Terminal and method for protecting user information against leakage
A user information and user technology, applied in the electronic field, can solve problems such as inability to assist equipment safety detection, and achieve the effect of not being easily leaked and ensuring safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be further described in detail below through specific embodiments in conjunction with the accompanying drawings.
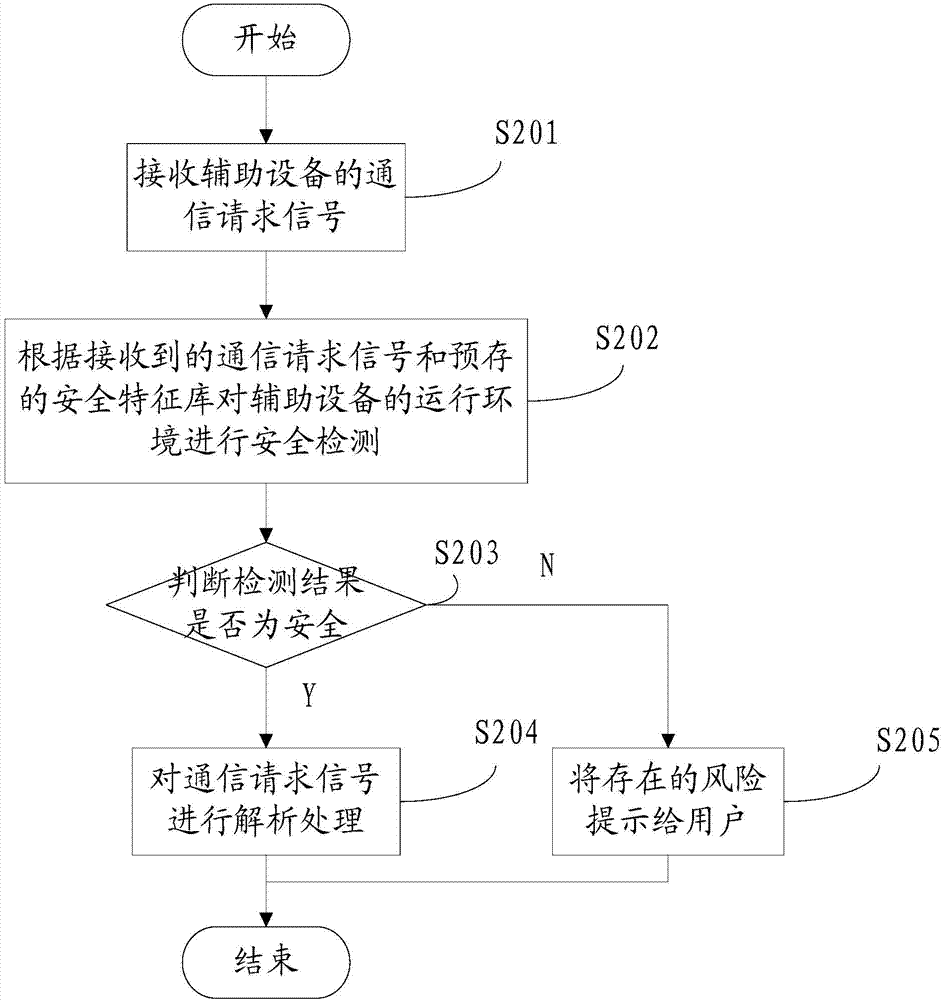
[0027] Such as figure 1 Shown is a structural diagram of a terminal for preventing user information leakage in this embodiment, please refer to figure 1 , the terminal 100 includes: a communication module 101, a safety detection module 102 and a control module 103, wherein the communication module 101 is used to receive a communication request signal from an auxiliary device; the safety detection module 102 is used to receive the communication request signal according to the received communication request signal and the pre-stored safety feature library to perform safety detection on the operating environment of the auxiliary device; the control module 103 is configured to analyze and process the communication request signal when the detection result of the safety detection module 102 is safe. The communication request signal inc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com