A client log processing method and device
A processing method and client-side technology, applied in the field of communication, can solve the problems of limited log quantity, low log security, limited disk space, etc., and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
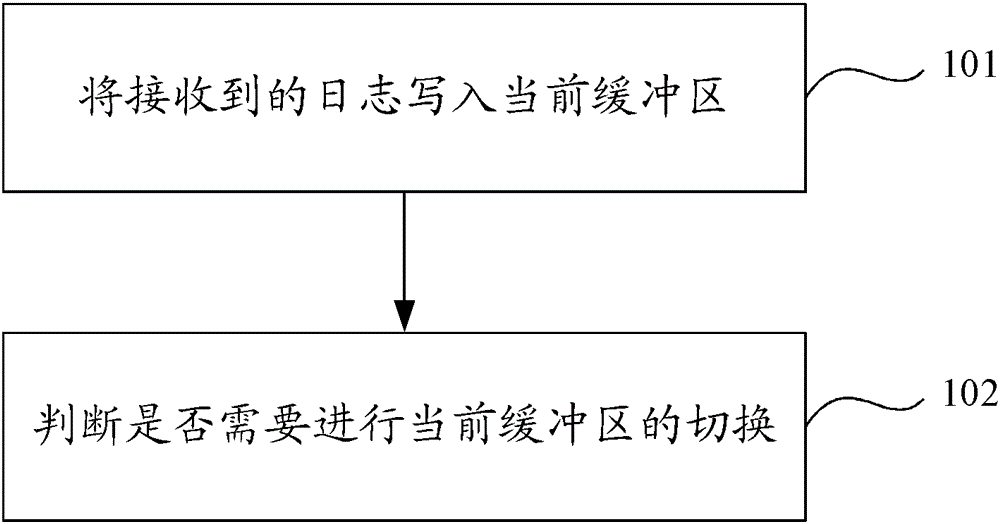
[0027] Embodiment 1 of the present application provides a client log processing method, the steps of the method are as follows figure 2 shown, including:
[0028] Step 101, write the received log into the current buffer.
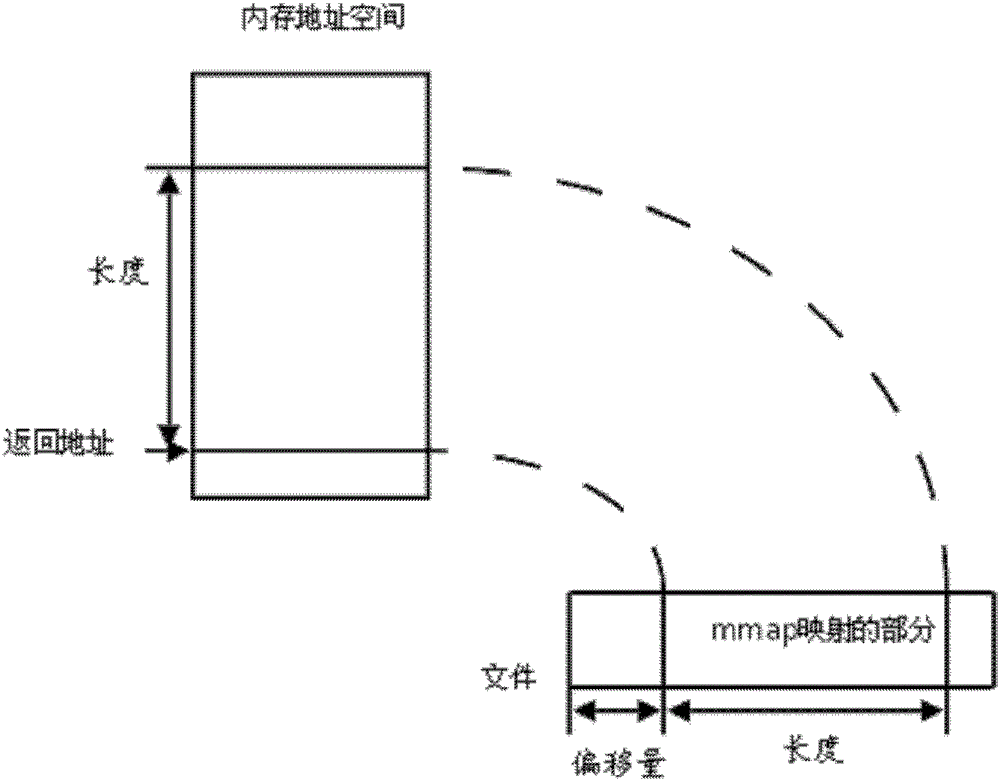
[0029] In this embodiment, two pieces of MMAP memory are set as the buffer, in this step, when receiving the log, write the log into the MMAP memory as the current buffer (this MMAP memory can be referred to as the first MMAP memory ).
[0030] Specifically, the data packet sent by the client through the POST mode of the hypertext transfer protocol (HTTP, HyperTextTransferProtocol) can be received, and the cyclic redundancy check (CRC) check is performed on the data packet, such as CRC16 check, when the check is passed , the asynchronous thread can be started to write the log in the data packet into the first MMAP memory as the current buffer (that is, receiving the data packet and checking the data packet can be synchronous, that is, the same thread can ...
Embodiment 2
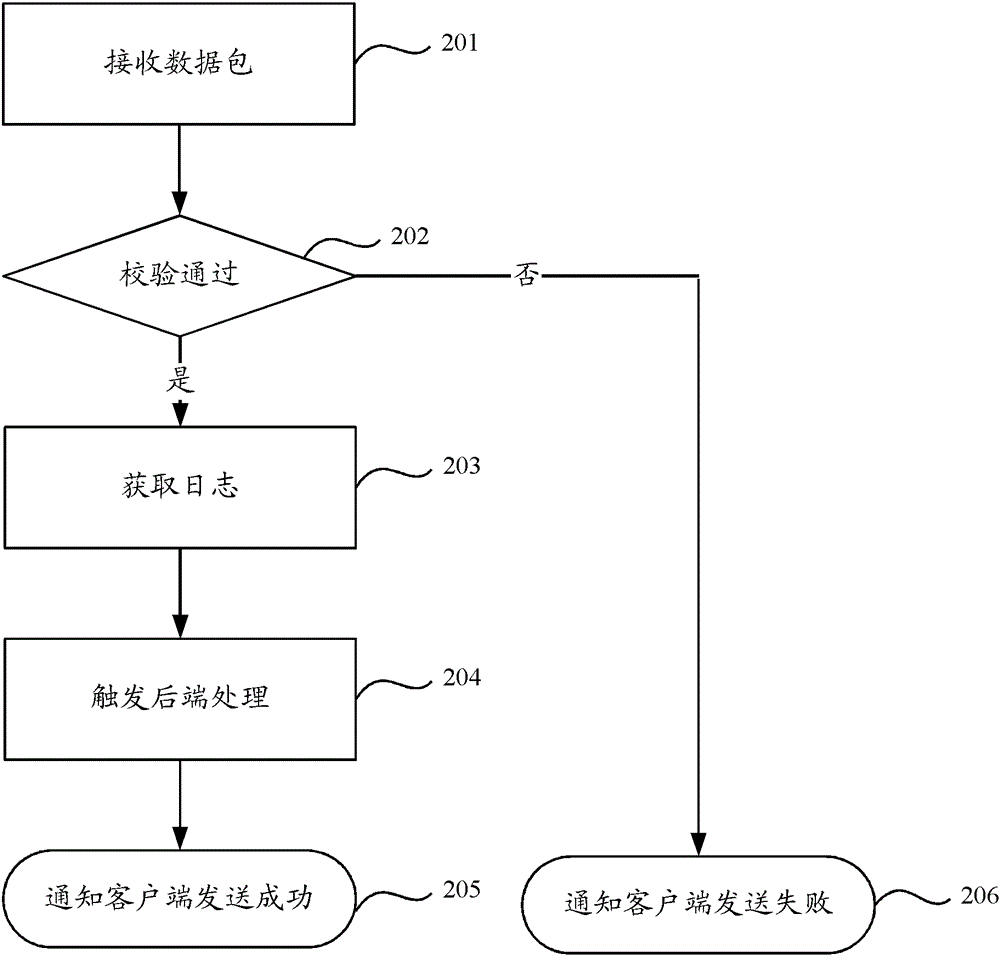
[0041] Embodiment 2 of the present application provides a front-end processing method, the step flow of the method is as follows image 3 shown, including:
[0042] Step 201, receiving a data packet.
[0043] In this step, the mobile client can transmit the collected logs (in the form of data packets) to the server through the POST method of the HTTP protocol.
[0044] Step 202, perform verification.
[0045] In this step, after receiving the data packet, the server first performs a crc16 check on the integrity of the data in the data packet to determine whether it is complete. If it is determined to be complete, it can continue to perform steps 203 to 205. If it is determined to be incomplete, It indicates that the data packet is incomplete or the data packet has been tampered with, and the execution of step 206 can be skipped.
[0046] Step 203, obtaining logs.
[0047] In this step, according to the protocol, the data packet can be decompressed and assembled to obtain t...
Embodiment 3
[0055] Embodiment 3 of the present application provides a back-end double-buffering processing method. The steps of the method are as follows: Figure 4 shown, including:
[0056] Step 301. Determine the logs obtained after front-end processing.
[0057] After being processed by the front end, the logs sent by the client can be obtained. And the obtained logs can be used to asynchronously trigger back-end double-buffering processing.
[0058] Step 302, write the obtained log into the current buffer.
[0059] In this step, the obtained log may be written into the MMAP memory as the current buffer.
[0060] Step 303, judging whether there is an exception of insufficient space in the current buffer.
[0061] In this step, it is possible to determine whether the MMAP memory as the current buffer is full by judging whether the current buffer returns a prompt that the memory is full, and when receiving the prompt that the memory returned by the current buffer is full, determine ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com