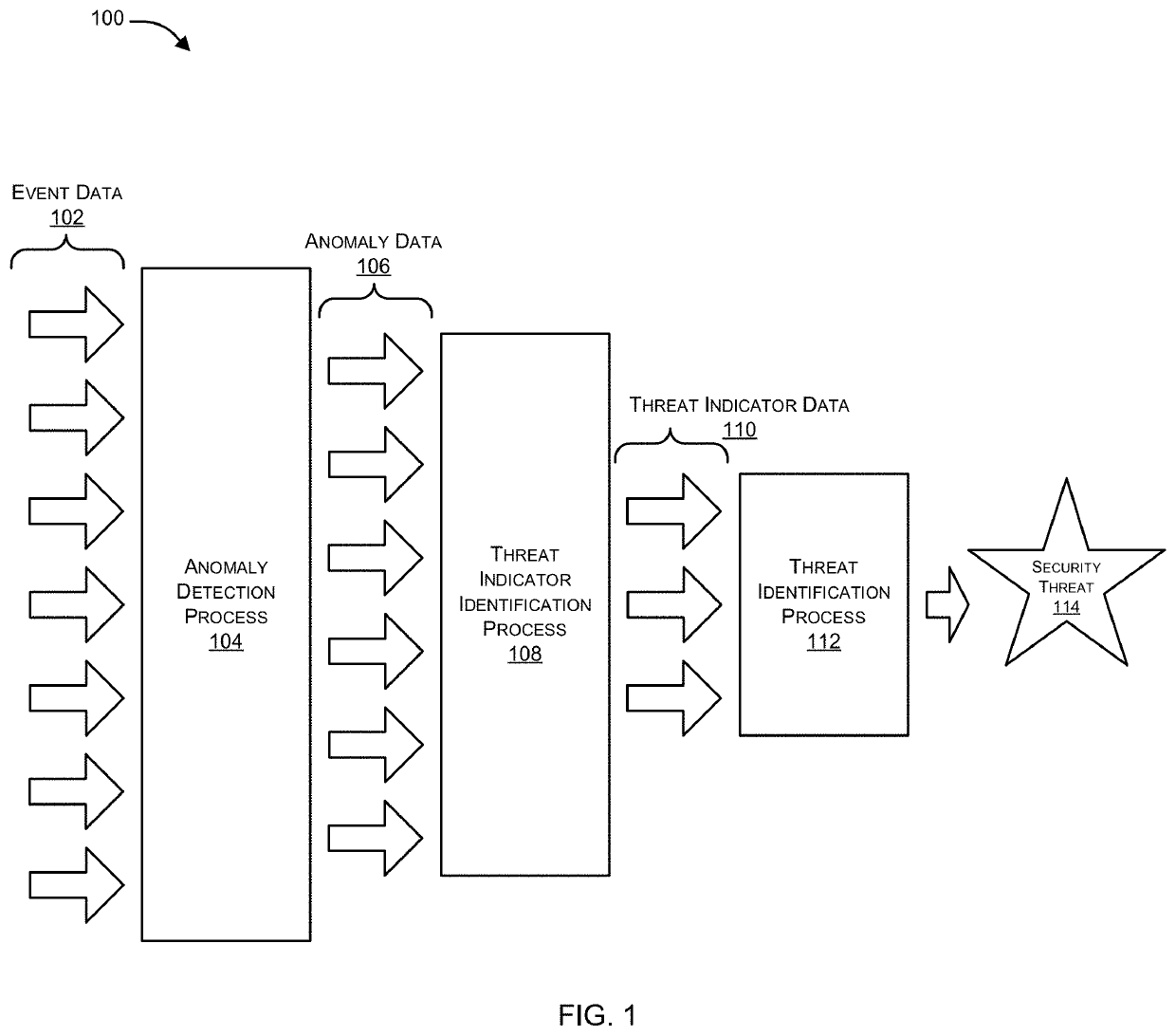
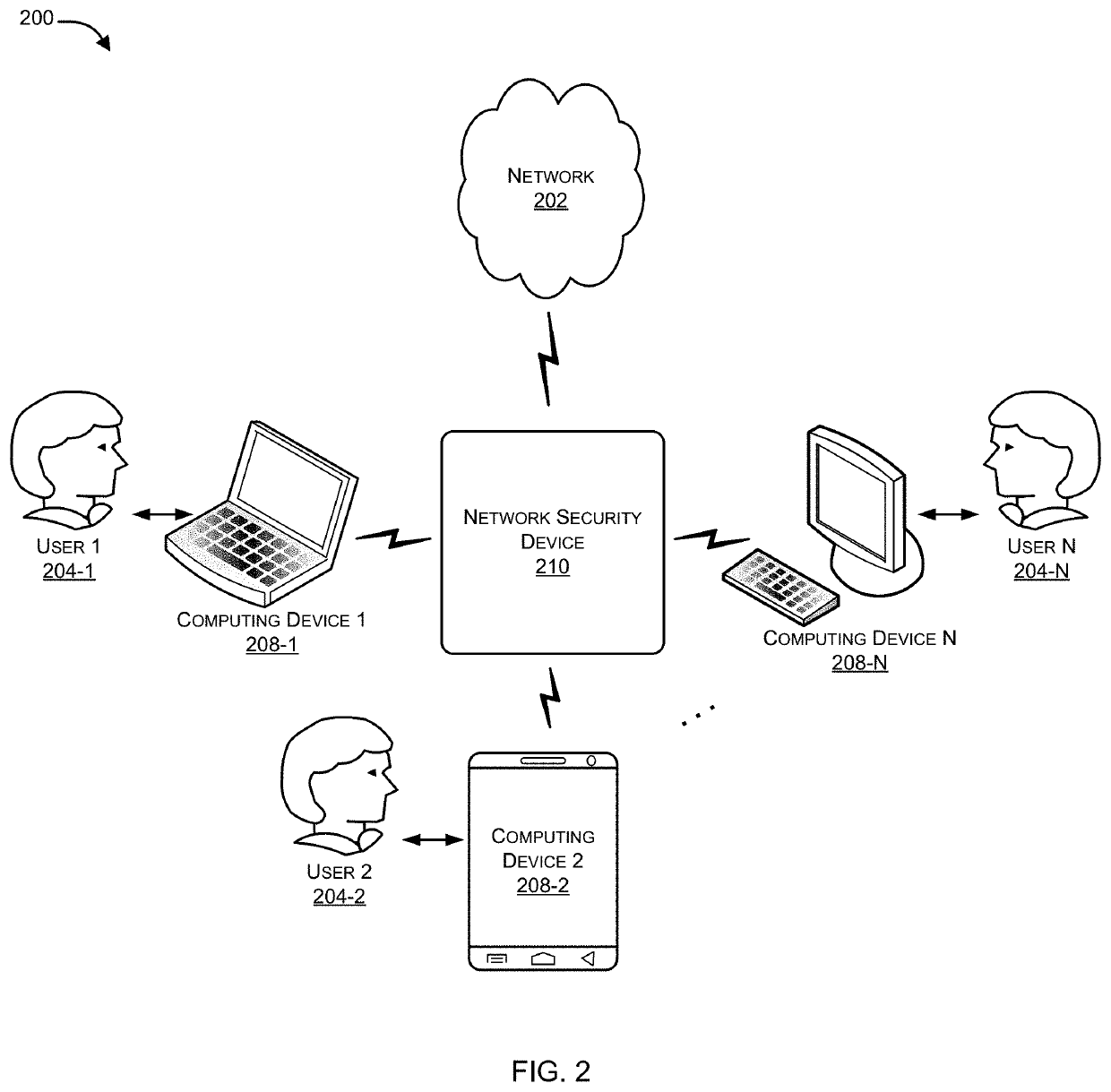
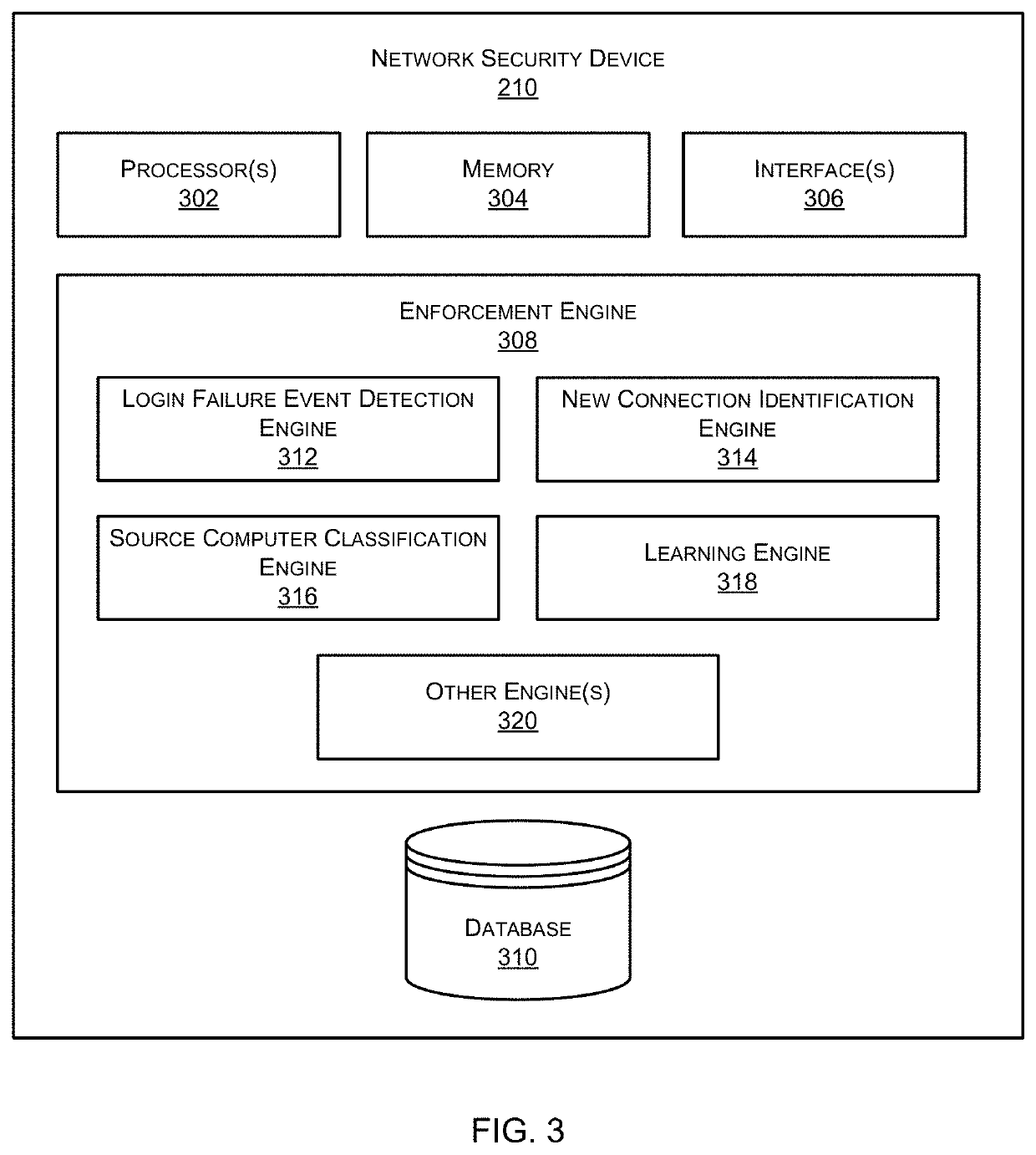
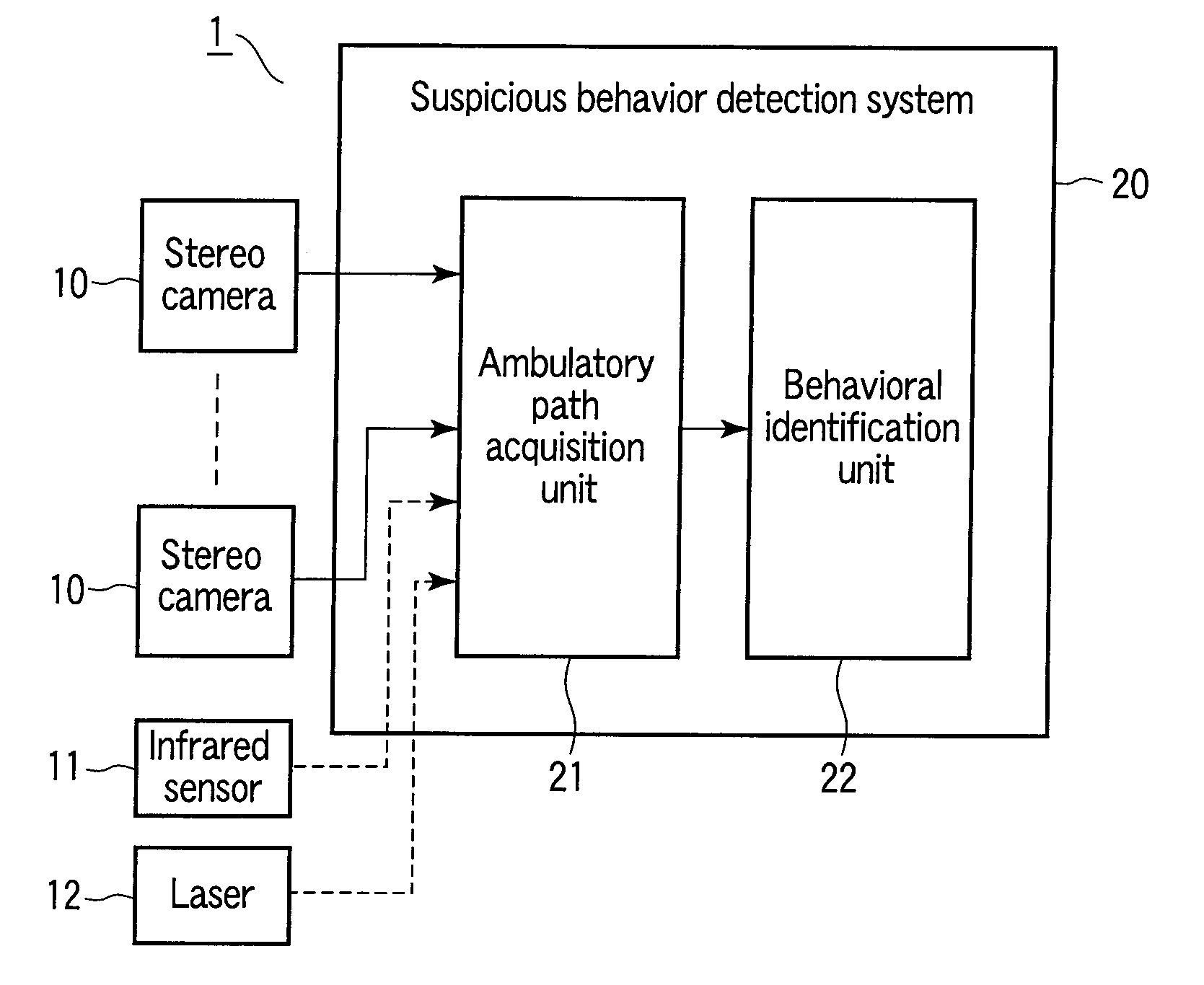
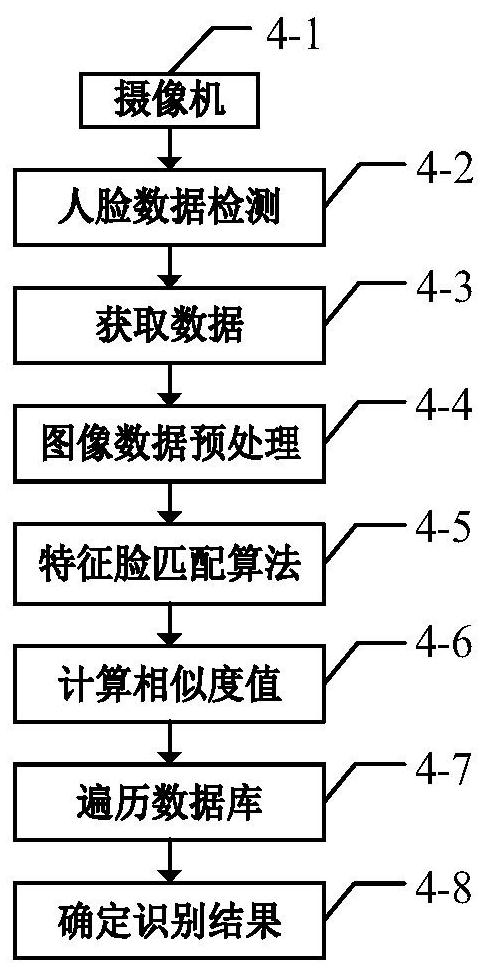
Patents
Literature
62 results about "Suspicious behaviour" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
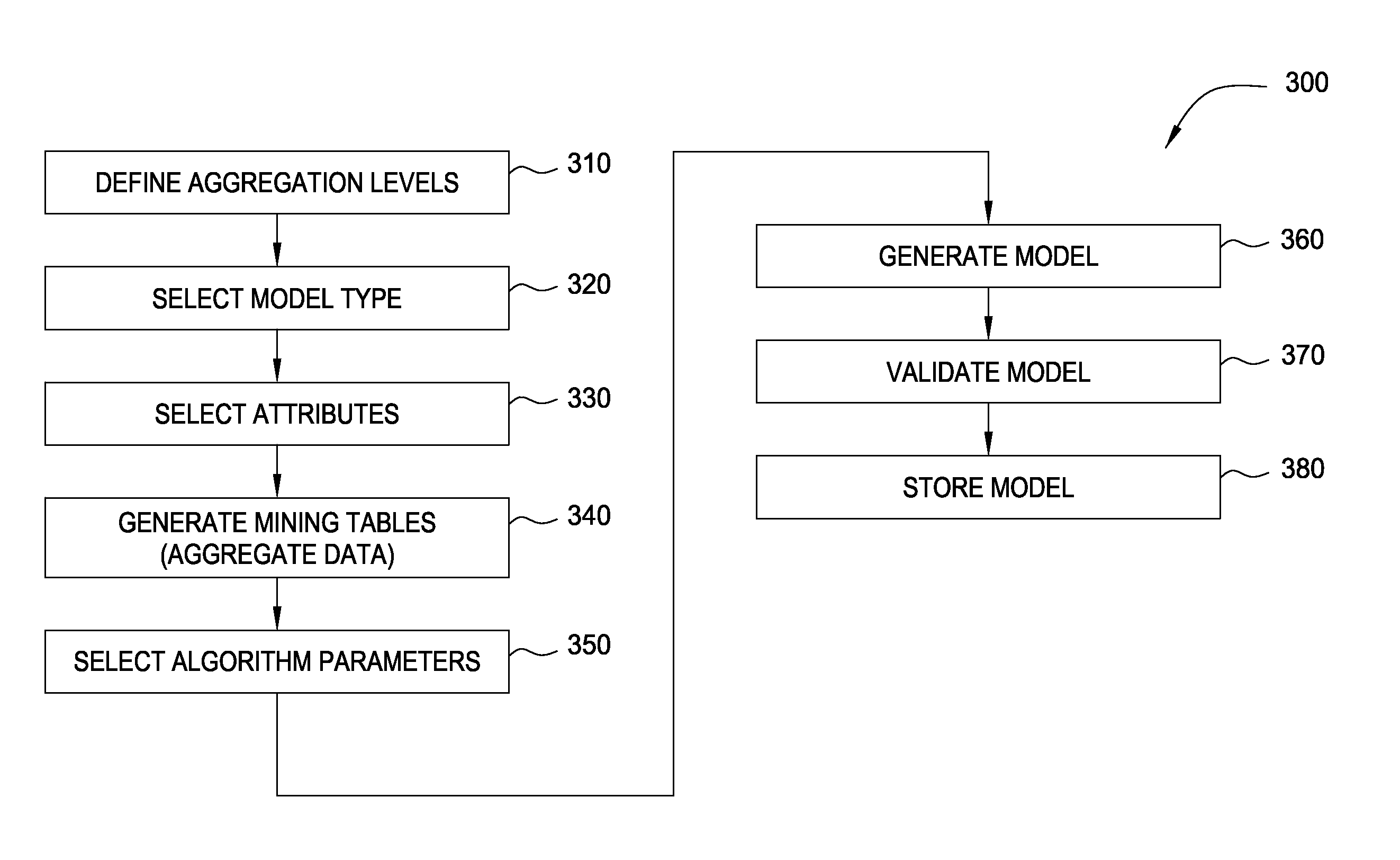
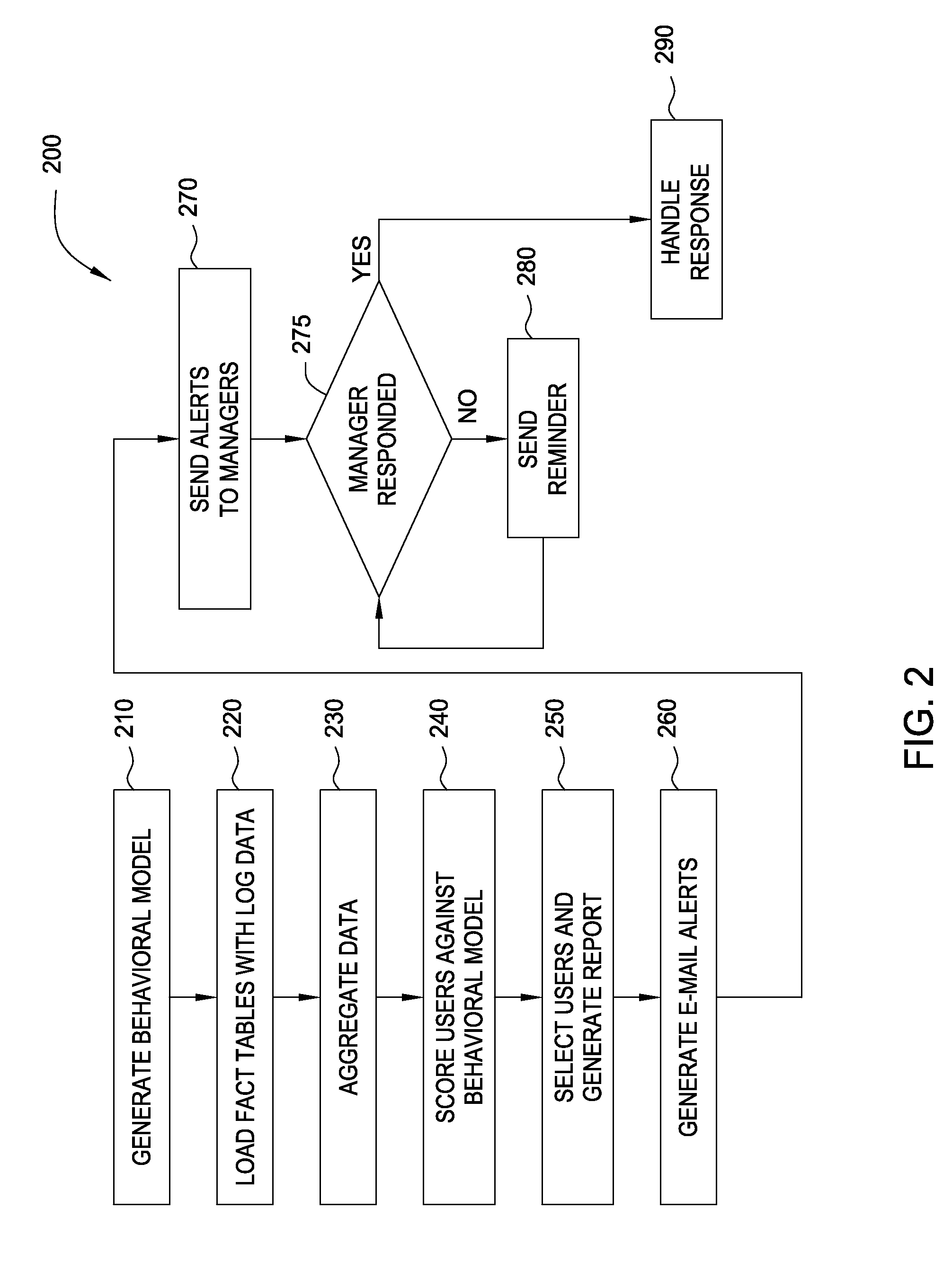
Modeling user access to computer resources
Embodiments of the invention provide a method for detecting changes in behavior of authorized users of computer resources and reporting the detected changes to the relevant individuals. The method includes evaluating actions performed by each user against user behavioral models and business rules. As a result of the analysis, a subset of users may be identified and reported as having unusual or suspicious behavior. In response, the management may provide feedback indicating that the user behavior is due to the normal expected business needs or that the behavior warrants further review. The management feedback is available for use by machine learning algorithms to improve the analysis of user actions over time. Consequently, investigation of user actions regarding computer resources is facilitated and data loss is prevented more efficiently relative to the prior art approaches with only minimal disruption to the ongoing business processes.
Owner:DAEDALUS BLUE LLC
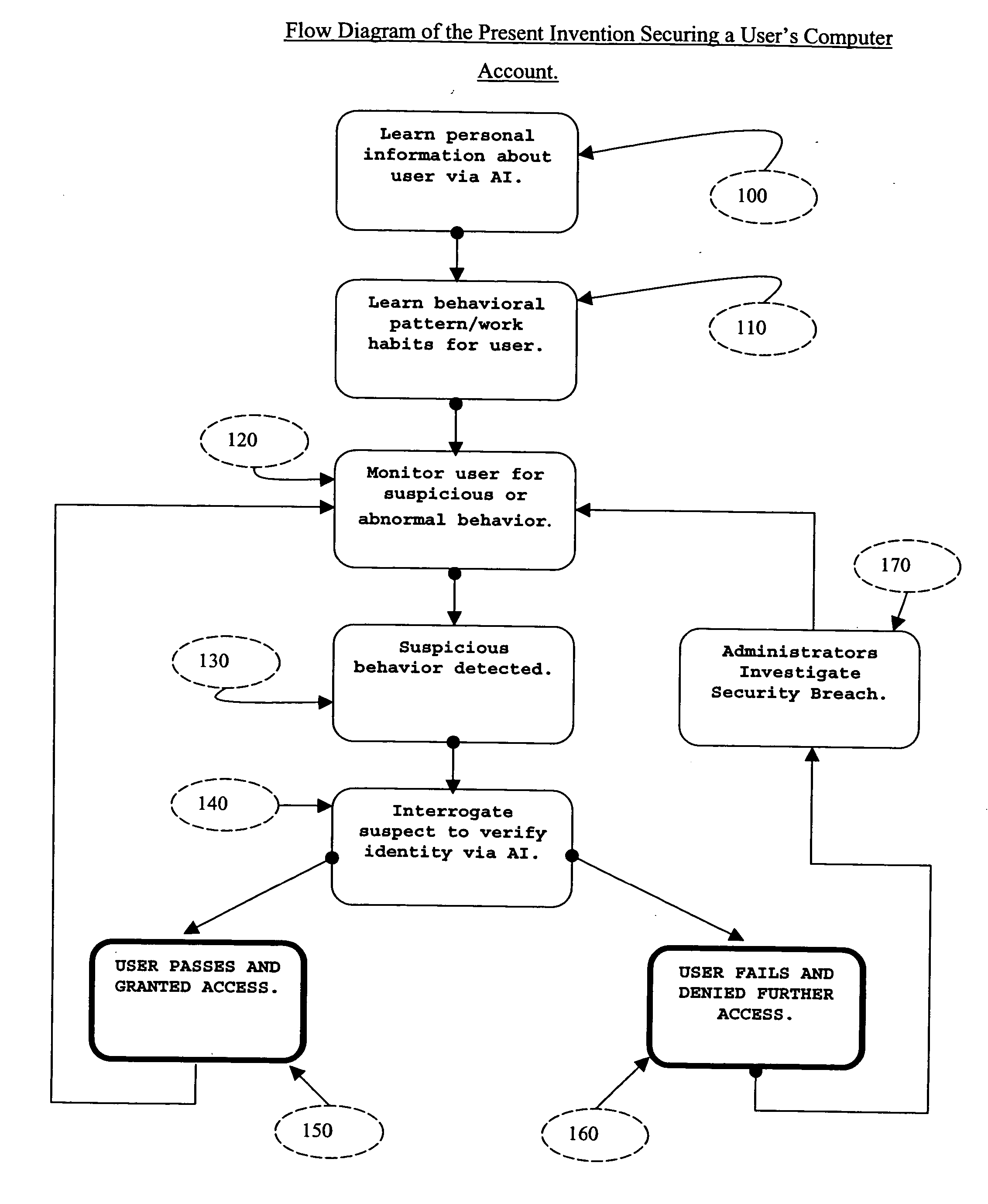
System and method for securing computer system against unauthorized access
ActiveUS20050097364A1Defeat computer security breachSecurity breachMemory loss protectionDigital data processing detailsComputer usersIdentity theft
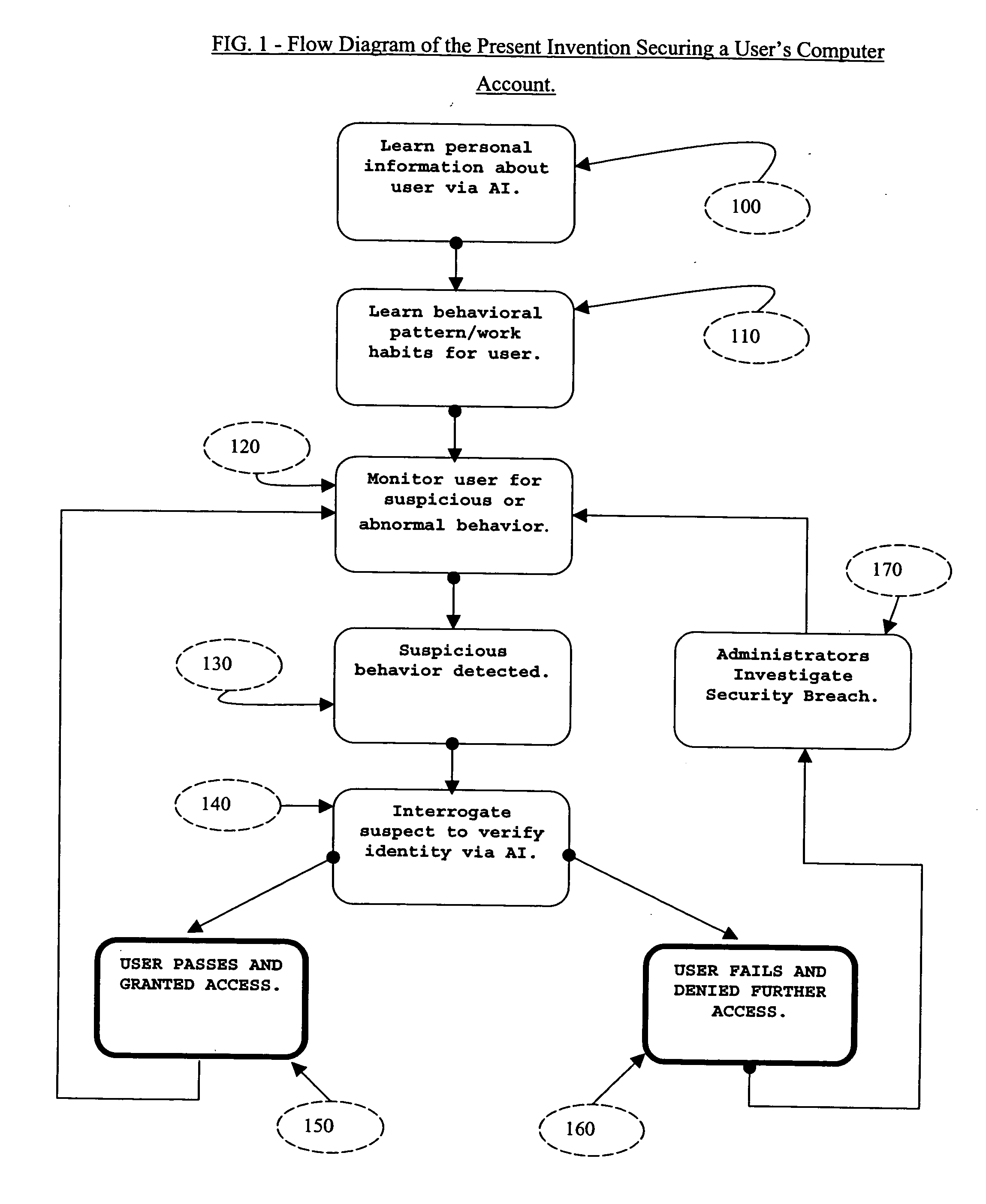
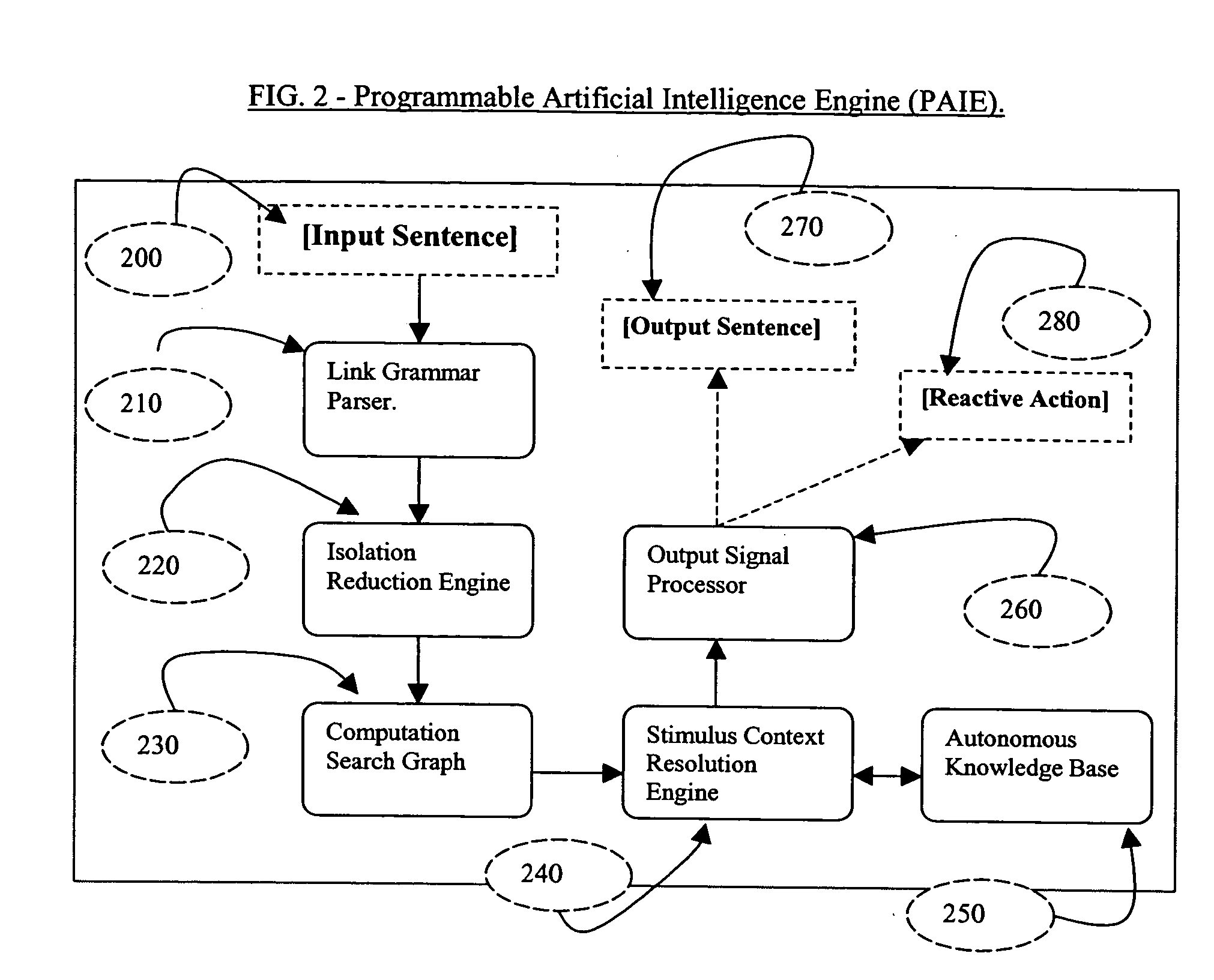
The present invention described secures a computer account against unauthorized access caused as a result of identity-theft, and insider-espionage using artificial intelligence and behavioral modeling methods. The present invention has the ability to detect intruders or impersonators by observing “suspicious” activity under a computer account. When it sees such suspicious behavior, it uses artificial intelligence to authenticate the suspect by interrogation. The present invention asks the suspect questions that only the legitimate computer account owner can verify correctly. If the suspect fails the interrogation, that proves that he / she is an impersonator and therefore further access to the computer account is denied immediately. On the other hand if the suspect passes, access to the computer account is restored. The present invention uses a Programmable Artificial Intelligence Engine (PAIE) to interact with computer users in human natural language. The PAIE can also be programmed to suit other applications where natural language interaction with humans is helpful.
Owner:EDEKI OMON AYODELE +2
Dynamic virus detection method and device for equipment based on Android system
ActiveCN103559446AEffective assessmentPlatform integrity maintainanceSpecific program execution arrangementsSoftware engineeringSuspicious behaviour
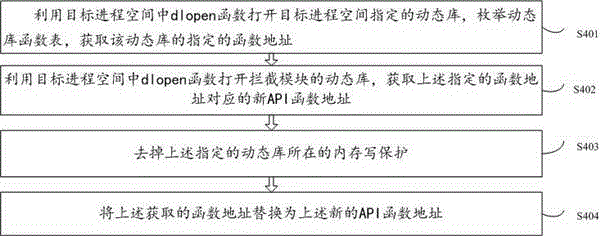
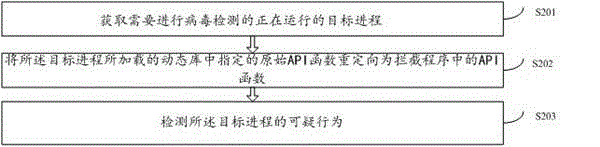
The invention relates to the field of information safety, and provides a dynamic virus detection method for equipment based on the Android system. The method comprises the following steps: the on-going target process required to be subjected to virus detection is acquired; a primitive API (Application Program Interface) function which is assigned in a dynamic library loaded through the target process is redirected into the API function in the interception program; the suspicious act of the target process is detected. According to the invention, interception and troubleshooting are performed in the Android underlying library, so that more underlying suspicious acts of the application program can be evaluated more effectively, and the detection method is a convenient and efficient virus detection method.
Owner:XIAMEN MEIYA PICO INFORMATION
Cloud server, application program verification, certification and management system and application program verification, certification and management method
ActiveCN103368987ADoes not affect the life cycle management mechanismImprove experiencePlatform integrity maintainanceTransmissionSafety controlComputer compatibility
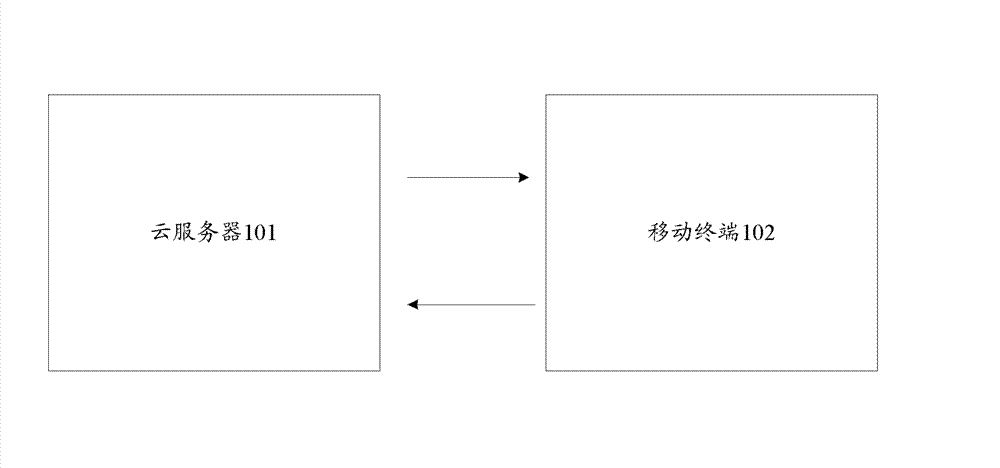
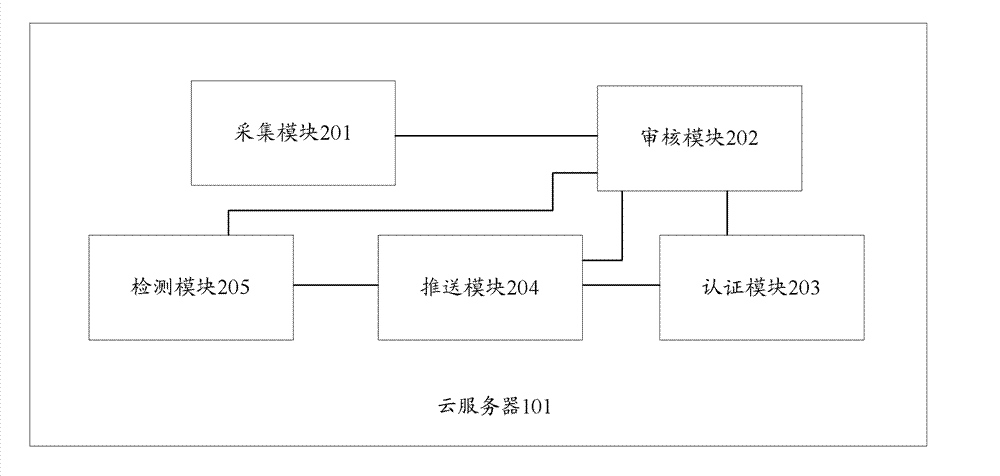
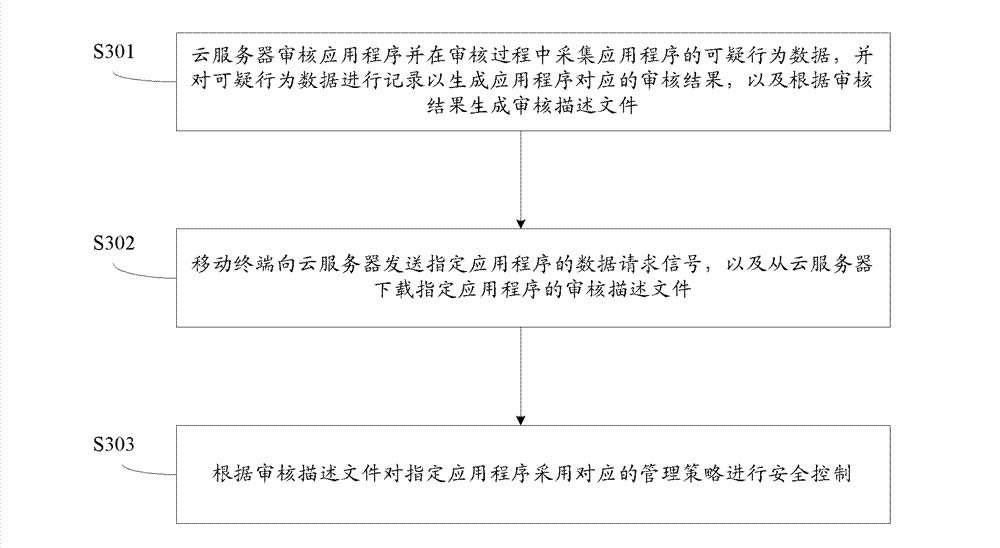
The invention provides an application program verification, certification and management system comprising a cloud server and a mobile terminal; the cloud server is used for verifying an application program, acquiring suspicious behavior data of the application program in the verification process, recording the suspicious behavior data to obtain a verification result of the application program and generating a verification description file according to the verification result, wherein the verification description file includes certification data and the verification result of the application program; and the mobile terminal is used for downloading the verification description file of a specified application program from the cloud server and using a corresponding management strategy to carry out safety control on the specified application program according to the verification description file. The system has a reasonable multi-strategy management mechanism, can bring a better real-time safety protection effect and has good compatibility. The invention further provides a cloud server and an application program verification, certification and management method.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
User identification system and method based on heterogeneous information network embedding algorithms
ActiveCN111163057AComprehensive Behavioral ModelingImprove recognition accuracyData switching networksNeural learning methodsAlgorithmInformation networks
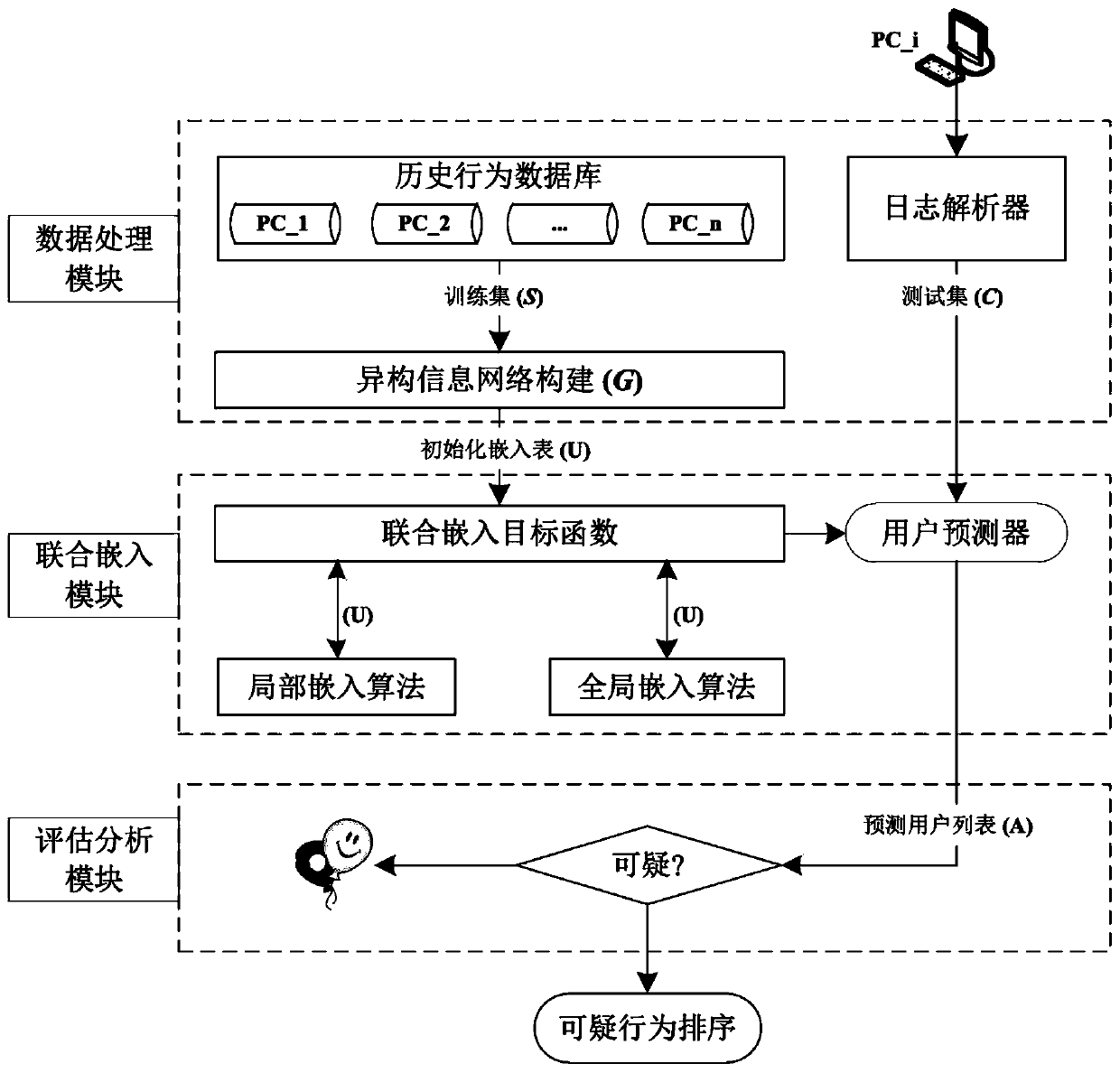
The invention relates to a user identification system and method based on heterogeneous information network embedding algorithms. The user identification system comprises a data processing module, a joint embedding module and an evaluation analysis module. According to the invention, multi-source heterogeneous user behavior data is utilized for constructing a normal behavior model based on the thought of behavior analysis, and user identification is executed by comparing the similarity between a current behavior and the normal behavior model when behavior data of a new time period arrives. Forthe condition of identification errors, suspicious behavior sorting is given based on dot product similarity operation. The system and method can be applied to an enterprise intranet to detect potential internal threats, a more comprehensive and accurate behavior model can be obtained by combining two heterogeneous information network embedding algorithms, and the user identification accuracy isimproved by about 10%. In addition, event-level traceability clues can be provided for further analysis of the safety monitoring personnel.
Owner:INST OF INFORMATION ENG CAS
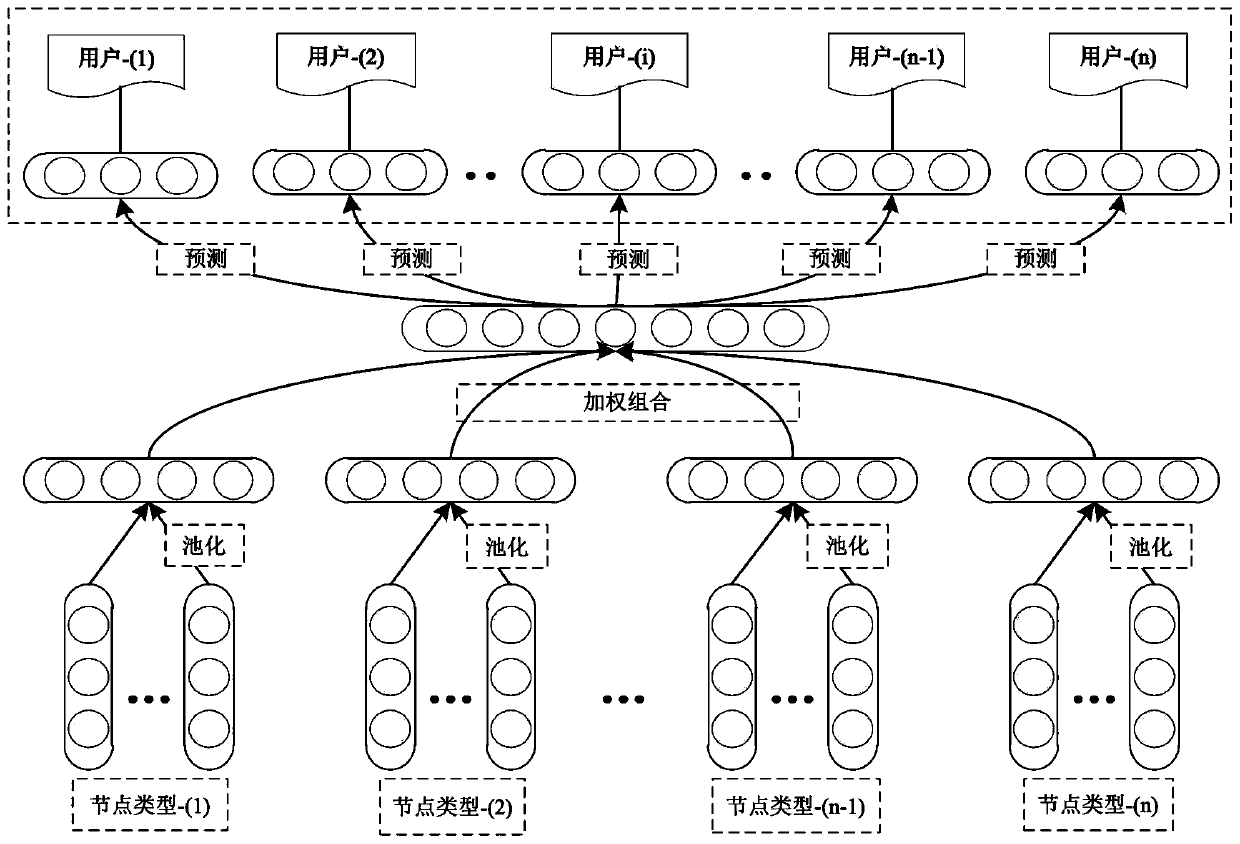
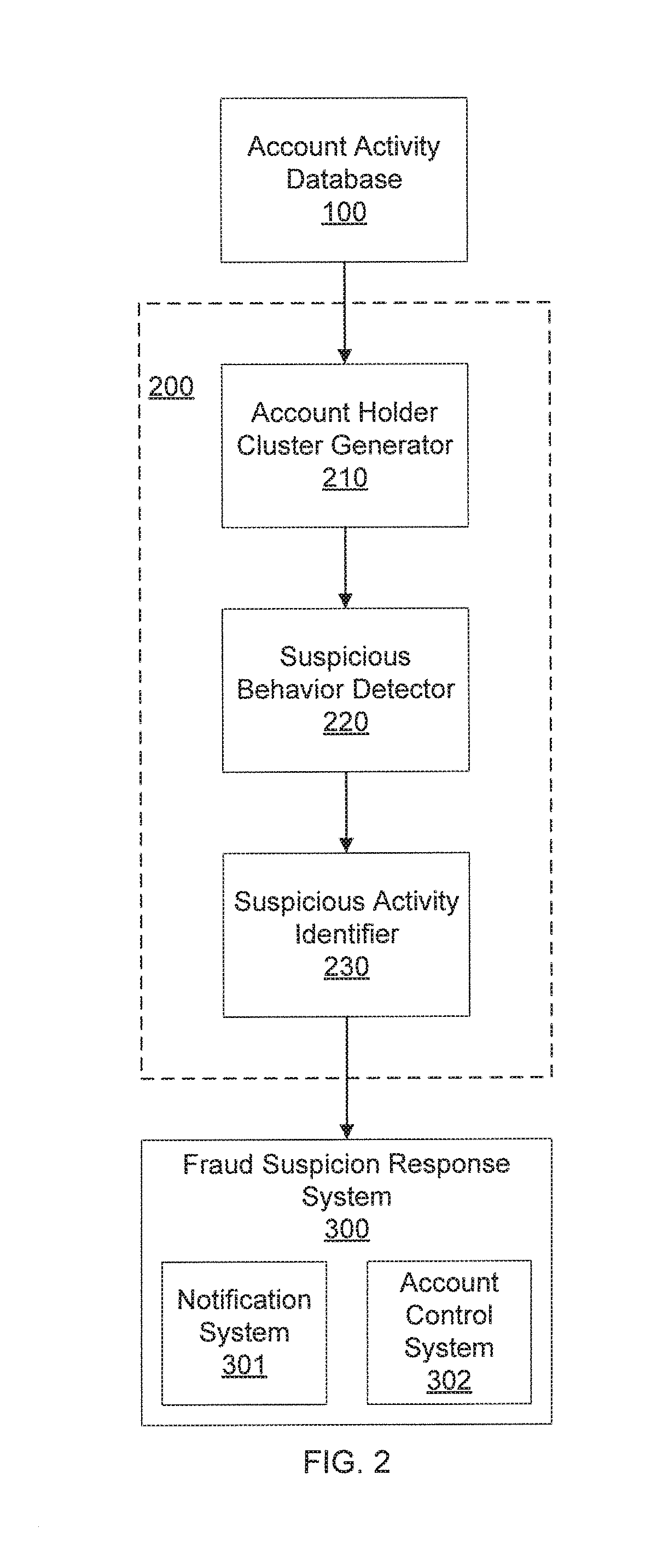
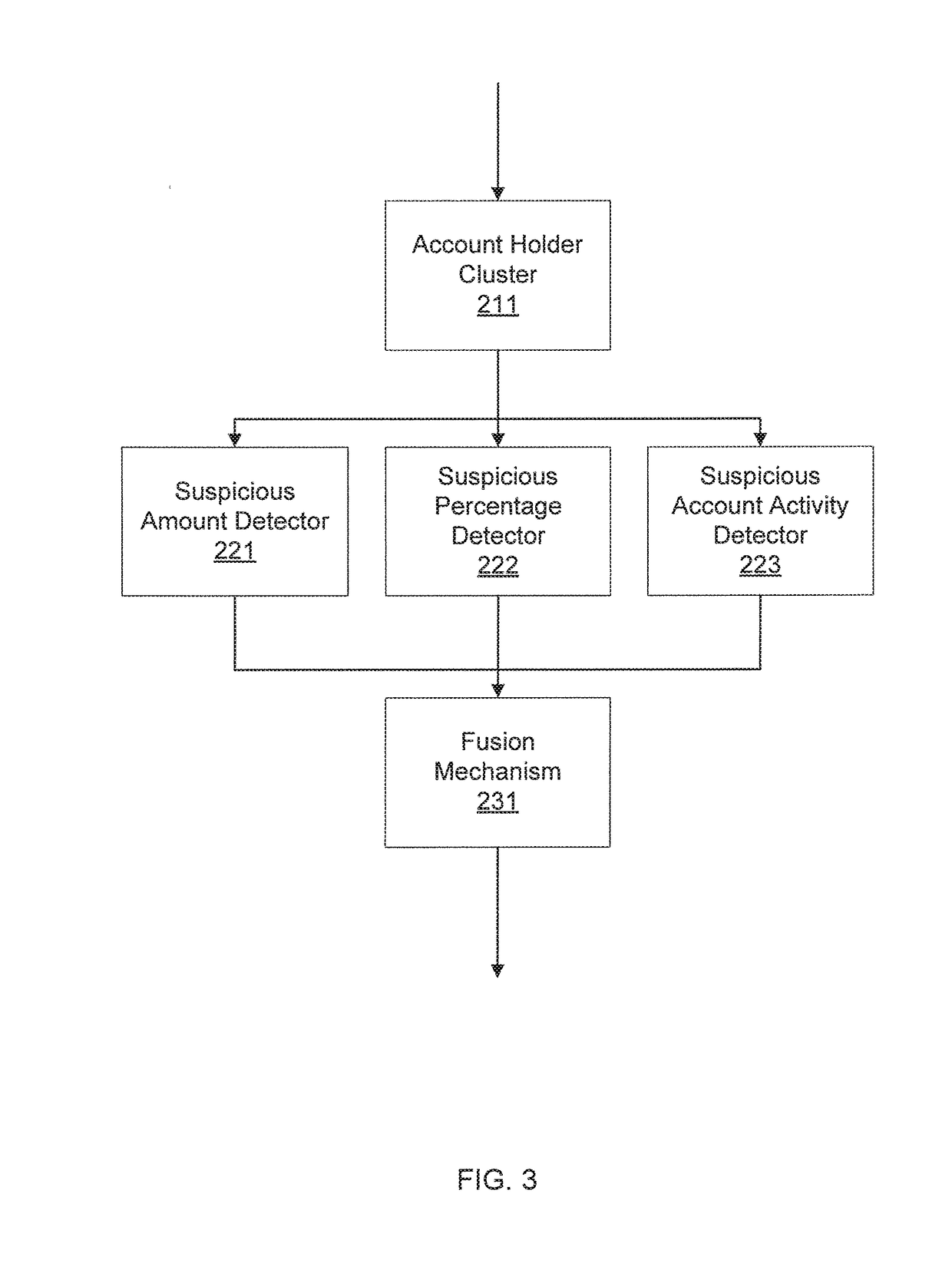
Financial fraud detection using user group behavior analysis
InactiveUS20180365696A1Reduce fraudMitigate suspicious transactionCharacter and pattern recognitionData switching networksCluster algorithmSuspicious behaviour
Systems and methods for mitigating fraud in transactions including clustering account holders into groups with a cluster generator by jointly considering account activities as features in a clustering algorithm such that account holders in each group have similar behavior according to analysis of the features in the clustering algorithm. In each group, a list of suspicious transactions is detected with a suspicious behavior detector by determining outlier transactions for a transaction type of interest relative to transactions of each account holder in a group. An alert is generated and sent to users with a fraud suspicion response system to mitigate the suspicious transactions.
Owner:NEC LAB AMERICA
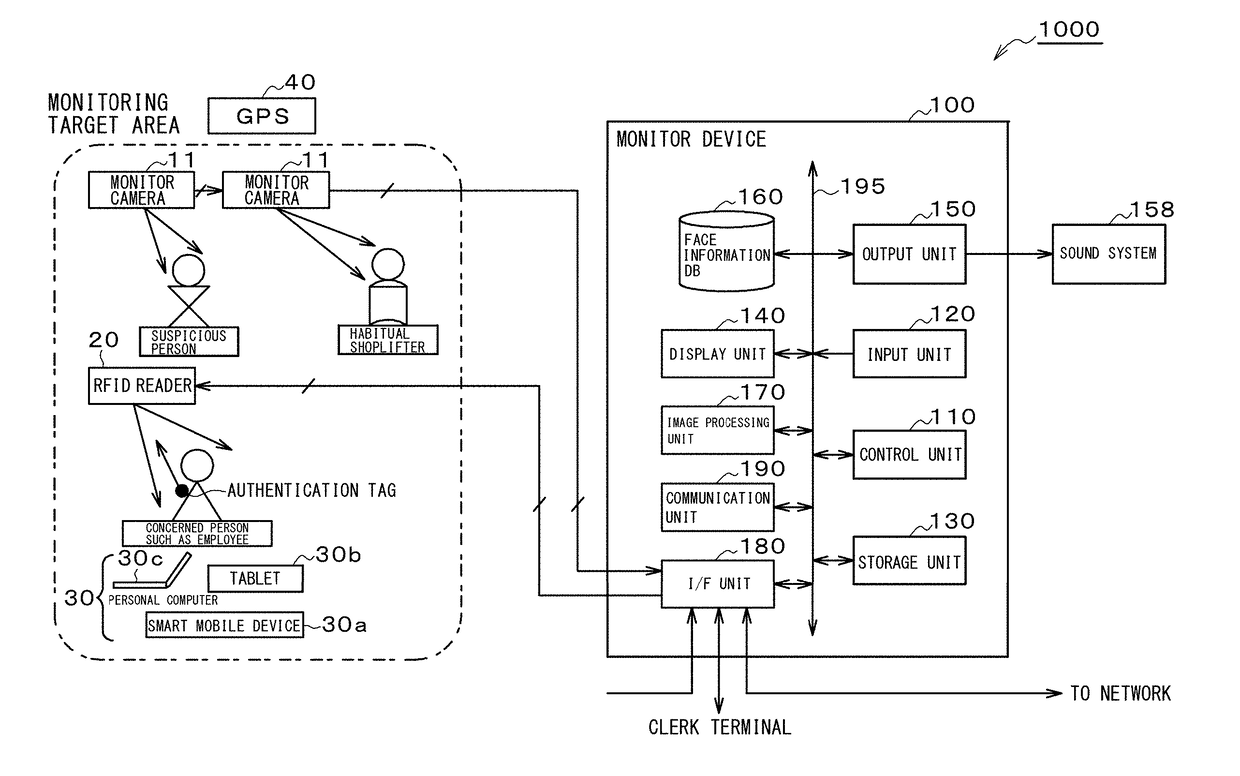
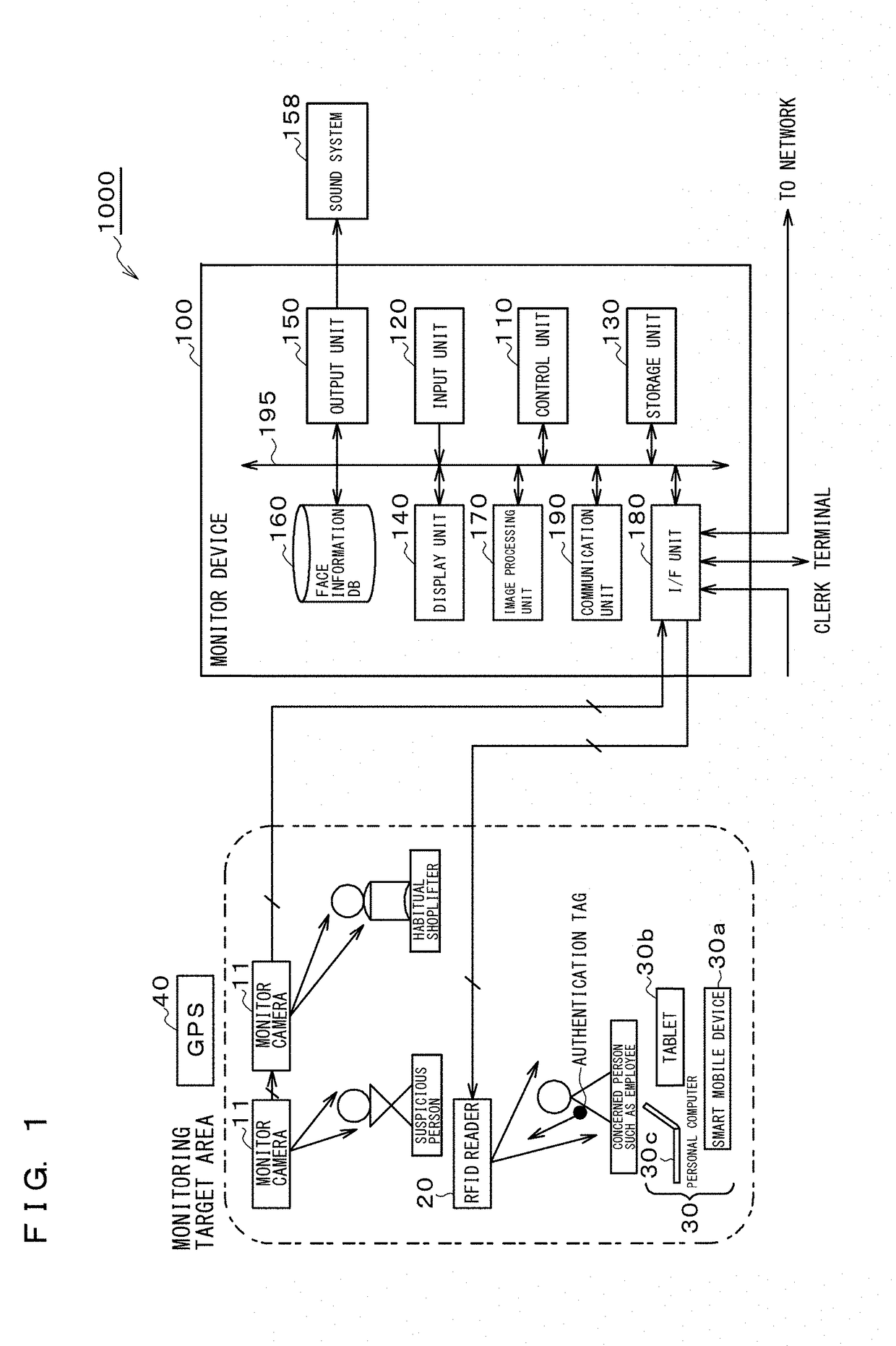
Smart-security digital system, method and program
ActiveUS20180239953A1Simple configurationCharacter and pattern recognitionClosed circuit television systemsImaging processingTerminal equipment
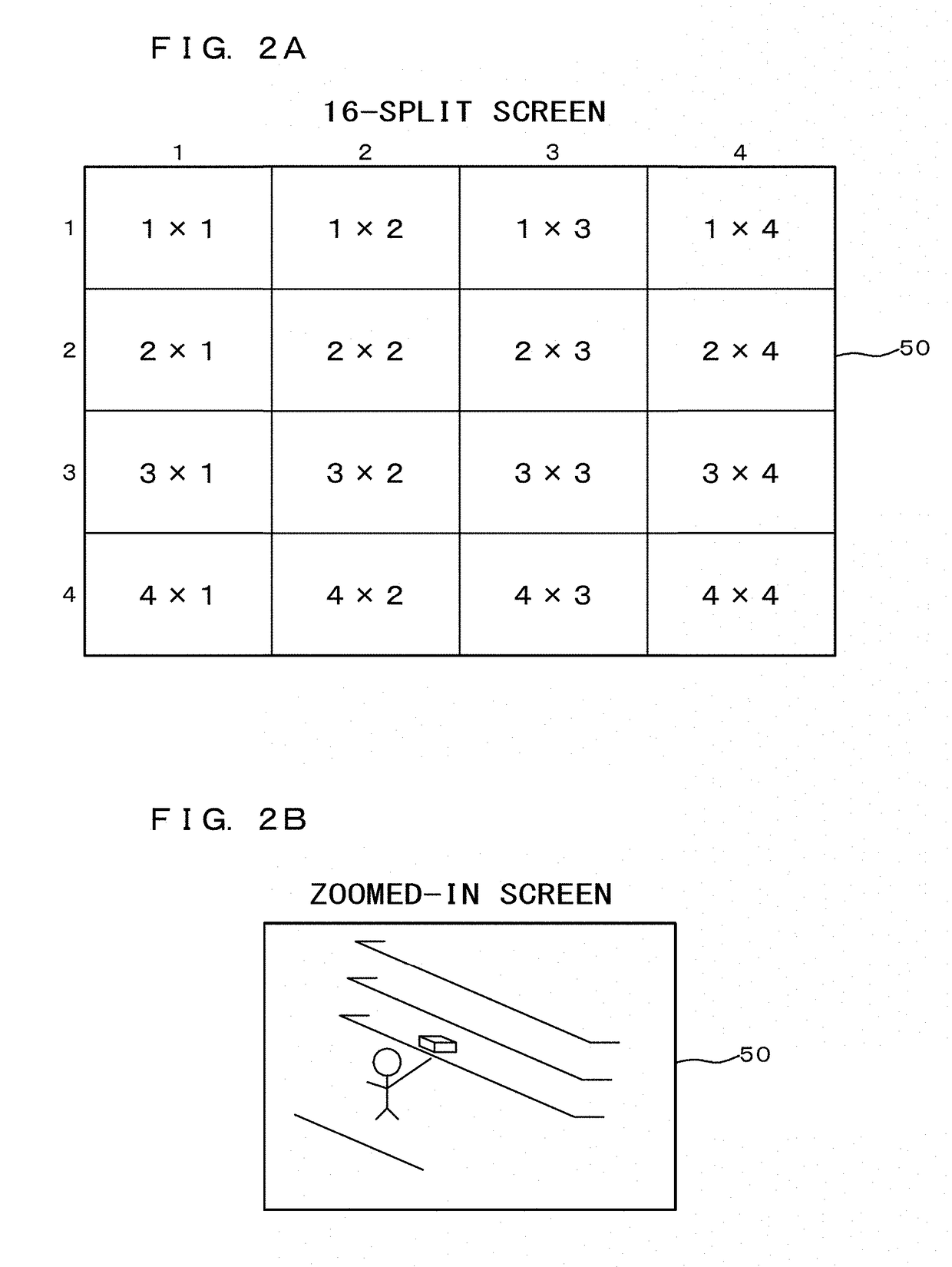
Provided is a smart-security digital system that enables, when there is a habitual shoplifter or suspicious behavior person, an employee or the like close to the habitual shoplifter or suspicious behavior person to quickly rush to the scene and prevent an act of shoplifting. The smart-security digital system (1000) comprises a face authentication function unit (111) that collates with facial images of habitual shoplifters or suspicious behavior persons accumulated in a face information DB (160), a control unit (110) that determines, when a result of collation by the face authentication function unit (111) is a match, a position of a mobile terminal device (30) closest to the habitual shoplifter or suspicious behavior person the collation result with whom is a match based on positional information acquired from a position determination unit (113), and transmits information on the habitual shoplifter or suspicious behavior person to the mobile terminal device (30), and an image processing unit (170) that synthesizes videos shot by monitor cameras (11) into a display screen consisting of a plurality of split screens, and performs a zoom-in processing to zoom in one of the split screens.
Owner:TECHNOMIRAI
Scheme for mining abnormal behaviour of industrial internet
InactiveCN106230772AImprove robustnessCalculation speedTransmissionIncremental learning algorithmClassification methods
According to data behaviour characteristics in an industrial control network in a mobile internet environment, the invention provides an improved hybrid multi-classification naive Bayesian algorithm and a mass data incremental learning algorithm based on two-step screening, and is applied to abnormal behaviour mining and analysis of a mobile industrial control system. An abnormal behaviour mining scheme is formed by abnormal behaviour classification and mining algorithm design: a suspicious behaviour classification method and a data mining process are included, and in the industrial control network in the mobile internet environment, behaviour data mining is divided into two stages including a classifier learning stage and a network behaviour monitoring stage; and, after all kinds of behaviour classifiers are obtained, malicious software behaviour data mining enters the second stage, namely the network behaviour monitoring stage. On the premise that classification categories are independent, the naive Bayesian classification algorithm has the characteristics of high calculation speed and classification accuracy, good robustness and the like, and are widely applied.
Owner:STATE GRID QINGHAI ELECTRIC POWER +1
System for Testing Computer Application
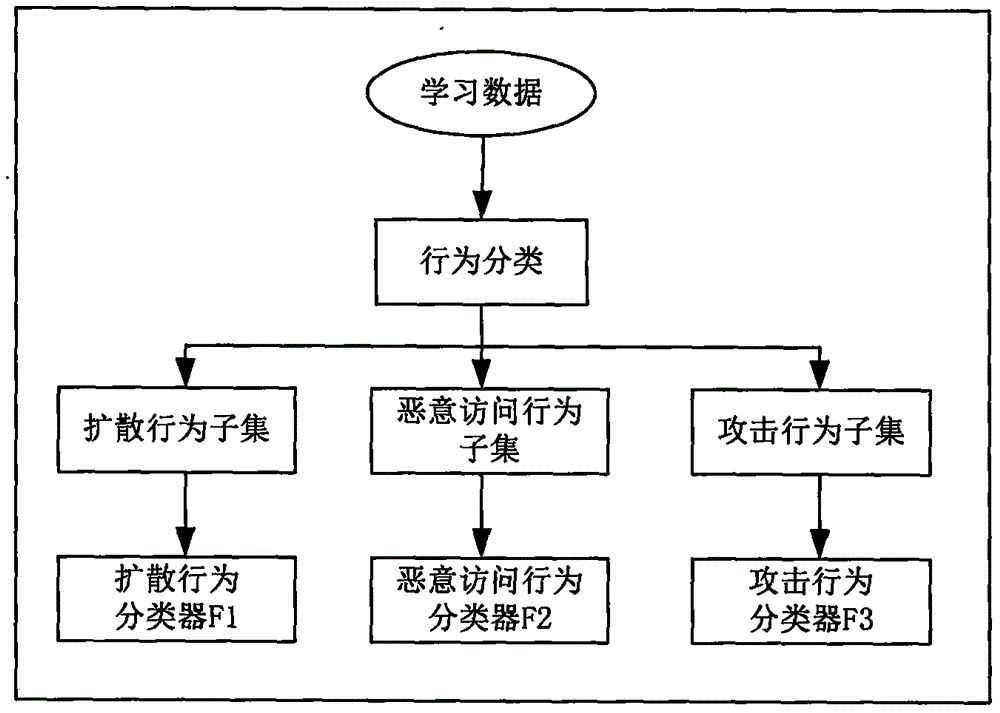
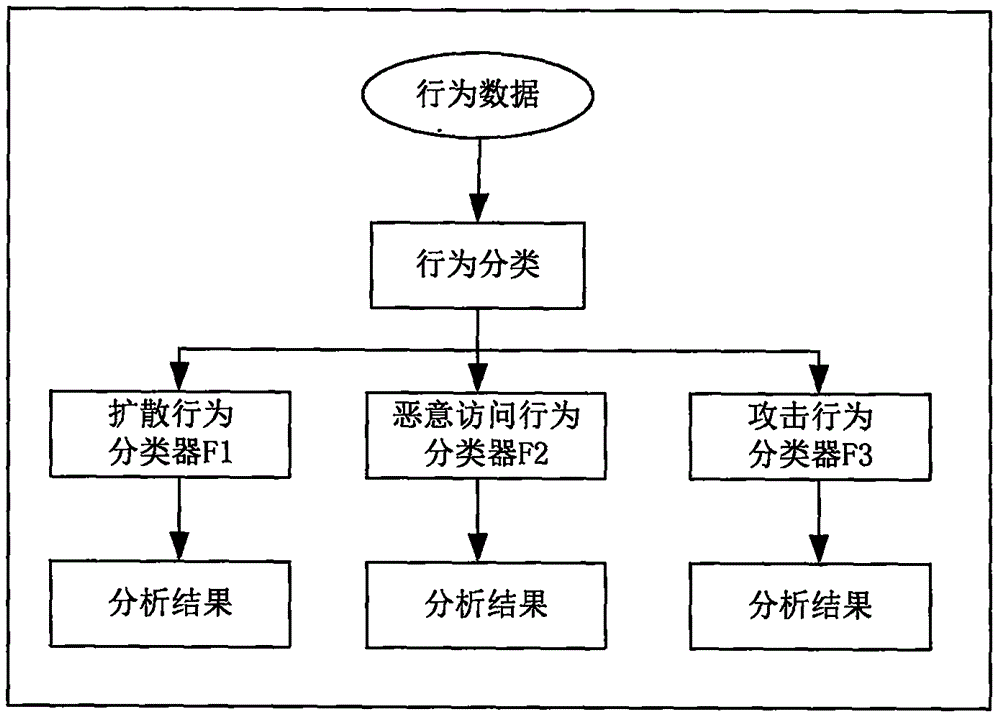
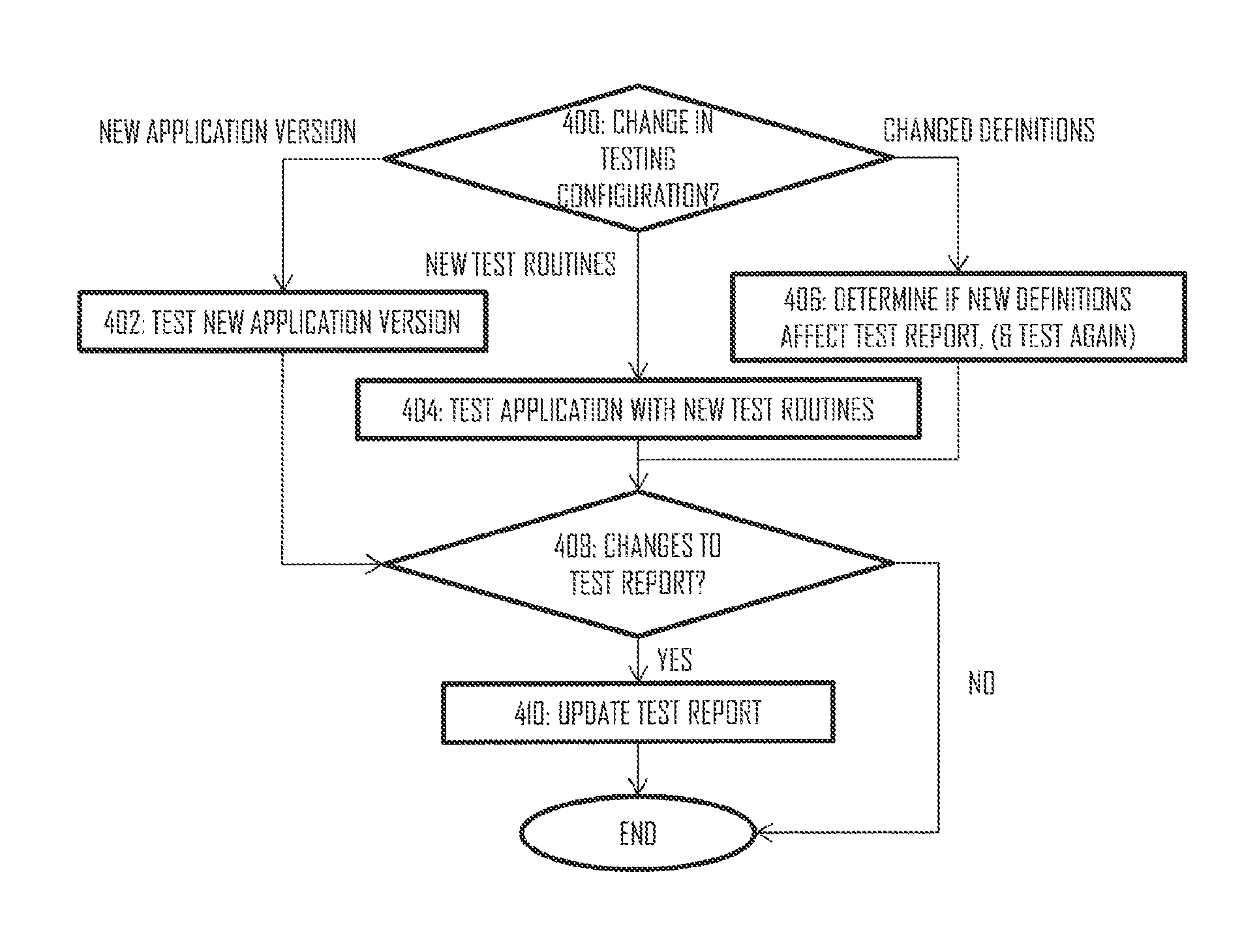
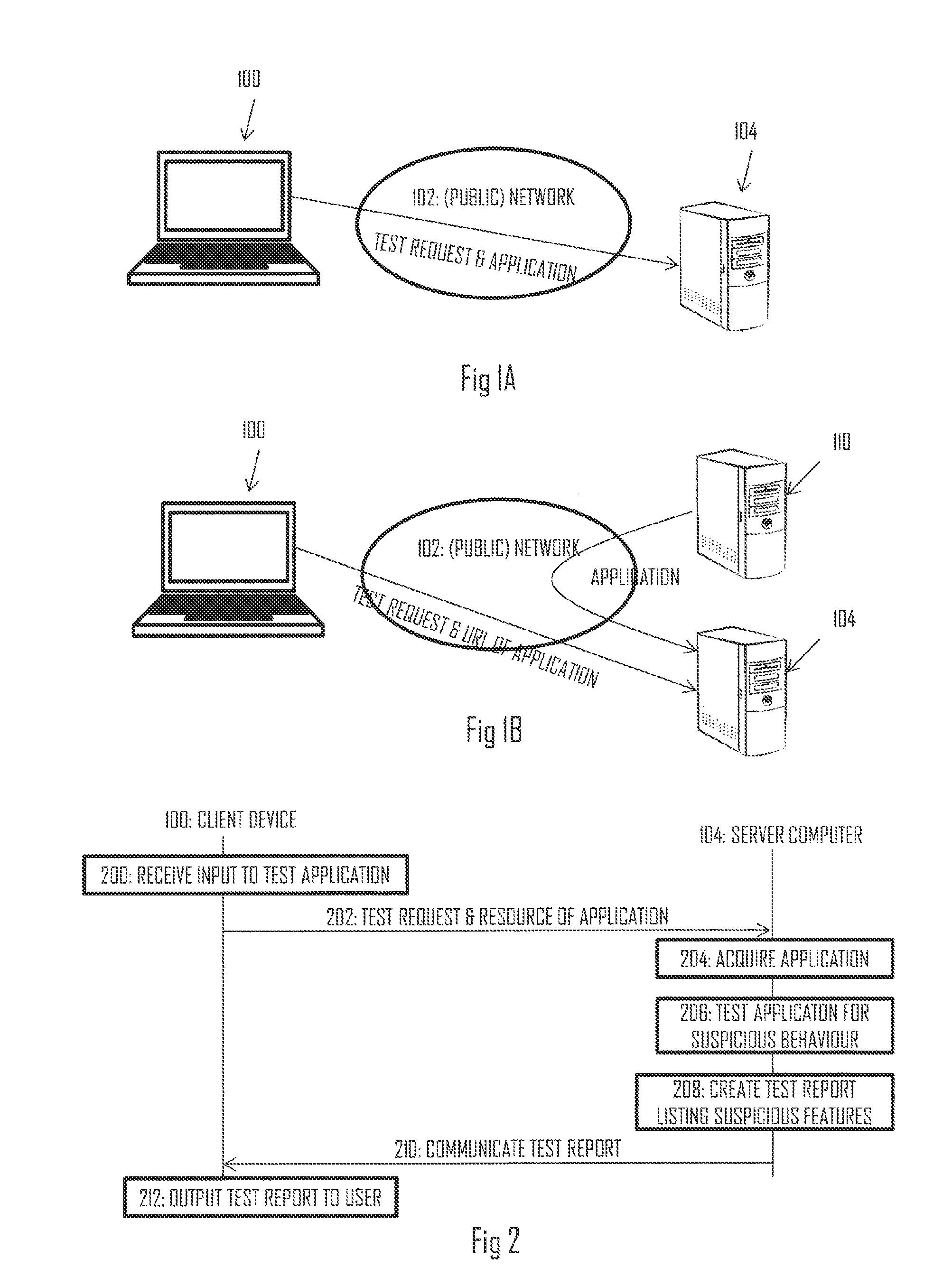
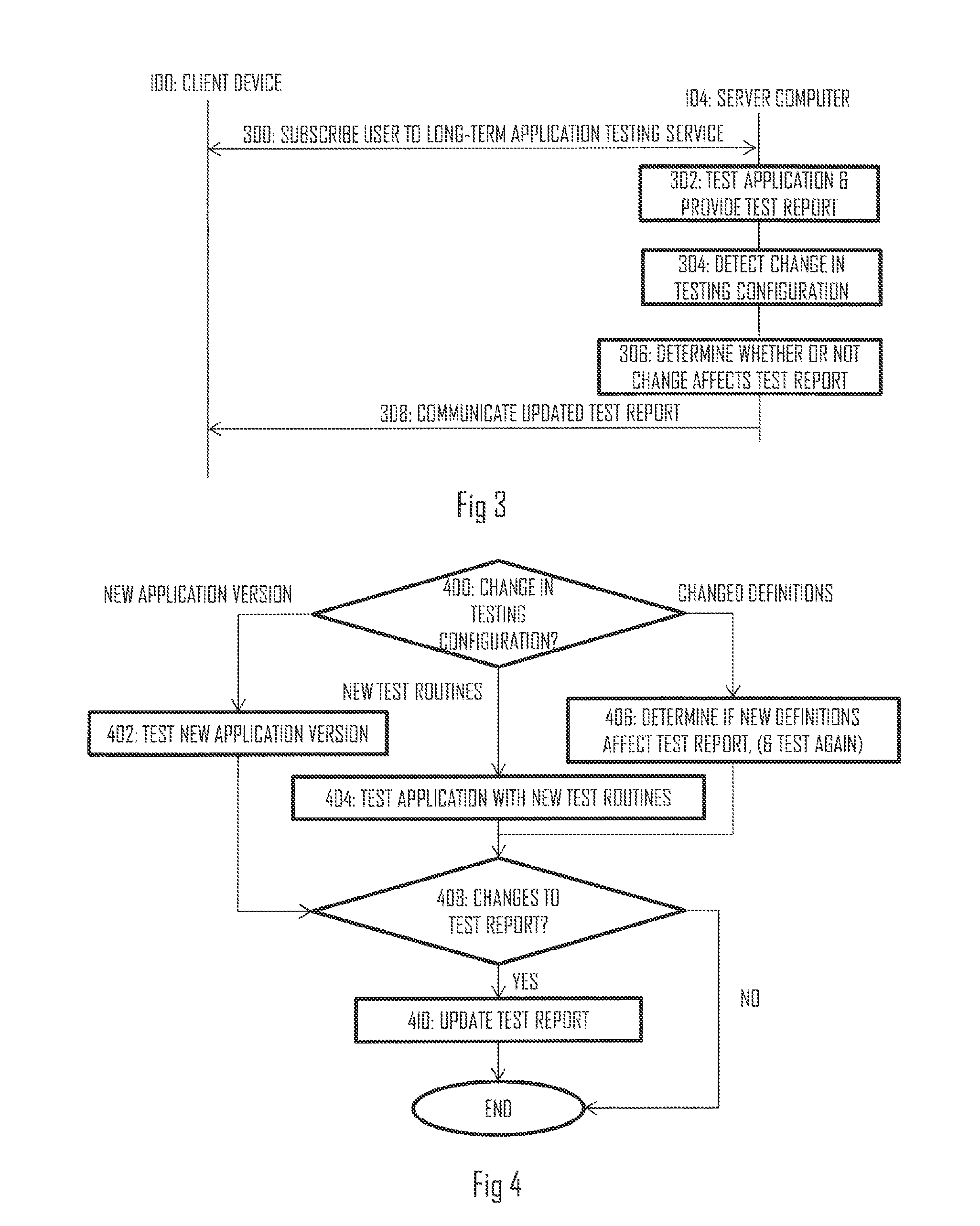
ActiveUS20140215620A1Memory loss protectionError detection/correctionSuspicious behaviourPaper document
This document discloses a method, apparatus, and computer program product for testing a computer program application in a server computer. The method comprises: receiving, from a client device, a test request requesting the server computer to test suspicious behaviour associated with the computer program application; acquiring the computer program application on the basis of the test request; applying at least one test routine to the computer program application and testing for suspicious behaviour associated with the computer program application; creating a test report specifying at least some features of the suspicious behaviour, if any found during the at least one test routine; and communicating the test report to the client device.
Owner:SYNOPSYS INC
Identifying Fraudulent and Malicious Websites, Domain and Sub-domain Names
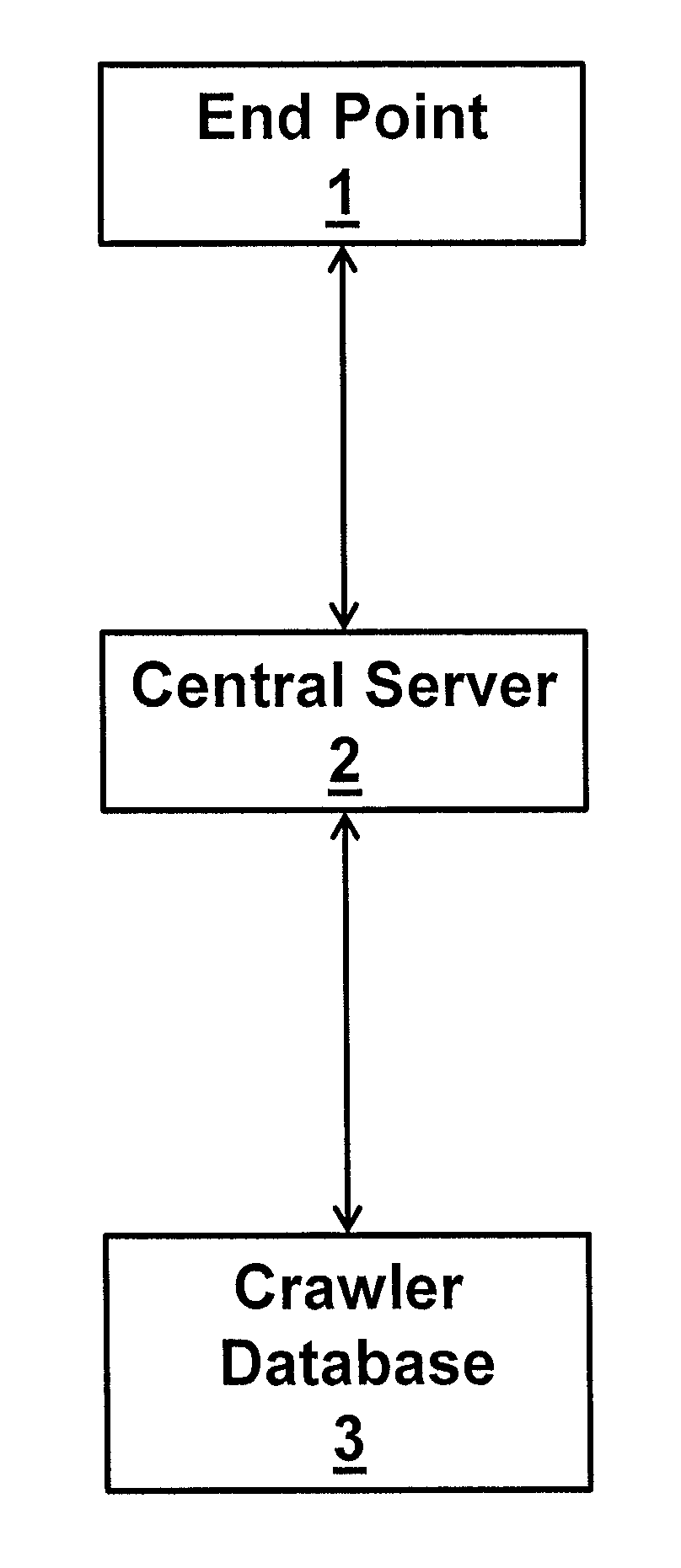
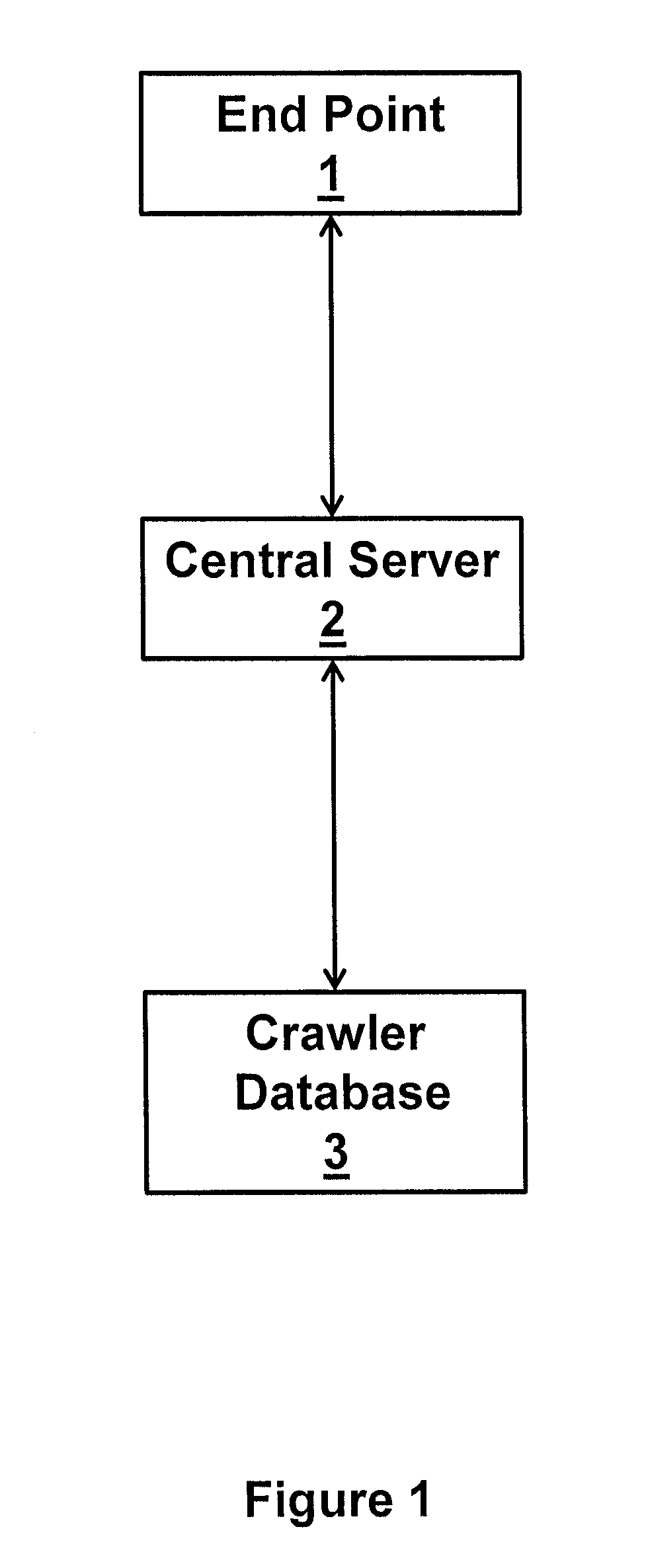
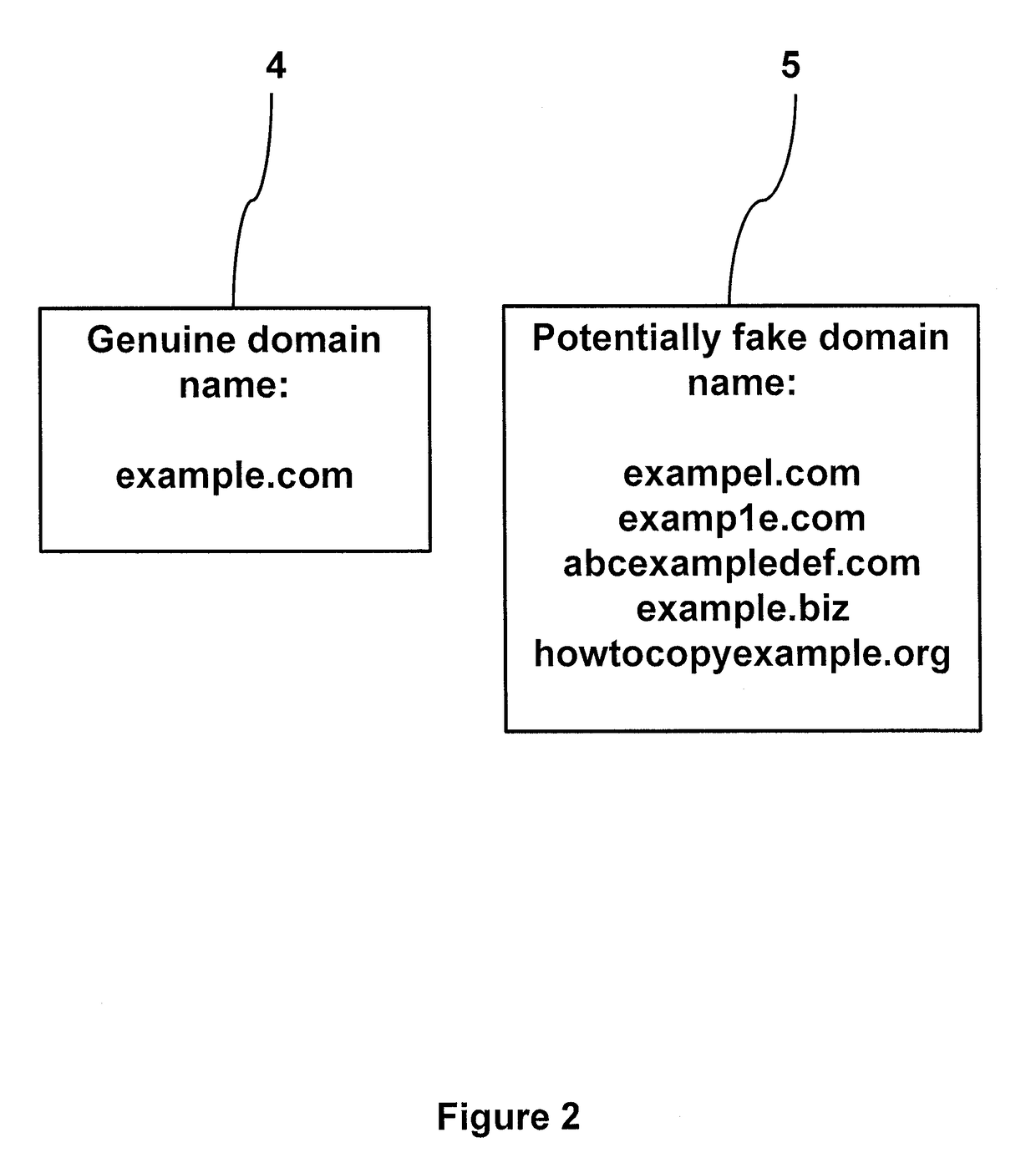
InactiveUS20180131708A1Digital data information retrievalTransmissionDomain nameSuspicious behaviour
A method of identifying fraudulent and / or malicious Internet domain and sub-domain names includes: crawling the web to identify in-use domain and / or sub-domain names and storing these in a database together with data linking domain and sub-domain names that have been determined to be associated with suspicious behaviours; receiving a search term; searching the database to identify domain and / or sub-domain names that contain the search term or a derivative thereof and saving the results as a first list of possibly suspect domain and sub-domain names; identifying within said first list one or more domain and / or sub-domain names that appear to be clearly fraudulent and / or malicious; using said database to identify domain and / or sub-domain names that are linked, in the database, to the identified domain and / or sub-domain names; and combining the identified domain and / or sub-domain names to generate a second list of highly suspect domain and / or sub-domain names.
Owner:F SECURE CORP
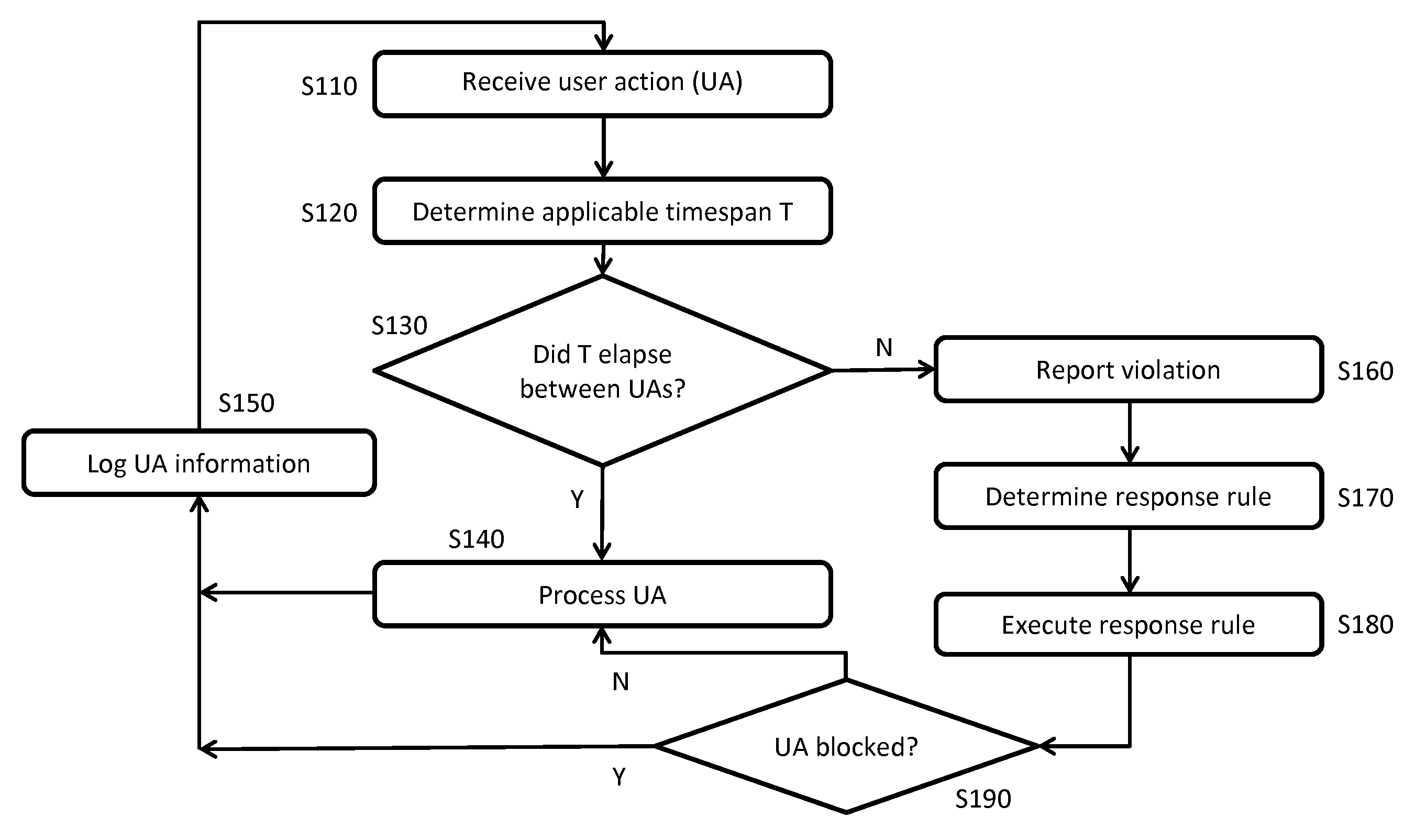
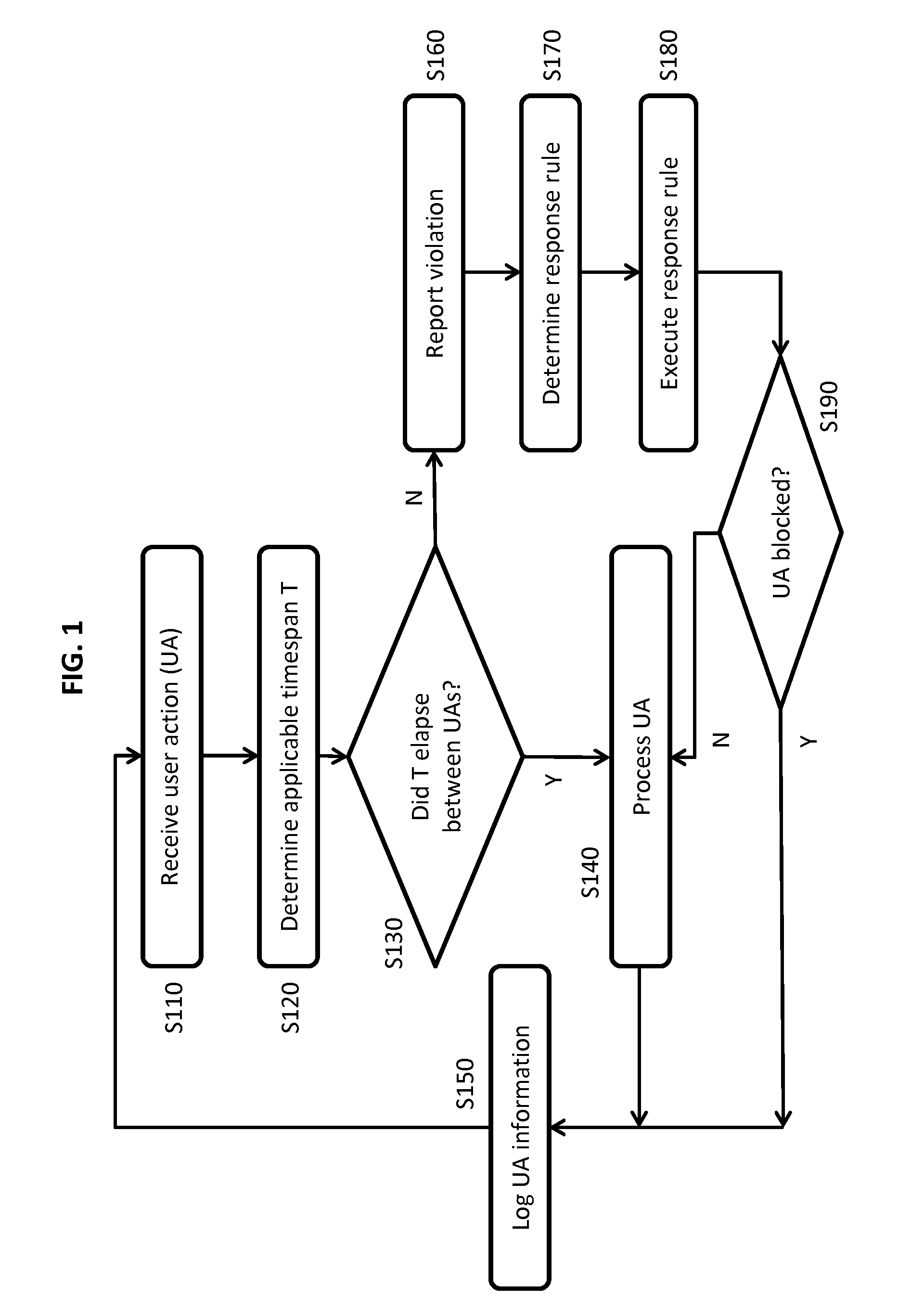
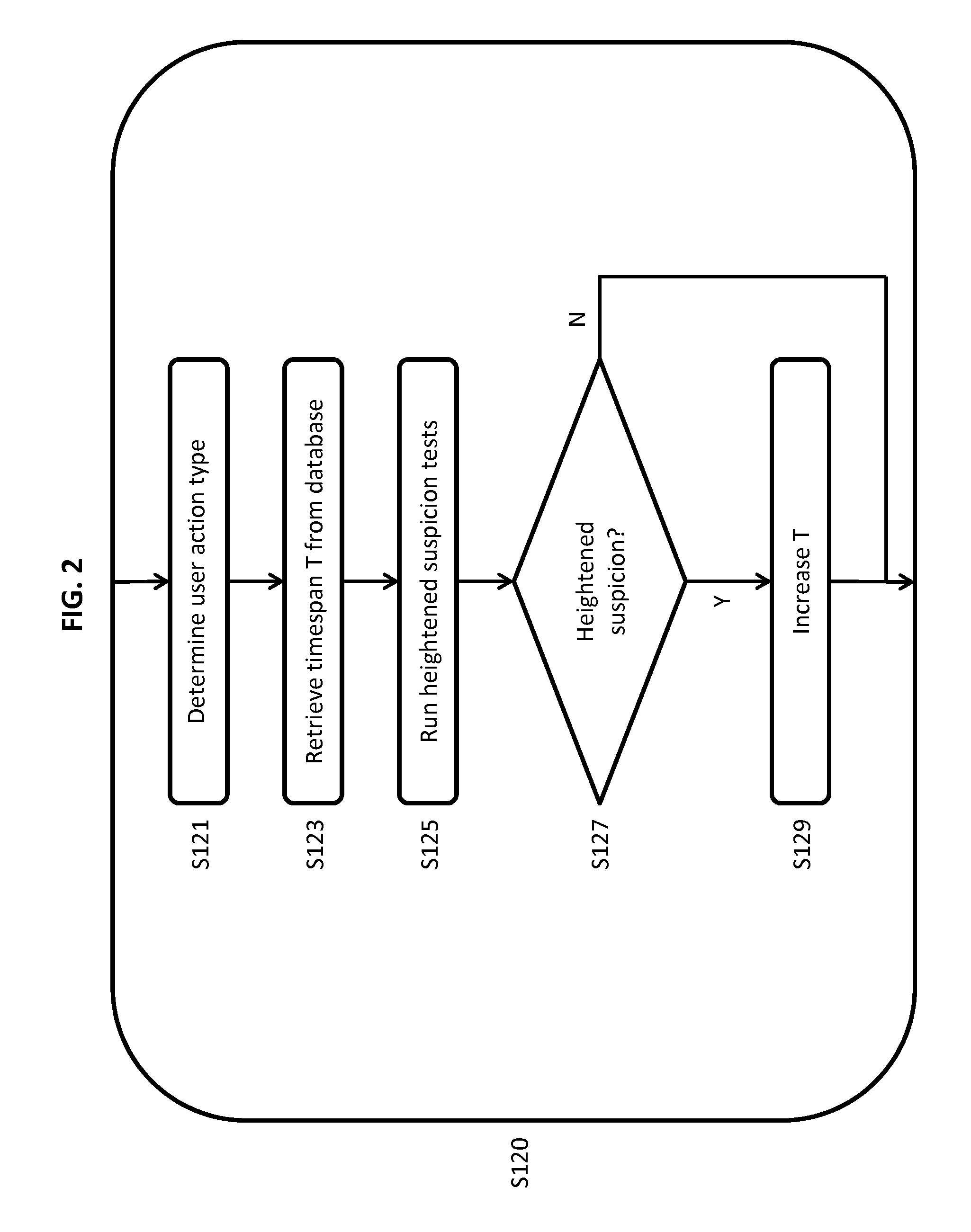
System and Method of Semi-Automated Velocity-Based Social Network Moderation
A method and system of detecting the activity of “bots” in an online community, by measuring the time elapsed between user actions and comparing this time to a timespan established as normal for users performing the same user actions without the assistance of bots. The timespan may be adjusted when other suspicion characteristics are detected. When detecting actions suspected to be bot-assisted, the method and system respond by executing one or more response instructions against the user suspected of using the bot, with the aim of preventing further bot activity. The response instructions are stored by associating them with a type of user action and a total number of suspect user actions. As a result, the response instructions may be set to increase in severity with each additional suspect act by a user.
Owner:INTERNET BRANDS
Forensic analysis
ActiveUS20180069881A1Less manipulationIncrease demandCode conversionData switching networksData setAnalysis method
The present invention relates to a forensic analysis method performed on a Distributed Computing System (DCS) (10) comprising a server (18) and at least one client machine (14). The method comprises collecting data in a client machine (14) of the DCS (10) to form a first data set, the collected data being a function call to a resource comprised in the DCS. The method further comprises applying a data reduction model to the first data set to form a second data set and processing the second data set in the server (18) of the DCS (10) to provide for detection of suspect behaviour at the client machine (14). The data reduction model is configured to extract a subset of data from the first data set to form the second data set, the subset of data comprising: user account identifier; and process and object identifier.
Owner:FORTINET
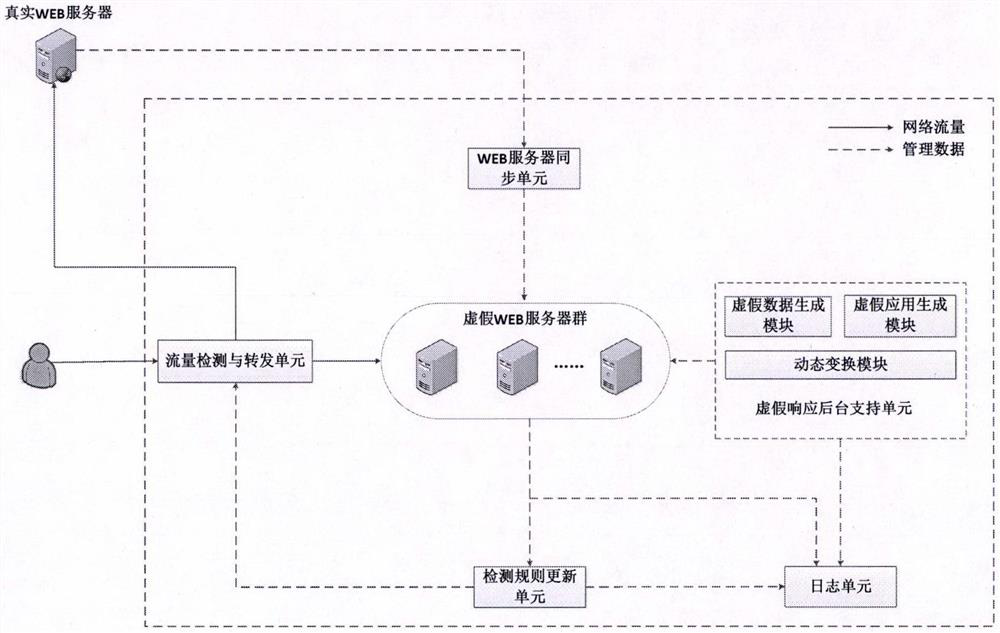
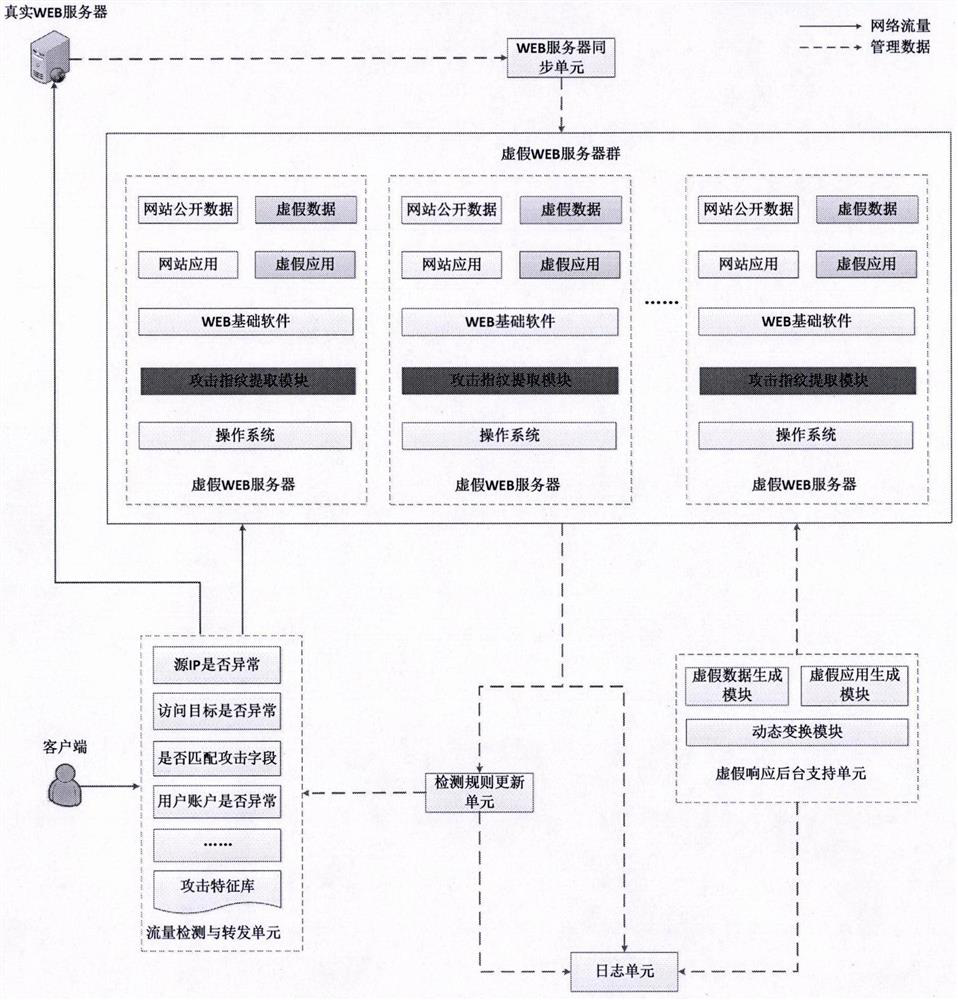
WEB dynamic adaptive defense system and defense method based on false response
The invention provides a WEB dynamic adaptive defense system and defense method based on false response. Based on the concept of moving target defense, a plurality of false WEB servers capable of being dynamically transformed is constructed around a protected WEB server, false sensitive data, false applications, false vulnerabilities and the like are constructed on the false WEB servers, and cheating hackers attack the false WEB servers. When a known attack or a suspicious behavior is identified, the known attack or the suspicious behavior is introduced into the false WEB server, and an attacker enters the false environment and then executes a subsequent attack action in the false environment until the attack is finished, so that multiple attempt attacks of the attacker are effectively defended, and meanwhile, the method has a relatively good defending capability on an unknown WEB attack. Besides, by continuously observing attack behaviors in a false environment, WEB attack features can be automatically extracted, attack detection rules are dynamically and adaptively adjusted, and the dynamic adaptive capacity of a defense system is improved.
Owner:张长河
Analyzing user behavior patterns to detect compromised nodes in an enterprise network
Systems and methods for analyzing user behavior patterns to detect compromised computing devices in an enterprise network are provided. According to one embodiment, an enforcement engine running on a network security device, identifies top users of a network exhibiting a suspicious behavior relating to login failures by determining a first set of users having a number of login failure events during a given time duration exceeding a threshold. The enforcement engine identifies from the first set of computers associated with the top users, a second set of computers exhibiting a suspicious behavior relating to new connections exceeding a threshold. The enforcement engine classifies a third set of computers, representing a subset of the second set exhibiting a suspicious behavior relating to consecutive new connections, as compromised source computers when their respective new connections are in a sequence that results in a Shannon entropy measure exceeding a threshold.
Owner:FORTINET
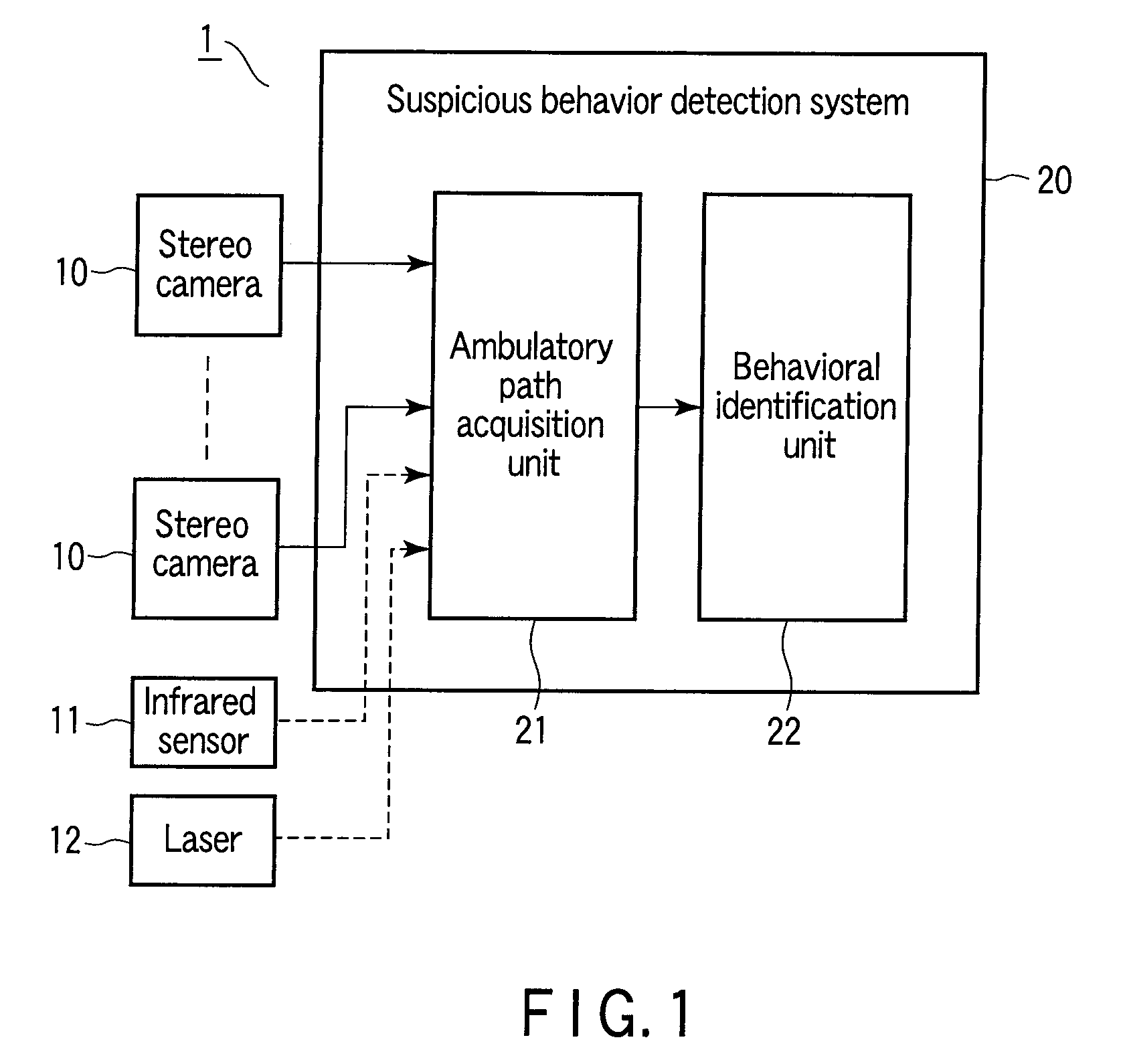
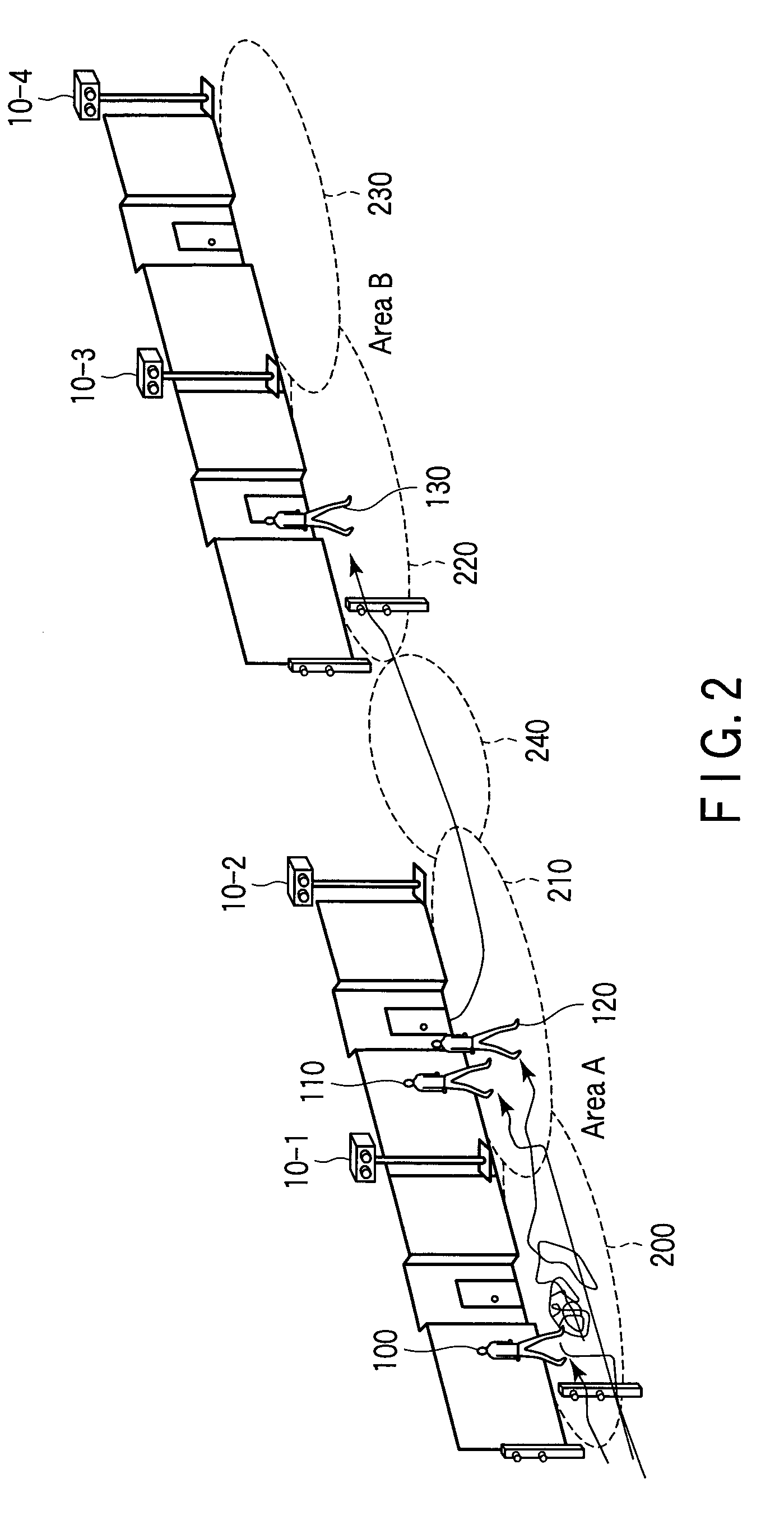
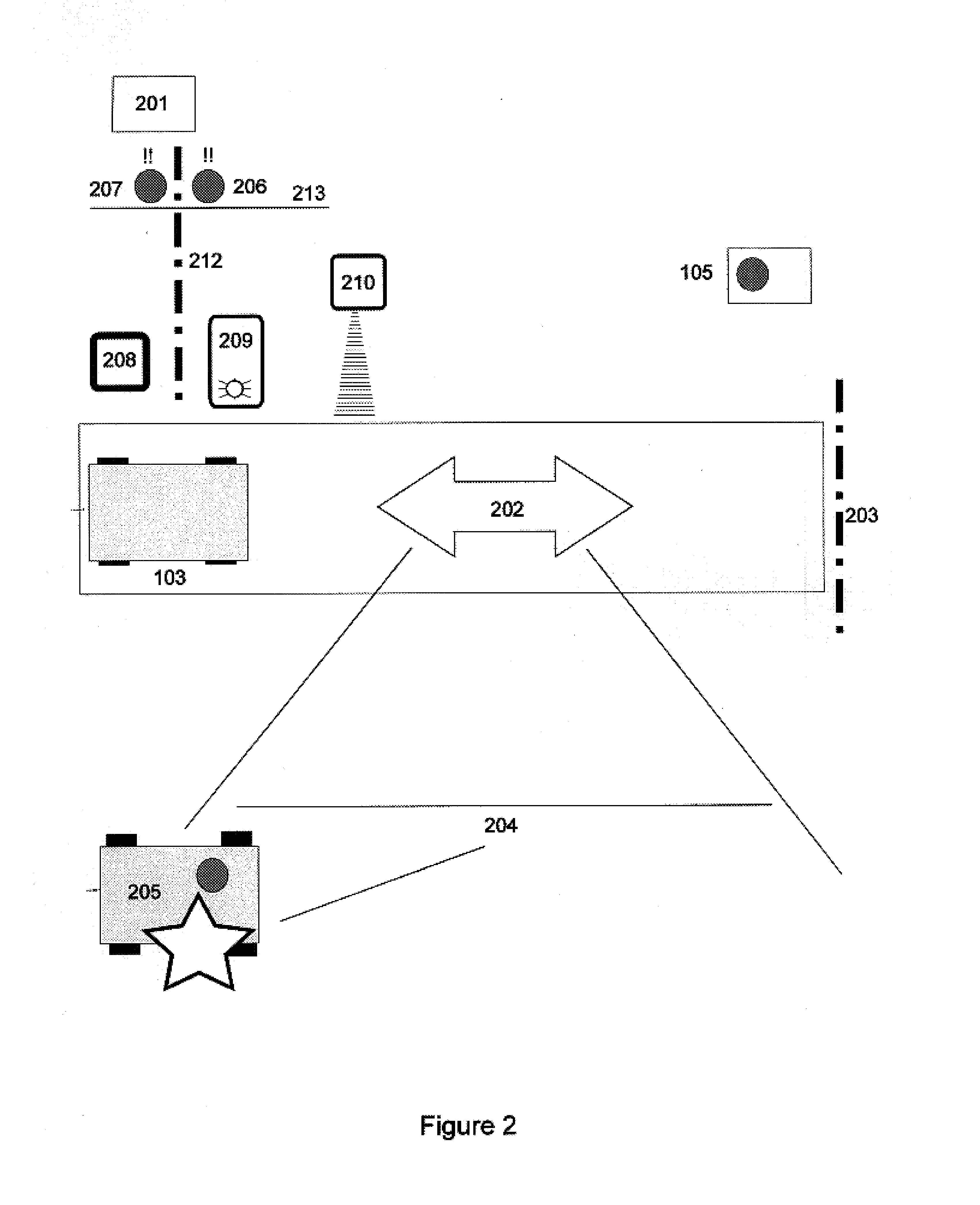
Suspicious behavior detection system and method
InactiveUS20090131836A1Person identificationCharacter and pattern recognitionSuspicious behaviourImage capture
There is provided a suspicious behavior detection system capable of specifying and identifying a suspicious person exhibiting abnormal behavior. A suspicious behavior detection system is a system to detect suspicious behavior of a monitored subject, by using images captured by a stereo camera. The suspicious behavior detection system has an ambulatory path acquisition unit which acquires ambulatory path information of the monitored subject, and a behavioral identification unit which identifies behavior of the monitored subject based on the ambulatory path information, and automatically determines suspicious behavior of the monitored subject.
Owner:KK TOSHIBA
Standoff security and real-time vendor verification system and apparatus
InactiveUS7280042B2Fast trainingReduce riskElectric signal transmission systemsMultiple keys/algorithms usageOperational systemEngineering
A stand-off security checkpoint system and apparatus that enables security officers entrusted with protecting our nations' critical infrastructure or other high risk locations, a means of verifying in real-time, the identity of entrants to a facility. Via a communications system and apparatus that is positioned a safe, stand-off distance away from the entrance to a facility, a person entering a facility exits his vehicle or walks up to a machine housing which is equipped with cameras and sensor equipment. A close up view of the persons' identification as well a picture of the person himself is captured and readied for real-time transmission to security personnel well away from the entrants location at the machine. Via wireless transmitter and receiver equipment, and computer hardware and software arrangements incorporated into the system, the entrant and his identification card can be viewed and verified, from a safe standoff distance by on-site, as well as off-site security screening personnel. The utilization of wireless networks and internet communications networks, along with the machines' physical features and use, creates multiple opportunities to detect suspicious behavior by entrants to facility well before they reach an unsafe distance to the entrance. While in operation, and with the person a safe distance away from the entrance, the system further equipped with sensors to detect metal, chemical and biological substances can also send special alerts to the detection of harmful substances, well before the entrant reaches the entrance to the facility or security checkpoint. By design, the system and apparatus creates a new and effective means of deterring terrorists who may be trying to effect a terrorist infiltration by disguising themselves as officials or vendors. Additionally, the system is designed to be laid out so as to prompt a direct separation of a would-be suicide or truck bomber from his vehicle. This can greatly deter his desire to effect an attack at that location, as the chances for nullification and or the detection of suspicious activity by security officers operating the system, well before he reaches his location are greatly in odds against him.
Owner:TRELA RICHARD STEVEN
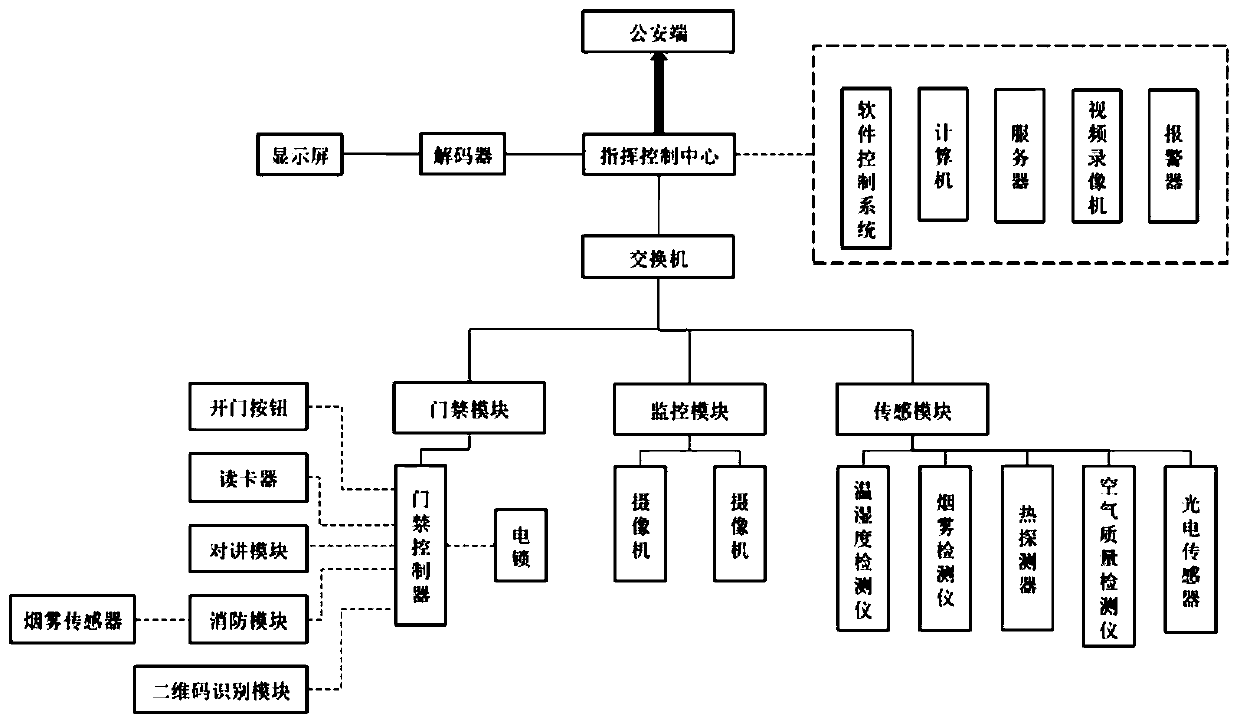
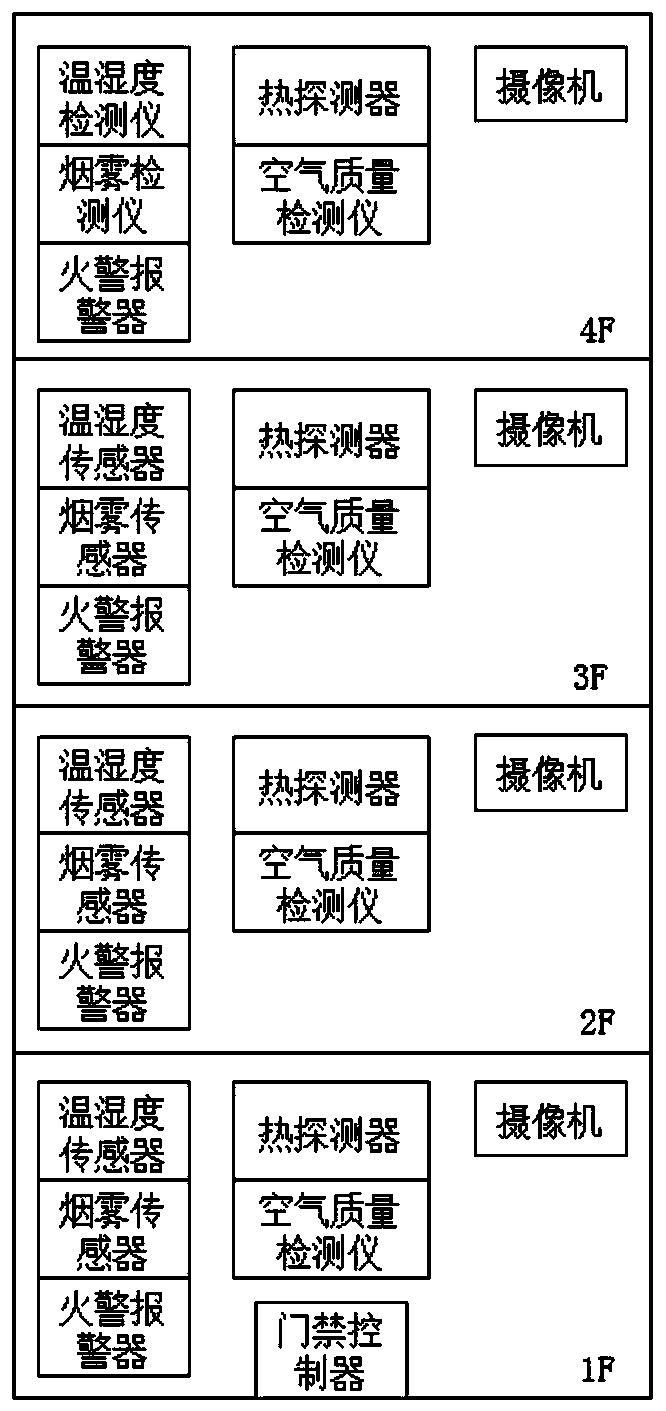
Intelligent building security system
PendingCN111212274AEffective blockingEffective predictionMechanical apparatusLighting and heating apparatusCommand and controlNetwork communication
The invention discloses an intelligent building security system. The system comprises a front-end security module and a rear-end command and control center; the front-end security module comprises anaccess control module, a camera monitoring module and a sensing module; the front-end security module is used for gathering information through a switch and gathering the information to the command and control center through a transmission network; the command and control center is used for monitoring the information and storing, forwarding and counting data, and the command and control center isin network communication with a public security terminal through a special line. According to the invention, through the arrangement of an access control controller and a reasonably arranged camera, two-stage joint defense can be carried out, strangers and unexpected guests can be effectively blocked through an access control system at the first stage, suspicious persons and suspicious behaviors can be effectively pre-judged through real-time monitoring and pre-judgment of a plurality of cameras at the second stage, and dangers are restrained before accidents as much as possible.
Owner:江苏中数智慧信息科技有限公司
Unknown virus retrieval method
ActiveCN103593614AMeet different needsReduce unnecessary analysis processPlatform integrity maintainanceSpecial data processing applicationsSuspicious behaviourData mining
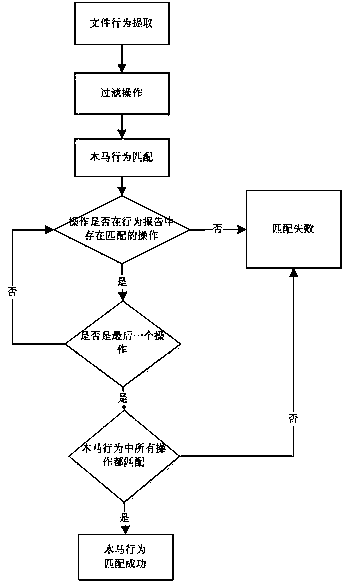
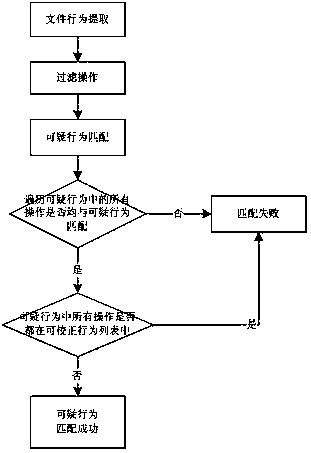
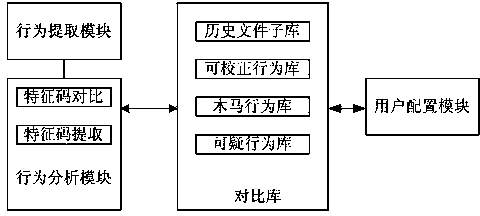
An unknown virus retrieval method includes the steps of comparison library configuration, behavior extraction and behavior analysis. The behavior analysis comprises Trojan recognition and suspicious behavior recognition. A comparison library is set in advance so as to divide basic behaviors into at least three levels, namely Trojan behaviors, suspicious behaviors and correctable behaviors according to danger levels. The behavior analysis includes Trojan recognition and suspicious behavior recognition and further comprises a suspicious behavior correction step and a filter step, wherein the suspicious behaviors are corrected in the mode that the suspicious behaviors are recognized and classified to be the correctable behaviors according to correctable comparison files in the comparison library set in advance. According to the unknown virus retrieval method and device, users can configure behaviors corresponding to the danger levels by themselves, different requirements of the different users can be met, configuration of the suspicious behaviors or the Trojan behaviors is reduced, and accordingly the unnecessary analysis process is reduced, and the virus searching efficiency is improved.
Owner:科来网络技术股份有限公司
Processing method and device in operation of application program
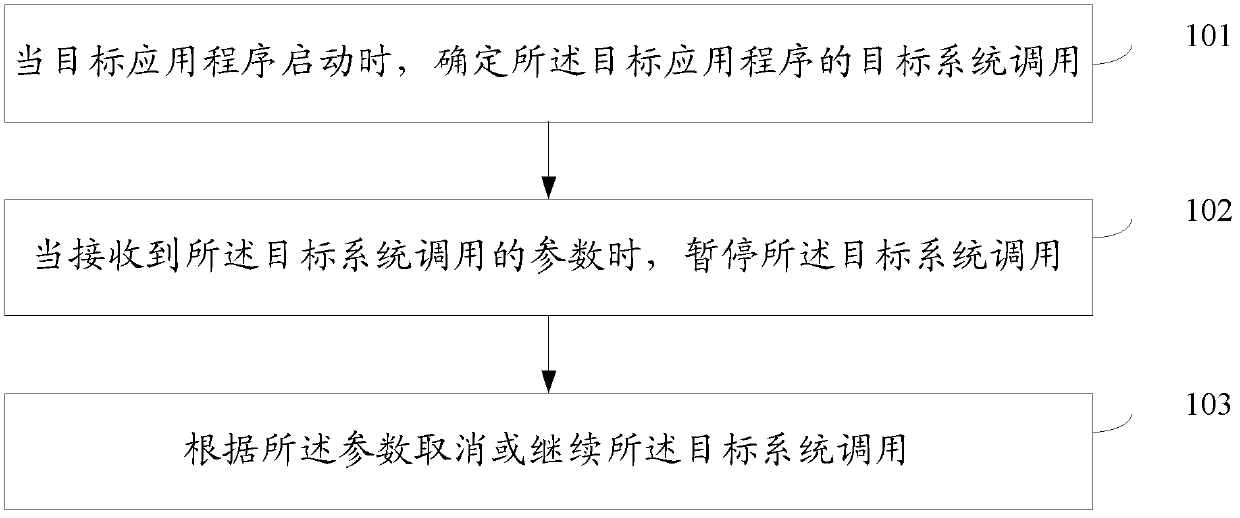
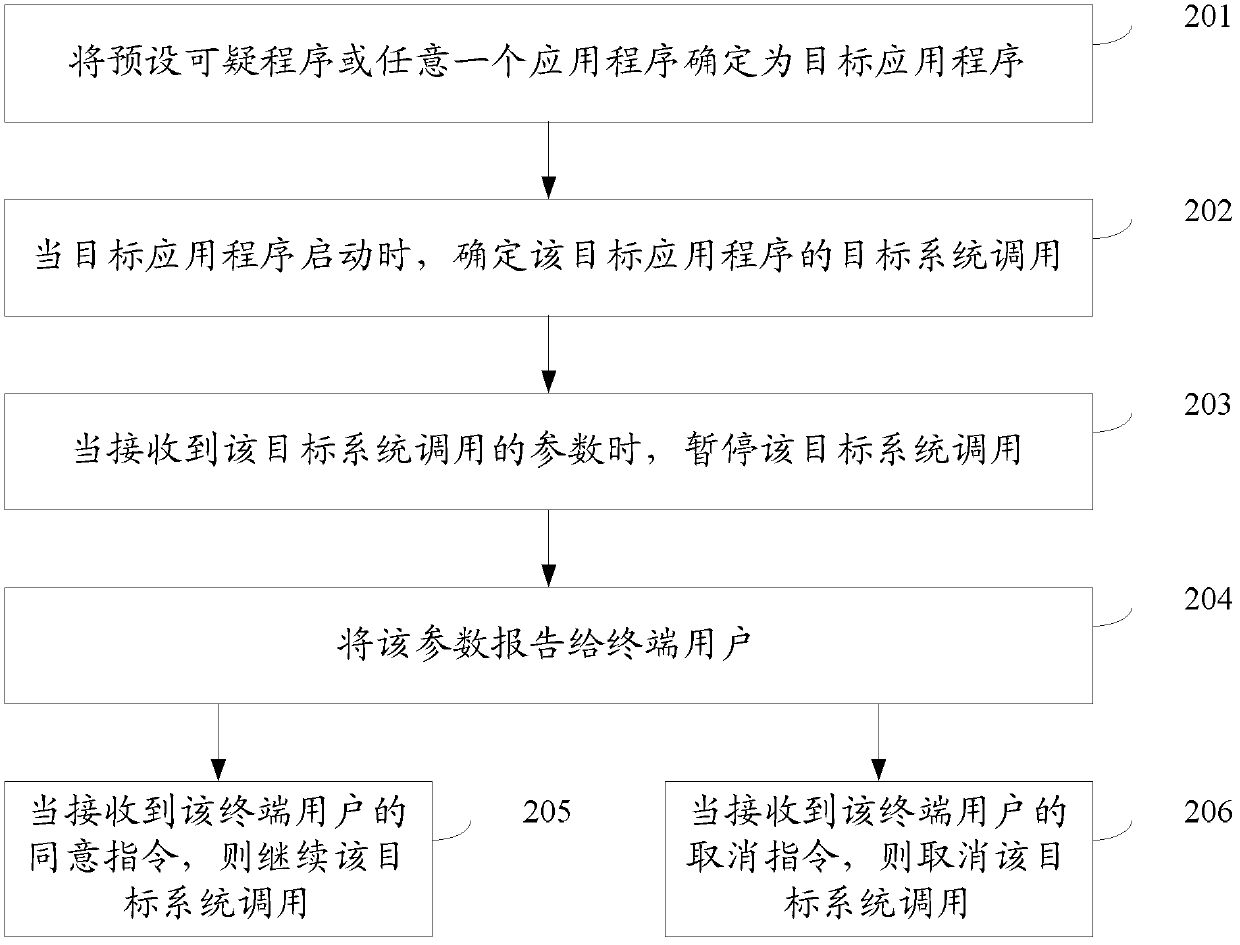
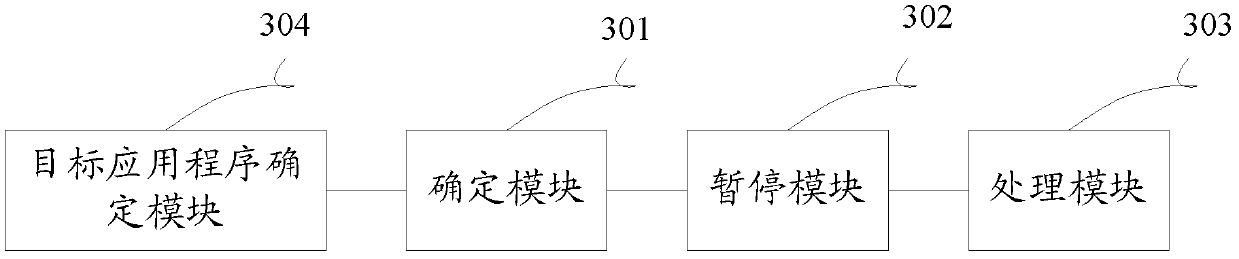
ActiveCN103294590AStrong real-timeMonitor thoroughlyMultiprogramming arrangementsSoftware testing/debuggingComputer moduleComputer terminal
The invention discloses a processing method and device in operation of an application program, and belongs to the field of mobile terminals. The method comprises the steps as follows: when a target application program is started, and target system call of the target application program is guaranteed; when a parameter for the call of the target system is received, the target system call is paused; and the target system call is canceled or continued according to the parameter. The device comprises a determining module, a pause module and a processing module. An embodiment of the method and the device can interrupt the behavior before the implementation of a suspicious act, and the operation of the application program is not required to be ended; and the monitoring timeliness is high, the application range is wide, a suspicious application program can be monitored more thoroughly and more widely, and a sensitive application program is protected.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
College student management system based on face recognition technology
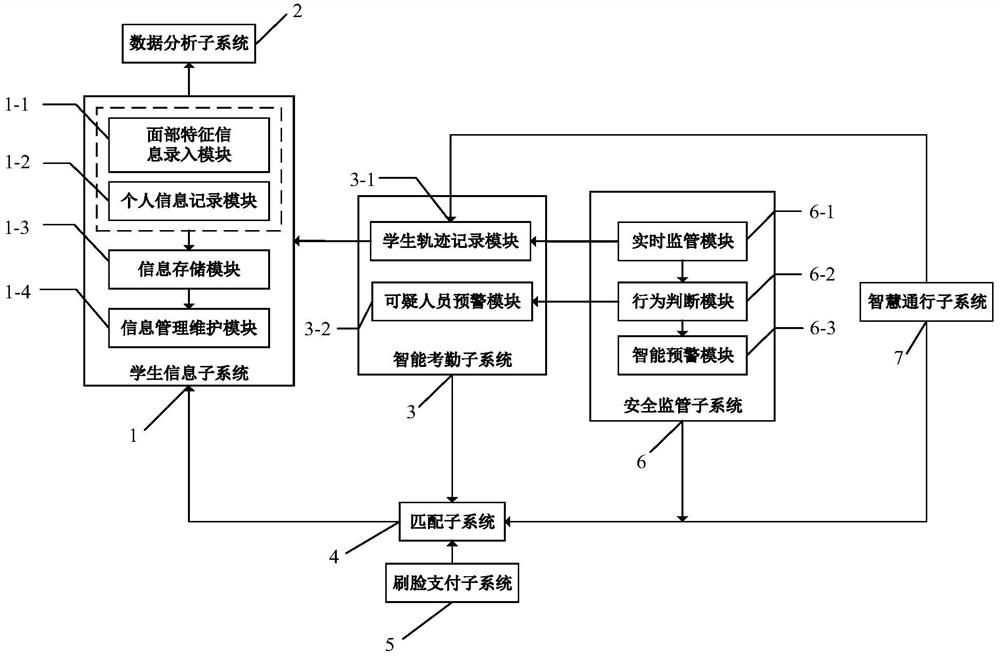
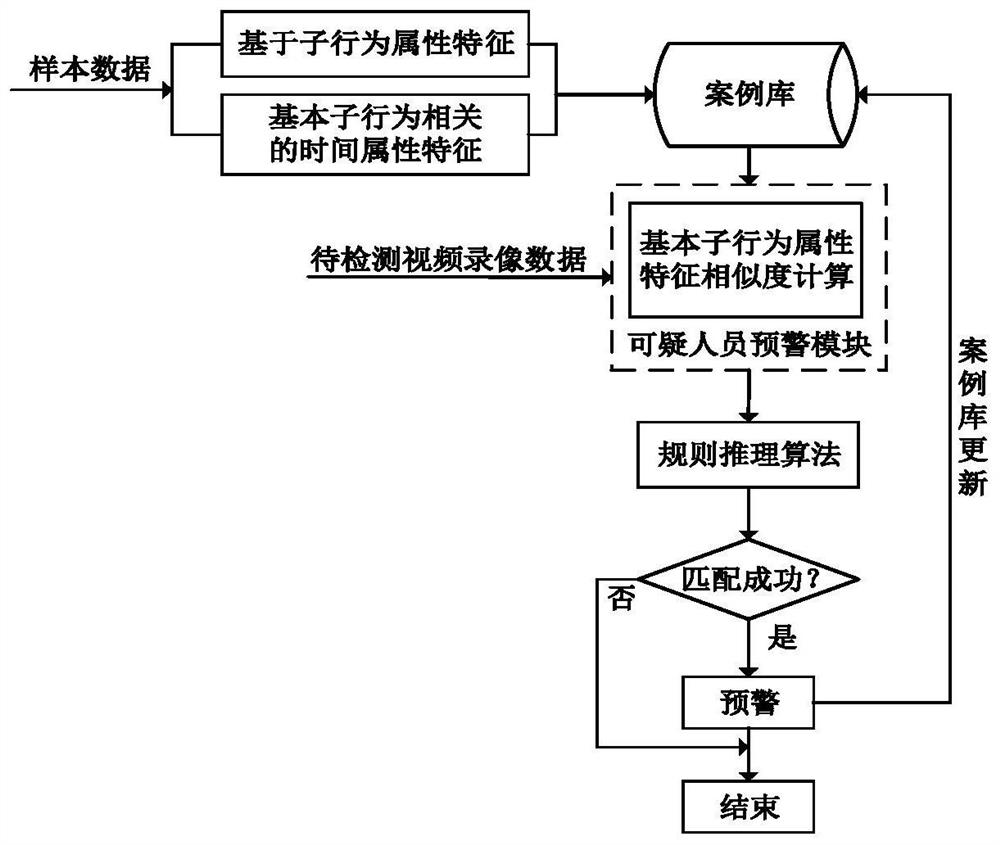
InactiveCN111754669AEnsure safetyWith real-time supervision and early warning functionData processing applicationsCharacter and pattern recognitionEngineeringSuspicious behaviour
The invention discloses a college student management system based on a face recognition technology. The system comprises a student information subsystem, a data analysis subsystem, an intelligent attendance subsystem, a matching subsystem, a face-scanning payment subsystem, a safety supervision subsystem and an intelligent passage subsystem. A student information database for storage is established; the recognized image data are matched through a face recognition technology, image preprocessing, a feature face matching algorithm and the like so as to be used for face-scanning payment, intelligent passage, data analysis and the like; a safety supervision subsystem is constructed, a behavior judgment module is designed, and early warning is performed on suspicious behaviors and sudden emergency abnormal conditions by adopting a suspicious behavior recognition model based on case-based reasoning; a data analysis technology and a data analysis tool are used to carry out visual data analysis on life and various aspects of students. According to the invention, colleges and universities are helped to manage students more intelligently and conveniently, a lot of human resources are saved,the management efficiency is improved, and the safety of students is effectively guaranteed to a certain extent.
Owner:GUILIN UNIVERSITY OF TECHNOLOGY
Endpoint inter-process activity extraction and pattern matching
ActiveUS11184374B2Facilitates discovery of complicated and/or long-actingOperation moreWeb data indexingPlatform integrity maintainanceCyber-attackPattern matching
An automated method for cyberattack detection and prevention in an endpoint. The technique monitors and protects the endpoint by recording inter-process events, creating an inter-process activity graph based on the recorded inter-process events, matching the inter-process activity (as represented in the activity graph) against known malicious or suspicious behavior (as embodied in a set of one or more pattern graphs), and performing a post-detection operation in response to a match between an inter-process activity and a known malicious or suspicious behavior pattern. Preferably, matching involves matching a subgraph in the activity graph with a known malicious or suspicious behavior pattern as represented in the pattern graph. During this processing, preferably both direct and indirect inter-process activities at the endpoint (or across a set of endpoints) are compared to the known behavior patterns. The approach herein provides for systematic modeling of inter-process behaviors for characterizing malicious or suspicious patterns among processes.
Owner:INT BUSINESS MASCH CORP
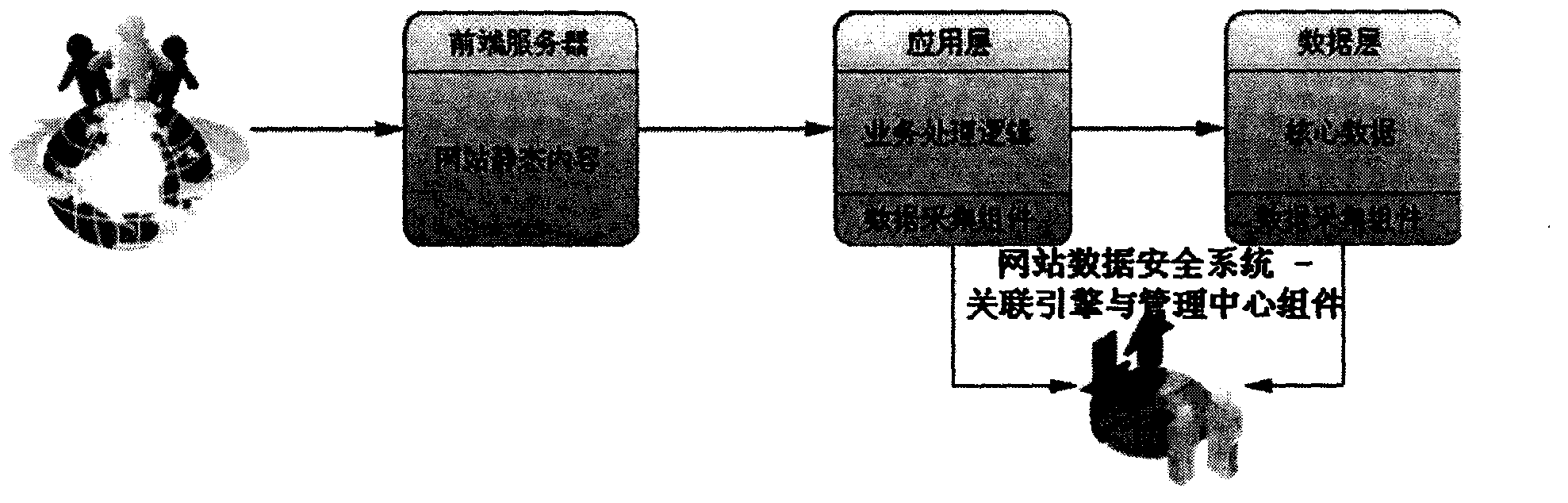
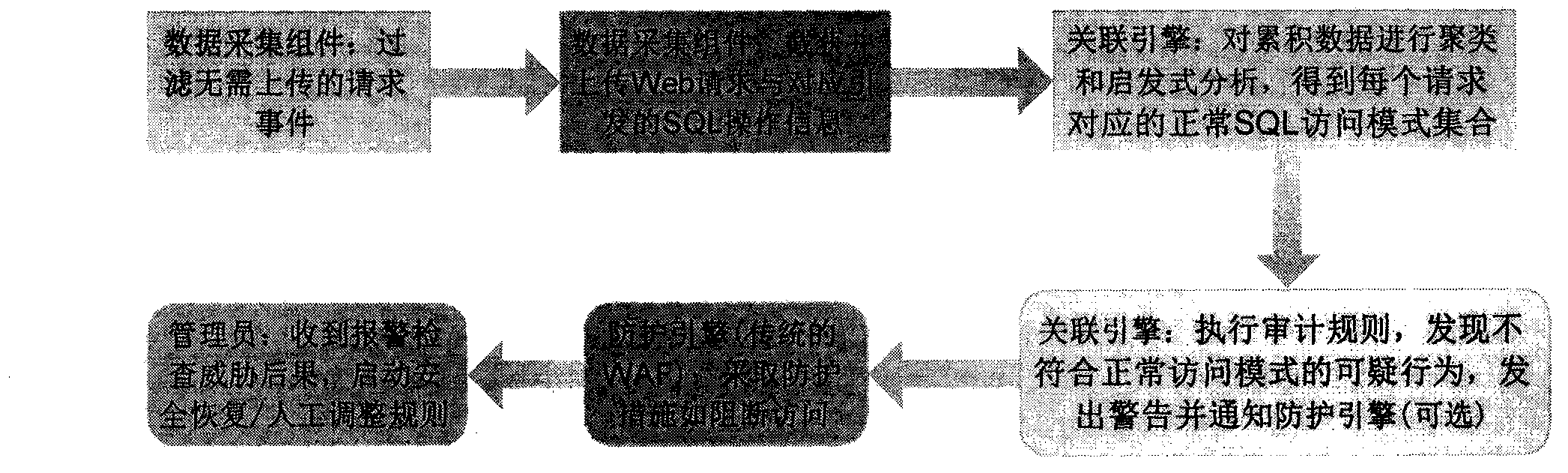
Website data security system based on association analysis of database activity and web access
InactiveCN104143064ADigital data protectionPlatform integrity maintainanceWeb siteStatistical analysis
At present, web security protection aims to discover and prevent attack and suspicious actions in time, but in reality, there are still new bug / attack manners can escape from system detection and protection. Webmasters most concern about security of core data; in other words, how to prevent data leakage / data tampering and corruption is the big problem which is in great need of being solved in the field of security protection. The website data security system adopts the database activity monitoring technology which is applied to the field front, realizes association and statistical analysis of web requests and responses, corresponding database access and feedback results to acquire a request mode set of normal access to the core data to the website, and further, checks the subsequent web access according to a rule generated by the set so as to discover suspicious data leakage / tampering actions, thus the difficult problem about website data security protection is solved thoroughly through a data security data backup component.
Owner:朱烨 +1
Real-time monitoring platform based on government affair application security
InactiveCN112104659AReal-time monitoring of government application dataQuick discoveryData processing applicationsTransmissionPrivate networkSuspicious behaviour
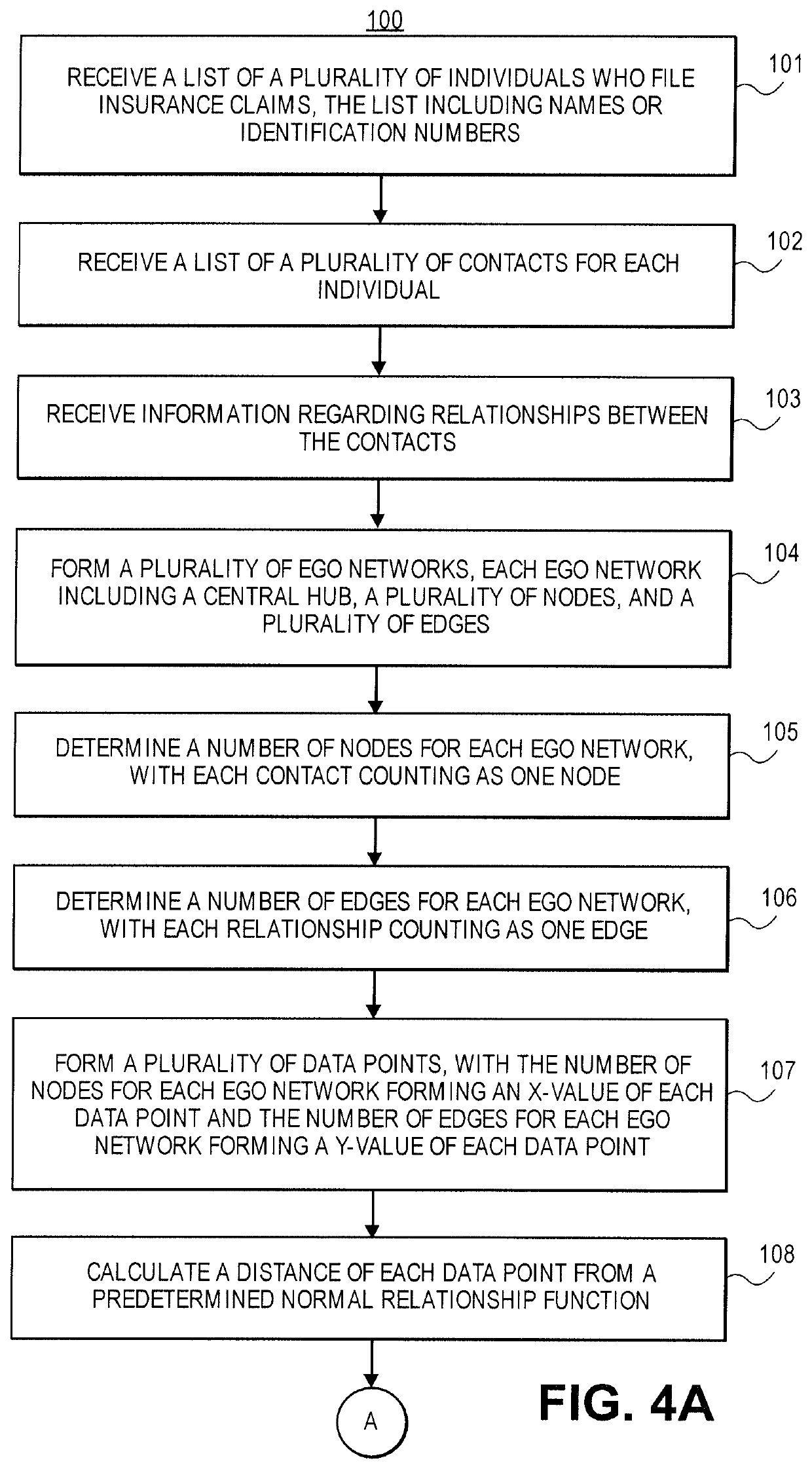
The invention relates to the technical field of government affair application security monitoring, and discloses a government affair application security-based real-time monitoring platform, which comprises a government affair big data center, a government affair application situation awareness analysis system, log acquisition equipment and flow auditing equipment, wherein the log acquisition equipment and the traffic auditing equipment acquire data from a government affair private network in a distributed manner and are connected to the government affair big data center; the government affairapplication situation awareness analysis system analyzes, models and learns a user of a government affair application based on data stored in a government affair big data center, thereby constructingnormal states of the user in different scenes and forming a baseline, and monitoring a current behavior of the user in real time. Suspicious behaviors existing in the user, the system and the equipment are discovered in time through the constructed rule model, the statistical model, the machine learning model and the unsupervised clustering analysis. According to the invention, the problems of lack of a real-time monitoring mechanism, incapability of timely analyzing threat elements and incapability of timely discovering abnormal behaviors in the current government affair application are solved.
Owner:宋清云
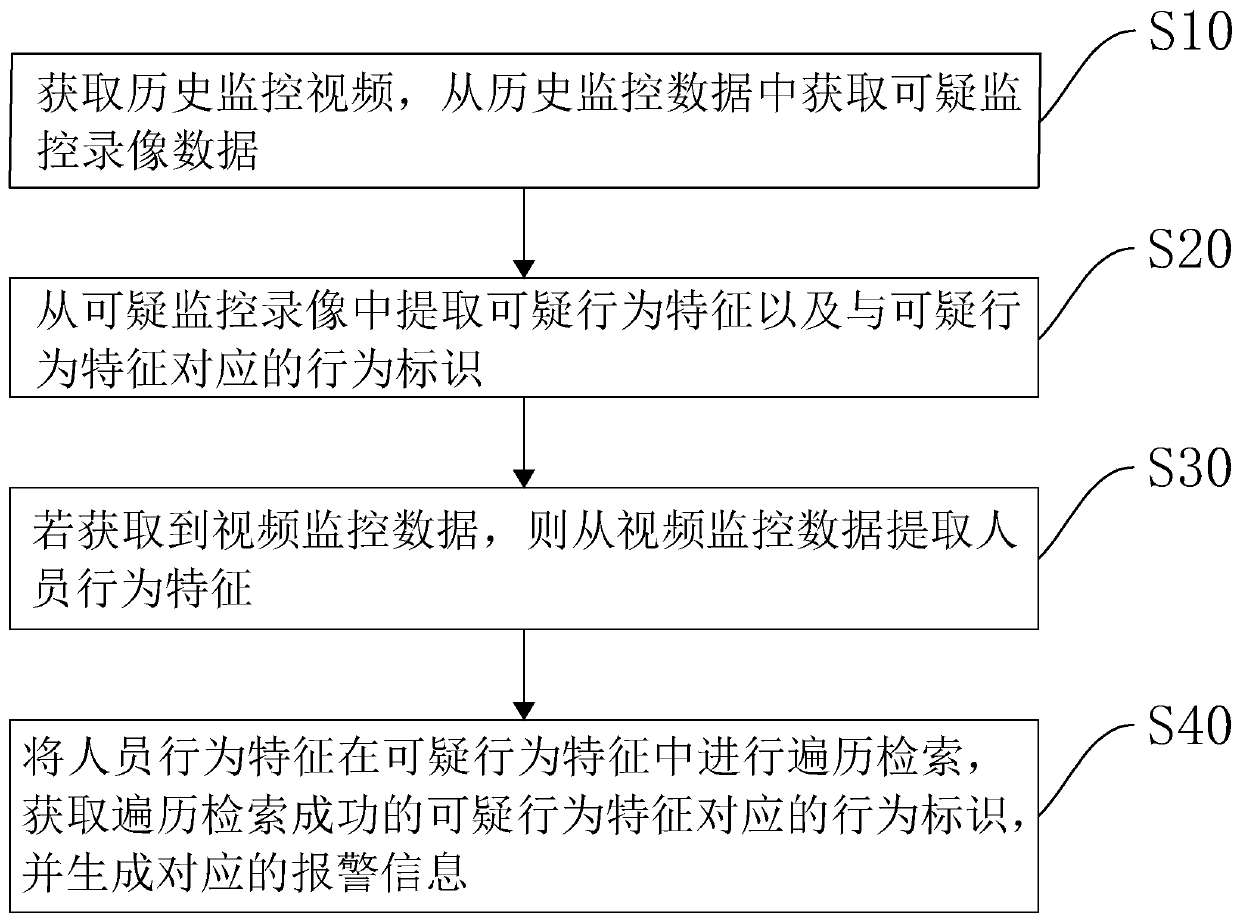
Big data video retrieval method and device, computer equipment and storage medium
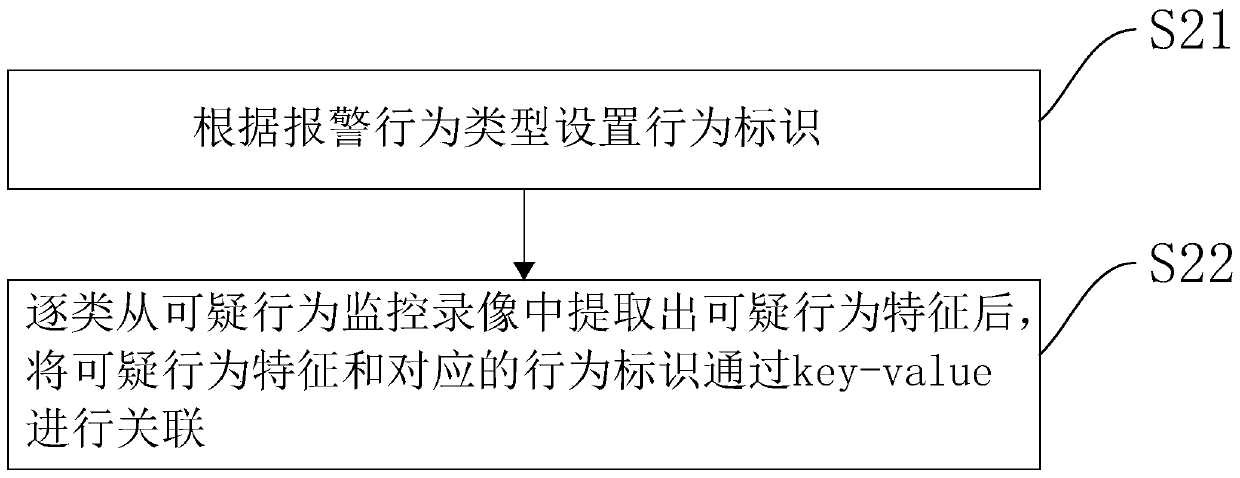
PendingCN111339366AImprove securityDigital data information retrievalCharacter and pattern recognitionVideo retrievalVideo monitoring
The invention relates to the technical field of computer technologies, in particular to a big data video retrieval method and device, computer equipment and a storage medium, and the big data video retrieval method comprises the following steps: S10, obtaining a historical monitoring video, and obtaining suspicious monitoring video data from the historical monitoring data; s20, extracting suspicious behavior characteristics and behavior identifiers corresponding to the suspicious behavior characteristics from the suspicious monitoring video; s30, if the video monitoring data is obtained, extracting personnel behavior characteristics from the video monitoring data; and S40, performing traversal retrieval on the personnel behavior characteristics in the suspicious behavior characteristics, obtaining the behavior identifiers corresponding to the suspicious behavior characteristics which are successfully traversed and retrieved, and generating corresponding alarm information. The method and the device have the effect of obtaining behaviors in the crowd in time.
Owner:广州市炬盾科技发展有限公司
Credit exchange cheating behavior processing method and device
PendingCN111681044AThe cheating is timely and accurateMathematical modelsMarketingSuspicious behaviourFinancial transaction
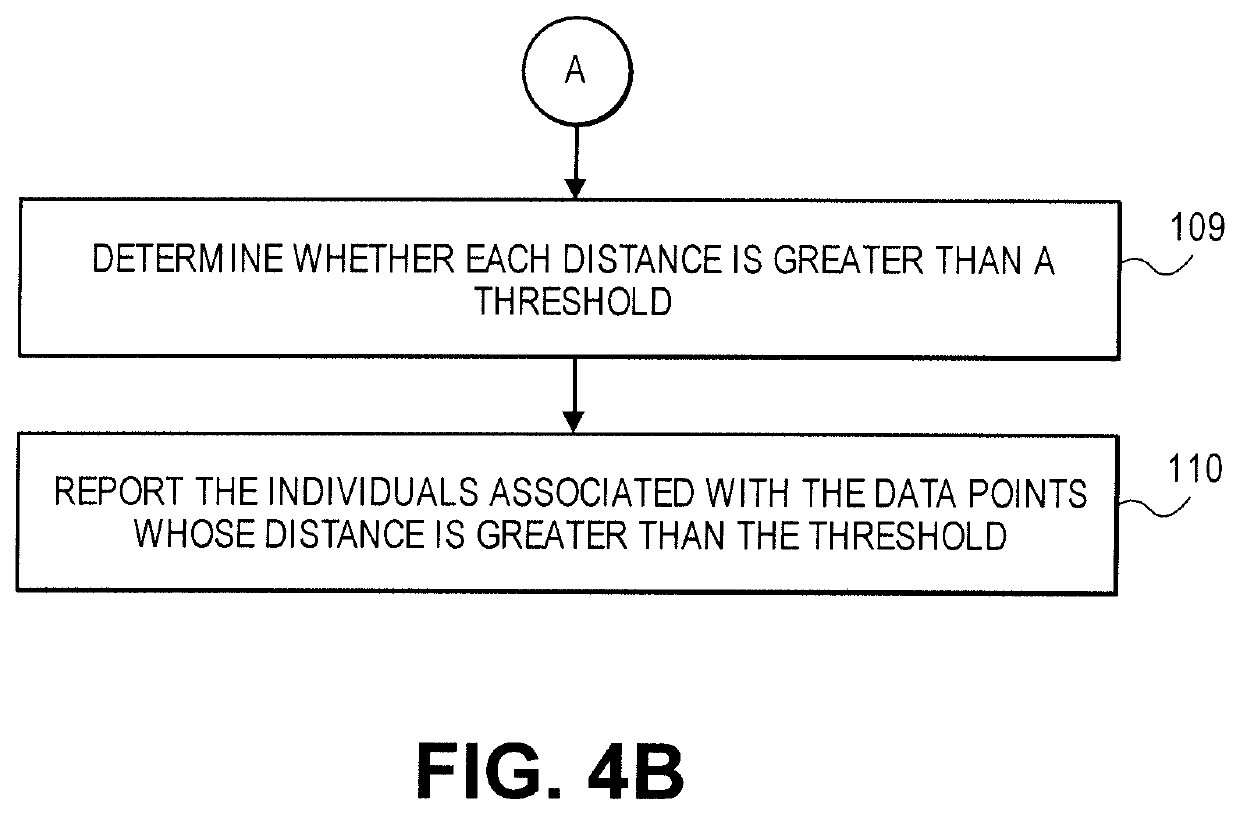
The invention provides a credit exchange cheating behavior processing method and device. Characteristic information of a card holding user is input into a preset Bayesian network model; according to output of the Bayesian network model, credit exchange transaction of a card is processed. The credit card credit exchange behavior of the card holder can be predicted under the condition that the credit exchange used by the normal card holder is not influenced, an alarm is given immediately once cheating or suspicious behaviors are found, and the customer cheating behaviors can be found timely andaccurately.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
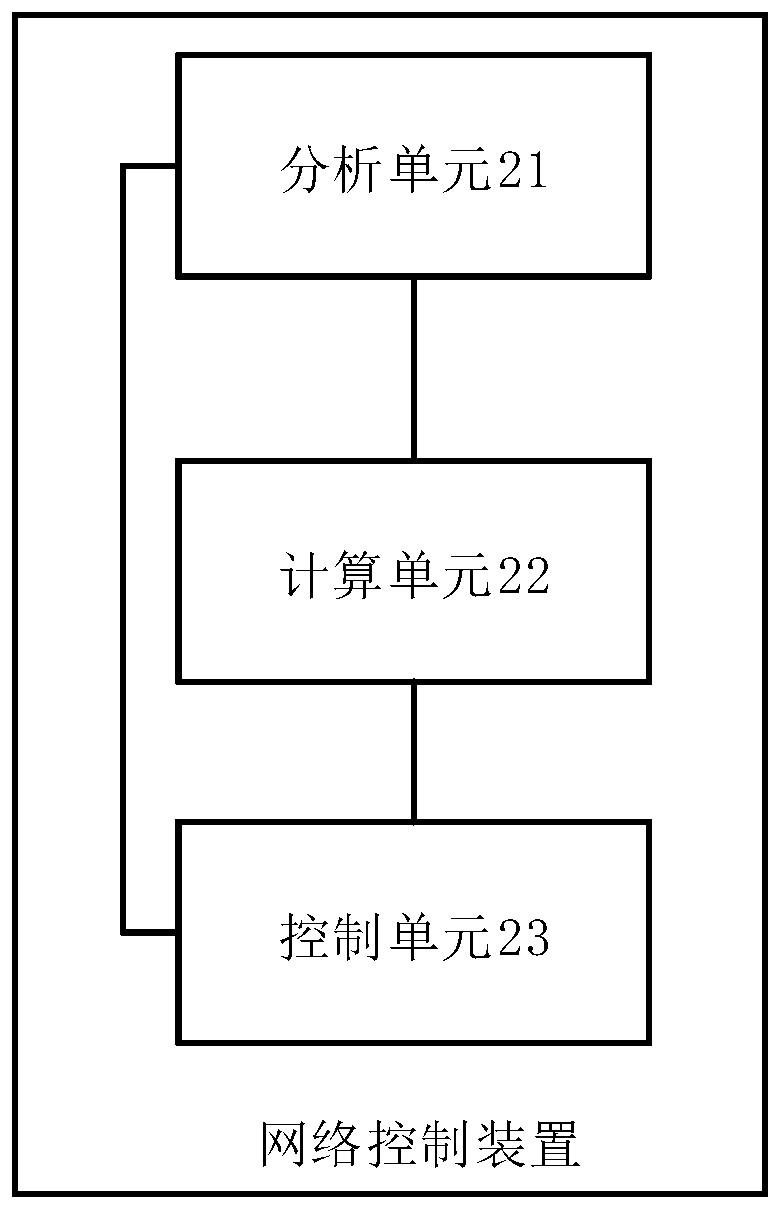
Network control method, device thereof and equipment and machine readable storage medium
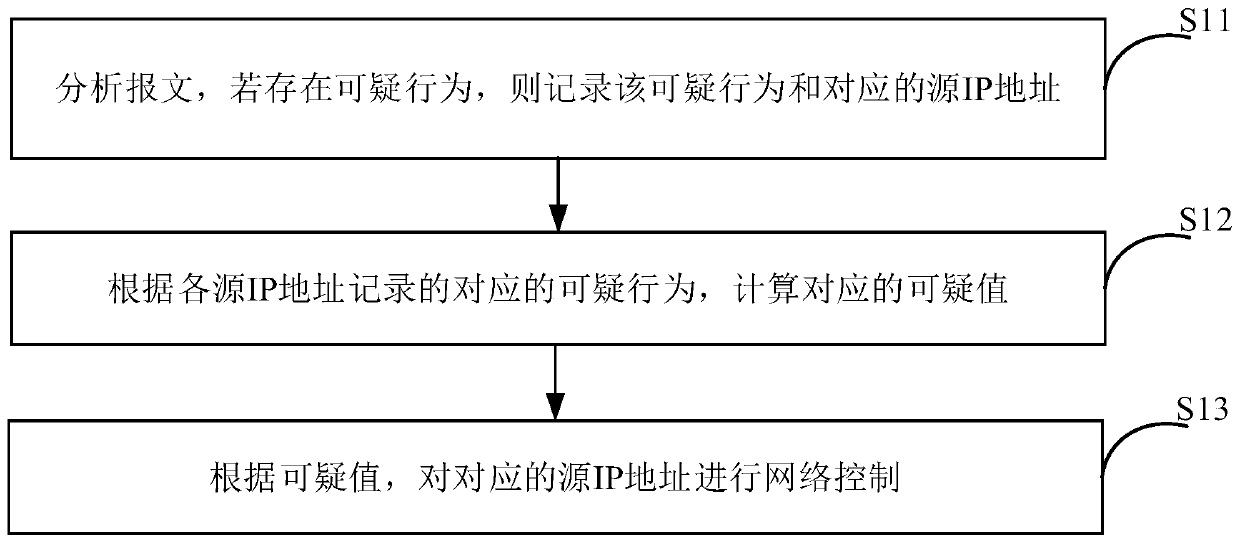
InactiveCN111478860AReduce the possibility of being mistakenly restrictedData switching networksIp addressNetwork control
The invention provides a network control method, a device thereof and equipment and a machine readable storage medium, and the method comprises the steps: analyzing a message, and recording a suspicious behavior and a corresponding source IP address if the suspicious behavior exists; calculating a corresponding suspicious value according to the corresponding suspicious behavior recorded by each source IP address; and performing network control on the corresponding source IP address according to the suspicious value. According to the technical scheme, the suspicious behaviors of the source IP addresses are analyzed, the suspicious values are obtained according to the suspicious behaviors, and the source IP addresses with high suspicious degree can be obtained according to the suspicious values, so that network control is carried out on the source IP addresses, and the possibility that normal users are mistakenly limited is reduced.
Owner:NEW H3C SECURITY TECH CO LTD
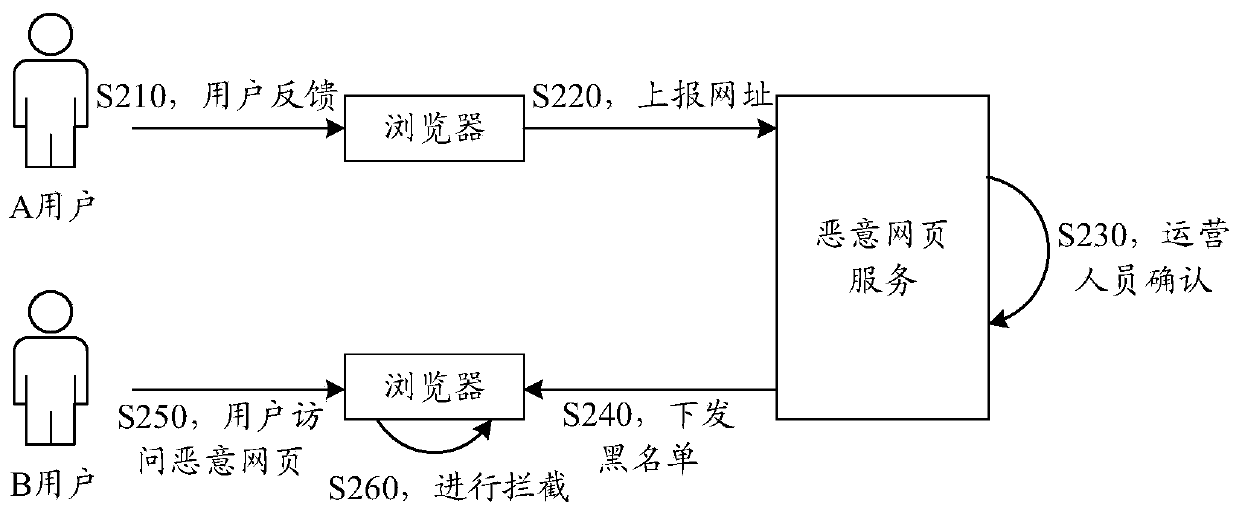
Method and device for detecting malicious behavior of webpage
ActiveCN111163054AImprove accuracyIncrease credibilityPlatform integrity maintainanceTransmissionThird partyEngineering
The invention provides a method and device for detecting a malicious behavior of a webpage. The method comprises the steps that a browser opens a webpage according to a webpage access request of a user; the browser determines that the webpage has a suspicious behavior, wherein the suspicious behavior includes one or more of popup, skip, camera calling, file access, third-party application pulling,calling and SMS sending; the browser reopens the webpage in a sandbox; and if the webpage opened in the sandbox still has the suspicious behavior, the browser reports that the webpage has a maliciousbehavior to a server. According to the technical scheme of the embodiment of the invention, the malicious behavior is identified according to the replay of the webpage behavior in the sandbox, and the malicious behavior of the webpage can be accurately and efficiently identified.
Owner:PETAL CLOUD TECH CO LTD
Intelligent building monitoring terminal, monitoring system and monitoring method
PendingCN111985413AImprove monitoring efficiencyHigh precisionCharacter and pattern recognitionMonitoring systemSuspicious behaviour
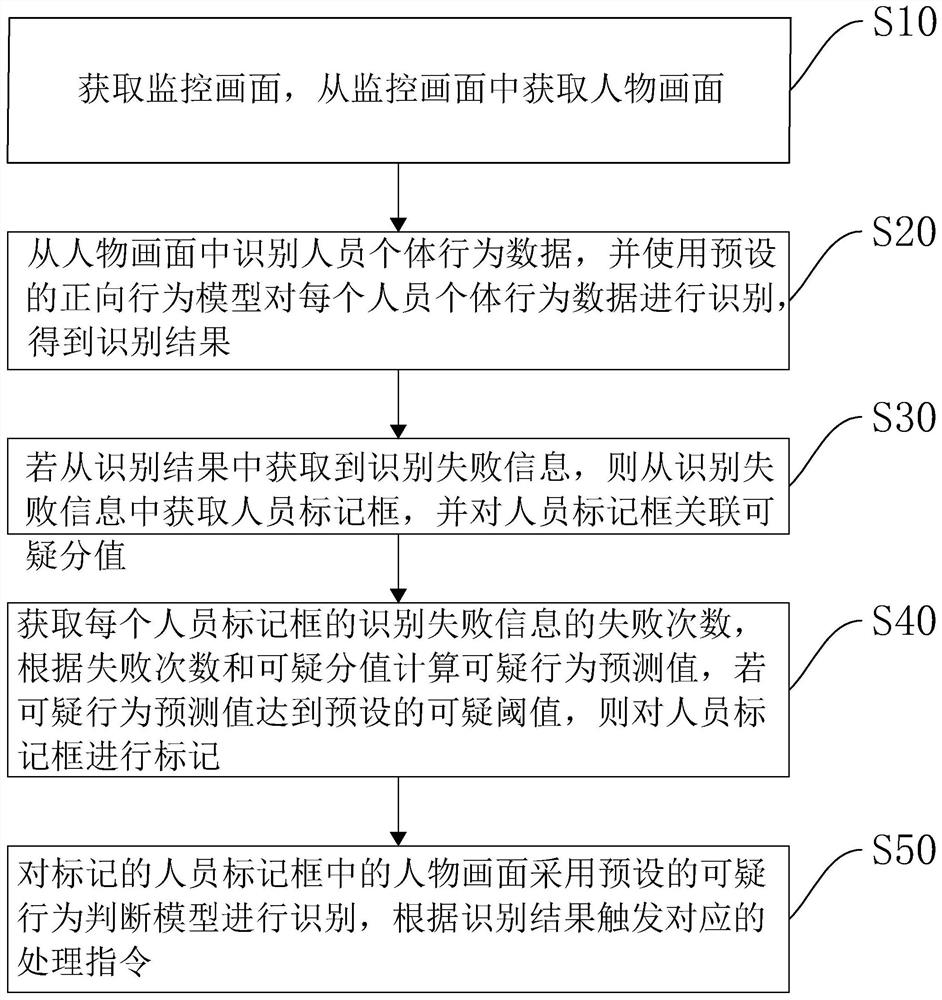
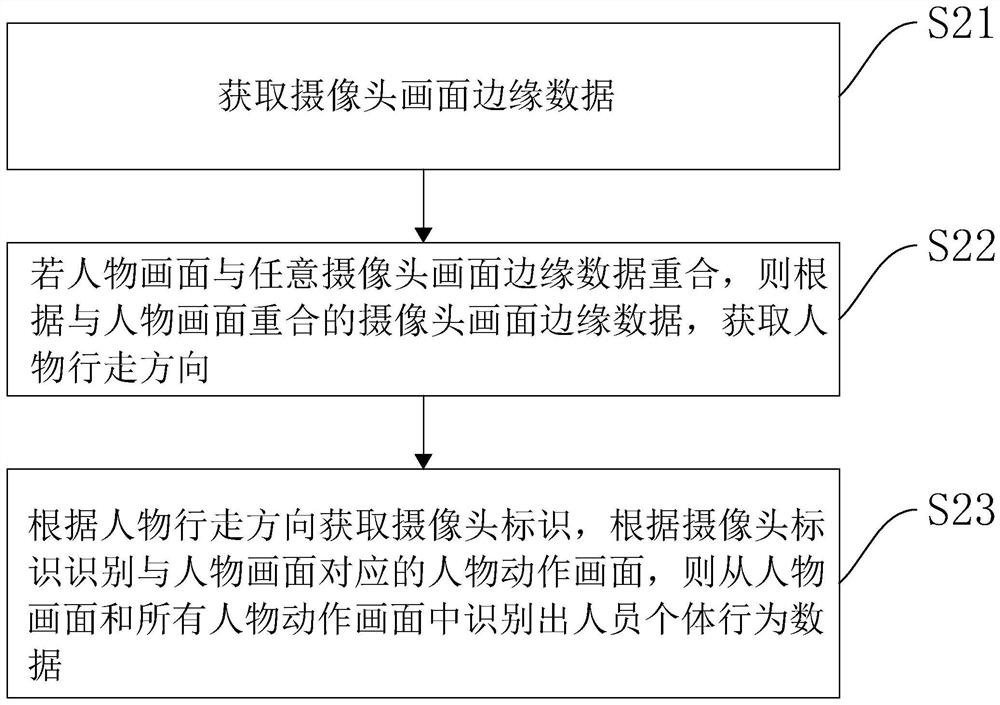
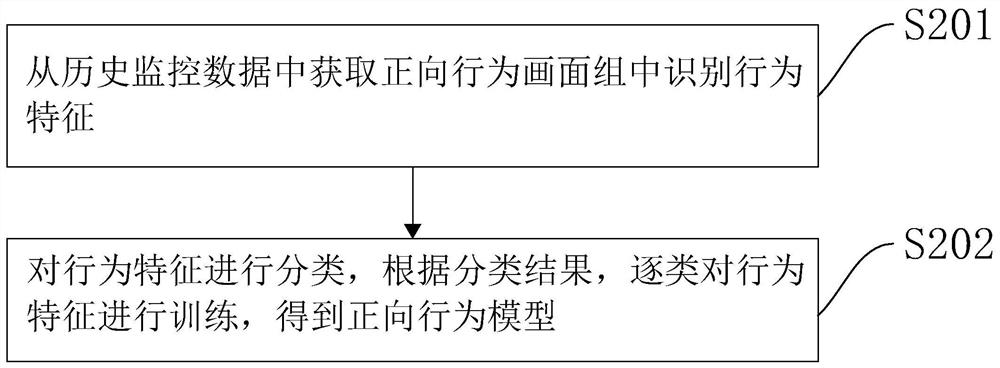
The invention relates to the technical field of building monitoring, in particular to an intelligent building monitoring terminal, monitoring system and monitoring method, and the method comprises thefollowing steps: obtaining a monitoring image, and obtaining a figure image from the monitoring image; identifying personnel individual behavior data from the figure picture, and identifying each piece of personnel individual behavior data by using a preset forward behavior model to obtain an identification result; if the identification failure information is obtained from the identification result, obtaining a personnel marking box from the identification failure information, and associating a suspicious score with the personnel marking box; and calculating a suspicious behavior prediction value according to the failure frequency of the identification failure information of each personnel marking box and the suspicious score, and marking the personnel marking boxes if the suspicious behavior prediction value reaches a preset suspicious threshold. The invention has the effect of reasonably predicting unknown suspicious behaviors from monitoring videos.
Owner:深圳市信诺兴技术有限公司
System and method for delaying an alert based on suspicious activity detection
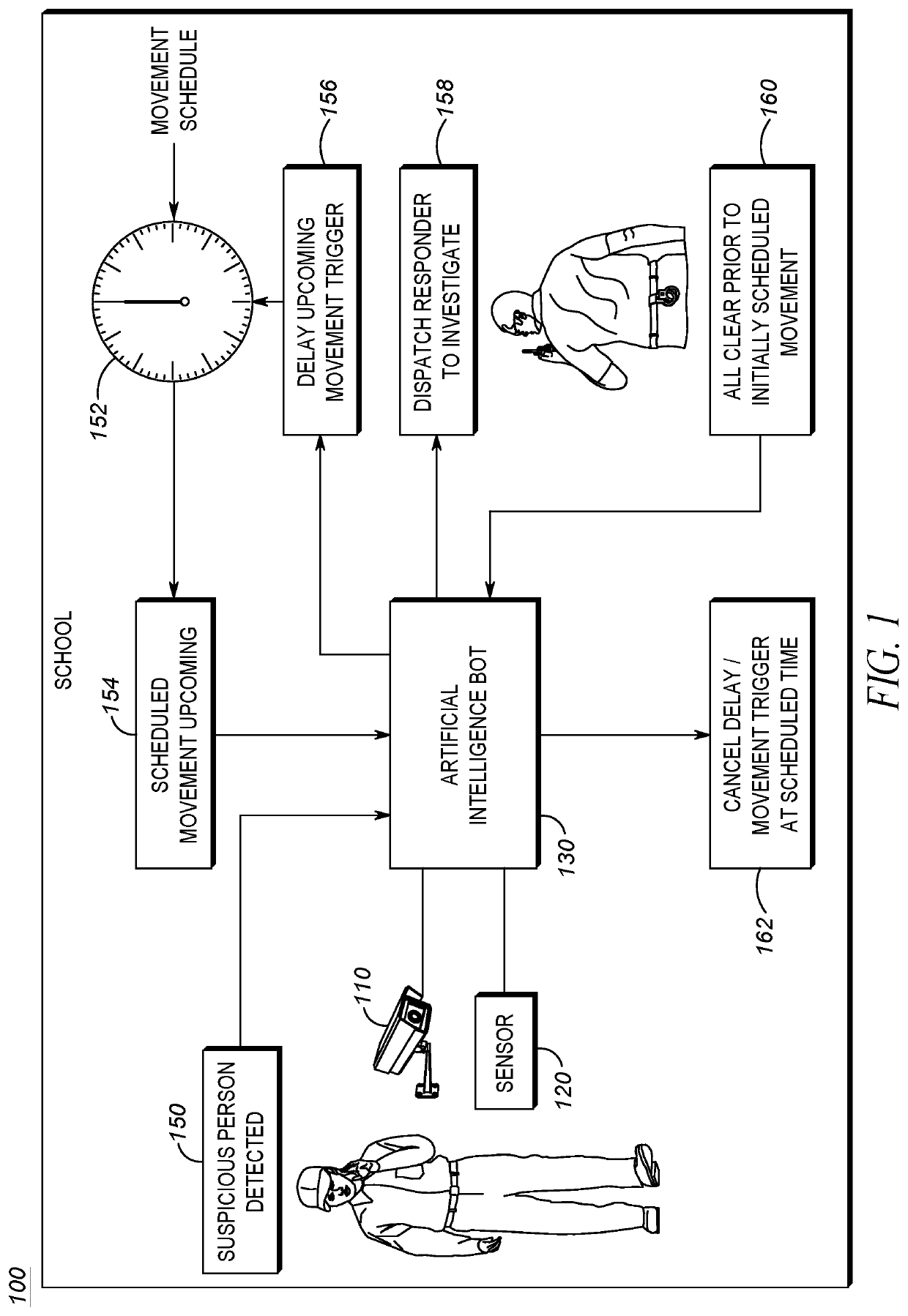
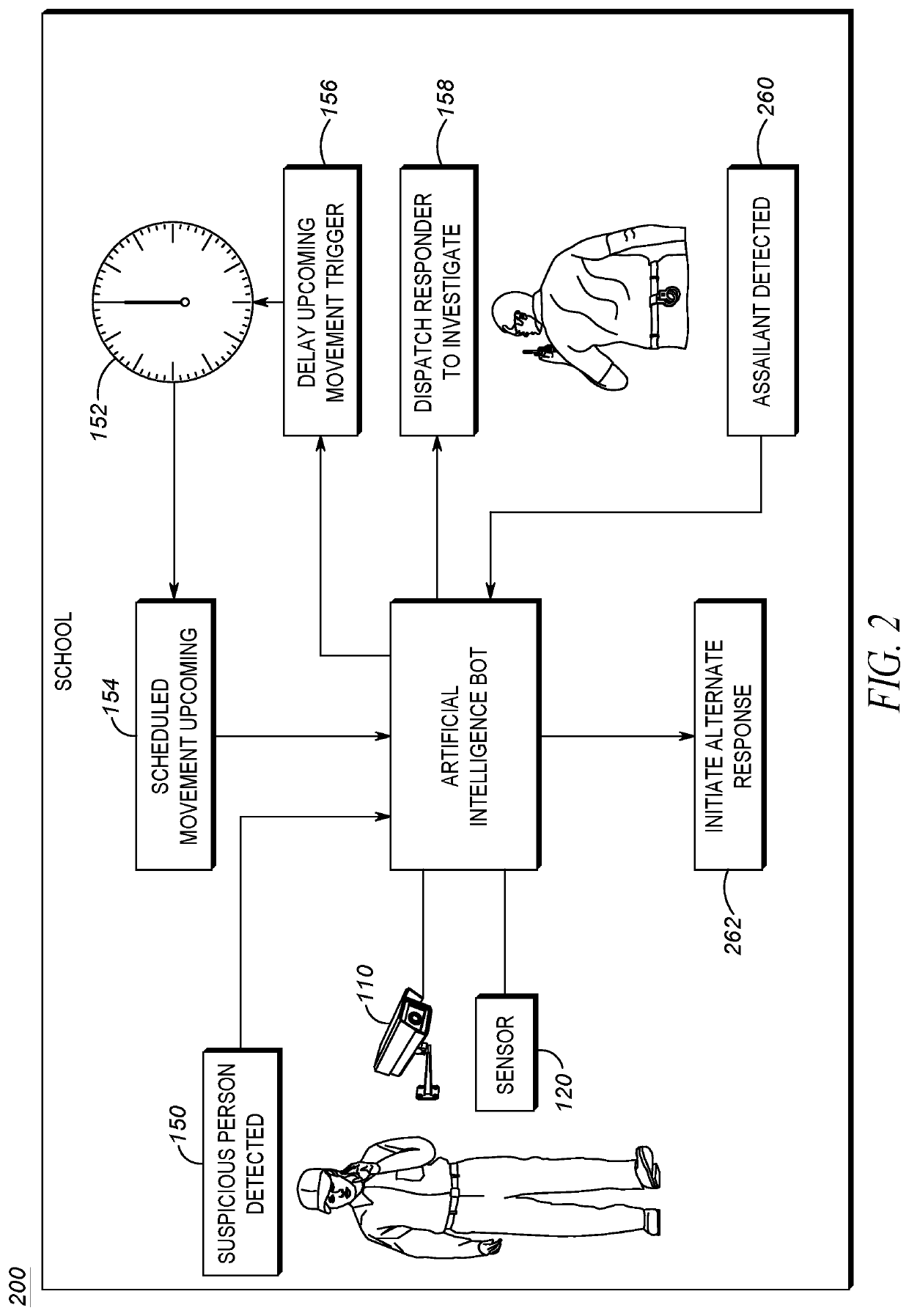
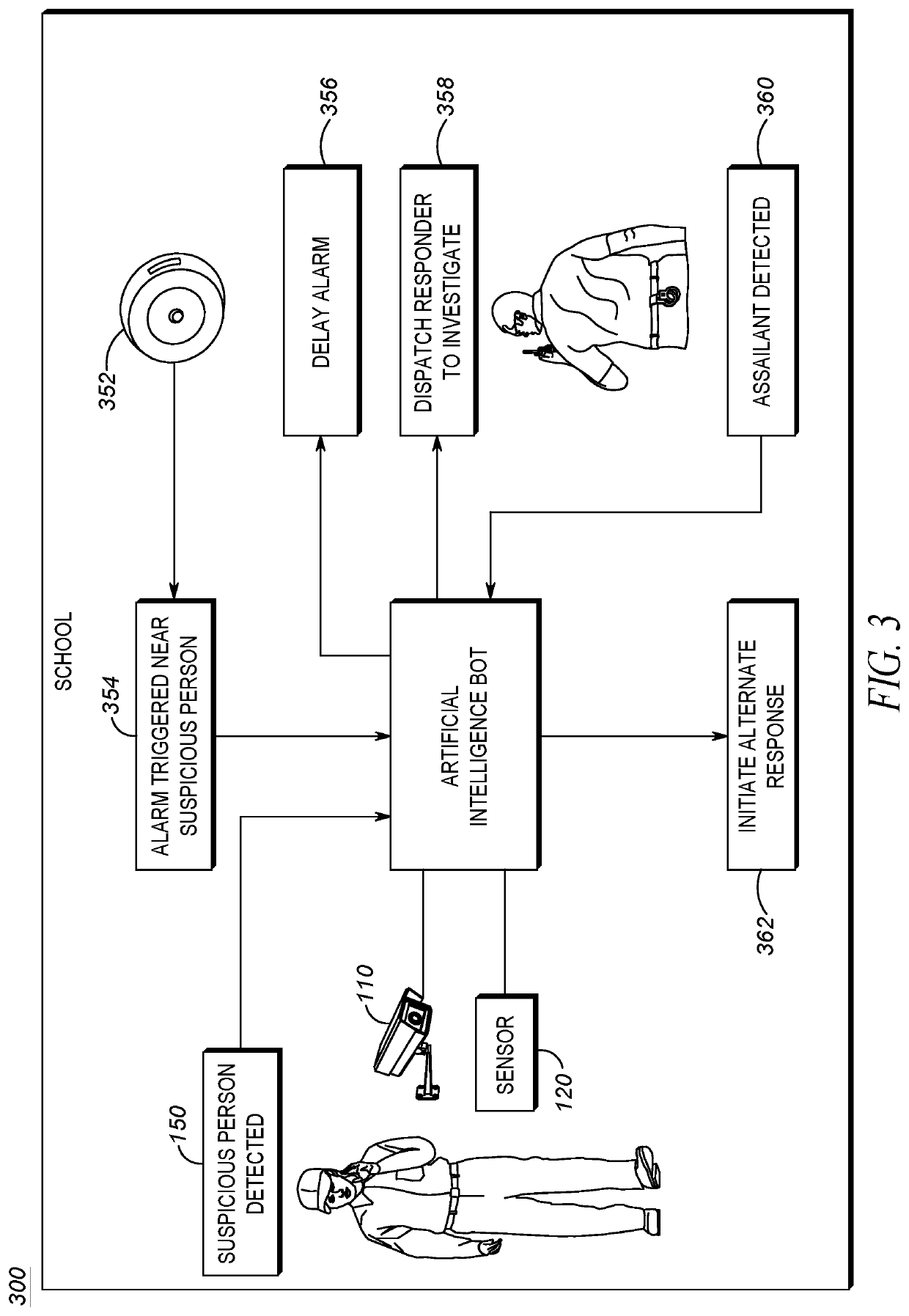
Techniques for delaying an alert based on suspicious activity detection are provided. An artificial intelligence system may detect suspicious behavior of a suspect within a vicinity of a school. A responder may be dispatched to investigate the suspect. An alert signal may be temporarily delayed. A time period for the delay may be associated with a time required for the responder to investigate and a severity of the alert signal. The delay may be canceled when the responder indicates the suspect behavior is not suspicious.
Owner:MOTOROLA SOLUTIONS INC
Network graph outlier detection for identifying suspicious behavior
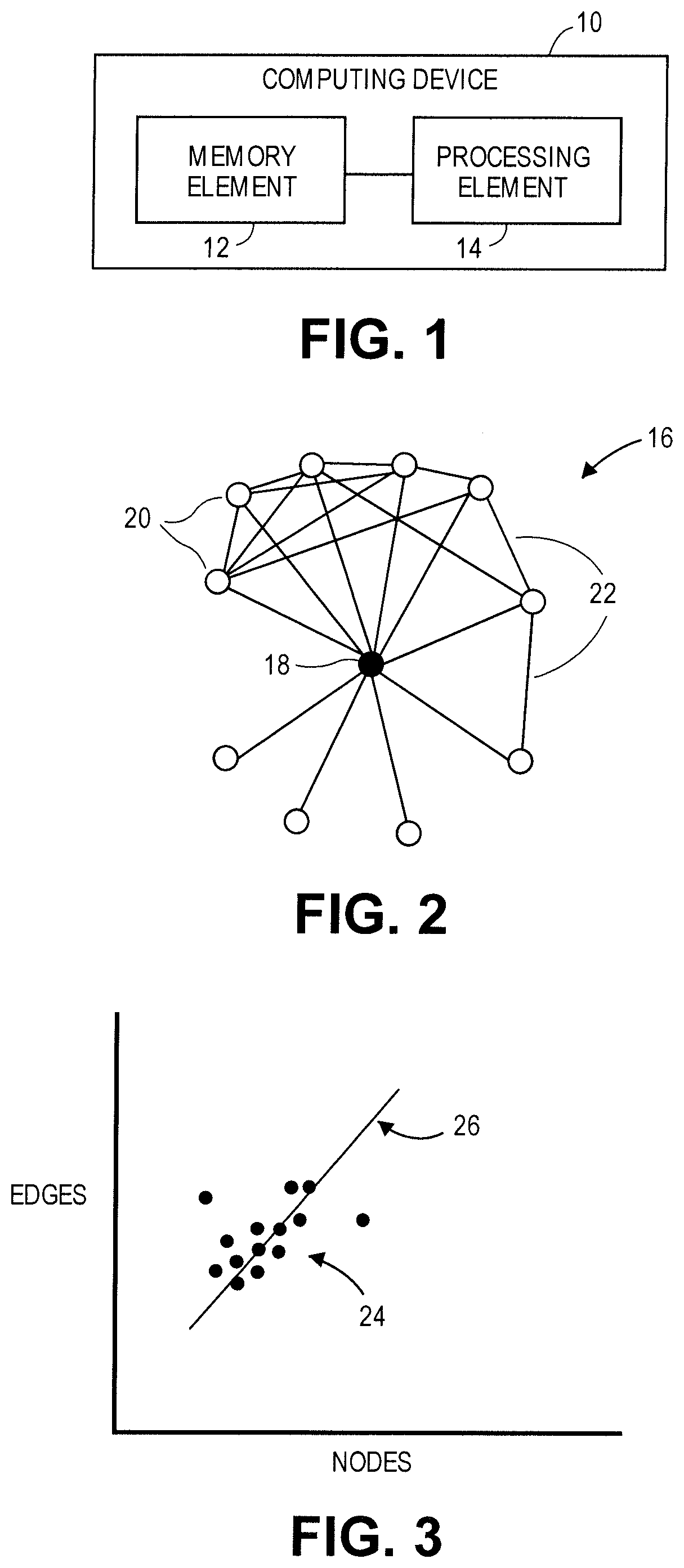
InactiveUS20210350468A1Facilitate identifying outlier behaviorFinanceSpecial data processing applicationsEgo networksEngineering
A computer-implemented method for detecting suspicious or fraudulent insurance claim filings may include receiving a list of individuals who file insurance claims; receiving a list of contacts for each individual; receiving information regarding relationships between the contacts; forming a plurality of ego networks that each include a central hub, a plurality of nodes, and a plurality of edges; determining a number of nodes for each ego network; determining a number edges for each ego network; forming a plurality of data points from the numbers of nodes and the numbers of edges; and calculating a distance of each data point from a predetermined normal relationship function to facilitate identifying outliers that warrant investigation or may be associated with insurance claim buildup.
Owner:STATE FARM MUTUAL AUTOMOBILE INSURANCE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com