Searchable encryption method and equipment thereof
An encryption method and equipment technology, applied to the public key and key distribution of secure communication, to achieve the effect of reducing network bandwidth and storage overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
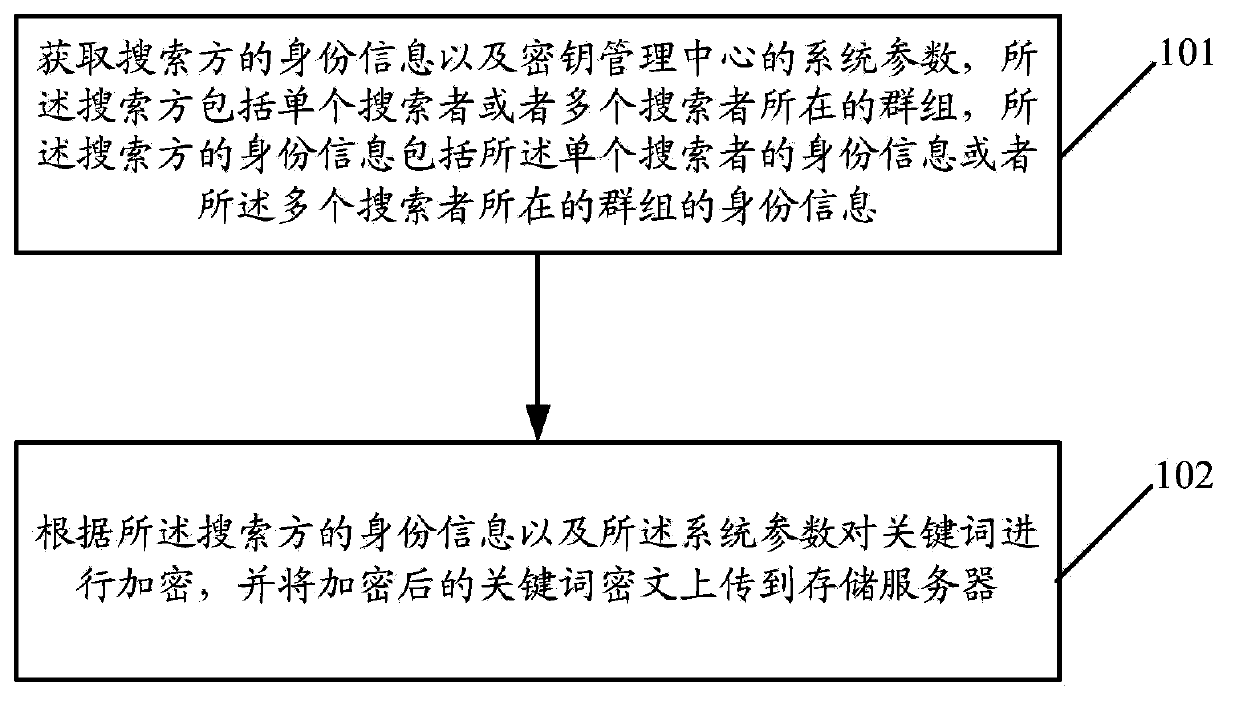
[0089] reference figure 1 , figure 1 It is a flowchart of a searchable encryption method provided in the first embodiment of the present invention. Such as figure 1 As shown, the method includes the following steps:
[0090] Step 101: Obtain the identity information of the searcher and the system parameters of the key management center. The searcher includes a single searcher or a group of multiple searchers. The identity information of the searcher includes the information of the single searcher. Identity information or identity information of the group where the multiple searchers are located;
[0091] Wherein, the identity information of the searcher includes but is not limited to the searcher's mobile phone number, work number, QQ number, Email and other information. The method of obtaining the identity information of the searching party includes, but is not limited to, obtaining by telephone query or email query. The identity information of the group where the searcher is lo...
Embodiment 2
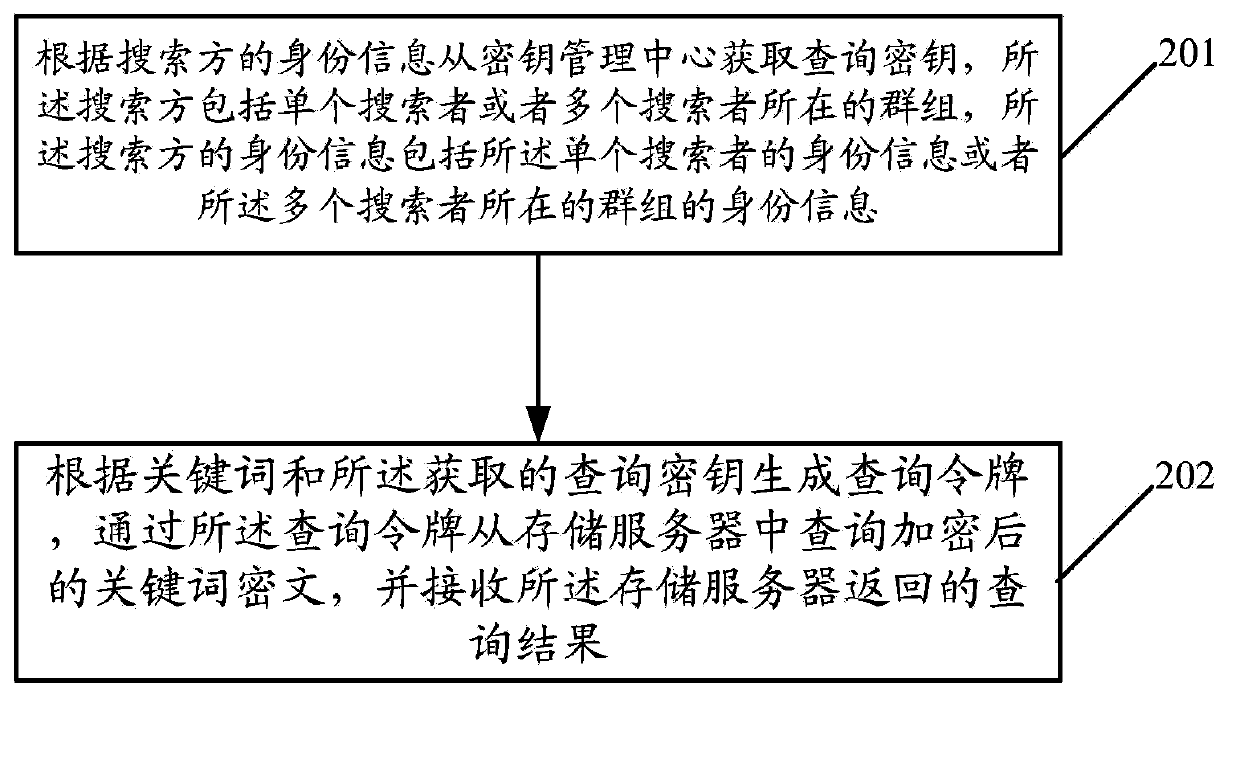
[0100] reference figure 2 , figure 2 It is a flowchart of an identity-based searchable encryption method provided in the second embodiment of the present invention. Such as figure 2 As shown, the method includes the following steps:
[0101] Step 201: Obtain a query key from the key management center according to the identity information of the searcher, the searcher includes a single searcher or a group of multiple searchers, and the identity information of the searcher includes the single searcher. The identity information of or the identity information of the group where the multiple searchers are located;
[0102] Wherein, the query key is a private key corresponding to an encryption key generated by the key management center according to the identity information of the searcher and system parameters. The key management center can also calculate the public key, because the key management center stores a public key factor matrix, and the private key only exists in the key ma...
Embodiment 3
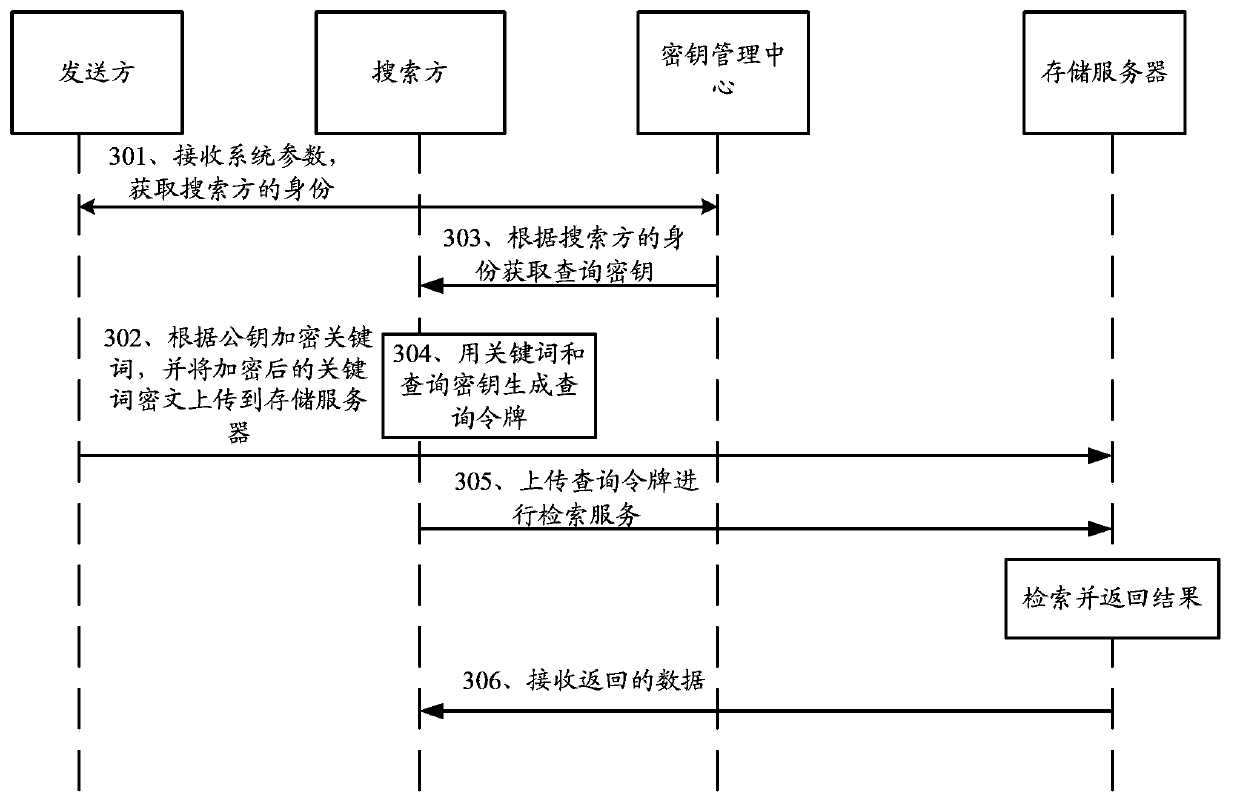
[0127] reference Figure 5 , Figure 5 It is a flowchart of an identity-based searchable encryption method provided in the third embodiment of the present invention. Such as Figure 5 As shown, the method includes the following steps:
[0128] Step 501: Obtain the identity of the searcher or the identity of the group where the searcher is located, and the system parameters of the key management center;
[0129] Step 502, encrypt keywords according to the identity of the searcher or the identity of the group where the searcher is located, and the system parameters, and upload the encrypted keyword ciphertext to the storage server;
[0130] Step 503: Encrypt the plaintext data according to any encryption method in the prior art, and upload the ciphertext of the encrypted plaintext data to the storage server.
[0131] In this step, the plaintext data corresponding to the keyword is encrypted by any encryption method in the prior art.
[0132] The embodiments of the present invention are a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com