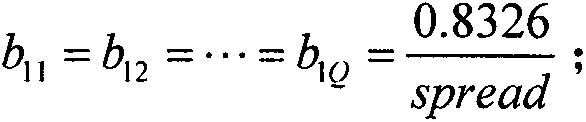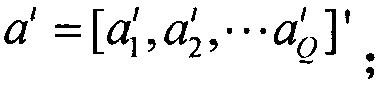Neural network-based intrusion detection algorithm for wireless sensor network
A network intrusion detection, wireless sensor technology, applied in wireless communication, network topology, electrical components, etc., can solve the problem of lack of research results in intrusion detection technology
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
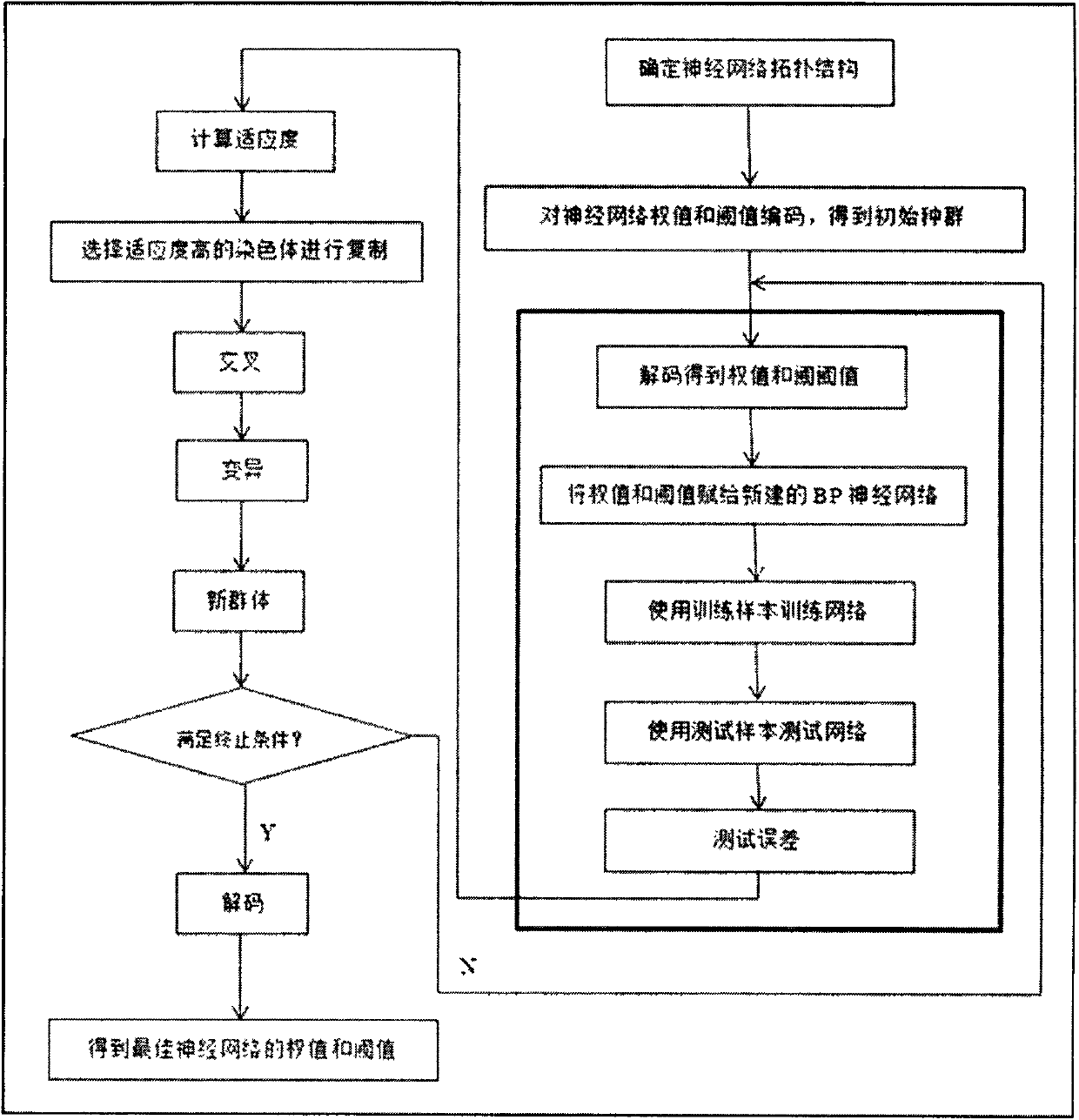
[0009] (1) A neural network-based wireless sensor network intrusion detection algorithm includes the following steps:
[0010] Preprocess the data;
[0011] Train the BP neural network;
[0012] Train the generalized neural network;
[0013] Improve and train the BP neural network.
[0014] (2) Preprocess the data as described in (1), and the main steps are as follows:
[0015] Step 1: Data Mapping. Each line of this data set is a record collected and processed by TCPdump, which contains 41 feature values and 1 attack type description. Each feature is separated by a comma, and finally the attack type is separated by a comma. is a standard CSV file. Due to the complex types of data, there are discrete types (such as protocol types TCP, UDP...) and continuous types (duration, number of packets sent, etc.), which need to be processed separately. First, data mapping is performed to map symbolic data to numerical data. For example, in the feature value, the second dimensio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com