An image privacy protection method and system
A privacy protection and privacy technology, applied in the computer field, can solve problems such as affecting information transmission, unauthorized users cannot view non-private parts of images, increase storage space and transmission bandwidth, etc., to reduce manual labor, save storage space and transmission The effect of bandwidth and flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
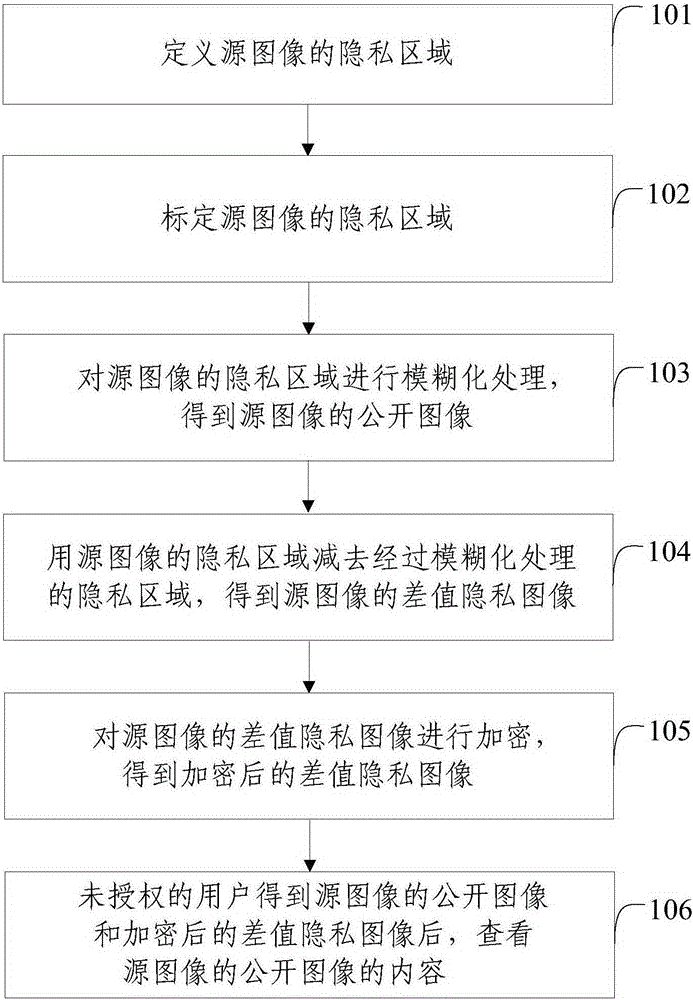
[0044] The embodiment of the present invention proposes an image privacy protection method, such as figure 1 As shown, the method includes the following steps:
[0045] Step 101: Define the privacy area of the source image.
[0046] Step 102: Mark the privacy area of the source image.
[0047] Step 103: Perform blurring processing on the private area of the source image to obtain a public image of the source image.
[0048] Step 104: Subtracting the blurred privacy area from the privacy area of the source image to obtain a differential privacy image of the source image.
[0049] Step 105: Encrypt the differential private image of the source image to obtain an encrypted differential private image.
[0050] Step 106: After obtaining the public image of the source image and the encrypted differential private image, the unauthorized user checks the content of the public image of the source image.
[0051] It can be seen that in the embodiment of the present invention, ...
Embodiment 2
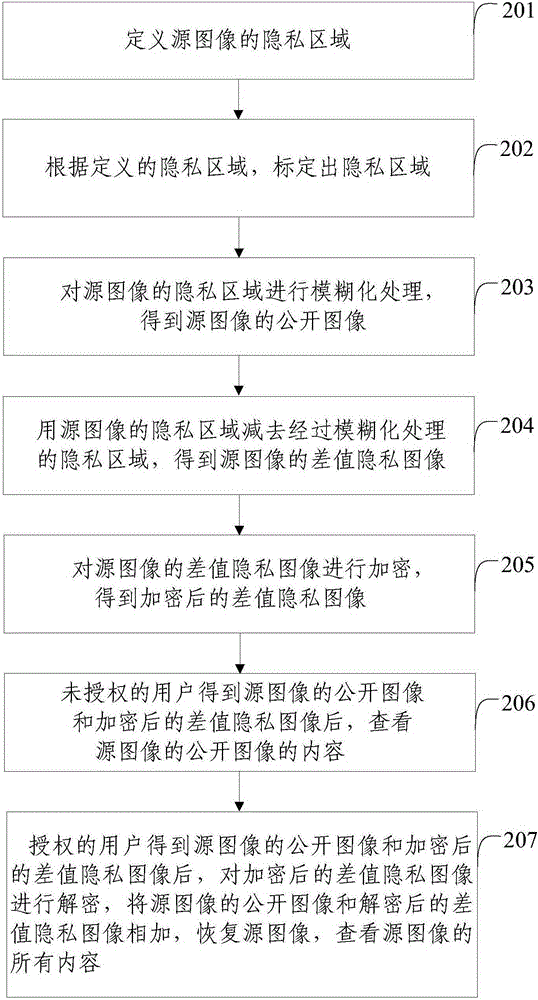
[0056] The implementation process of a preferred embodiment of the present invention will be described in more detail below through a specific example. see figure 2 , including the following steps:
[0057]Step 201: Define the privacy area of the source image.
[0058] In this step, the owner of the source image can define one or more specific entities in the source image and / or one or more types of entities in the source image as privacy areas. For example, define a certain person's face and / or a certain person's name as a privacy area, or define all people's faces and / or all texts as a privacy area, and define a certain person's face and all texts as a privacy area.
[0059] Step 202: Mark out the privacy area according to the defined privacy area.
[0060] In this step, according to the defined privacy area, the corresponding image recognition technology is used to automatically mark the privacy area, or according to the defined privacy area, the privacy area is manua...
Embodiment 3
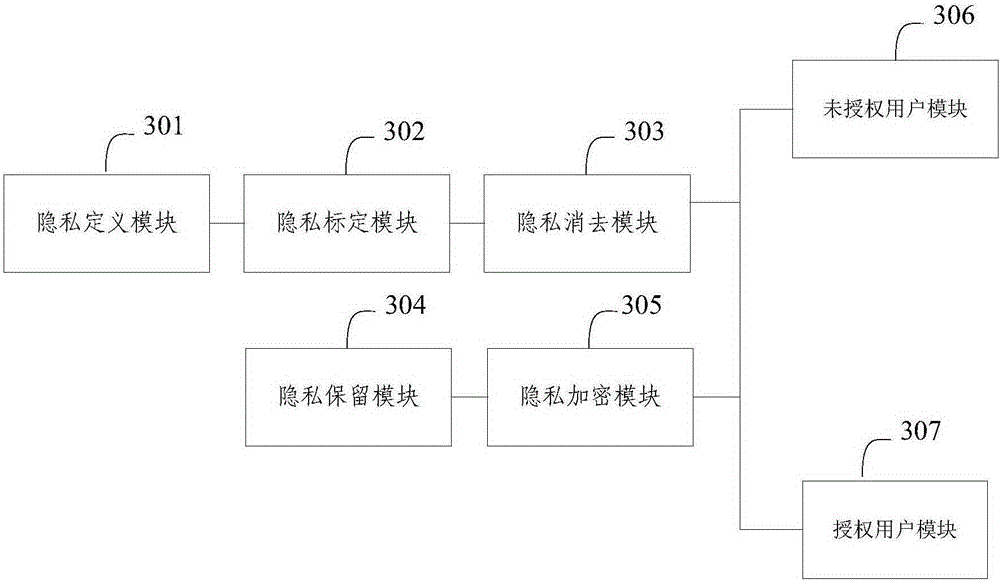
[0071] The embodiment of the present invention proposes an image privacy protection system, such as image 3 As shown, the system includes:
[0072] The privacy definition module 301 is used to define the privacy area of the source image, and send the defined privacy area of the source image to the privacy marking module 302;
[0073] The privacy marking module 302 is used to mark the privacy area of the source image, and send the marked privacy area of the source image to the privacy elimination module 303;
[0074] The privacy elimination module 303 is used to blur the privacy area of the source image, obtain the public image of the source image, and send it to the unauthorized user module 306 and the authorized user module 307;
[0075] The privacy preservation module 304 is used to subtract the privacy area of the fuzzy processing from the privacy area of the source image to obtain a difference value privacy image of the source image, and send the difference...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com