Unknown virus retrieval method
A technology of unknown virus and behavior, applied in special data processing applications, instruments, electronic digital data processing, etc., can solve the problems of inability to adjust the virus database, easy false positives, increased time for virus detection and anti-virus, etc., to improve the efficiency of virus detection , reduce the effect of unnecessary analysis process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
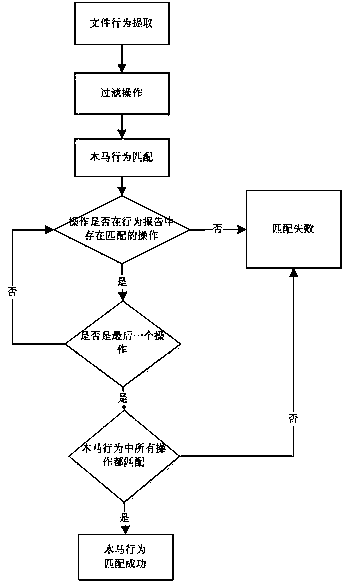
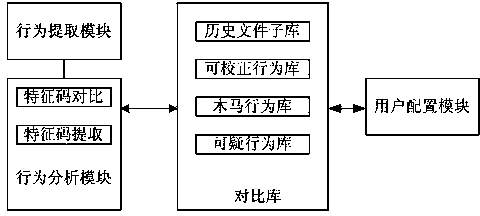
[0033] (1) Read the basic behavior report of the file extracted by the behavior extraction module, and filter out the behavior operations that do not need to be analyzed according to the filtering operation configuration;
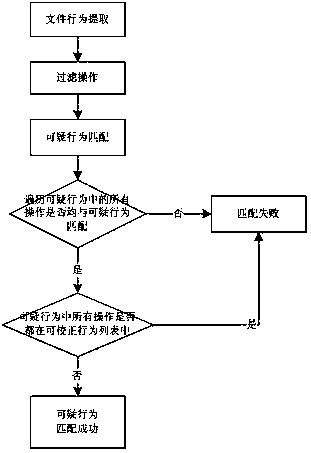
[0034] (2) Read a suspicious behavior configuration from the suspicious behavior list in the comparison library, and find all operations of the suspicious behavior from the file basic behavior operation report, if all operations of the suspicious behavior can be found in the suspicious behavior configuration in the comparison library If it is found in the relevant operation behavior of the suspicious behavior, go to step (3). If one of the basic operational behaviors of the suspicious behavior cannot be found, the matching of the suspicious behavior will fail.
[0035] (3) After the suspicious behavior is successfully matched, continue to match the correctable behavior for the behavior, and judge whether all the operation behaviors in the suspicious operatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com