Authentication system and method therefor
A technology of authentication system and authentication request, applied in the direction of transmission system, payment system structure, security device, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
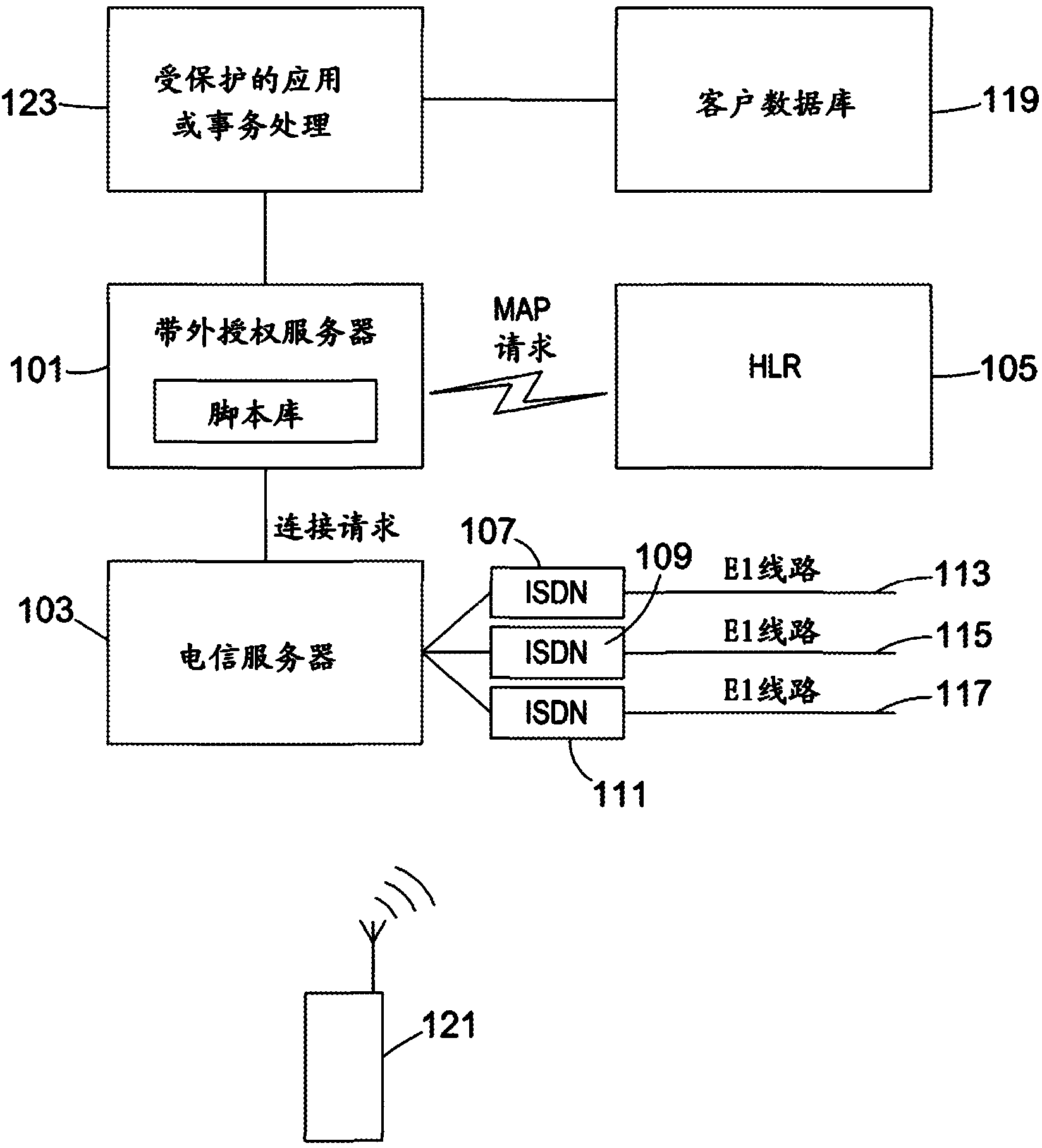
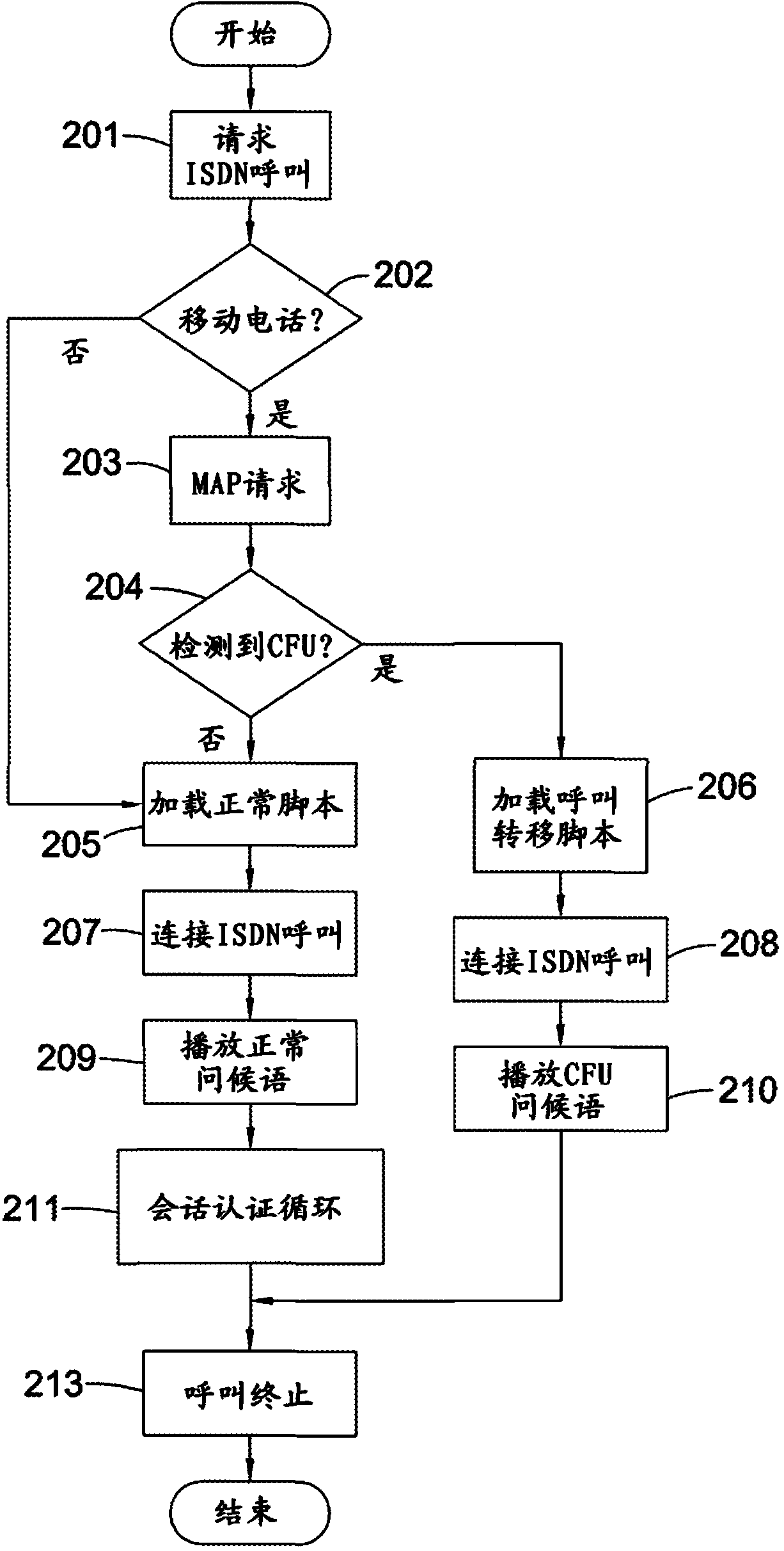
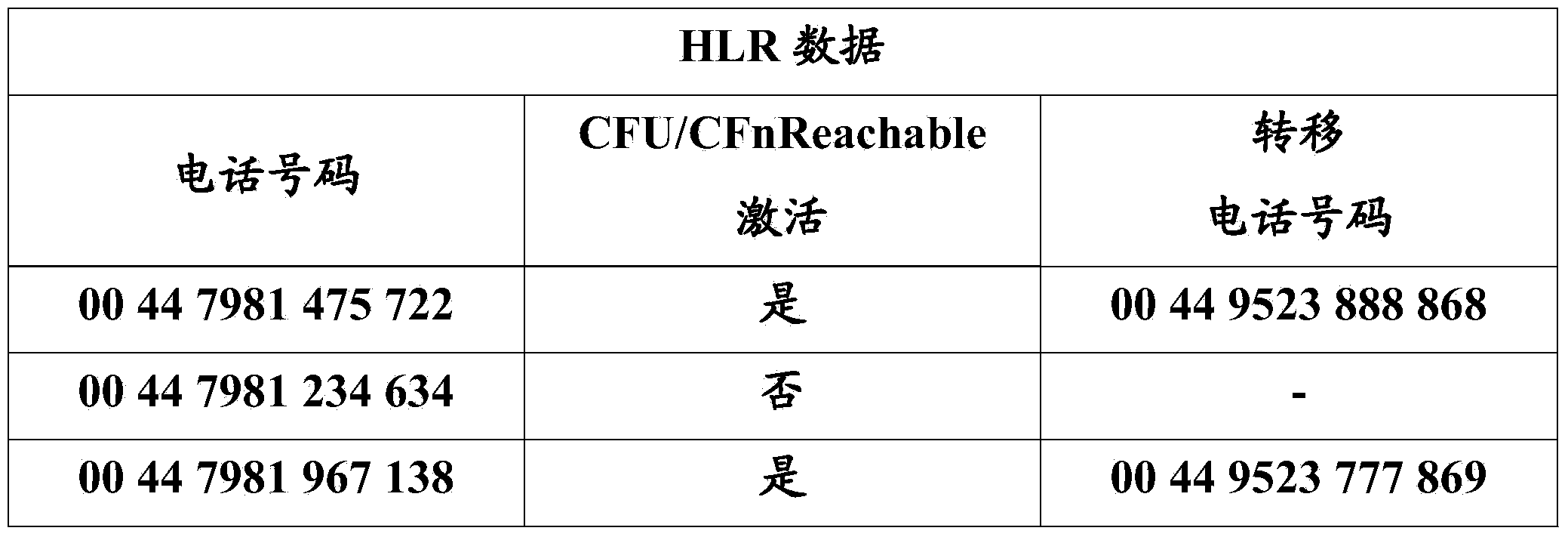
[0017] now refer to figure 1 , figure 1 is a schematic diagram of the main components of the authentication system implementing the present invention. The system includes an authentication server or an authorization server or both an authentication server and an authorization server 101 communicatively coupled to a telecommunications server 103 . The system may include a remote home location register (HLR) 105 operable to detect the unconditional call forwarding status of one or more mobile phones. An HLR database is maintained by each mobile network provider and includes information about that provider's permanent and visiting subscribers. The home location register may be stored in memory such as random access memory or other memory. Typically the home location register is stored on a server. HLR 105 is communicatively coupled to authorization server 101 . This is usually accomplished by wireless means, but wired connections, such as dedicated fiber optic links, may als...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com