Network worm active hampering method based on driver checking and confronting tool automatic generation system
An automatic generation and worm technology, applied in the field of network security, can solve problems such as the great harm of the Internet and the impact of network infrastructure, and achieve the effect of completely eliminating worms, improving response speed, and eliminating long-term worm-infected nodes.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
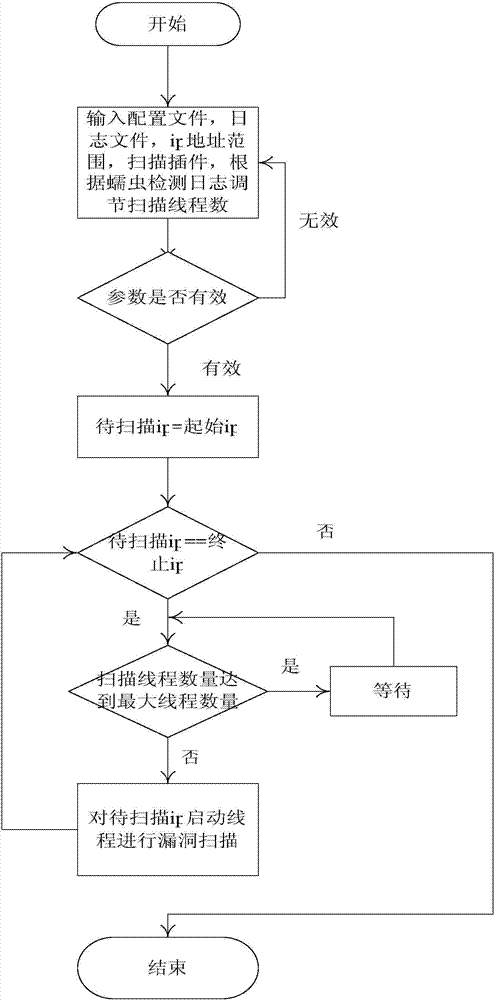
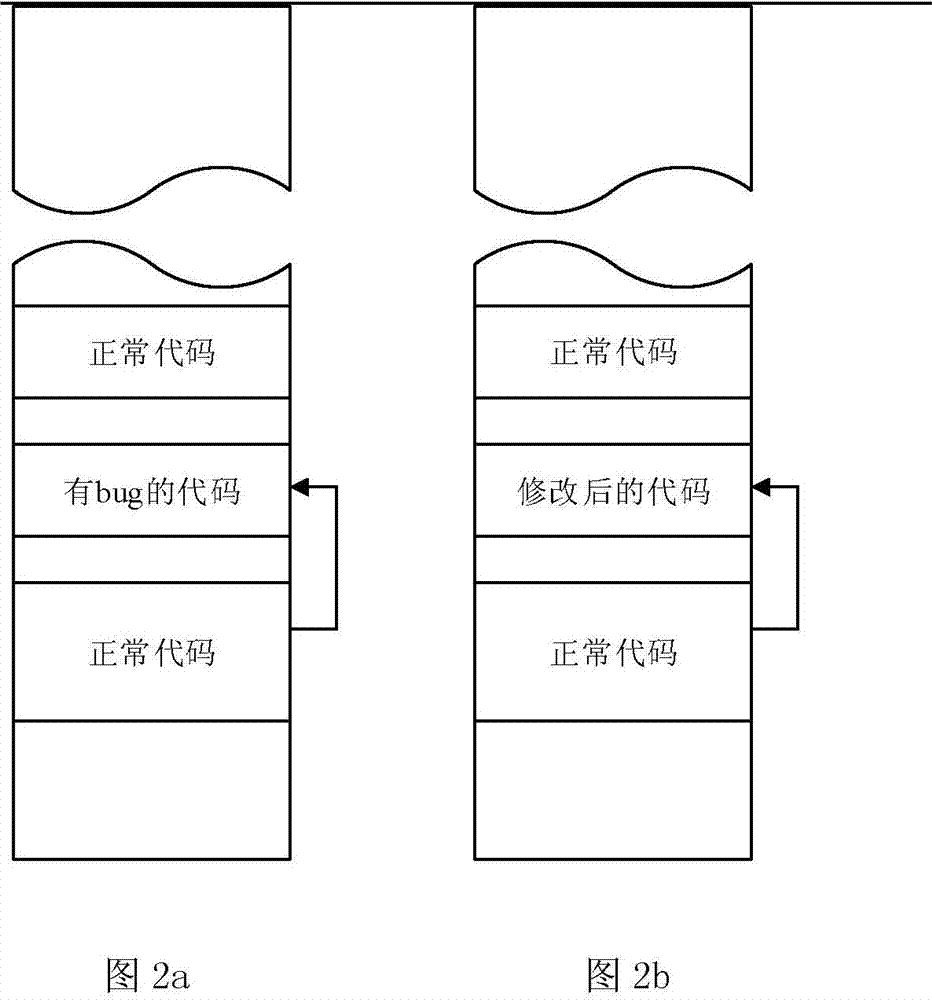
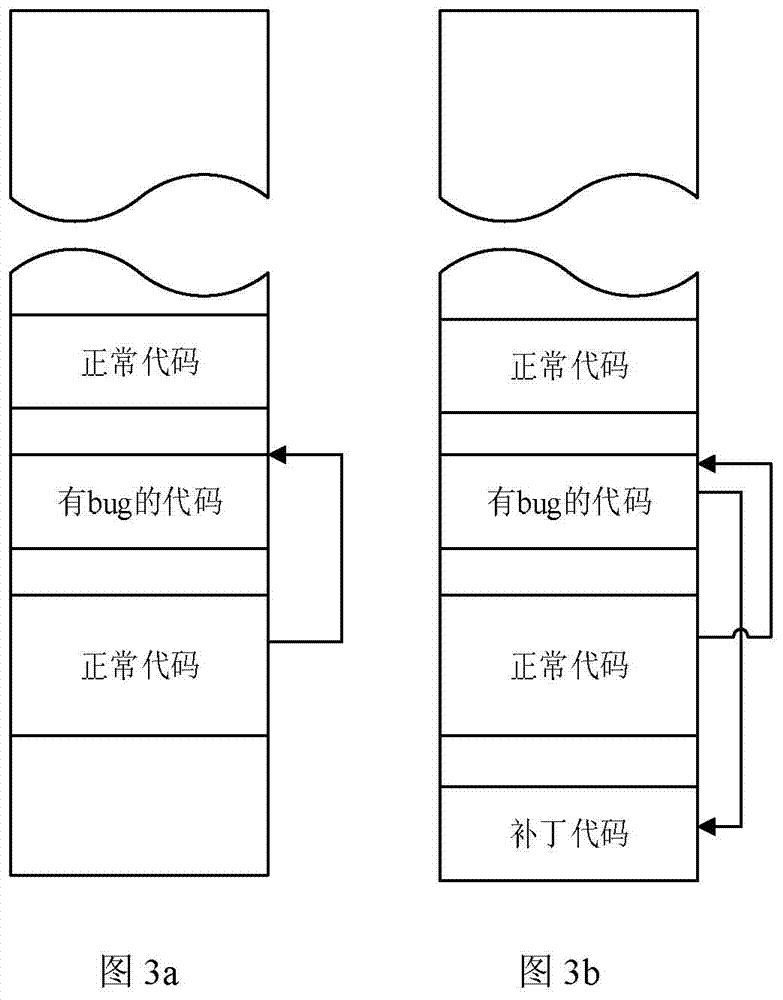
[0025] Such as Figures 1 to 3 As shown, this embodiment is described in detail as follows for the detection-driven active containment method for network worms and the automatic generation system for network worm countermeasures implementing the method:
[0026] 1. Determine the eigenvalues of the worm: continuous subsequences. Sequence X = {x 1 x 2 ... x n}, if there is a sequence Y={y 1 the y 2 ...y m}, and y 1 =x j+1 ,y 2 =x j+2 ,...y m =x j+m , where j≥0, j+m≤n, then Y={y 1 the y 2 ...y m} is a continuous subsequence of X. characteristics of worms. If the worm W spreads on the network, the data it transmits forms the sequence X=x 1 x 2 ... x n}, if there is a subsequence Y={y in X 1 the y 2 ...y m}, and this sequence must not exist in other network traffic without worm W propagating, then the subsequence Y is called a signature code of worm W.
[0027] 2. Capture traffic at the network entrance and exit for matching: capture network traffic and mat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com