Method, system and device for detecting Android malicious software
A malicious software and malicious technology, applied in the field of Android malware detection, can solve the problems of inability to detect whether the software is malicious software, complex trigger conditions, etc., and achieve the effect of accurate and timely malicious behavior detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
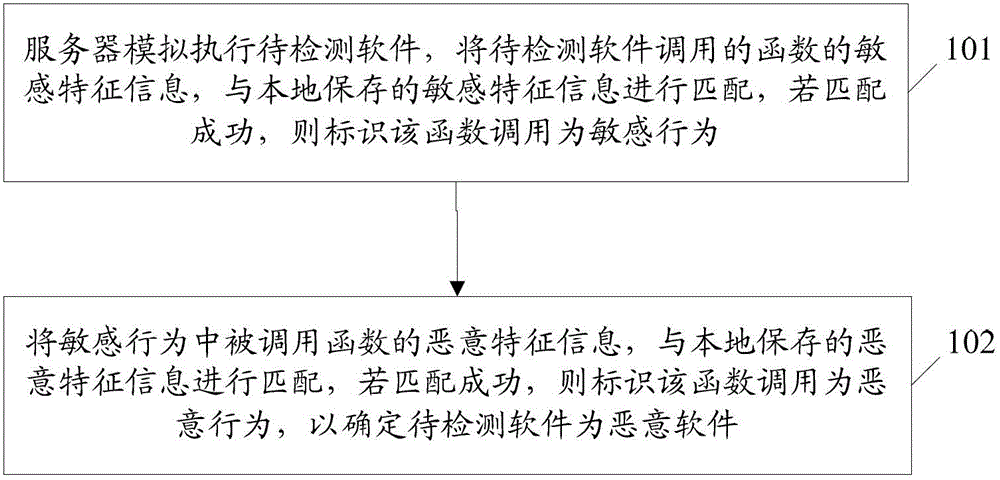
[0049] figure 1 It is a schematic diagram of the implementation process of the method for detecting Android malware in the present invention, such as figure 1 As shown, the method includes:
[0050] Step 101: The server simulates the execution of the software to be detected, and matches the sensitive feature information of the function called by the software to be detected with the sensitive feature information stored locally, and if the matching is successful, it identifies that the function call is a sensitive behavior;
[0051] Here, the sensitive feature information includes: function name, function class name, function parameter type, and number of function parameters. Among them, a certain function can be uniquely determined by function name, function class name, number of function parameters, and function parameter type. .
[0052] Here, the server locally saves the sensitive feature information of the dangerous function, where the dangerous function is a library function call...
Embodiment 2
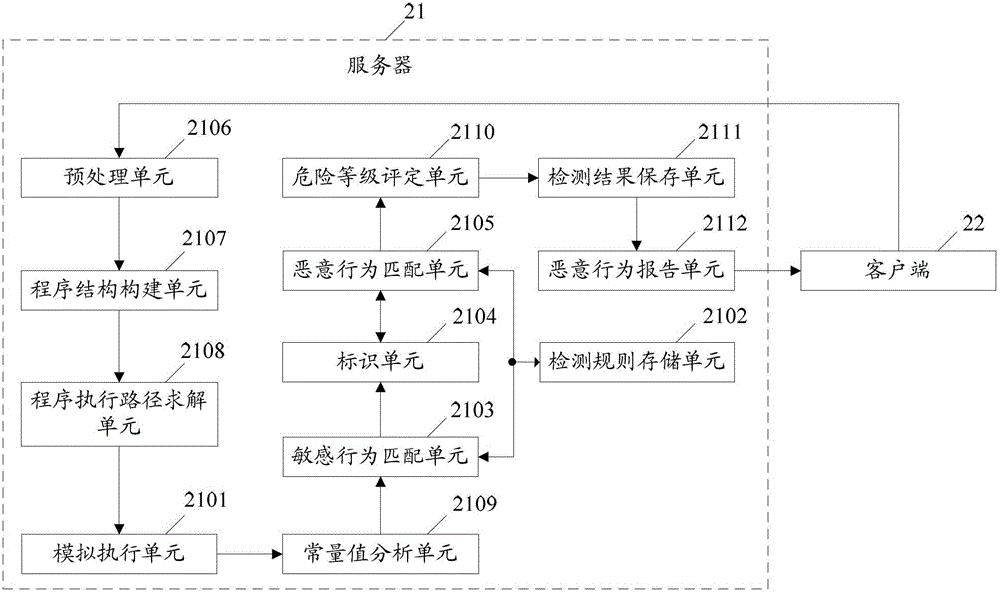
[0082] figure 2 It is a schematic diagram of the composition structure of the Android malware detection system of the present invention, such as figure 2 As shown, the system includes: a server 21 and a client 22: among them,
[0083] The server 21 is configured to simulate the execution of the software to be detected according to the received installation package of the software to be detected uploaded by the user through the client 22UI, and compare the sensitive feature information and malicious feature information of the function called by the software to be detected with the locally stored sensitive information. The characteristic information and the malicious characteristic information are matched, and if the matching is successful, it is determined that the software to be detected is malicious software, and the detection result is sent to the client 22;
[0084] The client 22 is used to enable the user to upload the installation package of the software to be tested to the s...
Embodiment 3
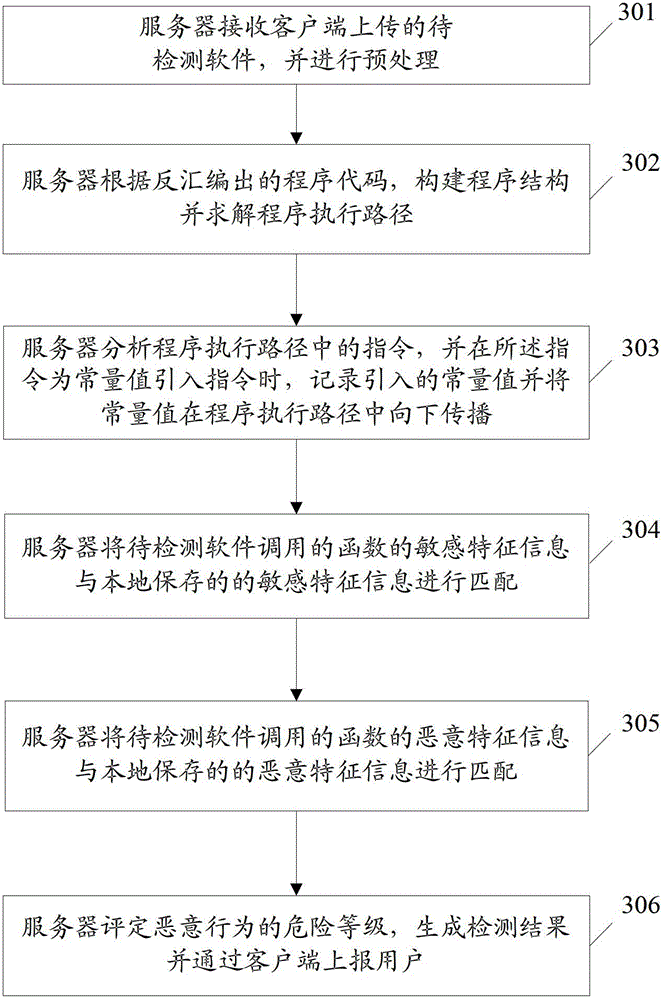
[0107] image 3 This is a schematic diagram of the implementation process of an embodiment of detecting Android malware in the present invention. The following takes hippoSMS as an example, as image 3 As shown, the process includes:
[0108] Step 301: The server receives the software to be detected uploaded by the client and performs preprocessing;
[0109] In this step, the user uploads the installation package hippoSMS.apk corresponding to the software hippoSMS to be detected to the server through the client UI. The server uses the decompression software to decompress the installation package, and extracts the bytecode file in the installation package with the suffix dex. And run the disassembly tool to disassemble the bytecode file and output the program code.
[0110] Wherein, the decompression software may use WINRAR or APKTOOL, and the disassembly tool may use IDA pro (Interactive Disassembler professional).
[0111] Step 302: The server constructs the program structure and s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com