Network firewall realization method suitable for virtual machine
A network firewall and virtual machine network technology, applied in the field of network firewalls, can solve the problems of no unified interface to display and modify rules, easy to cause confusion, occupying large computer resources, etc., to achieve flexible and convenient implementation methods and the effect of saving resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
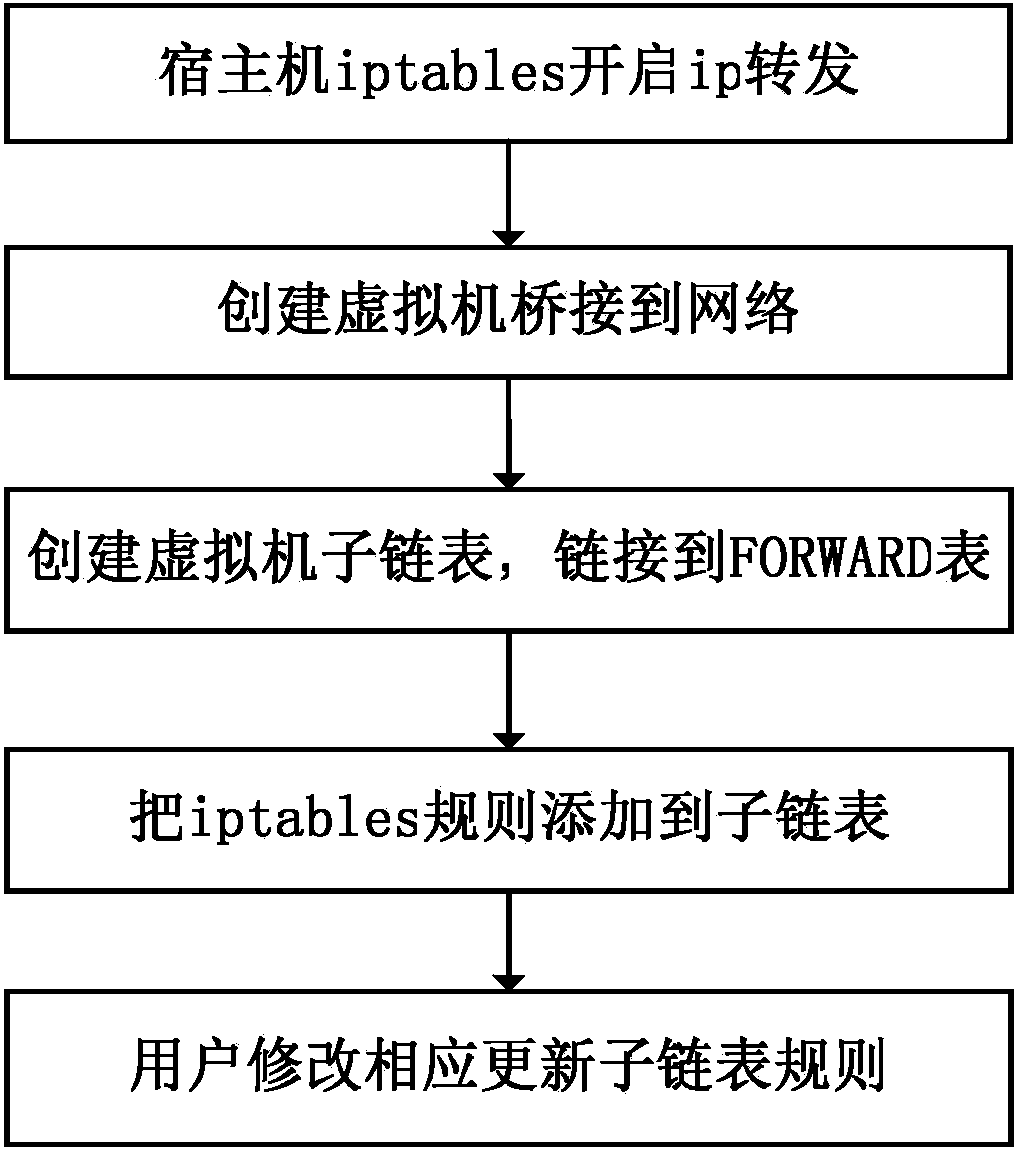
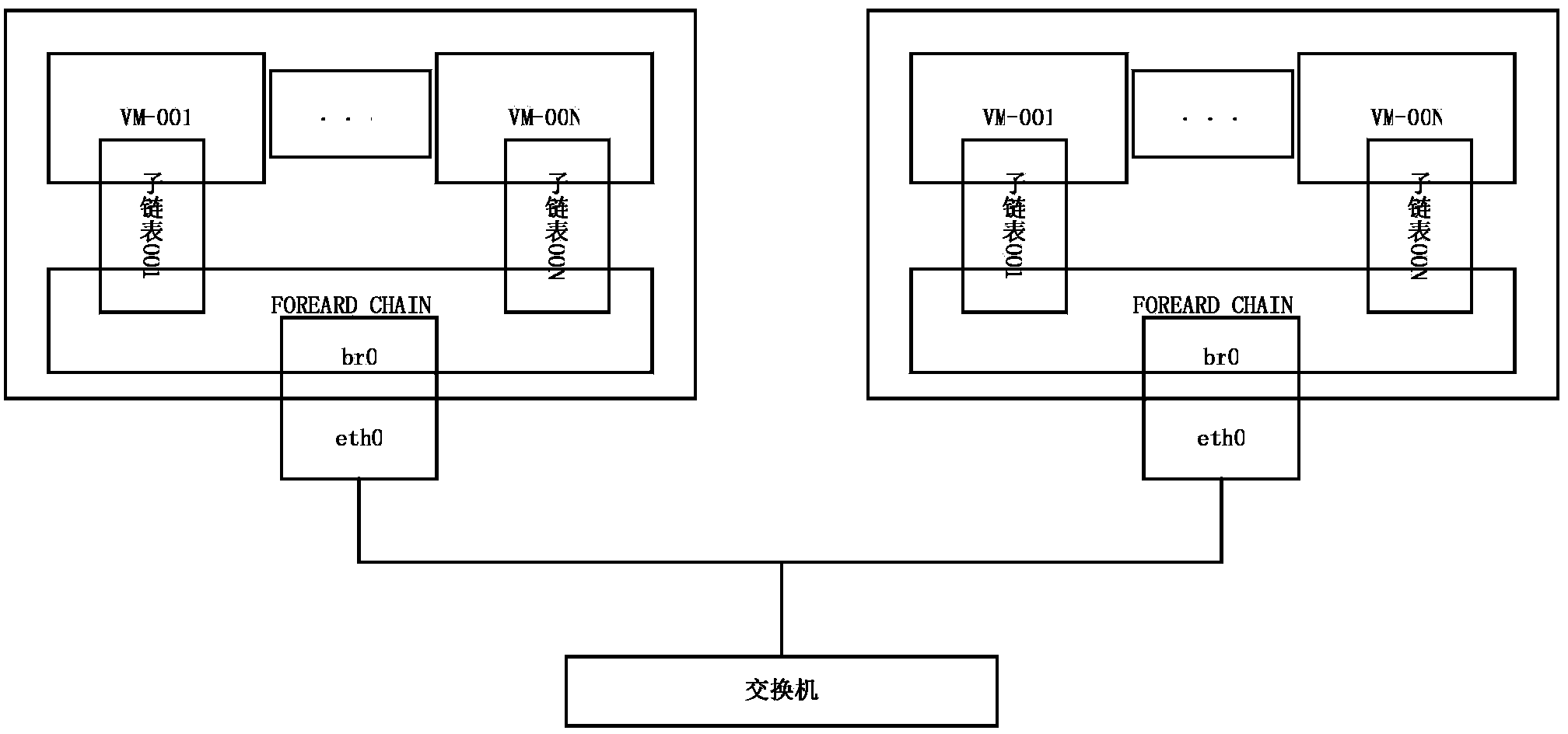
[0024] Such as figure 1 , 2 Shown, the present invention comprises the steps:
[0025] Step 1: Install firewall software on the host machine and enable ip forwarding.
[0026] Step 2: The virtual machine created by the host machine is connected to the network in a bridging manner; that is, the network interface of the virtual machine is connected to the linux bridge; the bridge is equivalent to implementing a virtual switch on the linux host machine.
[0027] Step 3: Create a new sub-list every time a virtual machine is created on the host, and the name of the sub-list is the same as the name of the virtual machine.
[0028] Step 4: Initialize the sub-link list rule on the host machine, and link to the FORWARD table; the FORWARD link list allows the network data packet to be forwarded to the network interface of the virtual machine again, and release it according to the method defined by the rule of the virtual machine sub-link list (accept ), reject (reject), and discard (...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com