currently detected page;
[0018] Step 102, if the attribute information of the currently detected page does not match the preset malicious attribute rules, then respectively perform page element matching, page change rate and page content detection on the currently detected page, and respectively according to the page The detection results of element matching, page change rate and page content determine whether the currently detected page is a suspected tampered page;
[0019] Step 103, if at least two detection results determine that the currently detected page is a suspected tampered page, then determine that the currently detected page is a tampered page. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com