Malicious node detection method based on clustering trust evaluation in internet of vehicles
A technology of malicious nodes and detection methods, applied in wireless communication, network topology, electrical components, etc., can solve the problems of recommended chain length, high control and routing overhead, poor scalability, etc., to simplify the recommended chain, facilitate expansion, reduce The effect of communication overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
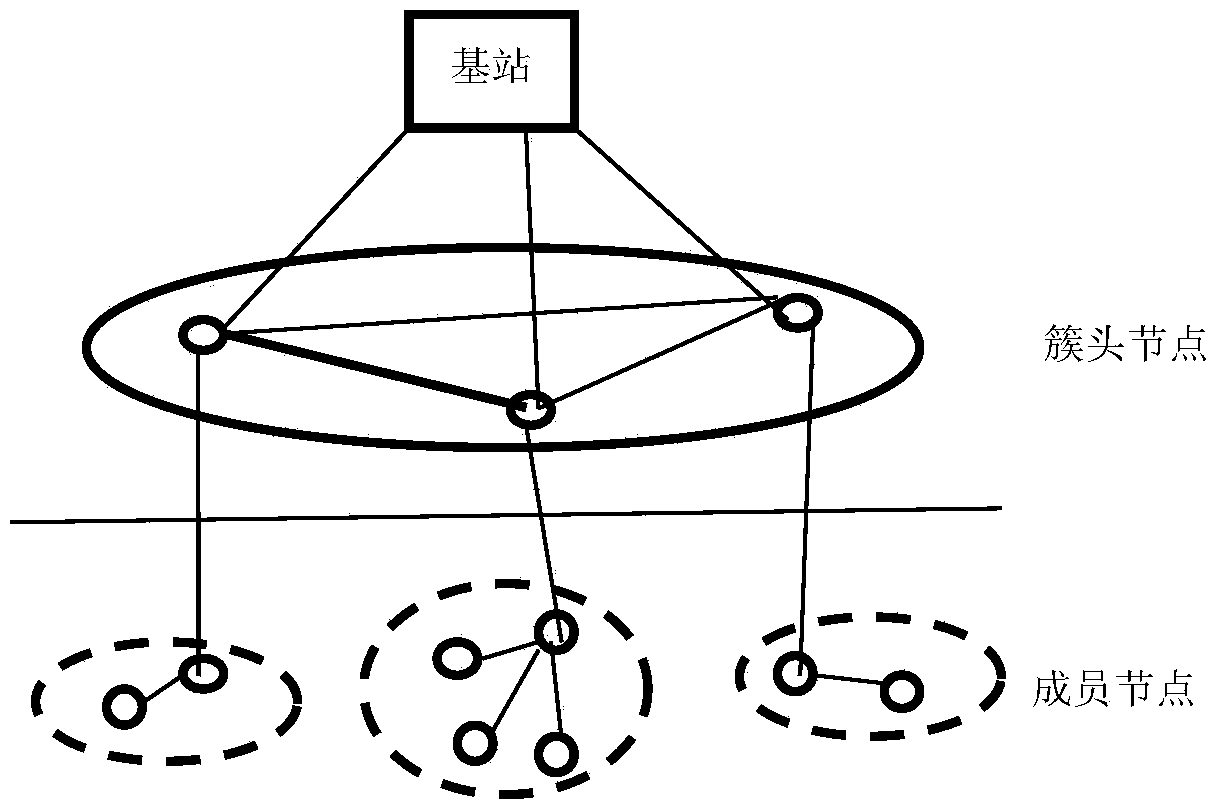
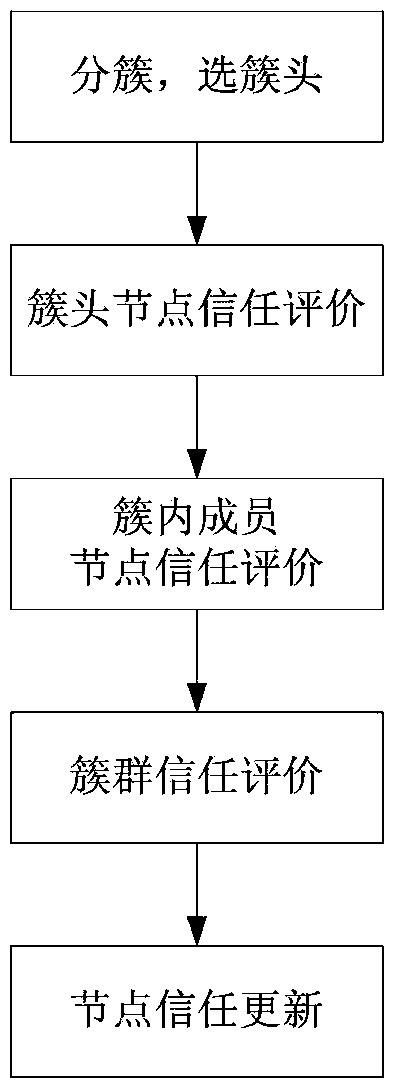
[0030] Such as figure 2 As shown, the detection method of the present invention has a total of 5 steps, namely:
[0031] (1) Clustering and cluster head selection: Initialize the network, form a cluster of nodes with less mobility among all nodes in the network, and select the node with the smallest mobility change relative to its neighbors as the cluster head;
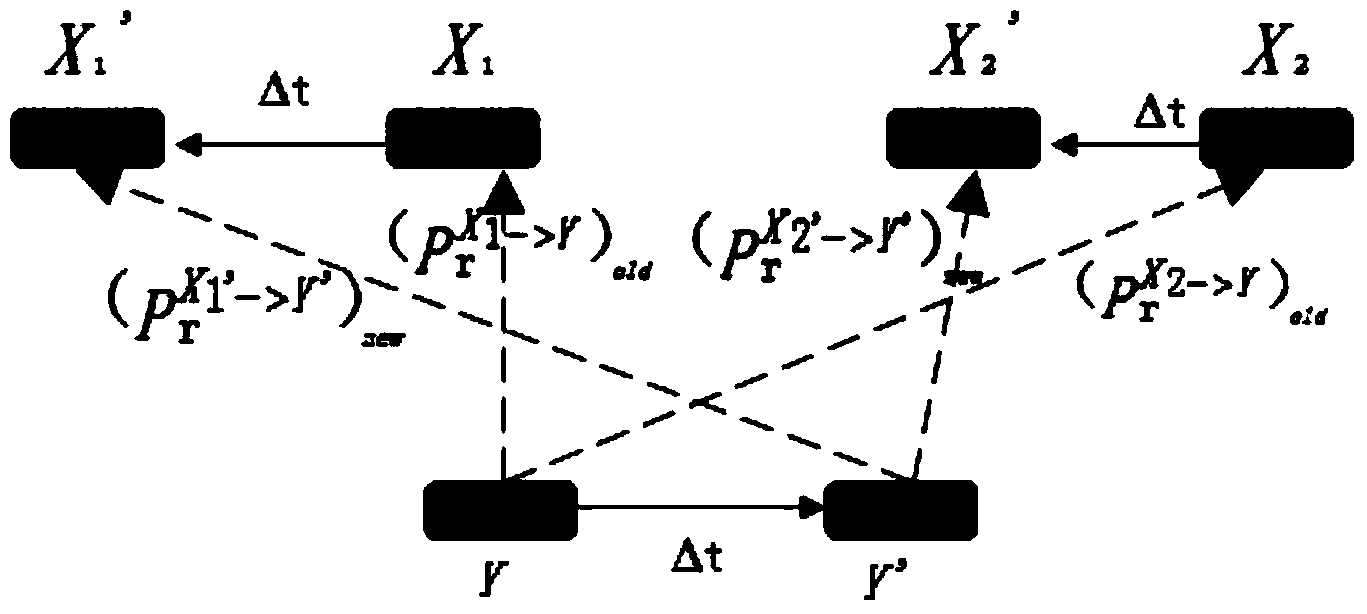
[0032] (2) Cluster head node trust evaluation: The cluster head node is managed by the base station, and its comprehensive trust value is evaluated according to the direct trust value of the base station and the recommended trust value of other cluster head nodes; the direct trust value is the result of objective statistics, according to The number of successful and failed interactions between the base station node and the cluster head node is calculated; the recommended trust value is calculated using the packet loss rate;
[0033] (3) Trust evaluation of the member nodes in the cluster: the member nodes in the cluster are...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com