Method and system for identifying malicious web sites
A malicious URL and URL technology, applied in the computer field, can solve the problem of low efficiency in identifying malicious URLs, and achieve the effect of reducing the number of times of calculation and identification, reducing the number of times, and improving efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] Now surfing the Internet with computers and mobile phones has become a common behavior. As long as you surf the Internet, you will come into contact with websites. Some websites spread some bad information, and even steal visitors’ personal information, spread viruses and damage the system, etc. We put such URLs are called malicious URLs. The following embodiments disclose a method and system for identifying malicious web addresses. For ease of understanding, descriptions are now made in conjunction with mobile phone browser browsing web addresses.
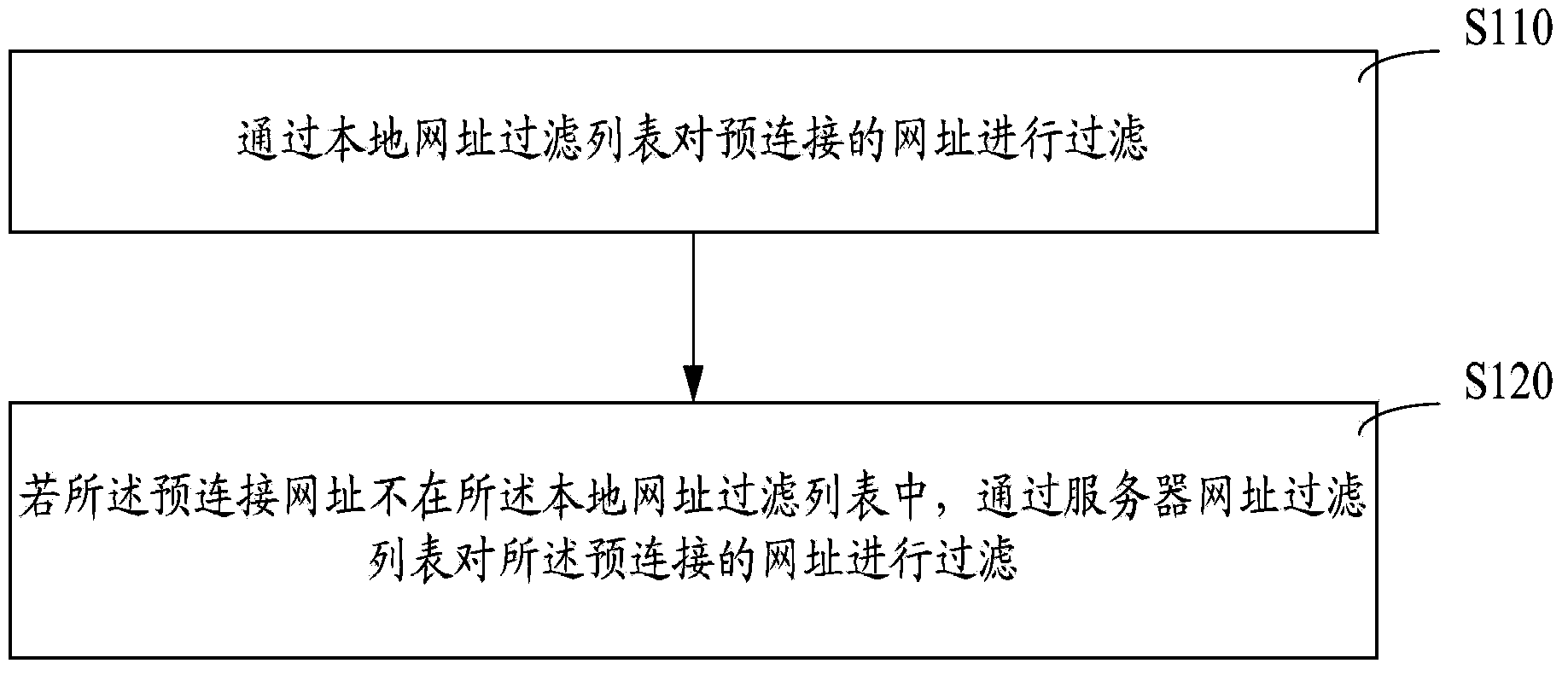
[0022] Such as figure 1 As shown, a method for identifying malicious URLs includes steps:
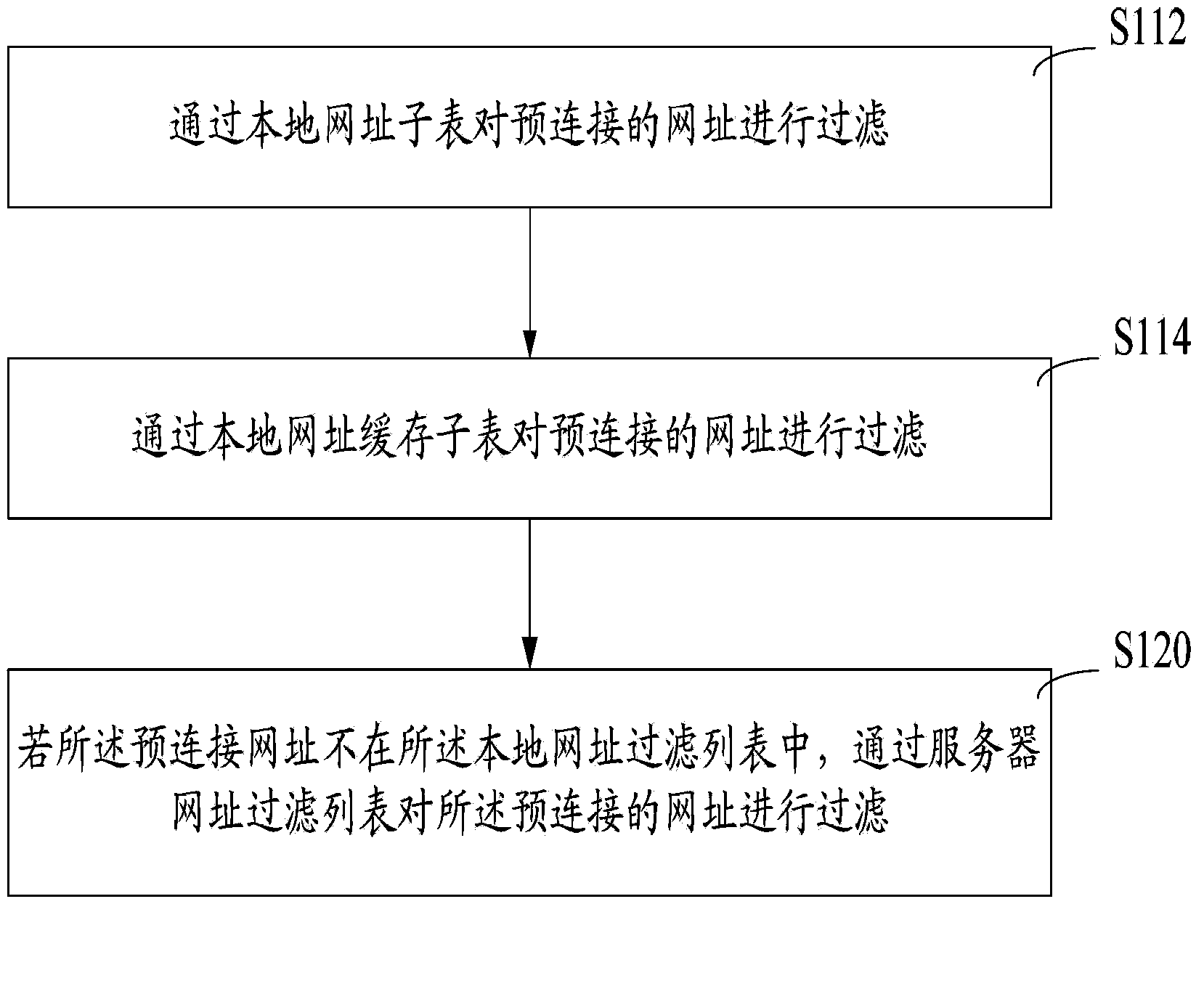
[0023] Step S110, filter the pre-connected URL through the local URL filtering list: if the pre-connected URL is a URL allowed in the local URL filtering list, allow the pre-connected URL to connect, if the pre-connected URL When filtering the prohibited URLs in the local URL list, the pre-connected URLs are blocked. The URLs adde...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com