Method and device processing commands
A technology for processing instructions and instructions, applied in the field of information security, can solve problems such as the security of the message transmission system, and achieve the effect of improving security and confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
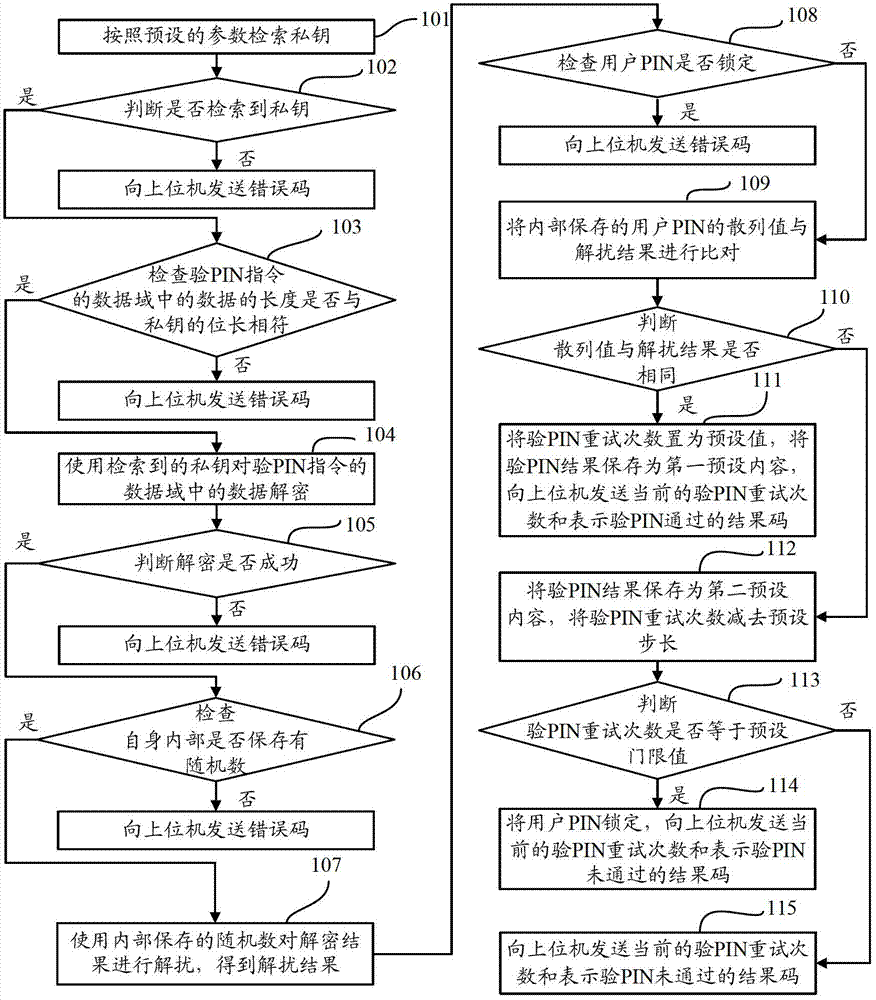
[0050] After the receiving device receives the PIN verification instruction from the host computer, the operations performed are as follows: figure 1 shown, including the following steps:
[0051] Step 101, retrieve the private key according to preset parameters.
[0052] Wherein, the preset parameters may be KID (Key Identity, key identifier) and Usage (usage).
[0053] Step 102, judge whether the private key is retrieved, if the private key is retrieved, execute step 103; otherwise, send an error code to the upper computer.
[0054] Step 103, check whether the length of the data in the data field of the PIN (Personal Identification Number, personal identification password) command matches the bit length of the private key, and if so, execute step 104; otherwise, send an error code to the host computer.
[0055] Step 104, use the retrieved private key to decrypt the data in the data field of the verification PIN instruction.
[0056] Specifically, the RSA algorithm can be ...
Embodiment 2
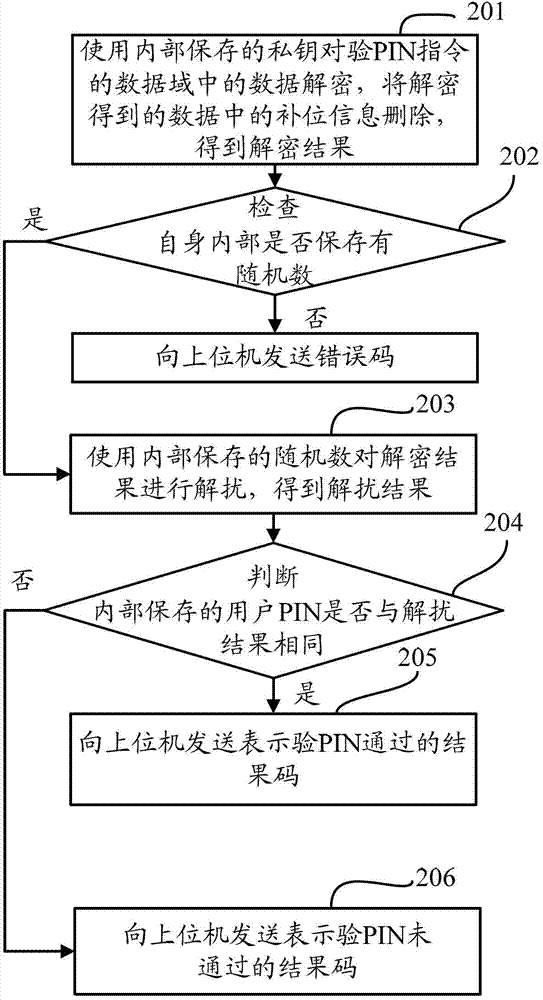
[0078] After the receiving device receives the PIN verification instruction from the host computer, the operations performed are as follows: figure 2 shown, including the following steps:
[0079] Step 201: Decrypt the data in the data field of the verification PIN command using the internally stored private key, delete the supplementary information in the decrypted data, and obtain a decryption result.
[0080] Among them, the RSA algorithm can be used to decrypt the private key. Correspondingly, the supplementary information can be data starting with "0001FF" and ending with "FF00", or starting with "0002" and ending with "00". end, and fill the data of one or more random numbers between "0002" and "00".
[0081] Step 202, check whether there is a random number stored inside itself, if yes, execute step 203; otherwise, send an error code to the host computer.
[0082] Step 203, use the internally stored random number to descramble the decrypted result to obtain the descra...
Embodiment 3
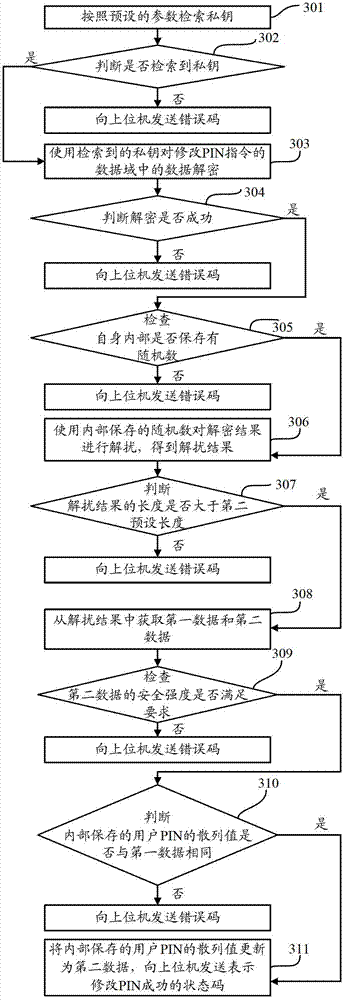
[0090] After the receiving device receives the modification PIN command from the host computer, the operations performed are as follows: image 3 shown, including the following steps:
[0091] In step 301, the private key is retrieved according to preset parameters.
[0092] Wherein, the preset parameters may be KID and Usage.
[0093] Step 302, judge whether the private key is retrieved, if the private key is retrieved, then execute step 303; otherwise, send an error code to the upper computer.
[0094] Step 303, using the retrieved private key to decrypt the data in the data field of the PIN modification instruction.
[0095] Specifically, the RSA algorithm can be used to decrypt the private key.
[0096] Step 304, judge whether the decryption is successful, if successful, execute step 305; otherwise, send an error code to the upper computer.
[0097] Step 305, check whether there is a random number stored inside itself, if yes, execute step 306; otherwise, send an error...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com