Website weak password detecting method
A weak password and website technology, applied in the field of electronic information security, can solve the problems of low missed detection rate, high missed detection rate, low scanning efficiency and accuracy rate, etc., to achieve low missed detection rate, short detection time, and occupation of website systems The effect of less resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
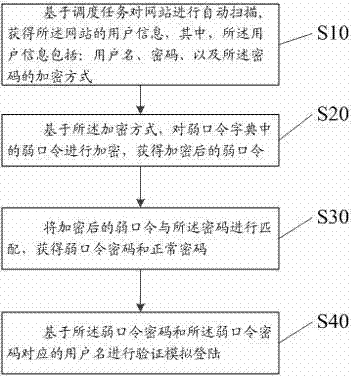
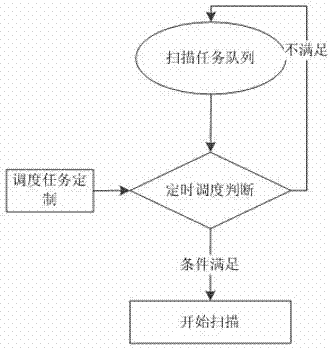
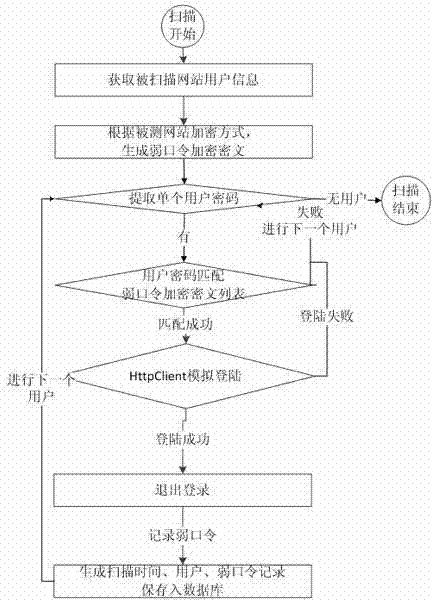
[0040] In Embodiment 1, a detection method for website weak passwords is provided, please refer to Figure 1-Figure 3 , the method includes:
[0041] S10, automatically scan the website based on the scheduling task, and obtain user information of the website, wherein the user information includes: a user name, a password, and an encryption method of the password;
[0042] S20. Based on the encryption method, encrypt the weak password in the weak password dictionary to obtain the encrypted weak password;
[0043] S30, matching the encrypted weak password with the password to obtain the weak password password and the normal password;
[0044] S40. Perform verification and simulate login based on the weak password and the user name corresponding to the weak password.
[0045] Wherein, in the embodiment of the present application, after the step of verifying and simulating login based on the weak password and the user name corresponding to the weak password, it also includes:
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com