Method and device for verifying data accuracy
A verification method and a technology of a verification device, which are applied in the field of data processing, can solve problems such as insufficient monitoring and processing, and achieve the effect of timely monitoring and verification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
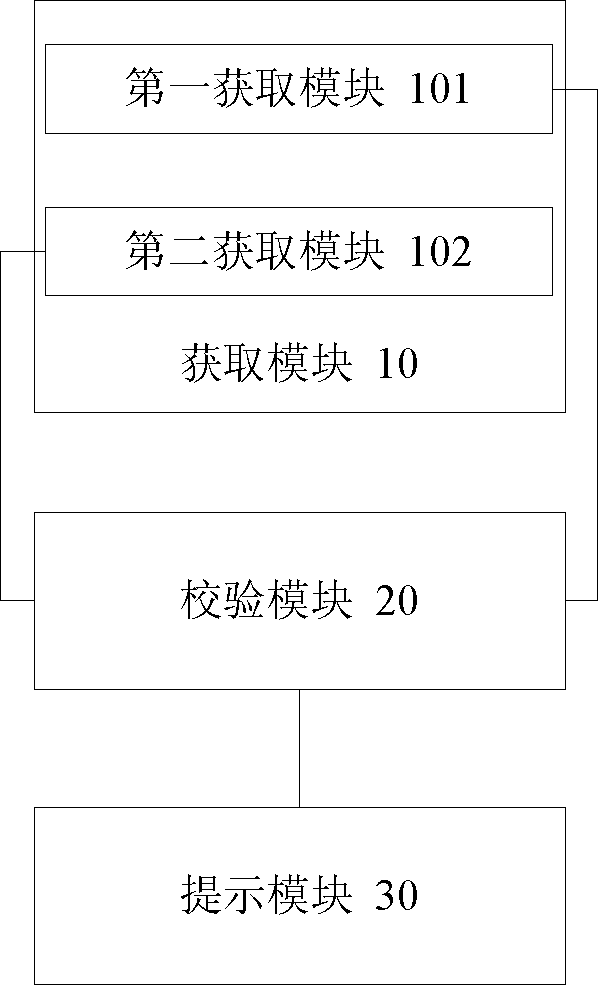
[0039] figure 1 is a schematic diagram of a verification device for data accuracy according to the first embodiment of the present application.
[0040] Such as figure 1 As shown, the data accuracy verification device includes an acquisition module 10 , a verification module 20 and a prompt module 30 .
[0041] Wherein, the obtaining module 10 is used to obtain verification rule information related to the target table, wherein the target table is a target data table that needs to be verified for data accuracy, wherein the verification rule information can be stored in a pre-configured table In , the verification rule refers to the logical rule for verifying the accuracy of the data, which is the standard for judging whether the data is accurate.
[0042] The verification module 20 is used to verify the data accuracy of the target table by using the verification rule information related to the target table. Specifically, the verification module 20 can use one or more pieces o...
Embodiment 2
[0048] In order to improve the versatility of the verification rules, as a preferred implementation of Embodiment 1, the acquisition module 10 may include a first acquisition module 101 and a second acquisition module 102, such as figure 2 shown.
[0049] The first obtaining module 101 is used to obtain the verification rule information related to the first target table in the verification rule configuration table; the second obtaining module 102 is used to obtain the verification rule information related to the second target table in the verification rule configuration table. verification rule information, where the verification rule information related to multiple target tables is configured in the verification rule configuration table.
[0050] This application defines a common verification rule configuration table in the data warehouse, and configures the data verification rules with the target table as the center. Further, by setting multiple acquisition modules in the d...
Embodiment 3
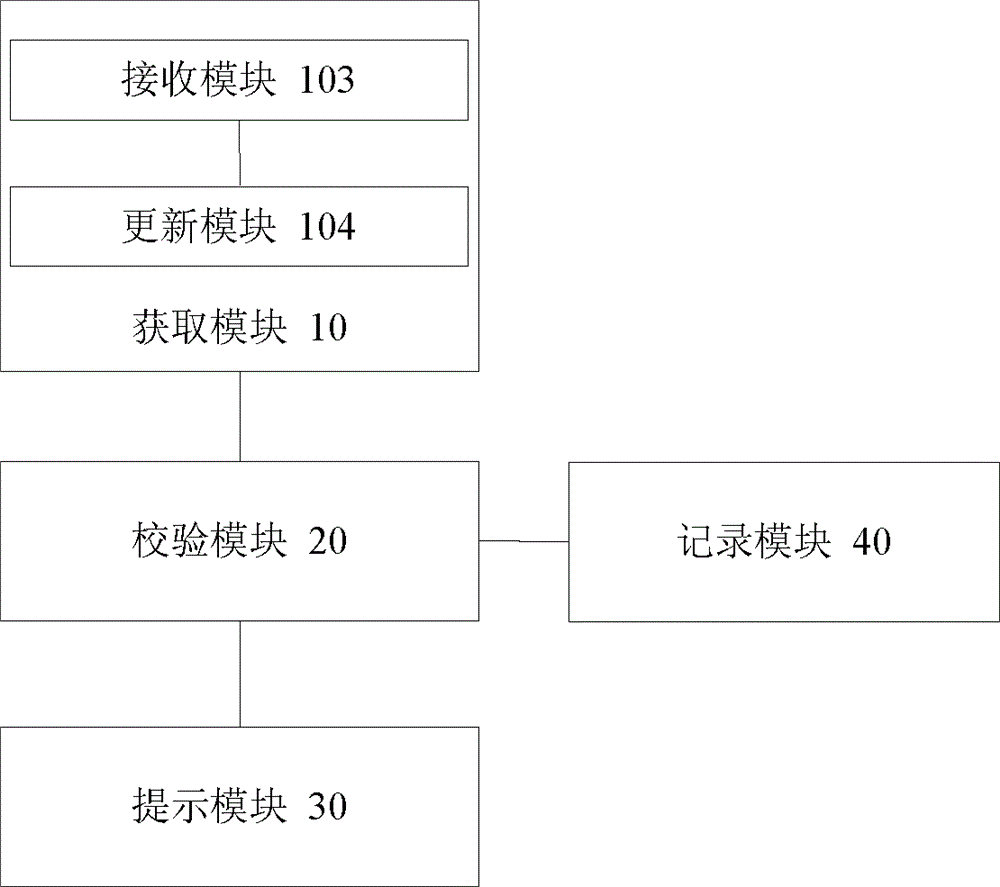
[0052] In order to facilitate the update of the verification rules and facilitate maintenance, as a preferred method of Embodiment 1, the acquisition module 10 may include a receiving module 103 and an updating module 104, such as image 3 shown.
[0053] The receiving module 103 is used for receiving the verification rule information input by the user, and the updating module 104 is used for updating the verification rule information in the verification rule configuration table according to the received verification rule information.
[0054] The acquiring module 10 in this embodiment may only include the receiving module 103 and the updating module 104 , or may include the first acquiring module 101 , the second acquiring module 102 , the receiving module 103 and the updating module 104 .
[0055] As described in Embodiment 2 above, this application realizes the unified configuration of the verification rules through the general verification rule configuration table, so that...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com