Secure search processing system and secure search processing method
A processing system and security technology, applied in the field of security search processing system, can solve cumbersome problems and achieve the effect of reducing risk, reducing time and energy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 approach
[0028] 1. System configuration
[0029] Embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
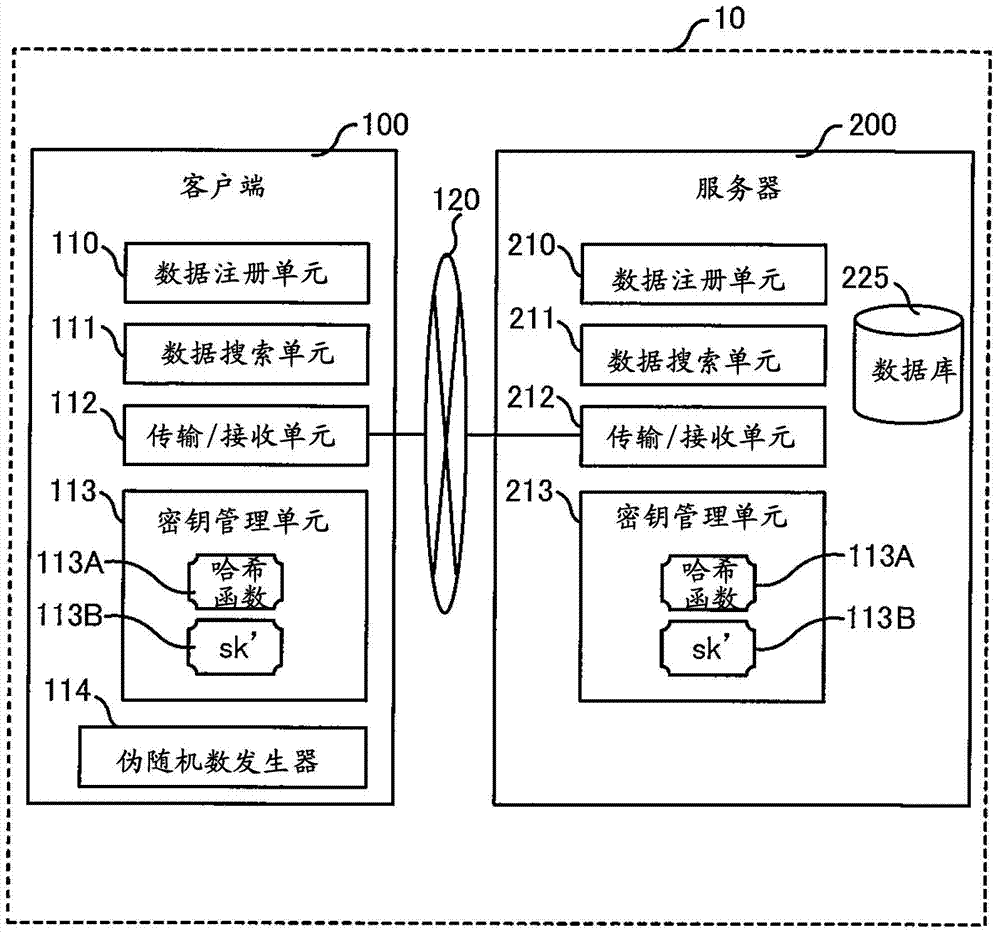
[0030] figure 1 It is a network configuration diagram showing the secure search processing system 10 of this embodiment. figure 1 The secure search processing system 10 (hereinafter, system 10) in the secure search technology is a computer system that can reduce the time and effort required to manage user keys and reduce the risk of information management when key leaks occur, including customer end 100 and server 200. Such a system 10 is based on the searchable encryption processing technique disclosed by the present inventor in Japanese Laid-Open No. 2012-123614, and is further configured to reduce management burden and prevent Risk and achieve exceptionally good results.
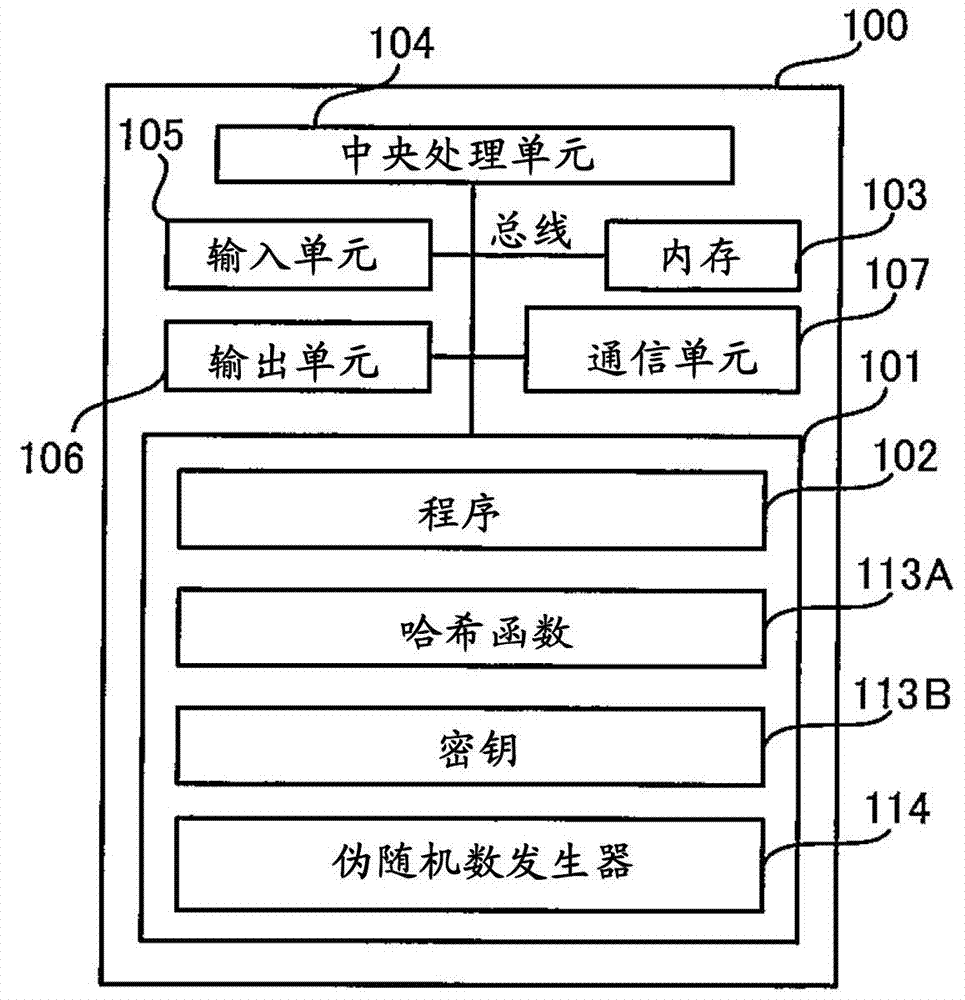
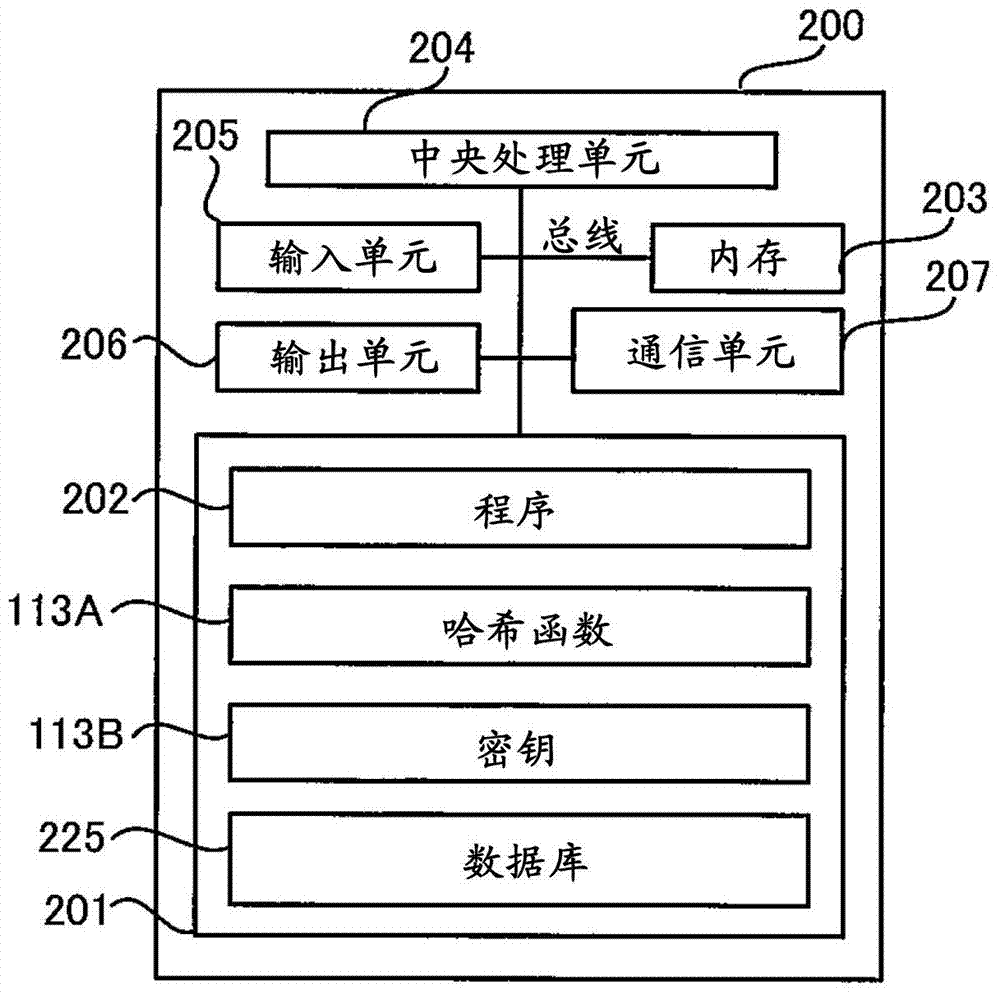
[0031] Next, functions provided by each of the client 100 and the server 200 constituting the system 10 of the present embodiment will be desc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com