Method for evolutionary analysis on anonymous graph data
An anonymous graph and graph data technology, which is applied in the field of evolution analysis of anonymous graph data, which can solve the problems of inability to perform evolution analysis, destroying identification information, and splitting snapshot connections.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0061] The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings and through specific implementation methods.
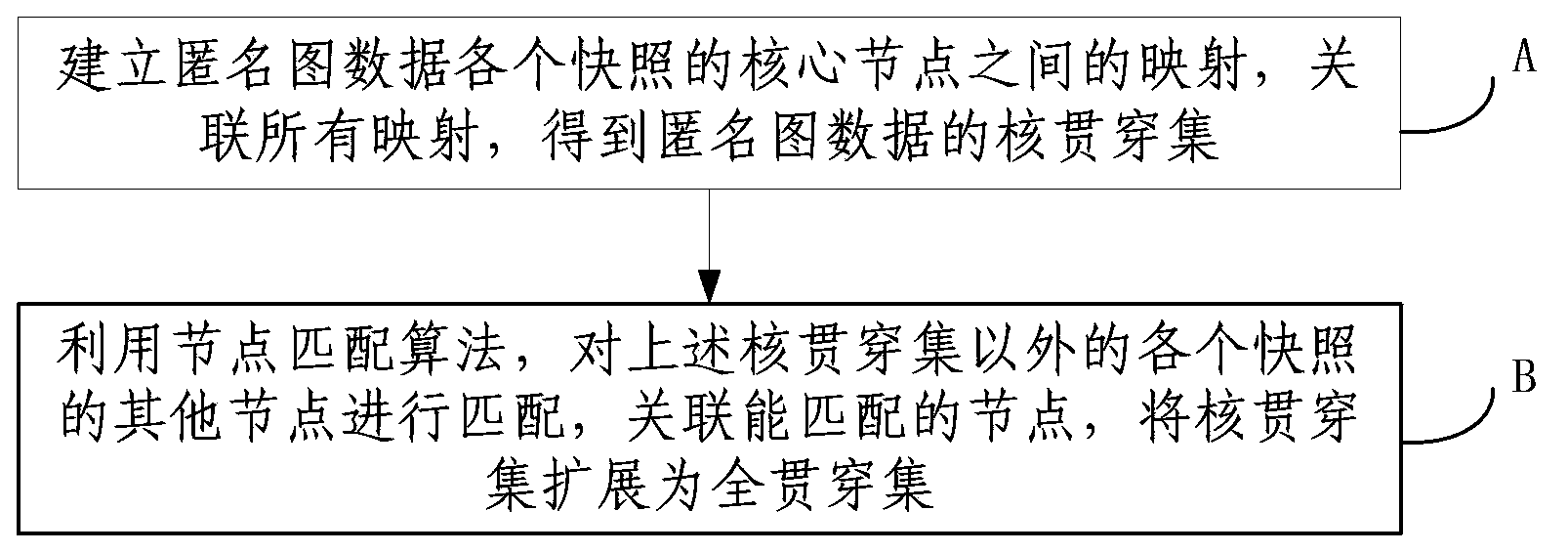
[0062] like figure 1 As shown, the embodiment of the present invention records a method for evolution analysis of anonymous graph data, the method mainly includes the following steps:
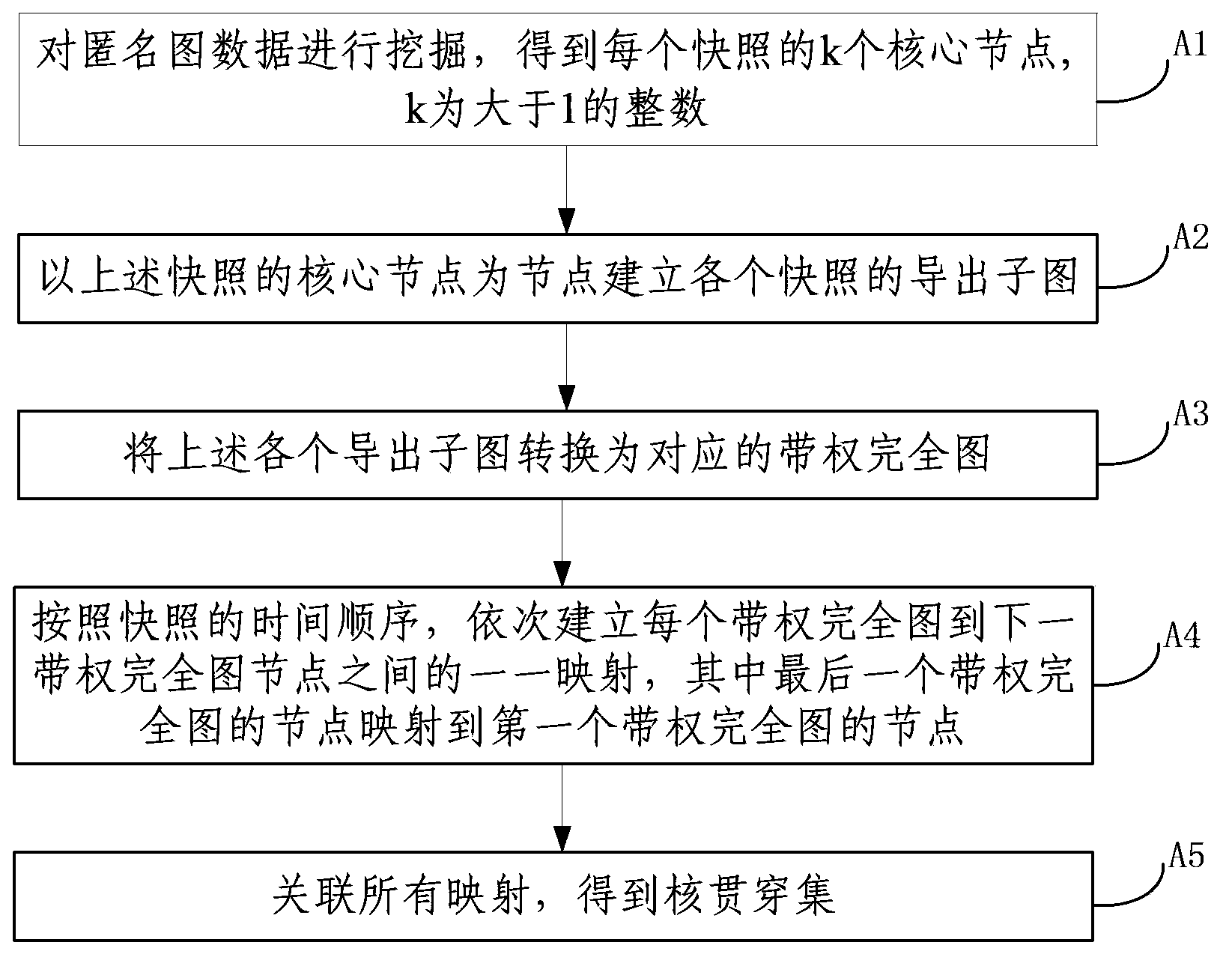
[0063] A. Establish the mapping between the core nodes of each snapshot of the anonymous graph data, associate all the mappings, and obtain the core penetration of the anonymous graph data;
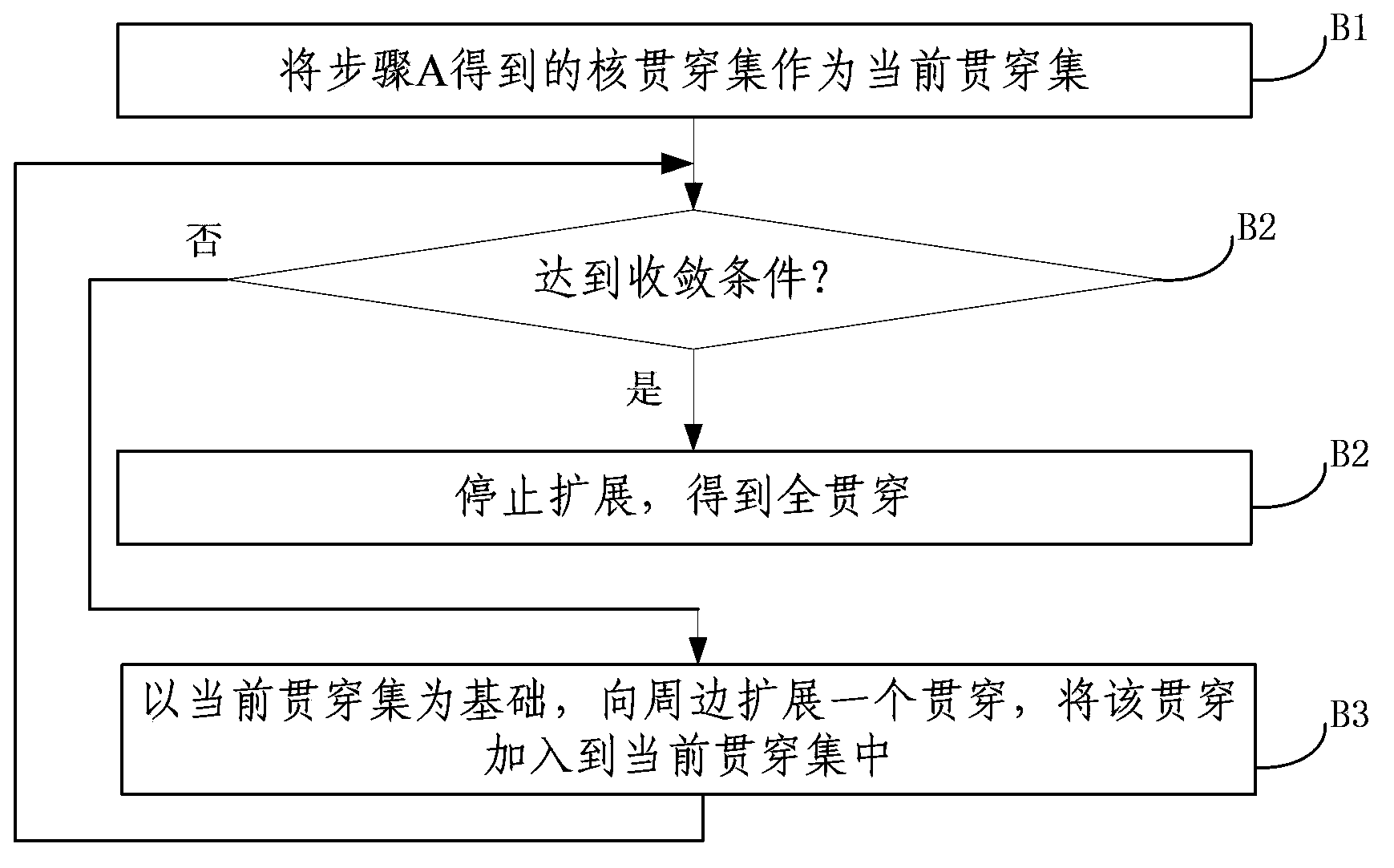
[0064] B. Use the node matching algorithm to match other nodes of each snapshot other than the above-mentioned core penetration, associate the nodes that can be matched, and expand the core penetration to full penetration;
[0065] The traversal refers to a node chain in which all nodes referring to the same object in each snapshot of the anonymous graph data are strung together in the time order of the snapshots; the core trav...
Embodiment 2
[0110] Based on Example 1, combined with Figure 4 and Figure 5 , this embodiment provides a specific implementation process of a method for performing evolution analysis on anonymous graph data.
[0111] like Figure 4 As shown, in this embodiment, a total of three snapshots of an anonymous graph data are obtained, which are recorded as like Figure 4 shown.
[0112] According to the degree of the node as the measure of the core degree of each node, select 3 nodes in each snapshot as the core nodes of the snapshot, then The corresponding core node sets are: respectively with Create a derived subgraph for the vertex set, and expand it into a weighted complete graph according to step A3 in Example 1 Calculate according to step A4 in the embodiment one again arrive the mapping m 1 ={→a2→,, arrive the mapping m 2 = {2→F, 3→B, 5→A}, arrive the mapping m 3 ={F→a, B→d, A→b}.
[0113] According to the mapping m 1 、m 2 and m 3 It can be seen that 2=m 1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com