Access request filtering method, device and facility
A technology of access request and filtering method, applied in the field of network security, can solve the problems of limited hardware firewall hardware processing capacity, increased labor cost and maintenance complexity, poor access request filtering ability, etc., to achieve reduced maintenance complexity and low cost , the effect of effective interception
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
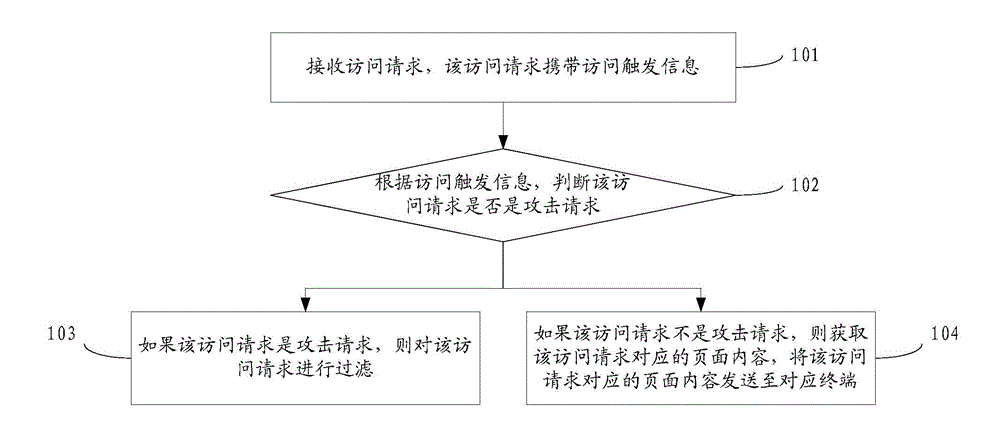
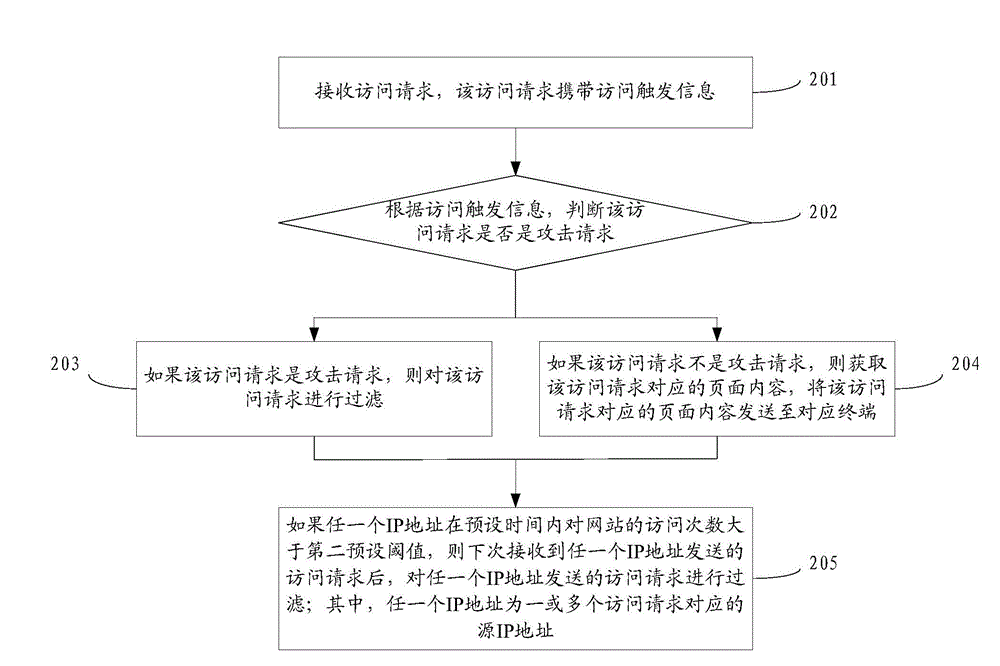
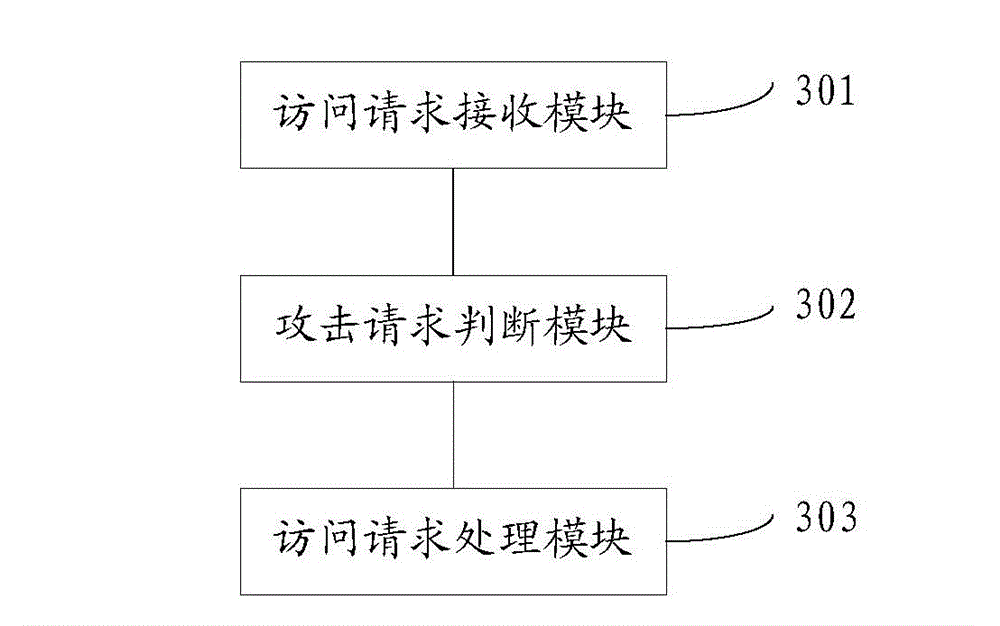
[0050]Reference will now be made in detail to the exemplary embodiments, examples of which are illustrated in the accompanying drawings. When the following description refers to the accompanying drawings, the same numerals in different drawings refer to the same or similar elements unless otherwise indicated. The implementations described in the following exemplary examples do not represent all implementations consistent with the present invention. Rather, they are merely examples of apparatuses and methods consistent with aspects of the invention as recited in the appended claims.
[0051] Before explaining the embodiments of the present disclosure in detail, the application scenarios of the present disclosure will be introduced first. As a common means of hacker attack, DDoS attack is to combine multiple computers as an attack platform to launch a DDoS attack on one or more targets, thereby multiplying the power of denial of service attacks. For e-book websites, when a DDo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com