Method and device for detecting malicious behavior of webpage
A behavior and webpage technology, applied in the field of detecting malicious behavior of webpages, can solve the problems of high identification costs, automatic pop-up windows, and error-prone interception, etc., to improve accuracy and reliability, improve efficiency and accuracy, avoid Effects of malicious behavior
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The following will clearly and completely describe the technical solutions in the embodiments of the present application with reference to the drawings in the embodiments of the present application. Obviously, the described embodiments are part of the embodiments of the present application, not all of them.
[0038] For ease of understanding, an application scenario of the embodiment of the present application is briefly introduced first.
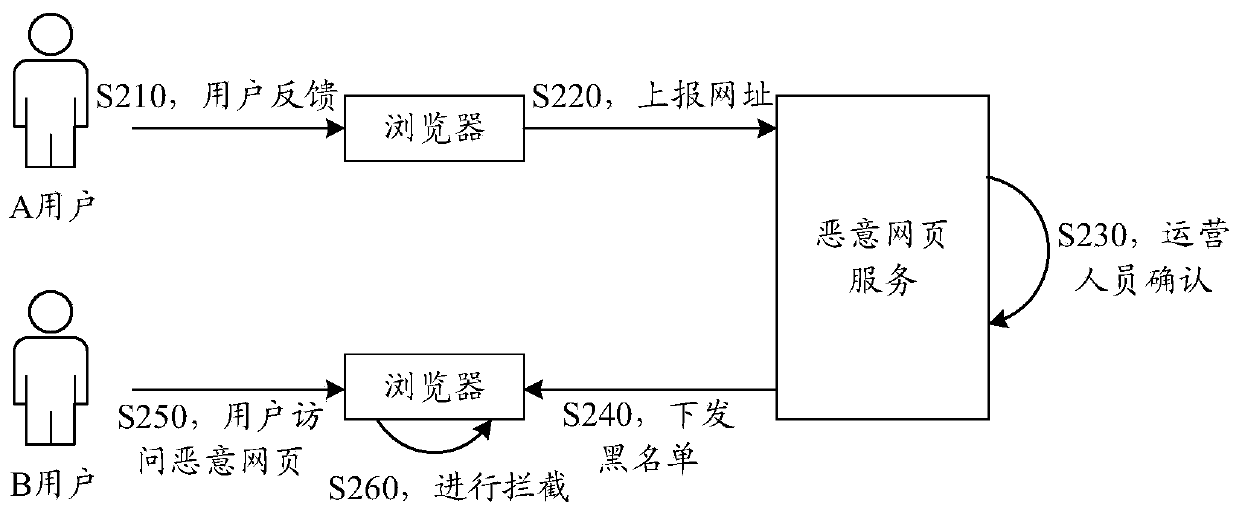
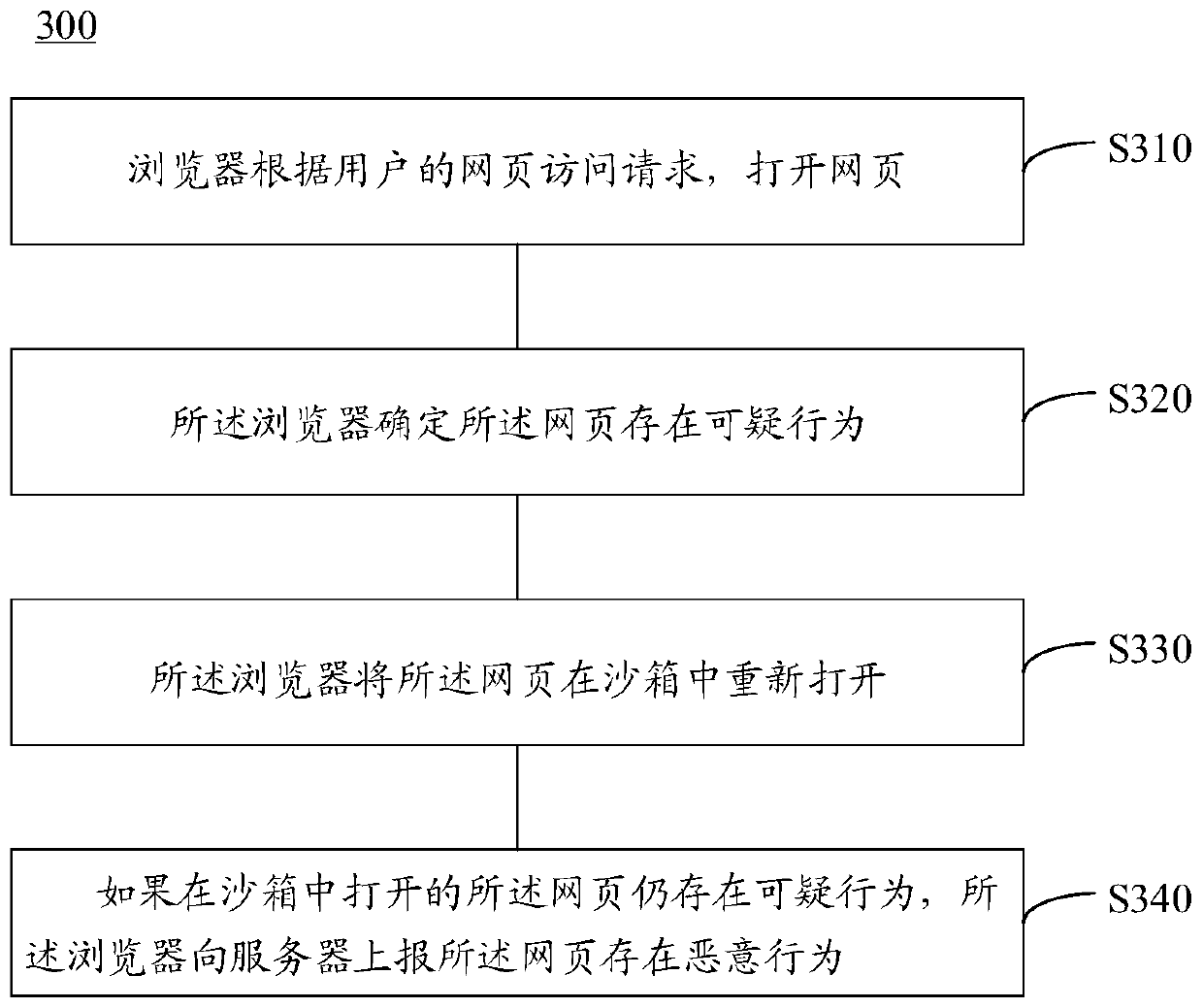
[0039]A browser is an application program for retrieving and displaying Internet information resources, which can be web pages, pictures, audio and video or other content. When a user uses a browser application to browse a webpage, the browser creates an independent window view for the webpage that the user browses. Inside this window view, the browser is responsible for the network request, page rendering, and page interaction response operations that the user needs to browse the webpage. In addition to the user actively opening the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com