Data protection method and device
A data protection and data technology, applied in the direction of digital data protection, digital data authentication, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
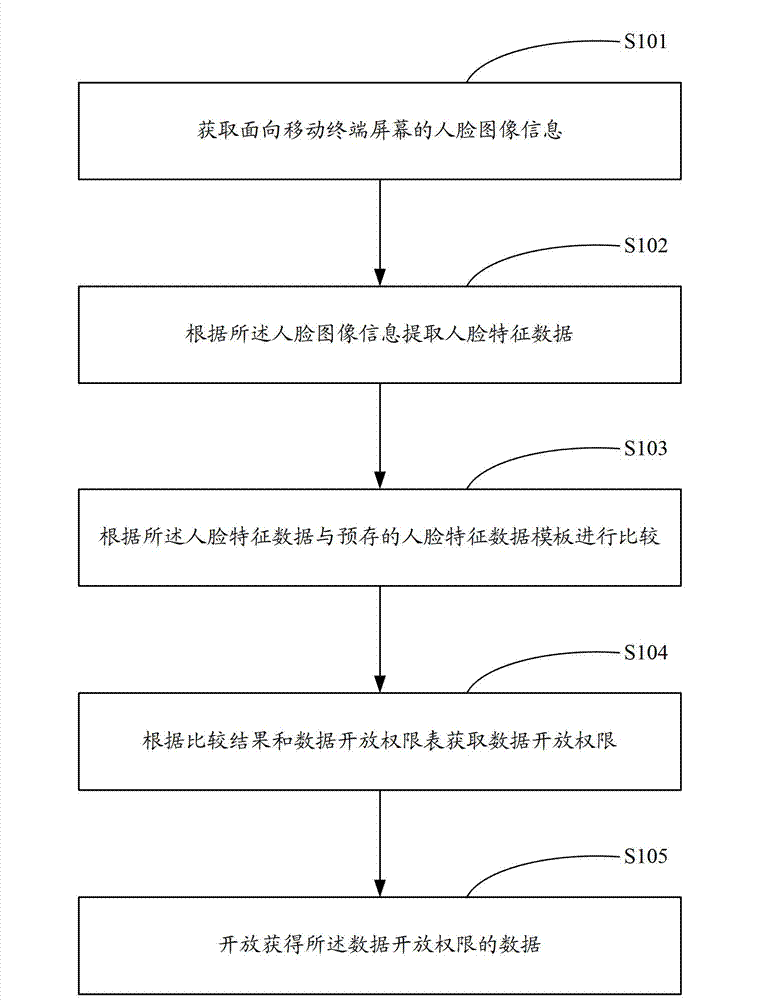
[0023] figure 1 The data protection implementation process provided by the first embodiment of the present invention is shown, and the process is described in detail as follows:
[0024] Step S101, acquiring face image information facing the screen of the mobile terminal.
[0025] At present, passwords, patterns, etc. have been used as unlocking or booting methods; this embodiment also has the function of the above-mentioned unlocking or booting methods, and a data protection function is added on this basis, and the data protection function provides the method. In the data protection mode, the data protection provided by this method is realized by enabling the data protection function.
[0026] In order to prevent users who have not obtained the data open permission from seeing the private data, setting a password or pattern unlock method may destroy the friendship, the user can enable the data protection function, which can avoid destroying the friendship and protect the pri...
Embodiment 2
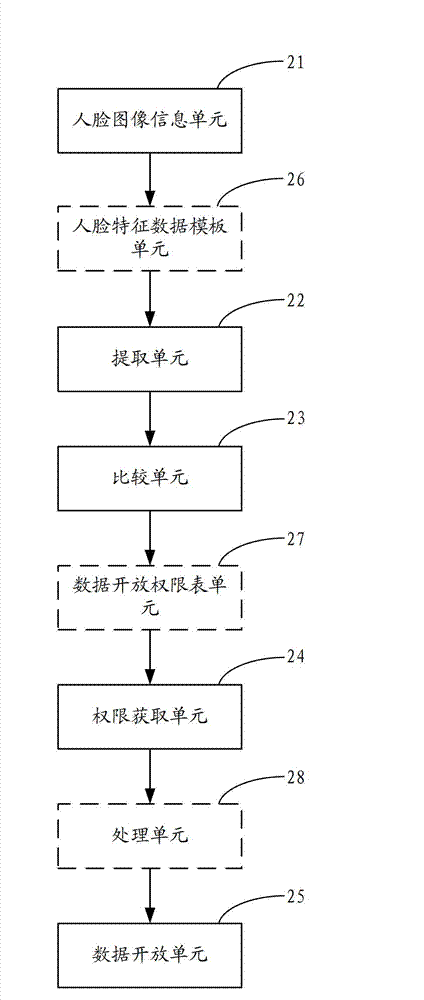
[0054] figure 2 The composition structure of the data protection device provided by the second embodiment of the present invention is shown, and for the convenience of description, only the parts related to the embodiment of the present invention are shown.
[0055] The data protection device can be a software unit, a hardware unit, or a combination of software and hardware running in each terminal device (such as a tablet computer, a smart phone), or it can be integrated into the terminal device as an independent pendant or run on a In the application system of the terminal device.
[0056] The present embodiment provides a data protection device, which can include a face image information unit 21, an extraction unit 22, a comparison unit 23, an authority acquisition unit 24, and a data opening unit 25, wherein each functional unit is described in detail as follows:
[0057] The face image information unit 21 is configured to acquire face image information facing the screen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com