Big data video retrieval method and device, computer equipment and storage medium
A big data and video technology, applied in the computer field, can solve the problem that personnel cannot obtain it in time, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
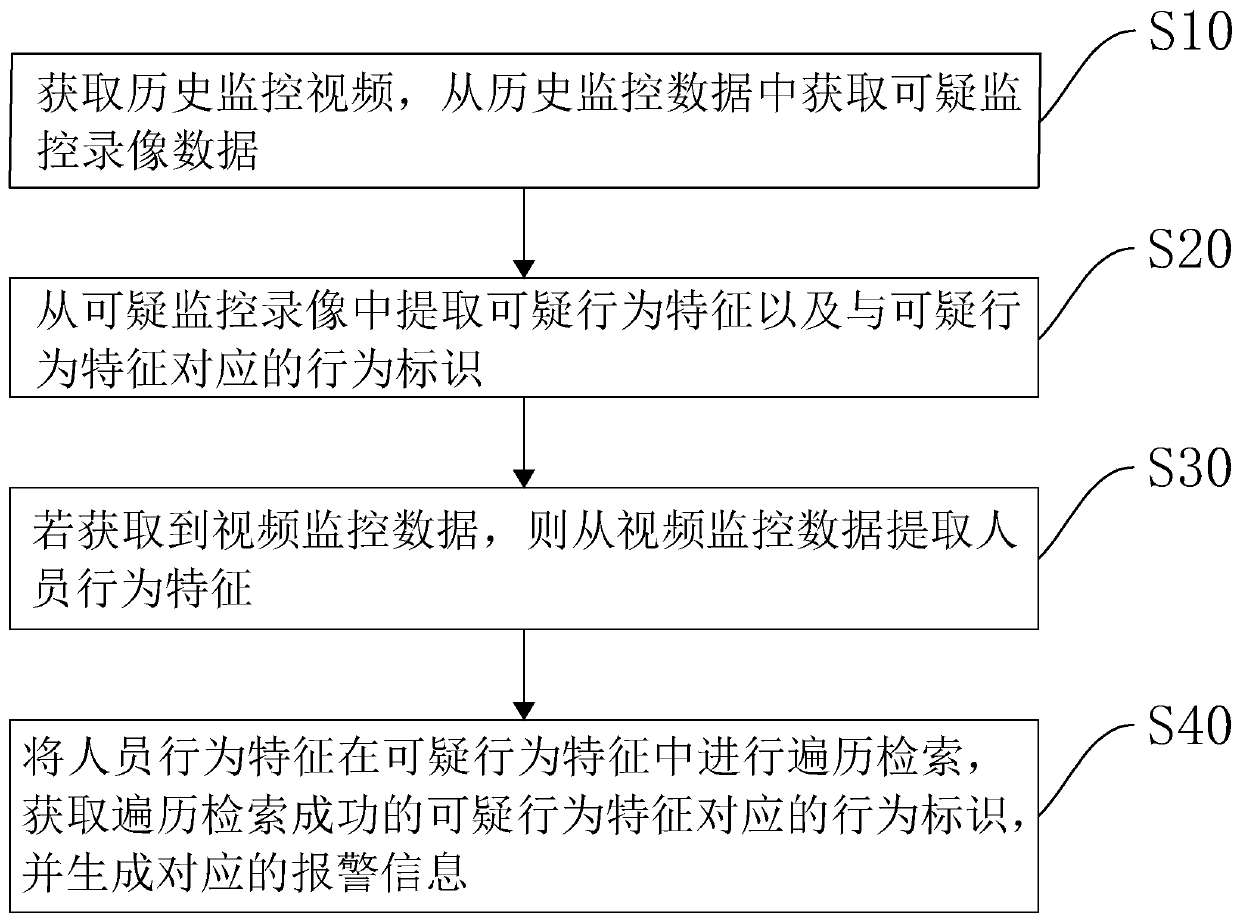
[0055] In one embodiment, as figure 1 As shown, the present invention discloses a large data video retrieval method, which specifically includes the following steps:
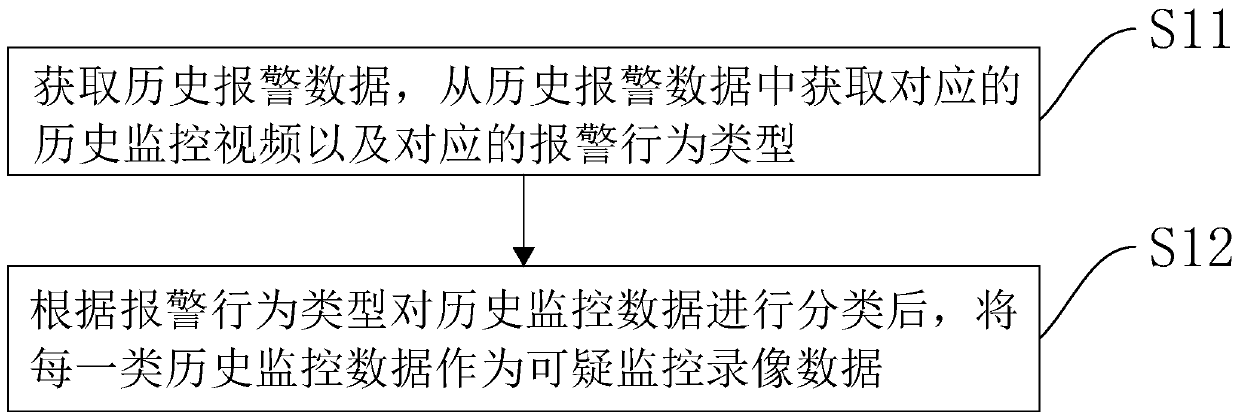
[0056] S10: Obtain historical surveillance video, and obtain suspicious surveillance video data from historical surveillance data.
[0057] In this embodiment, the historical surveillance video refers to video data acquired by a surveillance device within a certain period of time in the past. Suspicious surveillance video data includes surveillance videos with suspicious behaviors in historical surveillance videos.
[0058] Specifically, the historical surveillance video is obtained from a corresponding big data platform stored in a database storing the historical surveillance video. Wherein, the historical surveillance video can be a public place that actually needs to be monitored, or can be added to the historical surveillance data in the public security system according to the security requirements of the ...
Embodiment 2
[0106] In one embodiment, a big data video retrieval device is provided, and the big data video retrieval device is in one-to-one correspondence with the big data video retrieval method in the above embodiments. Such as Figure 6 As shown, the big data video retrieval device includes a historical video data acquisition module 10 , a suspicious feature extraction module 20 , a behavioral feature extraction module 30 and a retrieval alarm module 40 . The detailed description of each functional module is as follows:
[0107] Historical video data acquisition module 10, used to obtain historical surveillance video, obtain suspicious surveillance video data from historical surveillance data;
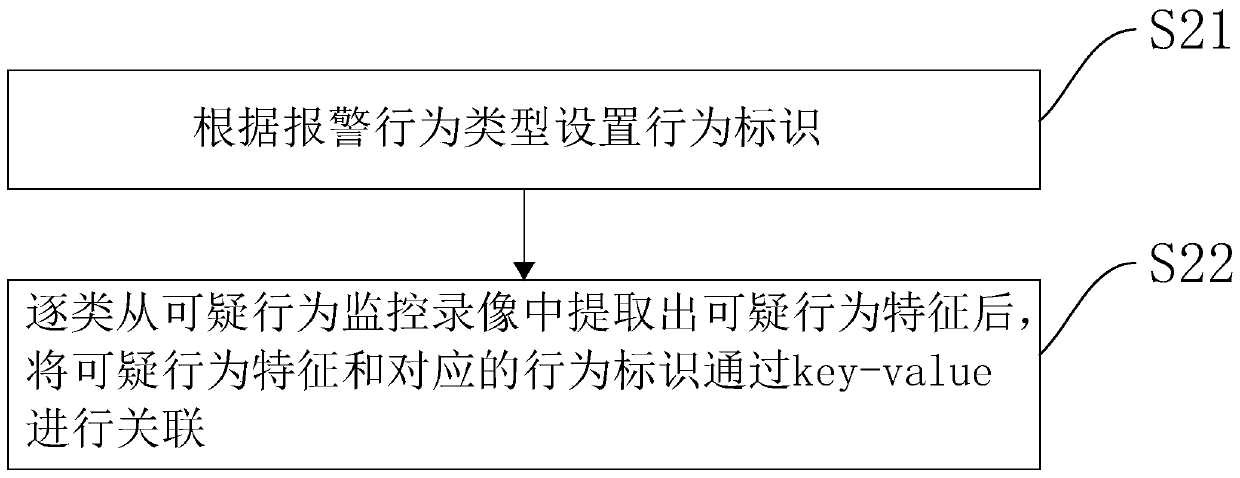
[0108] Suspicious feature extraction module 20, is used for extracting suspicious behavior feature and the corresponding behavior identification with suspicious behavior feature from suspicious monitoring video;
[0109] Behavior feature extraction module 30, if obtain video surveillance da...
Embodiment 3
[0128] In one embodiment, a computer device is provided, the computer device may be a server, and its internal structure diagram may be as follows Figure 7 shown. The computer device includes a processor, memory, network interface and database connected by a system bus. Wherein, the processor of the computer device is used to provide calculation and control capabilities. The memory of the computer device includes a non-volatile storage medium and an internal memory. The non-volatile storage medium stores an operating system, computer programs and databases. The internal memory provides an environment for the operation of the operating system and computer programs in the non-volatile storage medium. The database of the computer equipment is used to store historical monitoring data, suspicious behavior data and behavior identifiers corresponding to the suspicious behavior data. The network interface of the computer device is used to communicate with an external terminal via...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com