File security control method and device
A security and control technology, applied in the field of data security, can solve the problems of delaying office processes, unable to browse shared files in a timely manner, unable to control user access rights to shared files in real time, etc., to ensure security and avoid untimely encryption keys Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
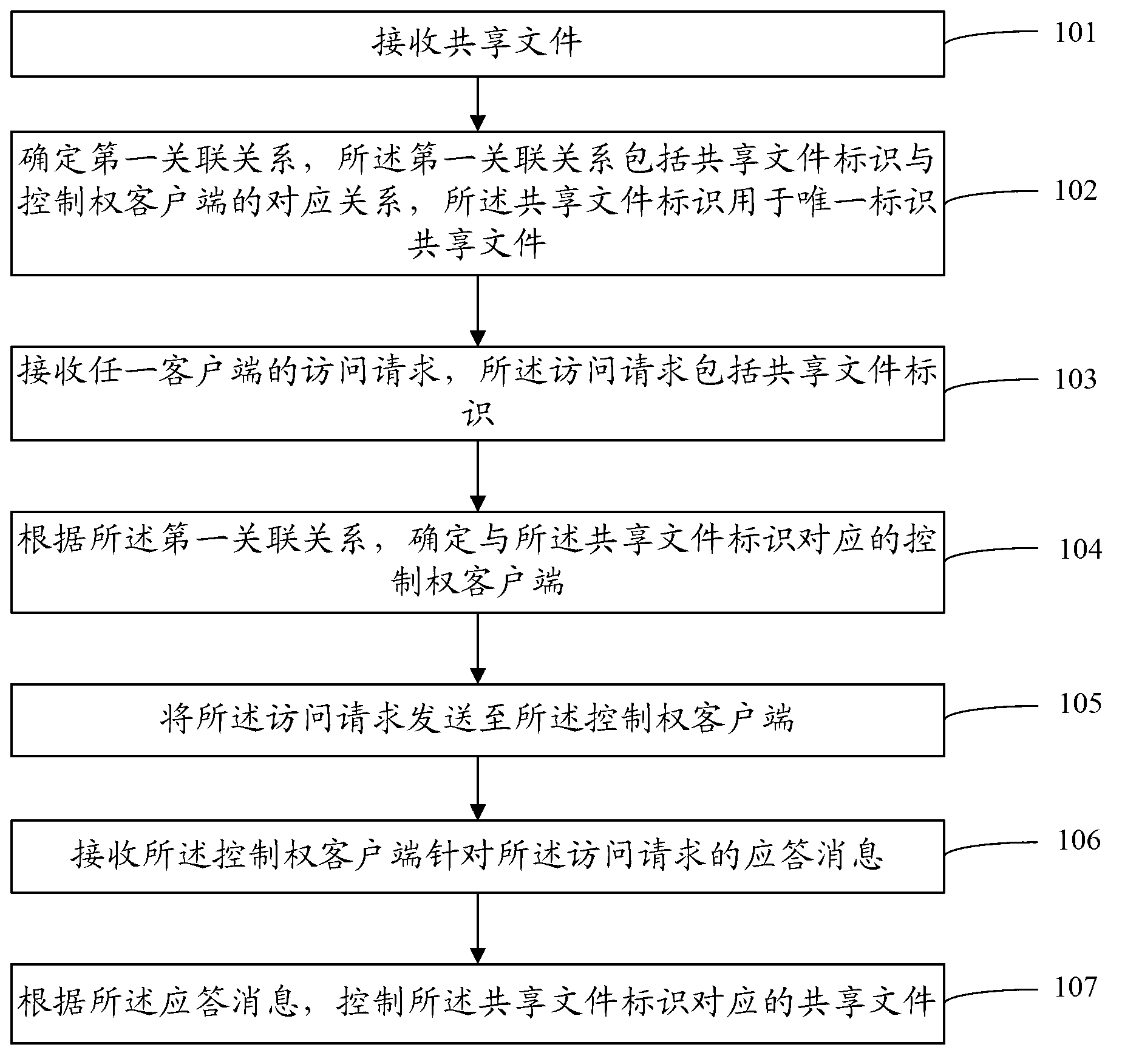
[0061] refer to figure 1 , figure 1 The flow chart of the method for controlling file security provided in this embodiment specifically includes:
[0062] Step 101, receiving a shared file.
[0063]In this embodiment, the system receives shared files, and the specific process of receiving files is not limited, and all are within the protection scope of the present invention. Wherein, the shared files include files in the form of Word documents, pictures, Excel tables, and the like. The form and content of specific shared files are not limited.
[0064] In a preferred embodiment, before receiving the shared file, the system may first authenticate the client that uploaded the shared file. Specifically, the system pre-stores the authentication information of the client with authority. When the client enters the authentication information , the system judges whether the uploaded identity information belongs to a client with permission. If yes, it allows uploading of shared fil...
Embodiment 2
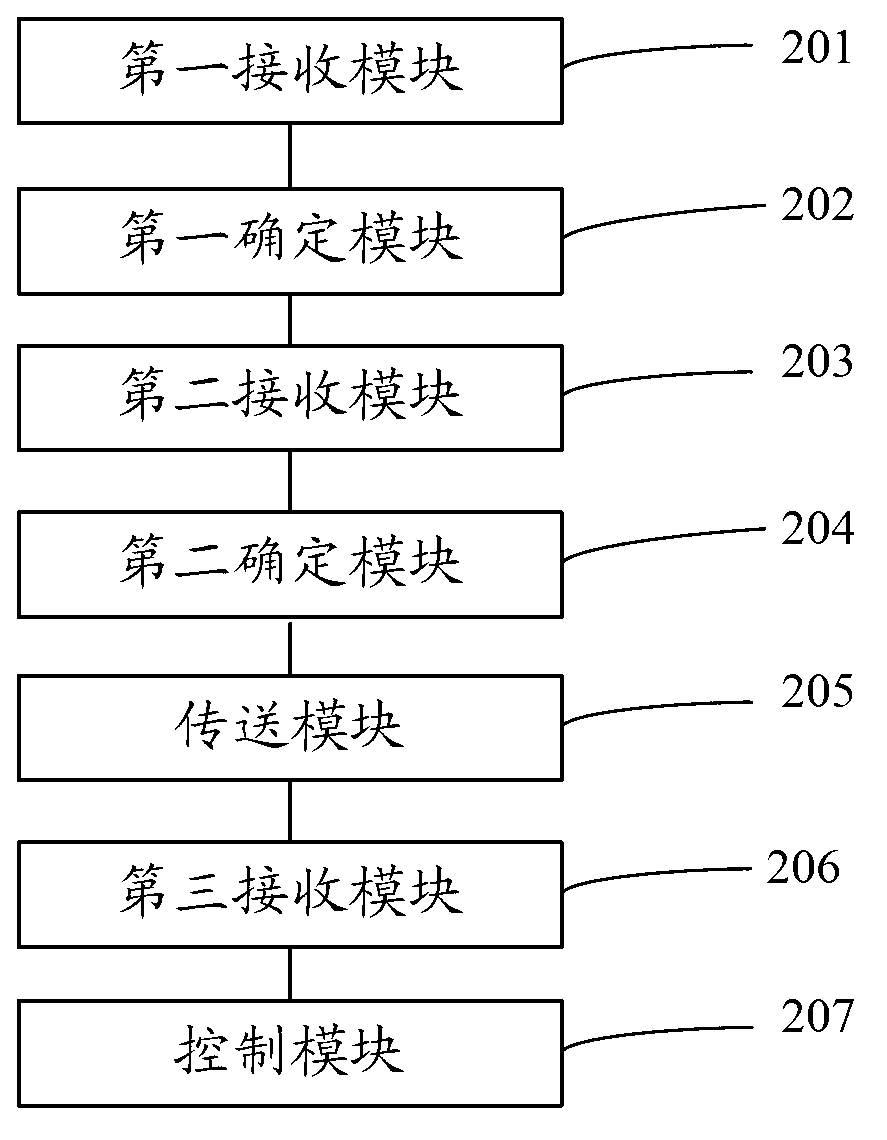
[0110] refer to figure 2 , figure 2 The device structure diagram for controlling file security provided in this embodiment may specifically include:
[0111] The first receiving module 201 is configured to receive shared files;
[0112] The first determining module 202 is configured to determine a first association relationship, the first association relationship includes a corresponding relationship between a shared file identifier and a control client, and the shared file identifier is used to uniquely identify the shared file;
[0113] The second receiving module 203 is configured to receive an access request from any client, where the access request includes a shared file identifier;
[0114]The second determination module 204 is configured to determine the control client corresponding to the shared file identifier according to the first association relationship;
[0115] A sending module 205, configured to send the access request to the control right client;
[0116...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com