Data set encryption pre-processing method
A data set and data concentration technology, applied in digital transmission systems, secure communication devices, electrical components, etc., can solve problems such as narrow applicability and inapplicability of large data sets, and achieve the effect of saving encryption time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] Below in conjunction with accompanying drawing and embodiment the present invention will be further described:
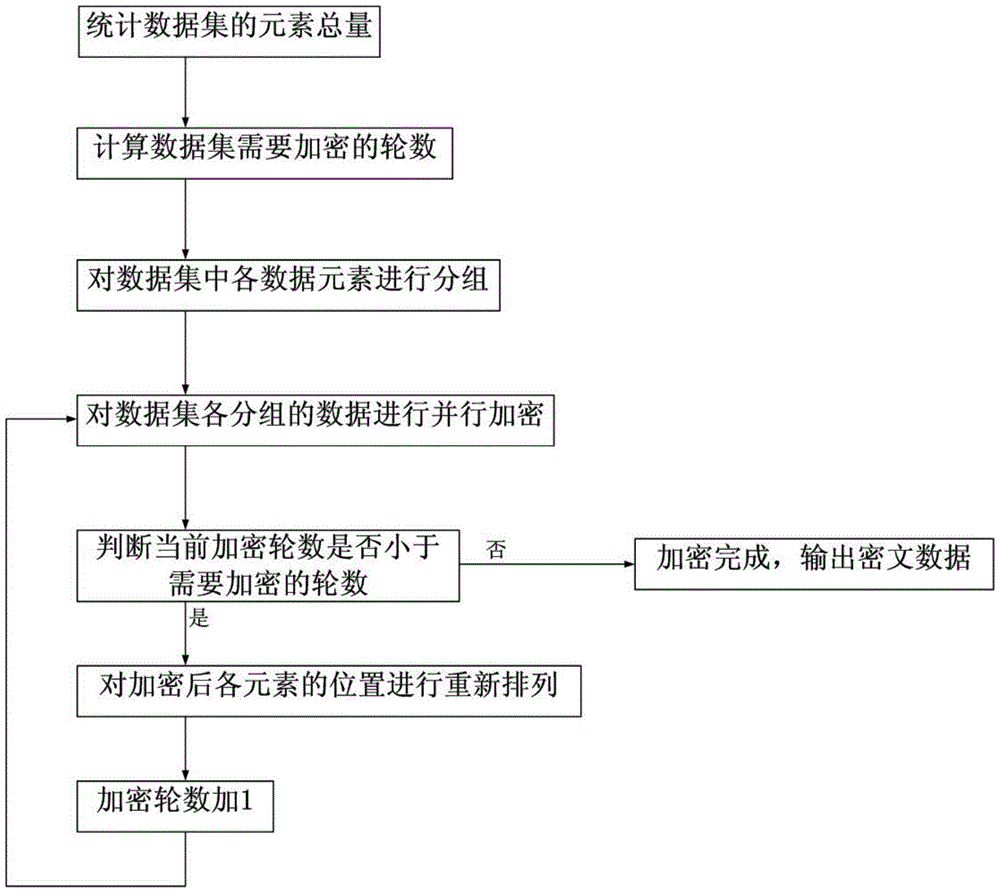
[0025] Such as figure 1 As shown, a data set encryption pre-processing method includes the following steps:
[0026] Step 1. The total number of elements N in the data set is counted, and N is a positive integer.
[0027] Step 2: Calculate the number of rounds that the data set needs to be encrypted.
[0028] Step 3, grouping each data element in the data set; it is carried out according to the following steps:
[0029] A1. The position of the data element in the data set is represented by an m-bit binary number, expressed as x m x m-1 …x 2 x 1 ; m is a positive integer, 2 m ≤Nm+1 ; x i Indicates the binary value represented by the i-th bit, i=1, 2, 3, ..., m.
[0030] A2. Group the data elements in the data set according to the grouping strategy;
[0031] The grouping of the data elements in the data set according to the grouping strategy is perfor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com