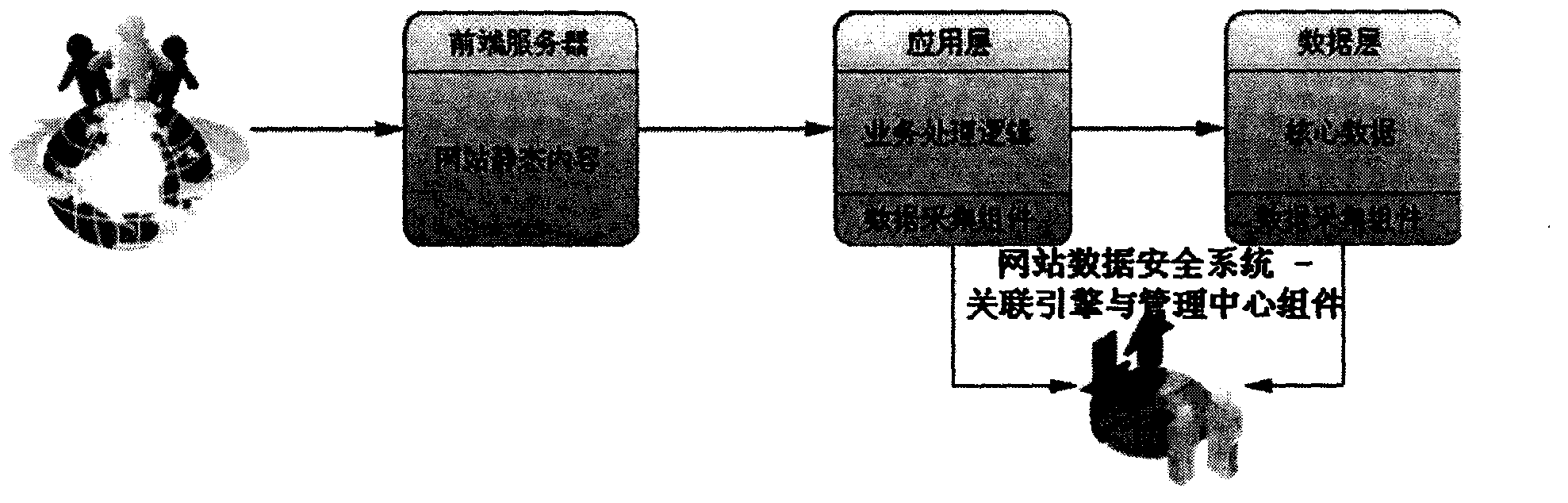
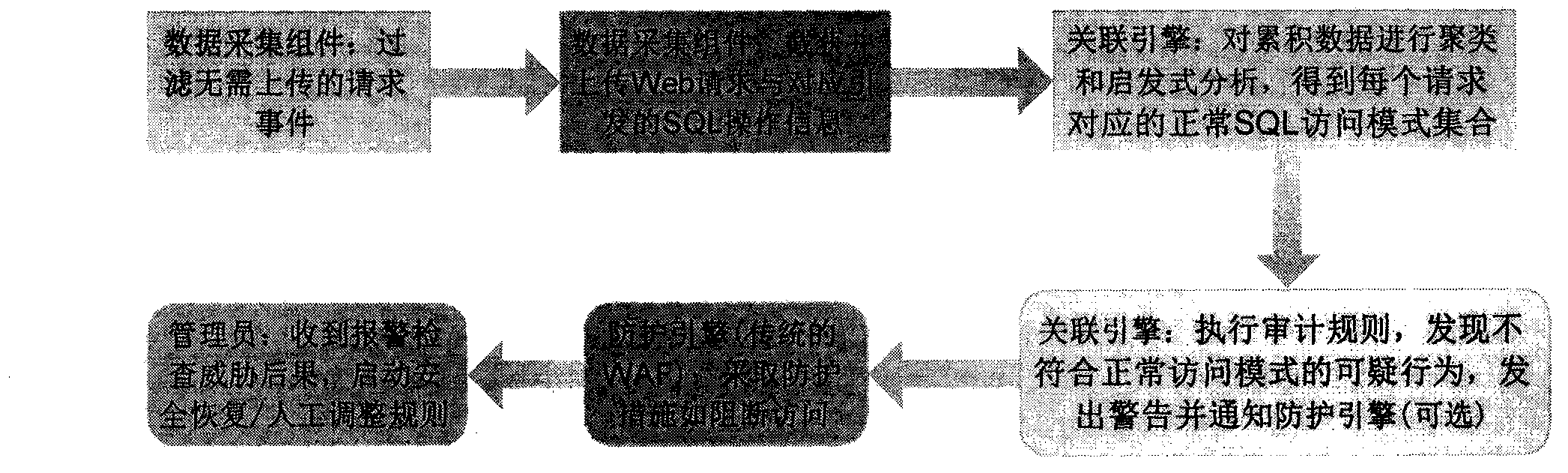
Website data security system based on association analysis of database activity and web access
A technology for databases and websites, which can be used in other database retrieval and computing redundancy for data error detection, digital data protection, etc., and can solve the problem of being unable to know whether the website has been attacked or invaded.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0014] The specific implementation of this system is as follows;
[0015] 1. Deploy the data acquisition component of the system of the present invention in the same network area where the application layer of the website is located, including deploying the plug-in module on the Web server where the application layer is located. The plug-in should implement the following functions: For the mainstream web site application layer based on J2EE / PHP, intercept the identification information that forwards the URL request to a background processing entry, and record all the processing threads during the entire processing period. The SQL operation to invoke. The overall component should realize the following data collection function: record and upload the information intercepted at the network layer and the information obtained directly from the log on the Web service (such as Apache / Tomcat) to the correlation engine. The meta information used for association includes: Web request an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com