Secret key changing and signature updating method for cloud data audit
A cloud data and key technology, which is applied in key distribution, can solve the problems of high computing expenditure, wide application, and untrusted cloud service providers in DO, and achieve the effect of reducing communication overhead and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] In order to make the technical means, creative features, goals and effects achieved by the present invention easy to understand, the present invention will be further described below in conjunction with specific illustrations.
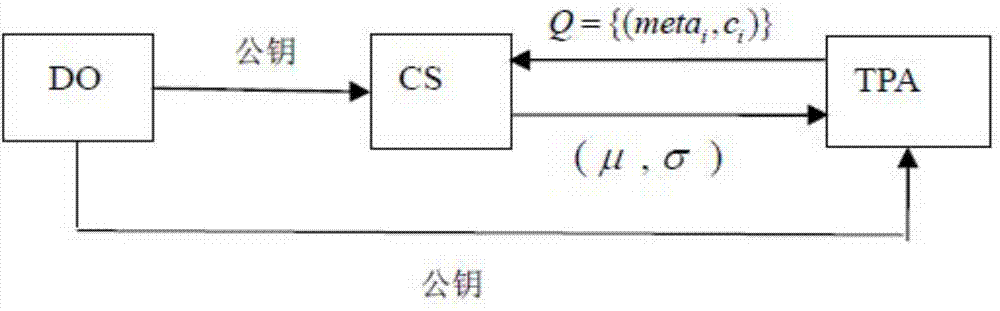
[0030] When the present invention performs key change and signature update on cloud data audit, it is mainly divided into three stages: (1) pre-update stage; (2) update stage; (3) post-update stage.
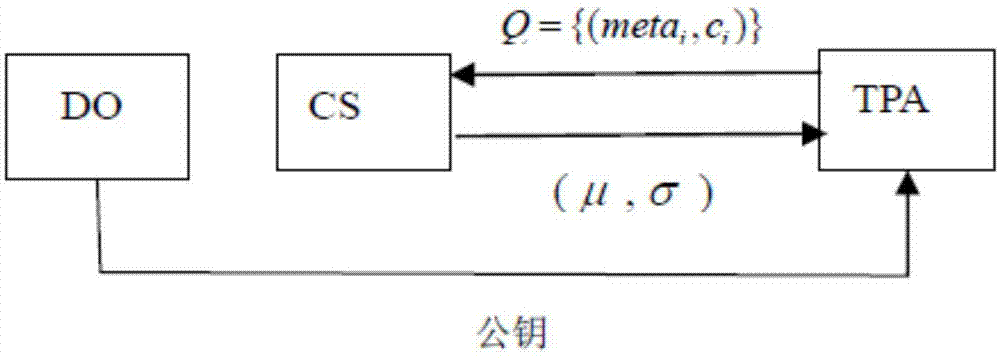
[0031] Among them, in the pre-update phase (BUP), the data owner (DO) calculates and generates the initial key and calculates the initial signature, and the cloud server (CS) calculates the initial integrity by the signature of the DO and the parameters accepted from the third-party audit (TPA) Prove the parameter P, and finally TPA will audit it.
[0032] In the update phase (UDP), DO selects a random number to generate a new key, calculates the key required to update the signature and sends it to CS, and CS calculates a new signature from the dat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com