Data interception and conversion method and system
A technology of data interception and data packet, applied in the field of data interception and conversion and system, to achieve the effect of strong security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
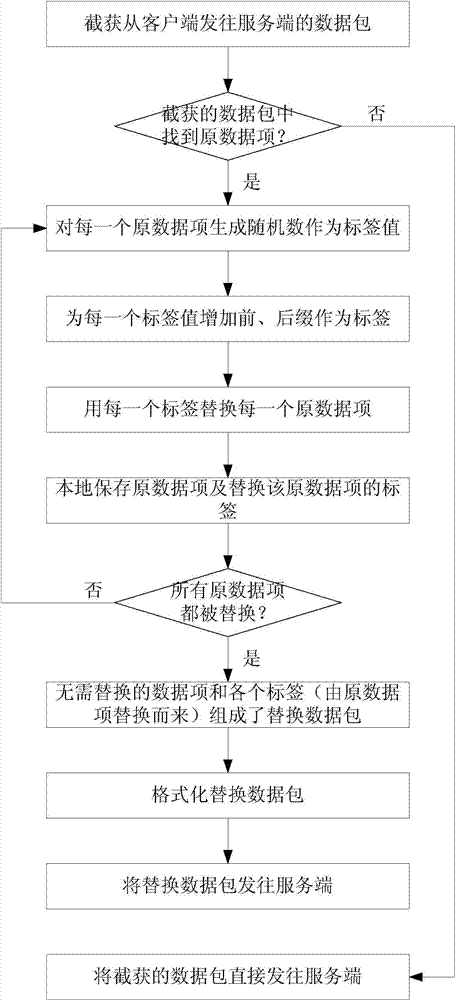
[0039] see figure 1 , the first embodiment of the method for intercepting and converting uplink data in the present application includes the following steps:
[0040] Step a1, intercepting the data packet sent from the client to the server;
[0041] Step a2, find the data item that needs to be replaced from the intercepted data packet, that is, the original data item; if no original data item is found, the intercepted data packet is directly sent to the server; if one or more original data items are found item, go to step a3;
[0042] Step a3, for each original data item, generate a random number as the label value; add a prefix and a suffix to each label value respectively to form a label; replace each original data item with each label, in Save the original data item locally and replace the label of the original data item;
[0043] The intercepted data packet usually consists of two parts: the data item that needs to be replaced (the original data item) and the data item ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com