System and method for identifying unauthorized or misconfigured wireless access point
A wireless access point, unauthorized technology used in wireless communications, security devices, electrical components, etc. to reduce data loss and possibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
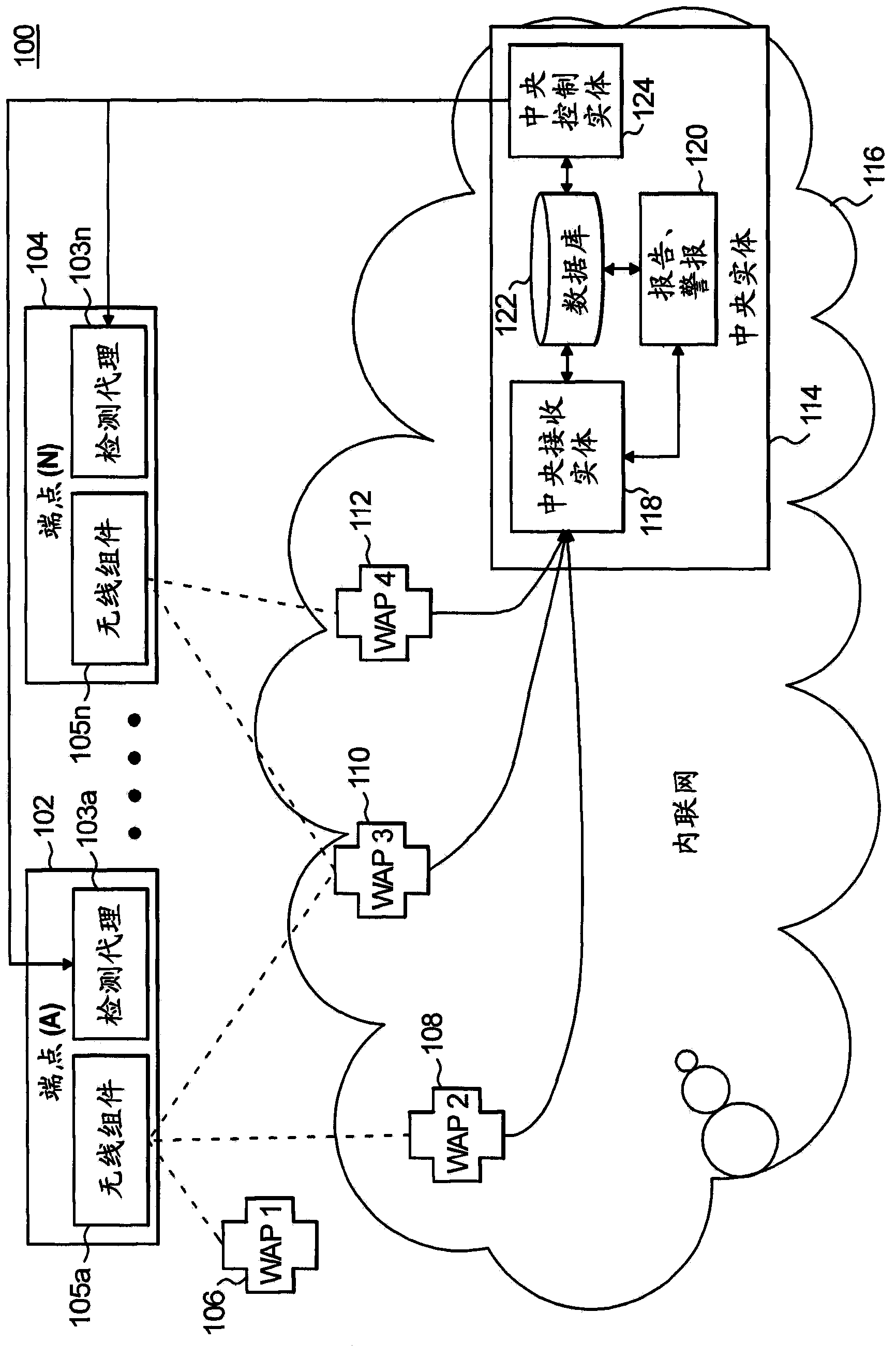
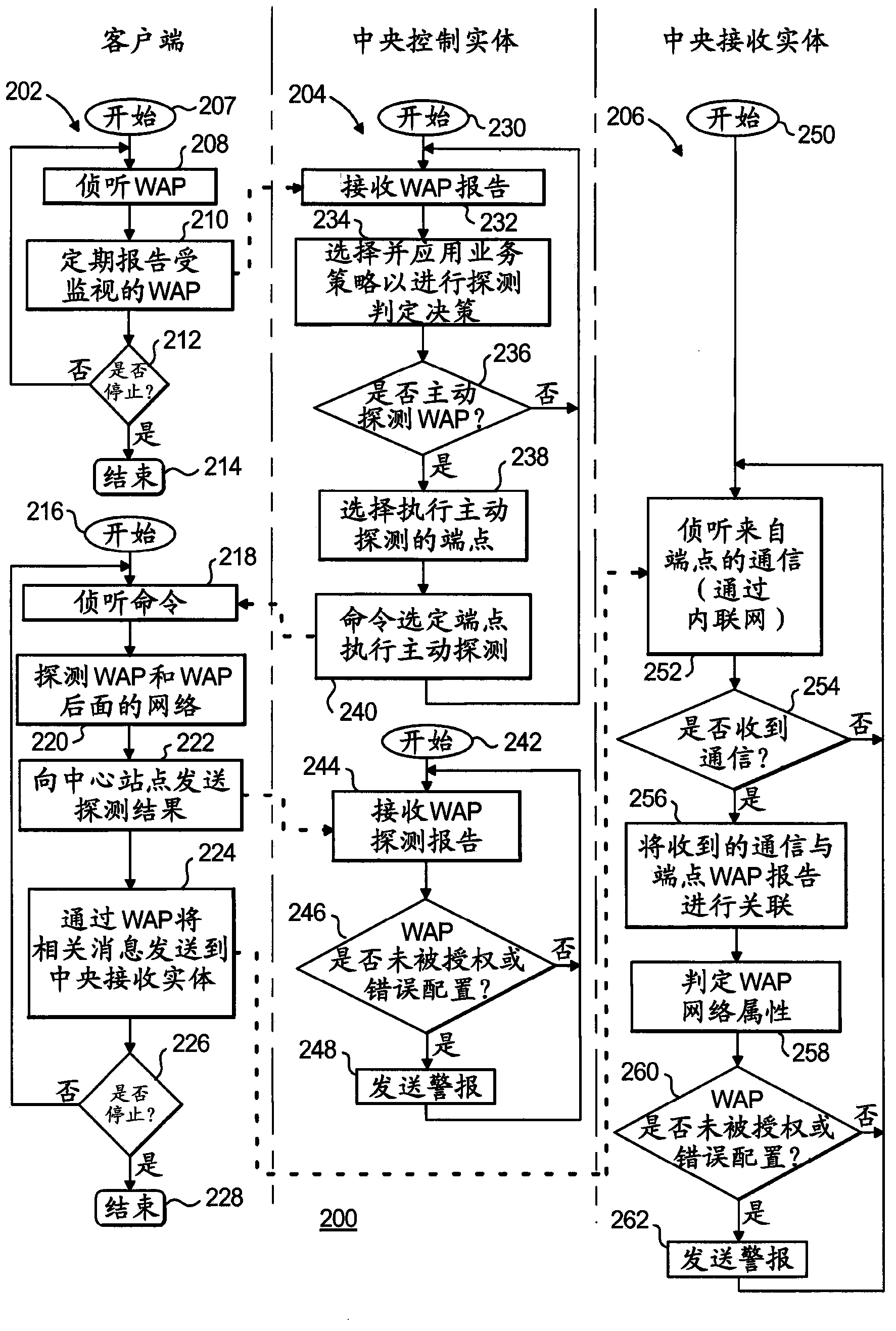
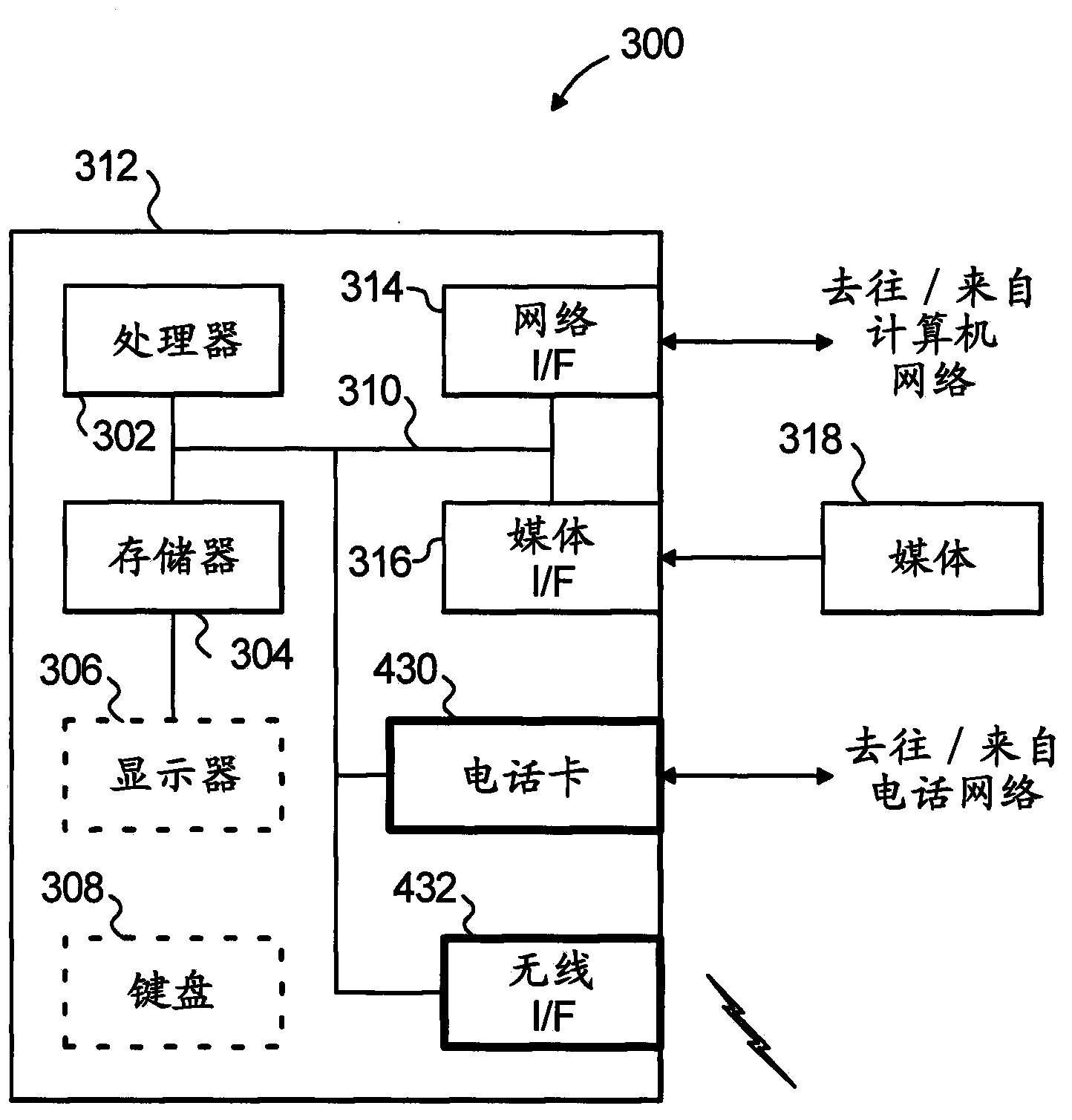
[0022] Aspects of the invention will be described herein in the context of an exemplary apparatus and method for identifying unauthorized or misconfigured wireless access points (WAPs) in a communications network (eg, a corporate intranet) that includes multiple endpoints. To this end, exemplary embodiments of the present invention advantageously place agents on multiple endpoints and then, based on the information received from the endpoints and the application of prescribed criteria (e.g., business rules), cause at least a subset of said endpoints to execute Certain operations, such as active probing operations, yield sufficient information to identify misconfigured and / or inappropriate WAPs in the network. Accordingly, techniques in accordance with exemplary embodiments of the present invention advantageously perform WAP monitoring and probing to identify unauthorized or misconfigured WAPs.
[0023] It is to be understood, however, that the invention is not limited to the s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com