Method and system for protecting data structure in Linux kernel initialization based on TPM (Trusted Platform Module)
A data structure and protection system technology, applied in the direction of digital data protection, platform integrity maintenance, etc., can solve problems such as poor real-time performance, unfavorable replay attacks, malicious code injection or dynamic modification of data structures that cannot be detected in time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
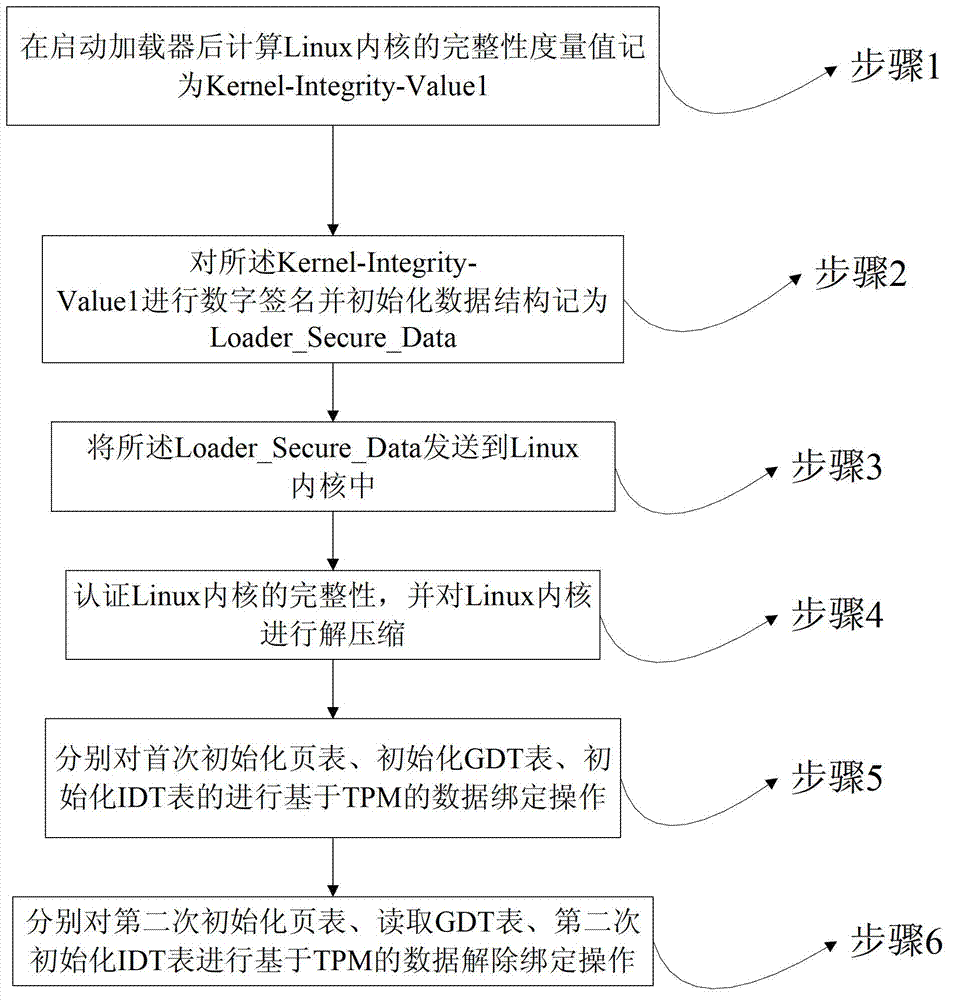
[0080] Taking GRUB-0.9.7 as the boot loader and the initialization of the Linux-2.6.32 kernel as an example, the data structure protection method in the TPM-based Linux kernel initialization of the present invention is further described.
[0081] figure 1 It is a flow chart of the data structure protection method in the TPM-based Linux kernel initialization of the present invention. Such as figure 1 As shown, the method includes:
[0082] Step 1, after booting the loader, calculate the integrity metric value of the Linux kernel as Kernel-Integrity-Value1;
[0083] Step 2, digitally sign the Kernel-Integrity-Value1 and initialize the data structure as Loader_Secure_Data;
[0084] Step 3, sending the Loader_Secure_Data to the Linux kernel;
[0085] Step 4, verify the integrity of the Linux kernel, and decompress the Linux kernel;
[0086] Step 5, perform TPM-based data binding operations on the initial page table initialization, initialization GDT table, and initialization ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com