CPU-protecting mass-flow attack identification method and device
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
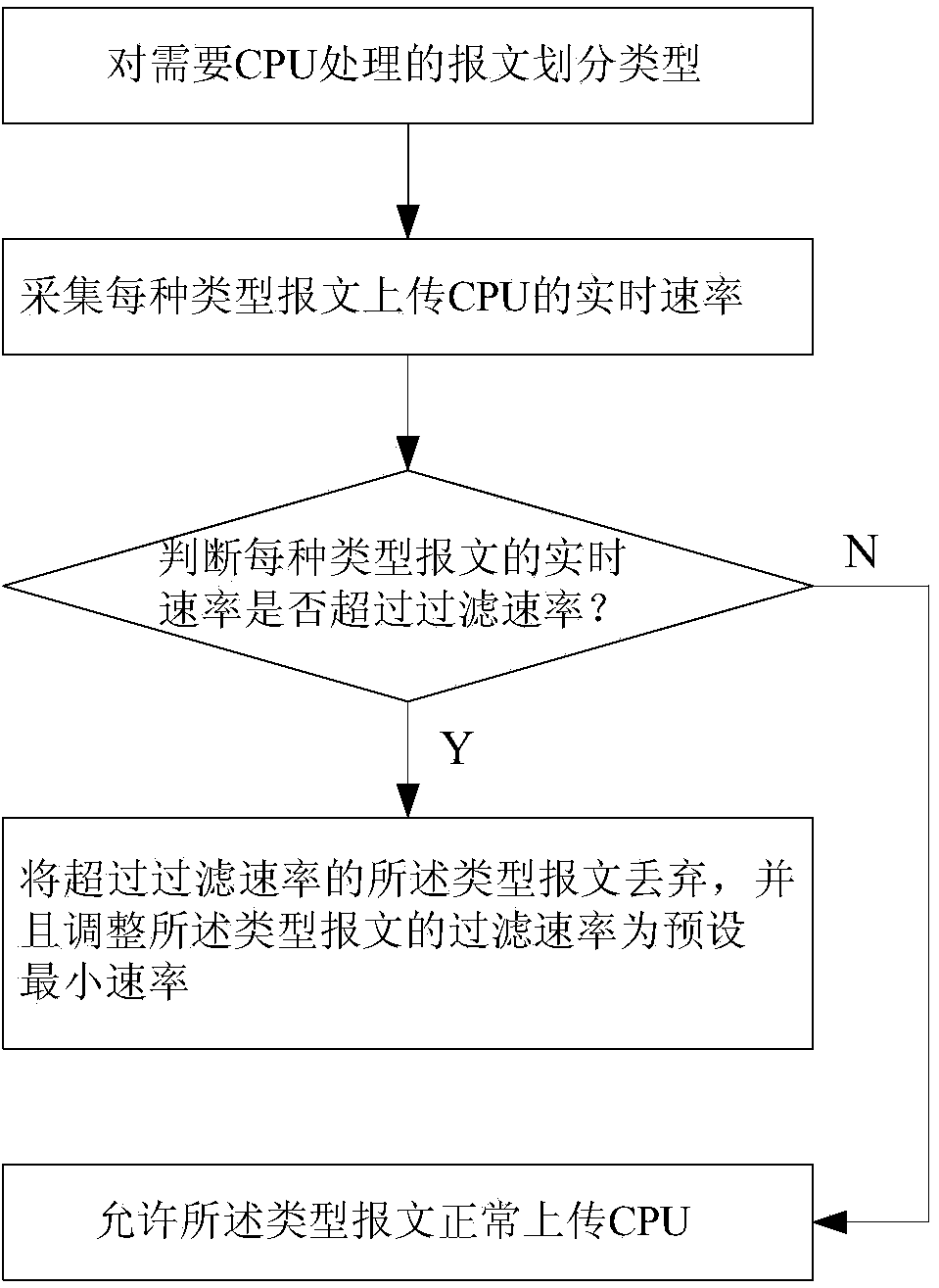
[0052] This embodiment provides a method for identifying large traffic attacks for protecting the CPU, such as figure 1 As shown, the large flow attack identification method for protecting the CPU includes:
[0053] Packets that need to be processed by the CPU are classified into types, and the typed packets are called typed packets. Further, the basis for classifying the message type includes the protocol type of the message, the port number through which the message is input to the CPU, or / and the VLAN number of the message. The definition basis of the message type comes from the message that the CPU needs to process. The invention defines its type for the message that needs to be processed by the CPU, and stipulates the rate at which the CPU allows receiving and processing; for messages that do not need to be clearly classified, the present invention can unify Defined as "other" type, such as the following definition:
[0054]
[0055] The scope of protection of the pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com