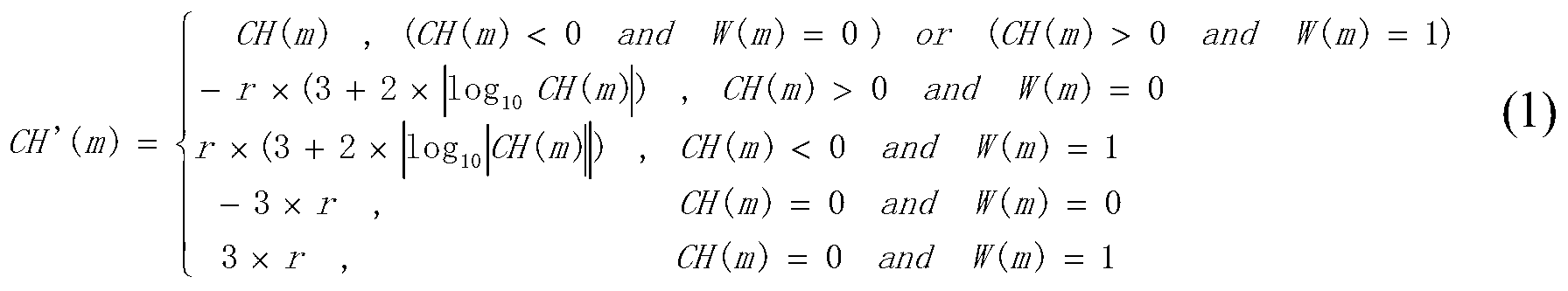Digital watermarking method with robustness and transparency in optimum balance
A digital watermark, the best balanced technology, applied in the field of information security, can solve the problem of short generation time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0037] Using the 512×512 gray-scale image Lena.bmp in the international general digital watermarking standard test image library as the original carrier image, using the attachment drawing in the Windows XP system as a tool, to make the words "Shaanxi Normal University" in bold Song typeface on the 9th The composed 64×64 binary image Shaanxi Normal University.bmp is used as a watermark, and the binary image watermark embedding and extraction are respectively carried out as an example. The method is as follows:
[0038] 1. Binary image watermark embedding process
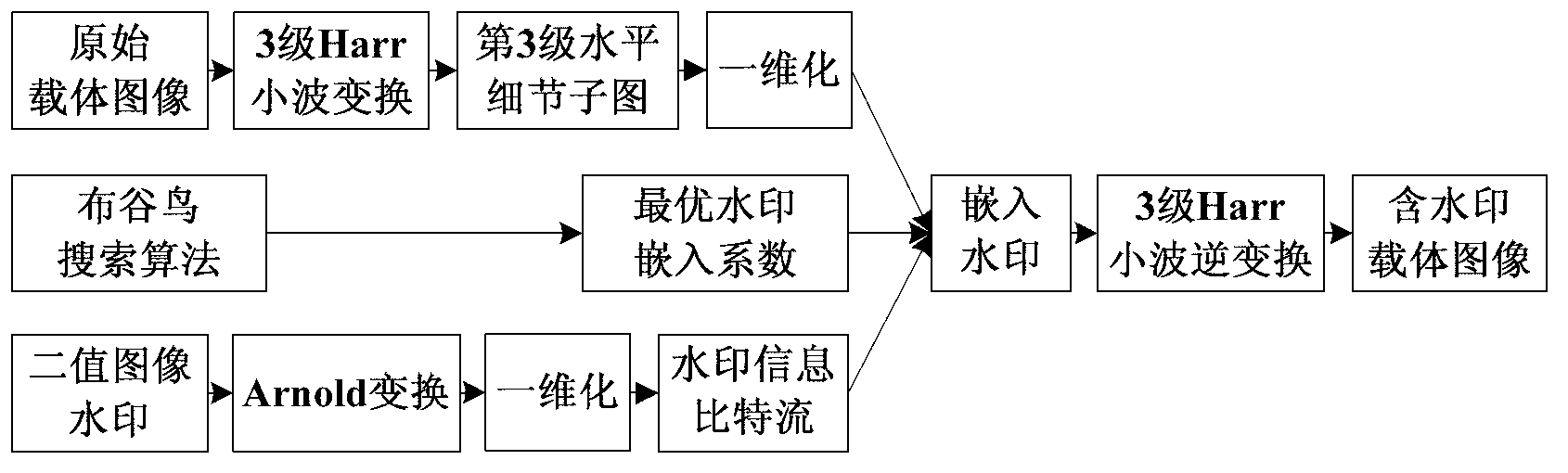
[0039] Such as figure 1 As shown, the specific steps of the embedding process of the binary image watermark Shaanxi Normal University.bmp are as follows:
[0040] (1) Preprocessing of the original carrier image
[0041] The 512×512 original carrier image Lena.bmp is decomposed by three-level Harr wavelet to obtain the first-level horizontal detail sub-image, the first-level vertical detail sub-image, the first-lev...
Embodiment 2
[0064] Using the 512×512 grayscale image Airplane.bmp in the international general digital watermarking standard test image library as the original carrier image, the 64×64 binary image watermark Shaanxi Normal University.bmp is the same as in Example 1, and the binary image watermark is embedded respectively And extract as an example, the method is as follows:
[0065] 1. Binary image watermark embedding process
[0066] Such as figure 1 As shown, the specific steps of the embedding process of the binary image watermark Shaanxi Normal University.bmp are as follows:
[0067] The preprocessing step (1) of the carrier image Airplane.bmp and the preprocessing step (2) of the binary image watermark Shaanxi Normal University.bmp are the same as those in Embodiment 1.
[0068] In the embedding step (3) of the watermark information bit stream, use the formula (1) to embed the watermark information bit stream in the third-level level detail sub-graph of the original carrier image A...
Embodiment 3
[0078] Using the 512×512 grayscale image Peppers.bmp in the international general digital watermarking standard test image library as the original carrier image, the 64×64 binary image watermark Shaanxi Normal University.bmp is the same as in Example 1, and the binary image watermark is embedded respectively And extract as an example, the method is as follows:
[0079] 1. Binary image watermark embedding process
[0080] Such as figure 1 As shown, the specific steps of the embedding process of the binary image watermark Shaanxi Normal University.bmp are as follows:
[0081] The preprocessing step (1) of the original carrier image Peppers.bmp and the preprocessing step (2) of the binary image watermark Shaanxi Normal University.bmp are the same as those in Embodiment 1.
[0082] In the embedding step (3) of the watermark information bit stream, use the formula (1) to embed the watermark information bit stream in the third level detail sub-image of the original carrier image ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com