Safety detection method and device
A detection method and security technology, applied in computer security devices, platform integrity maintenance, instruments, etc., can solve the problems of poor computer system security and stability, affecting system security and stability, and coarse security detection granularity. , to achieve the effect of ensuring security and stability, improving security detection efficiency, and improving security and stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
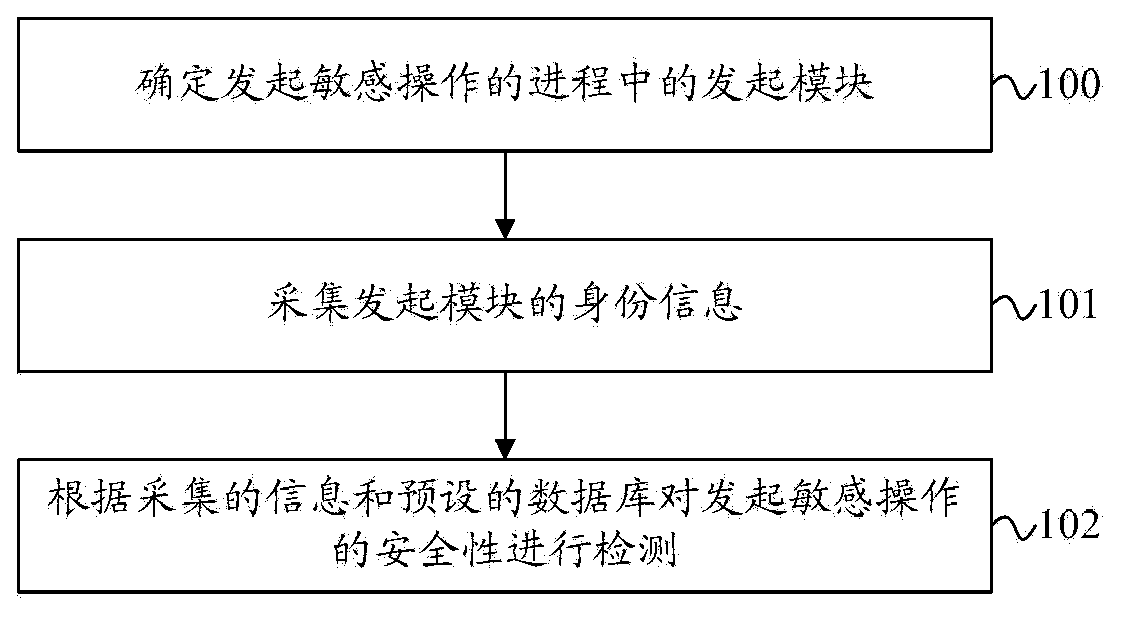
[0051] figure 1 It is a flow chart of the safety detection method provided by Embodiment 1 of the present invention. Such as figure 1 As shown, the security detection method of this embodiment may specifically include the following steps:
[0052]100. Determine the initiating module in the process of initiating the sensitive operation;
[0053] 101. Collect the identity information of the initiating module;
[0054] 102. Check the safety of initiating sensitive operations according to the collected information and the preset database.
[0055] For example, the sensitive operation in this embodiment may be driver loading, modification of system registry keys, or injection. Compared with the prior art, the technical solution of this embodiment can specifically determine the initiating module in the process that initiates the sensitive operation. Then collect the identity information of the initiating module, for example, the identity information of the initiating module may...
Embodiment 2
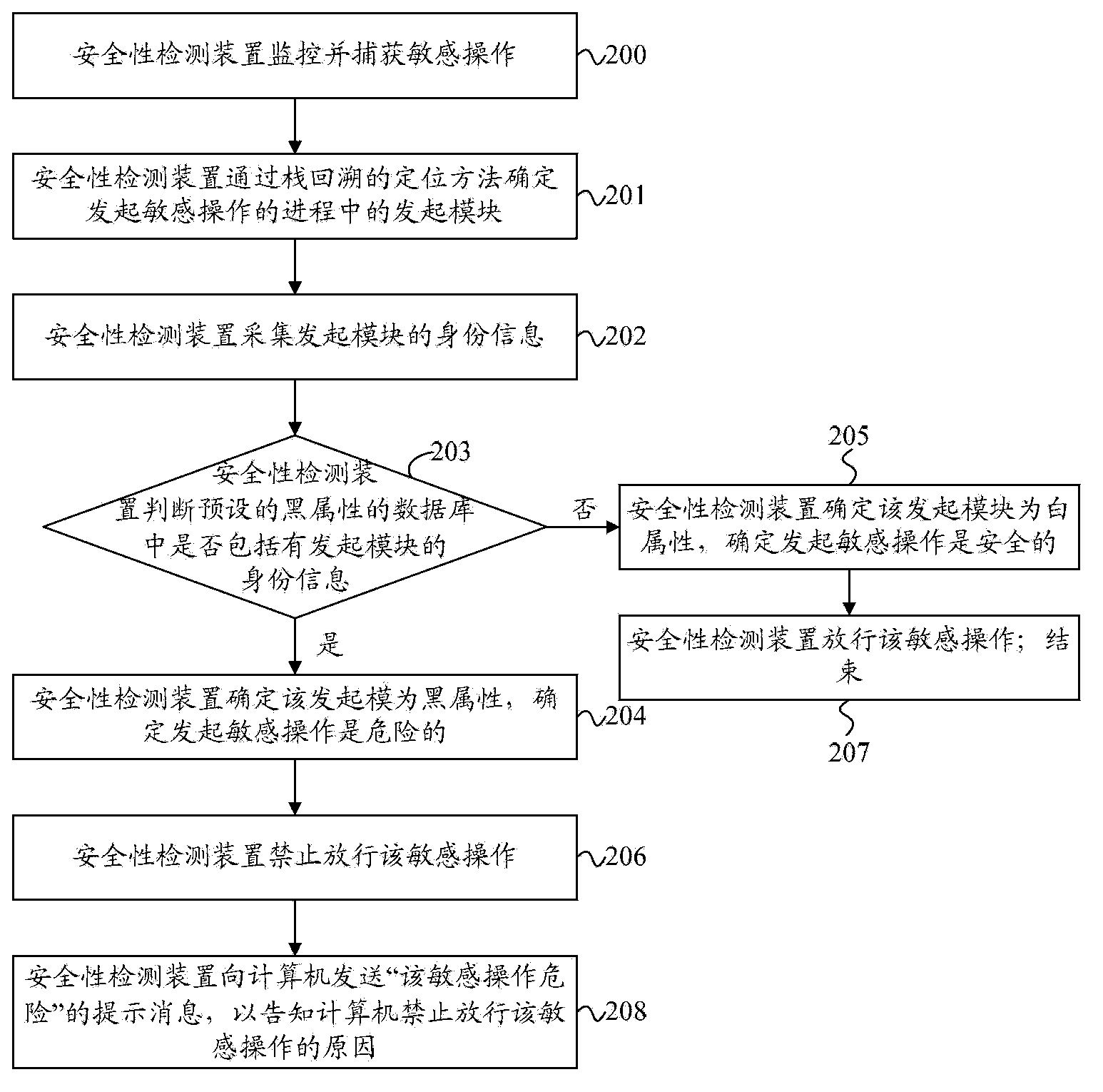
[0083] figure 2 It is a flow chart of the safety detection method provided by Embodiment 2 of the present invention. Such as figure 2 As shown, the security detection method of this embodiment may specifically include the following steps:
[0084] 200. The security detection device monitors and captures sensitive operations;
[0085] 201. The safety detection device determines the initiating module in the process of initiating the sensitive operation through the positioning method of stack backtracking;
[0086] 202. The security detection device collects the identity information of the initiating module;
[0087] 203. The safety detection device judges whether the identity information of the initiating module is included in the preset black attribute database, and if it is included, execute step 204; otherwise, when it is not included, execute step 205;
[0088] In this embodiment, the technical solution of the present invention is described by taking the preset database ...
Embodiment 3
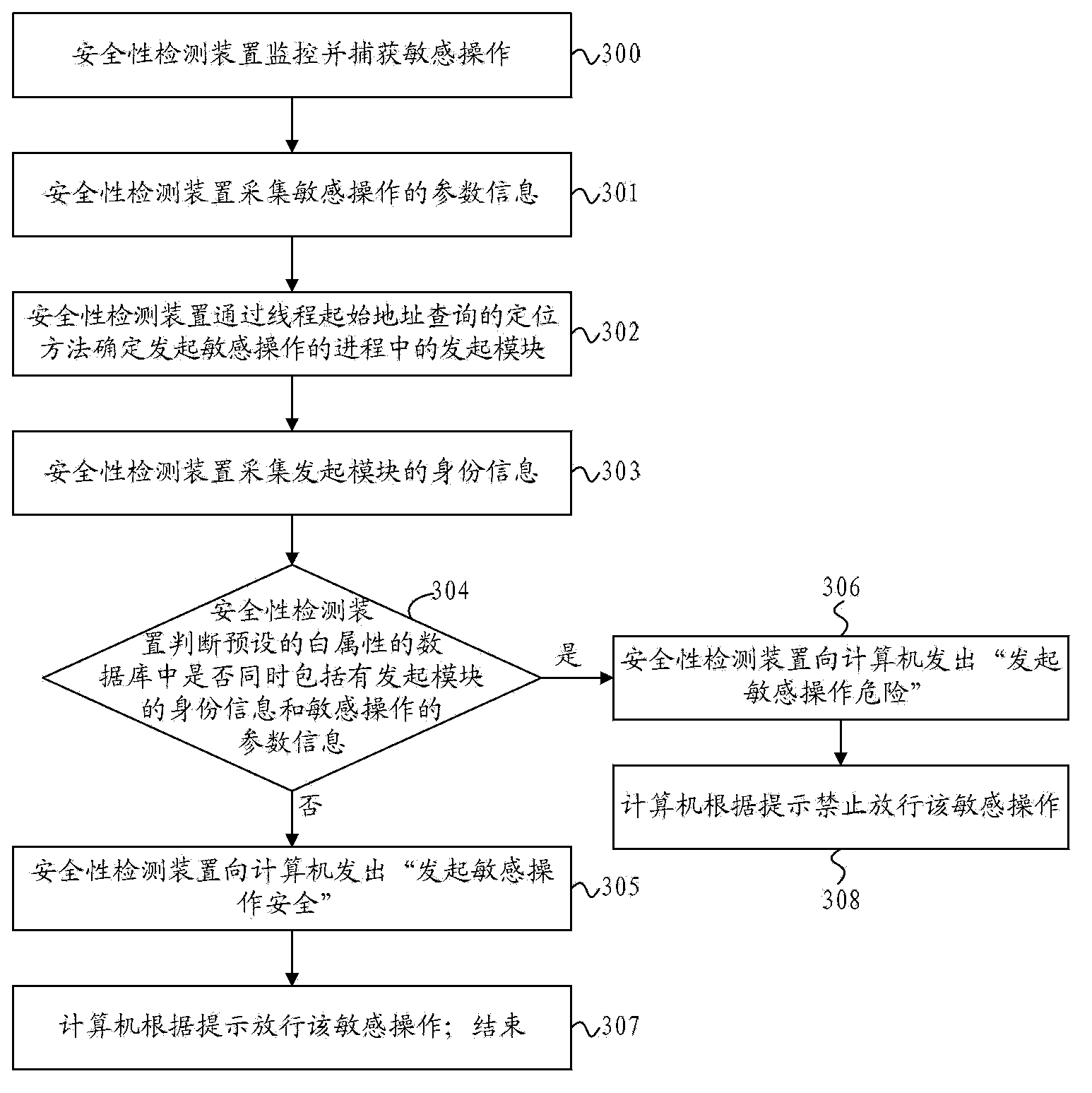
[0096] image 3 It is a flow chart of the safety detection method provided by Embodiment 3 of the present invention. Such as image 3 As shown, the security detection method of this embodiment may specifically include the following steps:
[0097] 300. The security detection device monitors and captures sensitive operations;
[0098] 301. The safety detection device collects parameter information of sensitive operations;
[0099] 302. The security detection device determines the initiating module in the process of initiating the sensitive operation through the location method of thread start address query;
[0100] 303. The security detection device collects the identity information of the initiating module;
[0101] 304. The safety detection device judges whether the preset white attribute database includes both the identity information of the initiating module and the parameter information of the sensitive operation, when the preset white attribute database includes both...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com