Predictive Heap Overflow Protection
A memory and malware technology, applied in platform integrity maintenance, instrumentation, computing, etc., can solve the problem that anti-malware solutions cannot detect malware
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
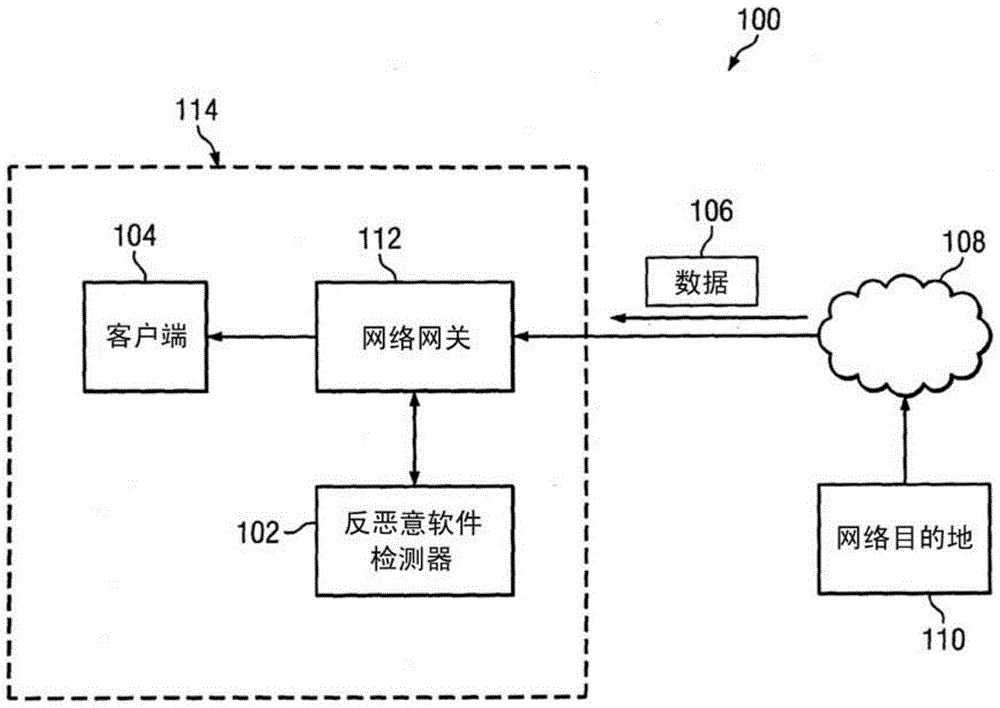
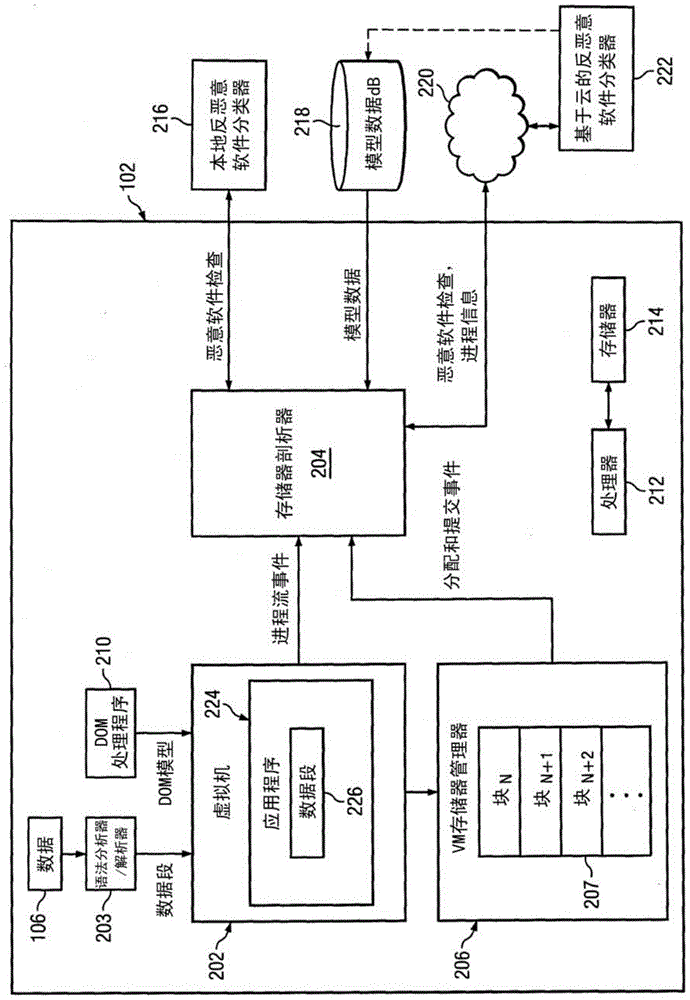
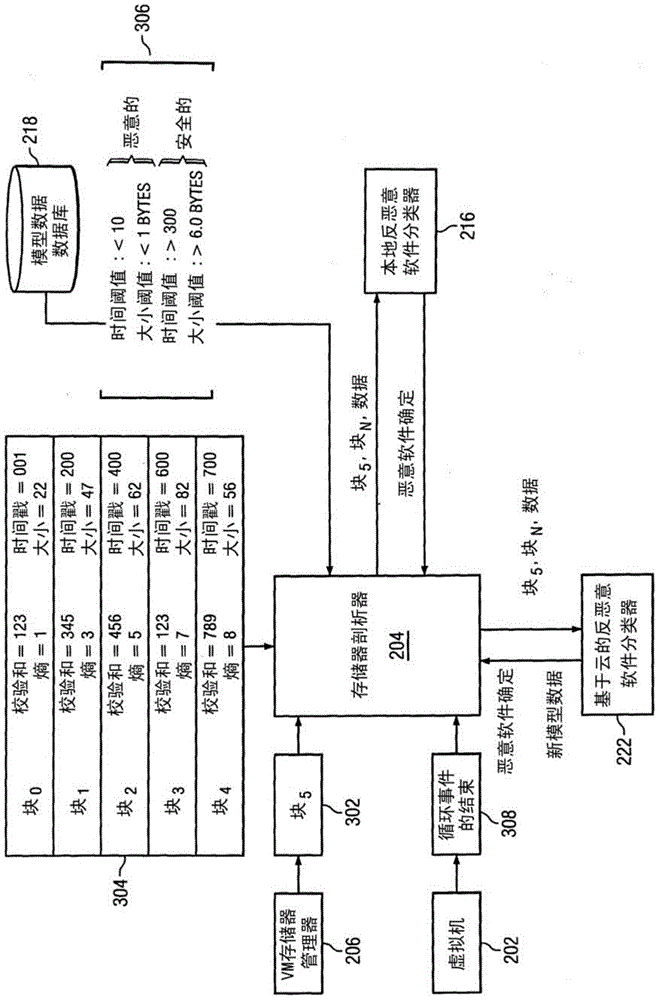
[0013] figure 1 is an illustration of an exemplary system 100 for predictive heap overflow protection. System 100 may be configured to determine whether an entity in the form of an application or data for an application is malware. Such data may be malware configured to exploit overflow weaknesses in the system or vulnerable applications. In an embodiment, system 100 may be configured to detect malware attempting to exploit flaws, such as heap overflow vulnerabilities.
[0014] A heap overflow vulnerability in a system may include a system flaw for a buffer overflow, where data is written to the buffer, but the data is written into memory adjacent to the buffer. Exploitation of an overflow vulnerability may include, for example, malware using stack-based or heap-based exploitation techniques. Heap exploitation-based techniques may include corrupting memory allocated in the target system's memory heap with malicious code. Such memory allocation can be done in real time. Sy...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com