Multi-permission distribution method based on SAN storage system
A technology of storage system and authority distribution, which is applied in the direction of transmission system, digital data protection, internal/peripheral computer component protection, etc. It can solve the problems of super administrator misoperation and false identification, so as to ensure safety, controllability and avoid safety Hidden danger, practical effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] A method for assigning multiple permissions based on a SAN storage system of the present invention will be described in detail below in conjunction with the accompanying drawings.
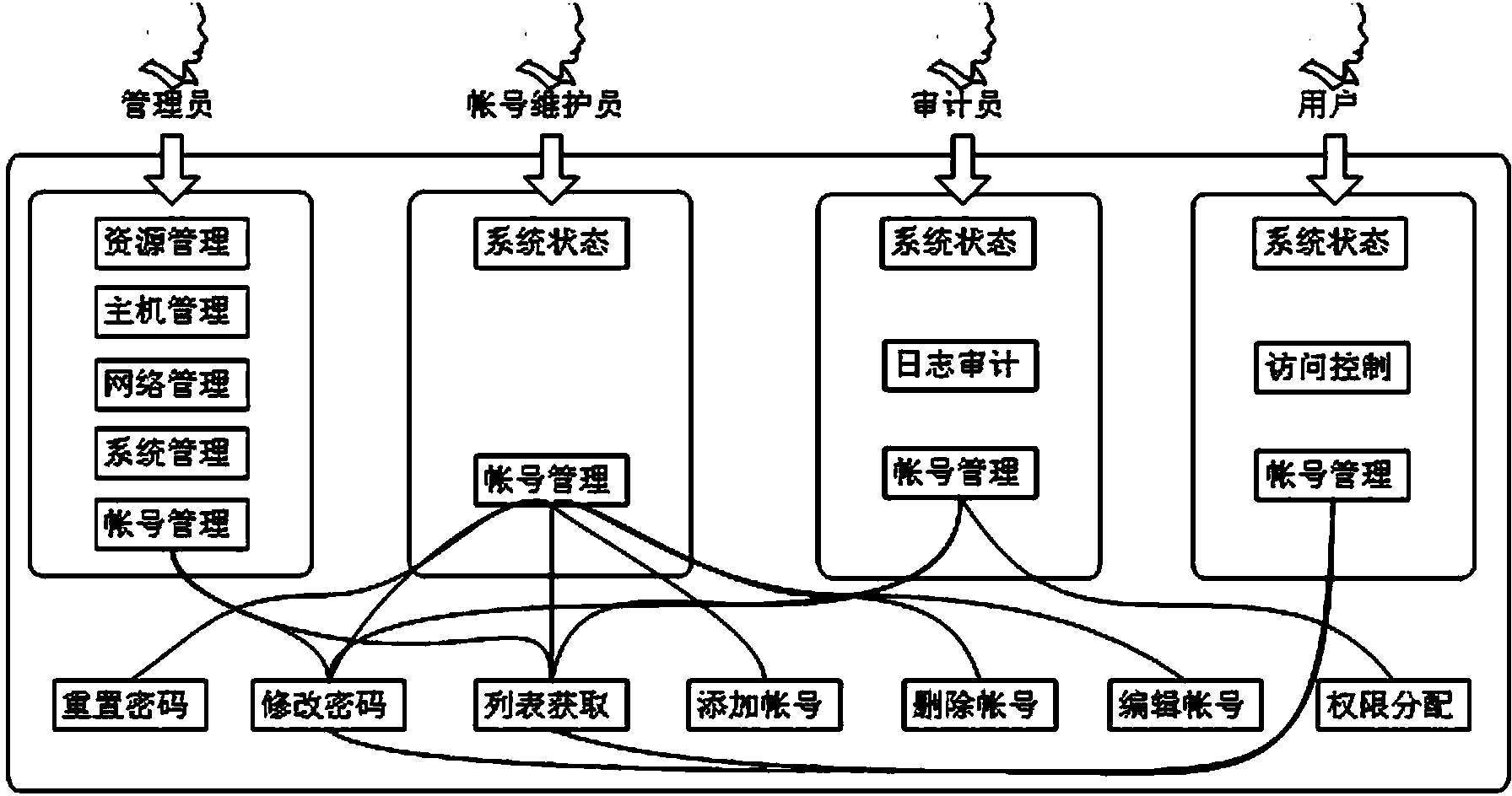
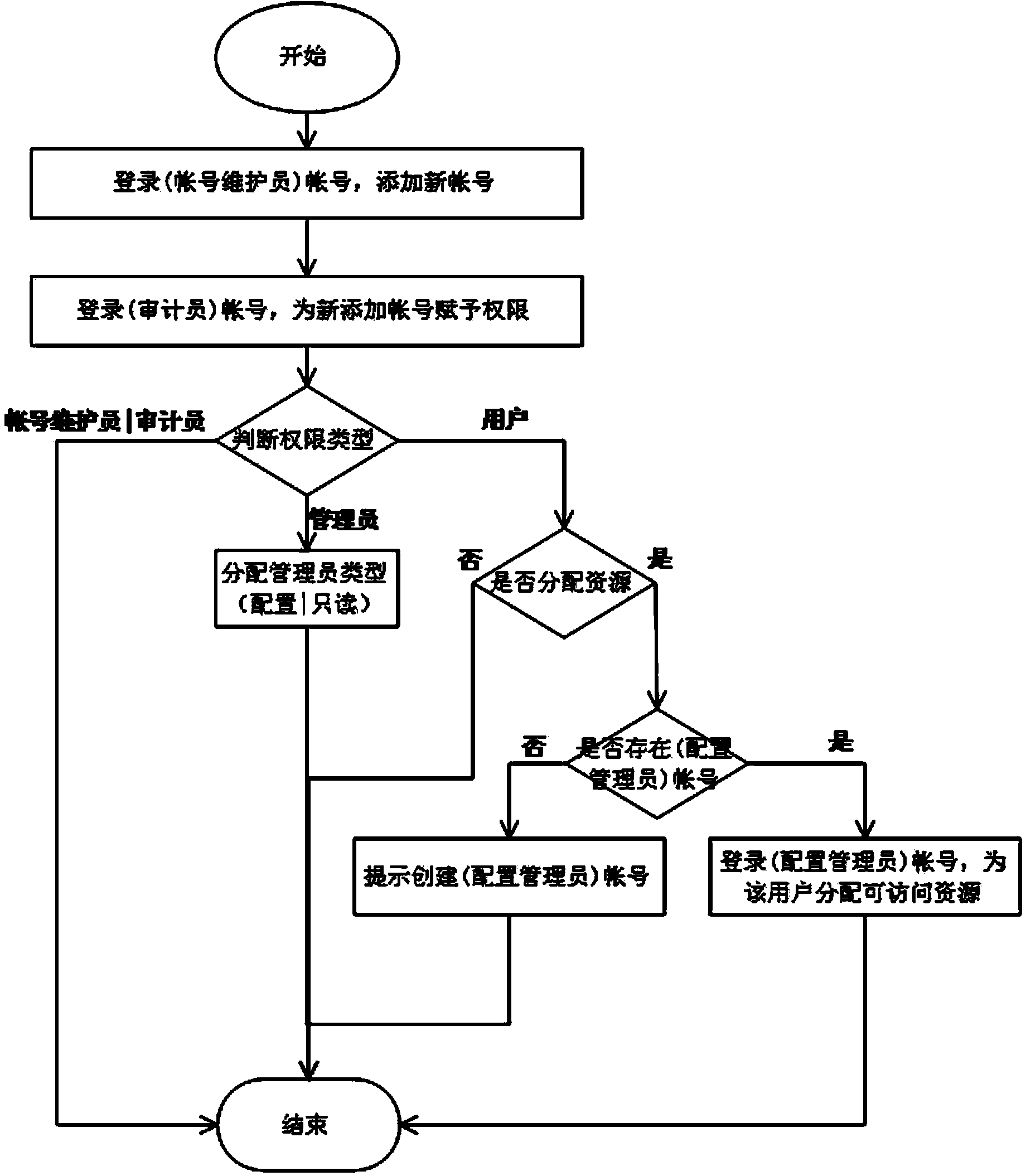
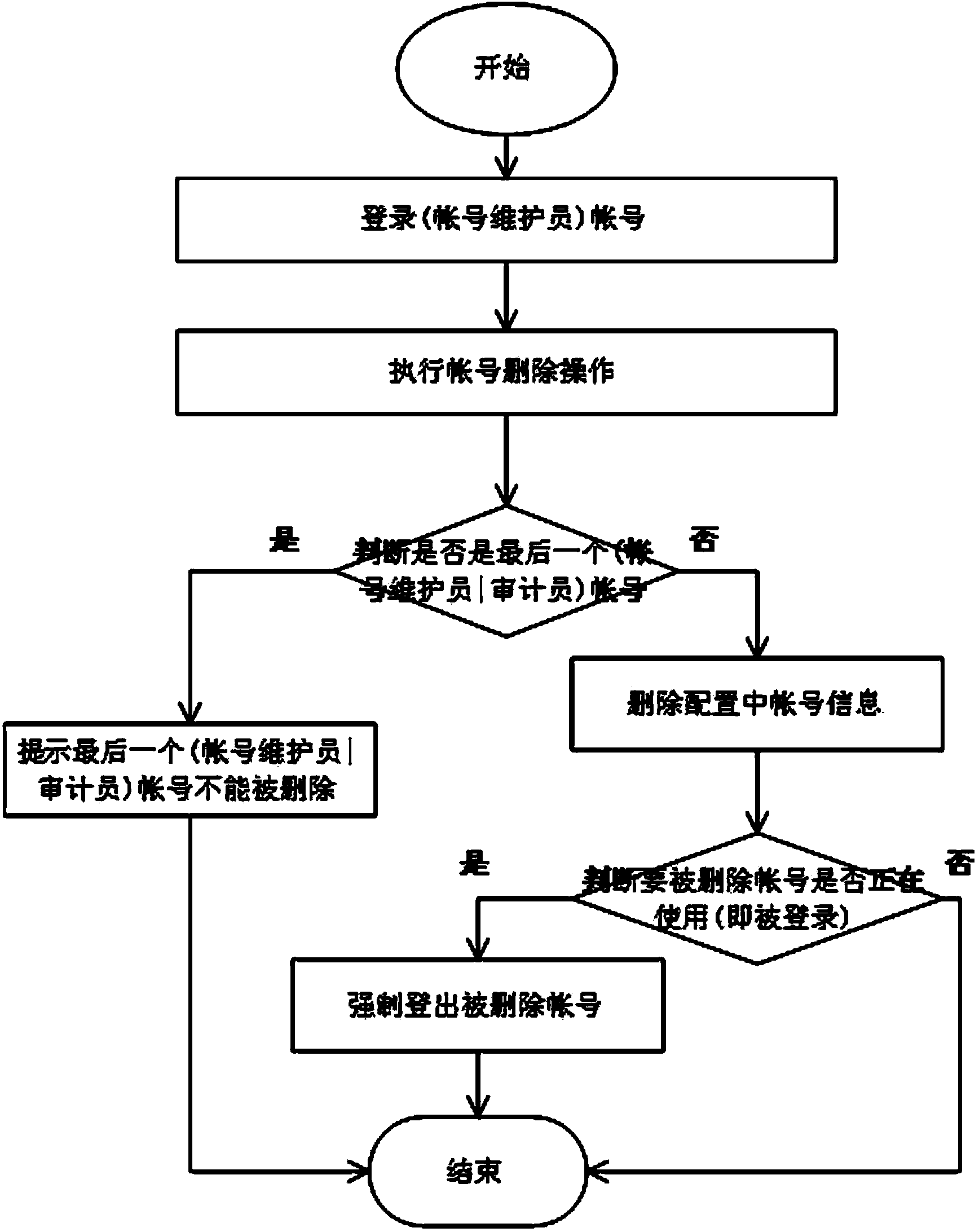
[0037] as attached figure 1 As shown, a method for assigning multiple permissions based on a SAN storage system, the specific assignment process is:
[0038] Assign multiple roles, that is, set up four roles of account maintainer, auditor, administrator, and user in system management tasks and assign corresponding permissions and management scopes. The four roles are mutually restricted, and the storage system is implemented according to specific security principles. Separation of permissions. The security principle refers to the principle of least privilege. The above-mentioned separation of permissions includes two parts: management permissions and data access permissions to the storage system. Full control of the system.
[0039] The authority of the account maintainer includes two part...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com