Tenant-driven security system and method in storage cloud
A tenant, secure technology, applied in the field of cloud computing, which can solve the problem of customers not fully trusting data and so on
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
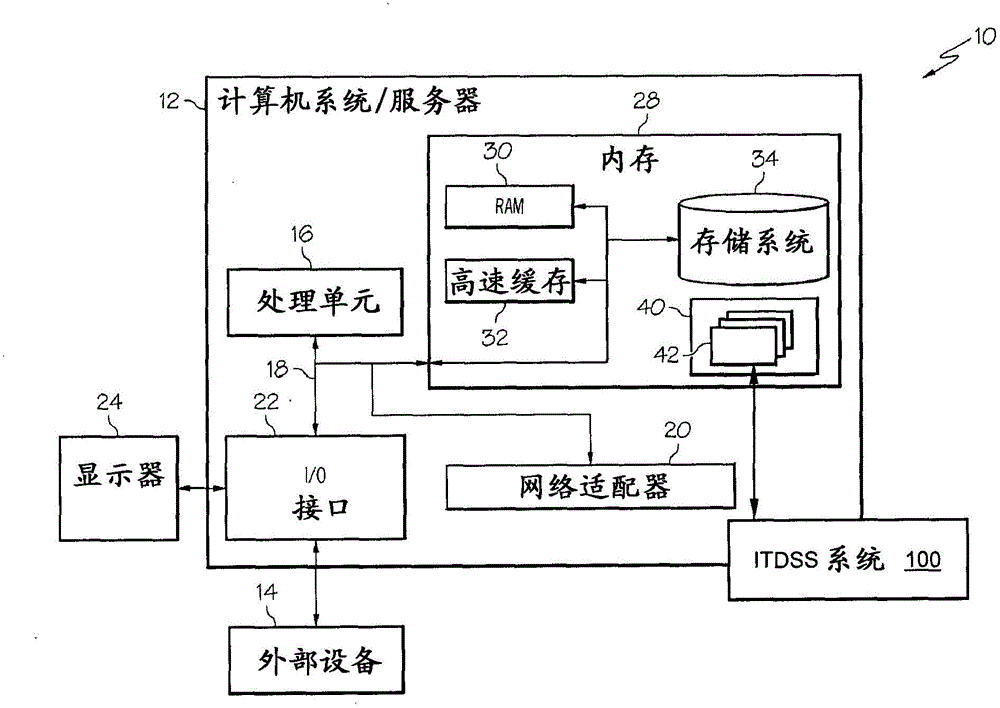
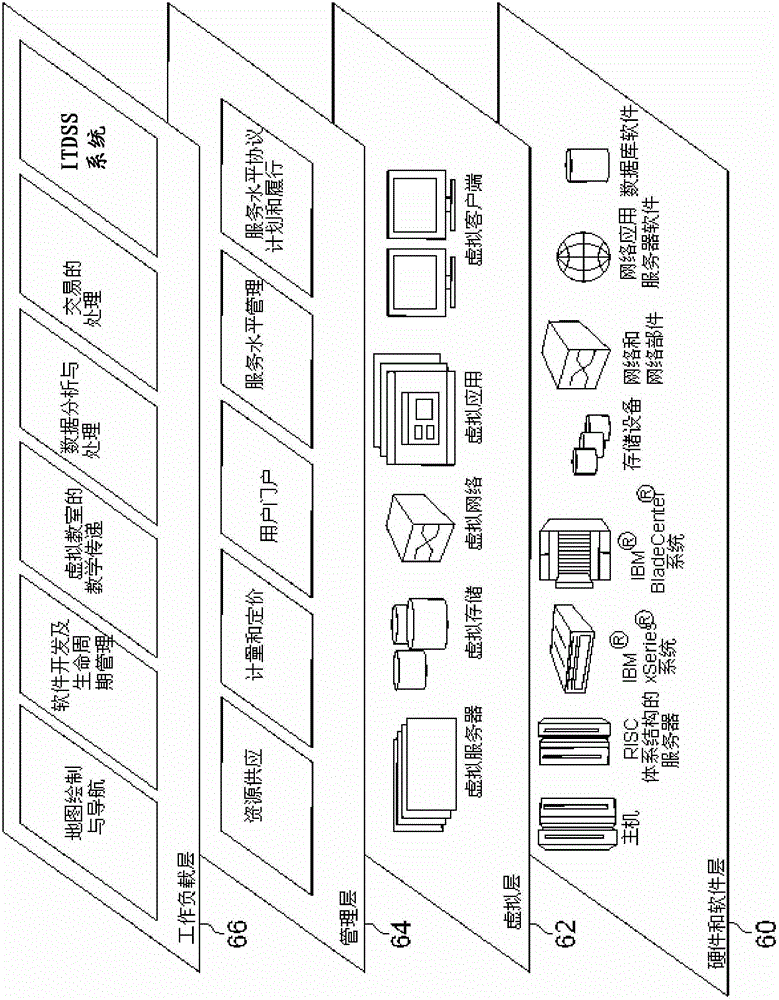
[0016] The present invention relates generally to cloud computing and, more particularly, to tenant-driven security in storage clouds. In an embodiment, the present invention includes an Intelligent Tenant Drive Security Steward (ITDSS) system that provides control over one or more tenants or customers (eg, companies) of one or more cloud services to share data security. The ITDSS system may include a hard (eg, physical) key assigned to each tenant and a Key Hook Substrate (KHS) with a slot suitable for the corresponding hard key. The ITDSS system may also include a hard key controller or "core ITDSS" located in the KHS, which works together with the hard disk controller of at least one hard disk provided by the cloud service.
[0017] In one implementation, to ensure data security in the cloud service, the hard disk controller defaults to Access is denied until the tenant puts the corresponding hard key in the slot. Once this happens, the KHS and / or hard key controller will...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com