Method and device for setting Wifi access authority and Wifi authentication
A technology of access authority and authentication method, which is applied in the field of Wifi authentication according to the set access authority, which can solve the problems of inconvenient authentication process and network security issues, and achieve the effect of ensuring network security and simplifying the authentication process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
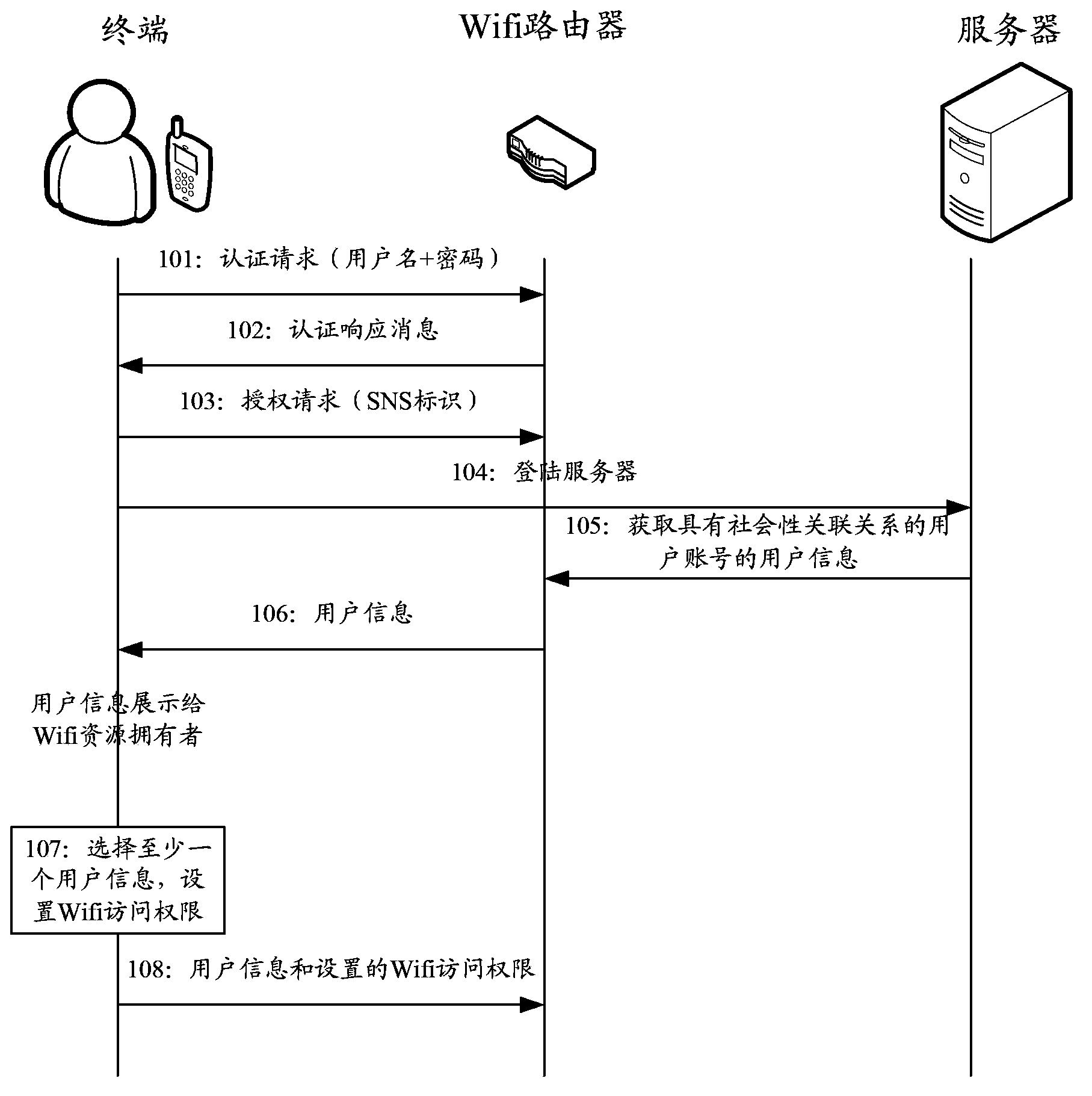
[0068] Embodiment 1 of this application describes a method for setting Wifi access rights, such as figure 1 As shown, it is a schematic diagram of the steps of the first solution of this embodiment, which mainly includes the following steps:
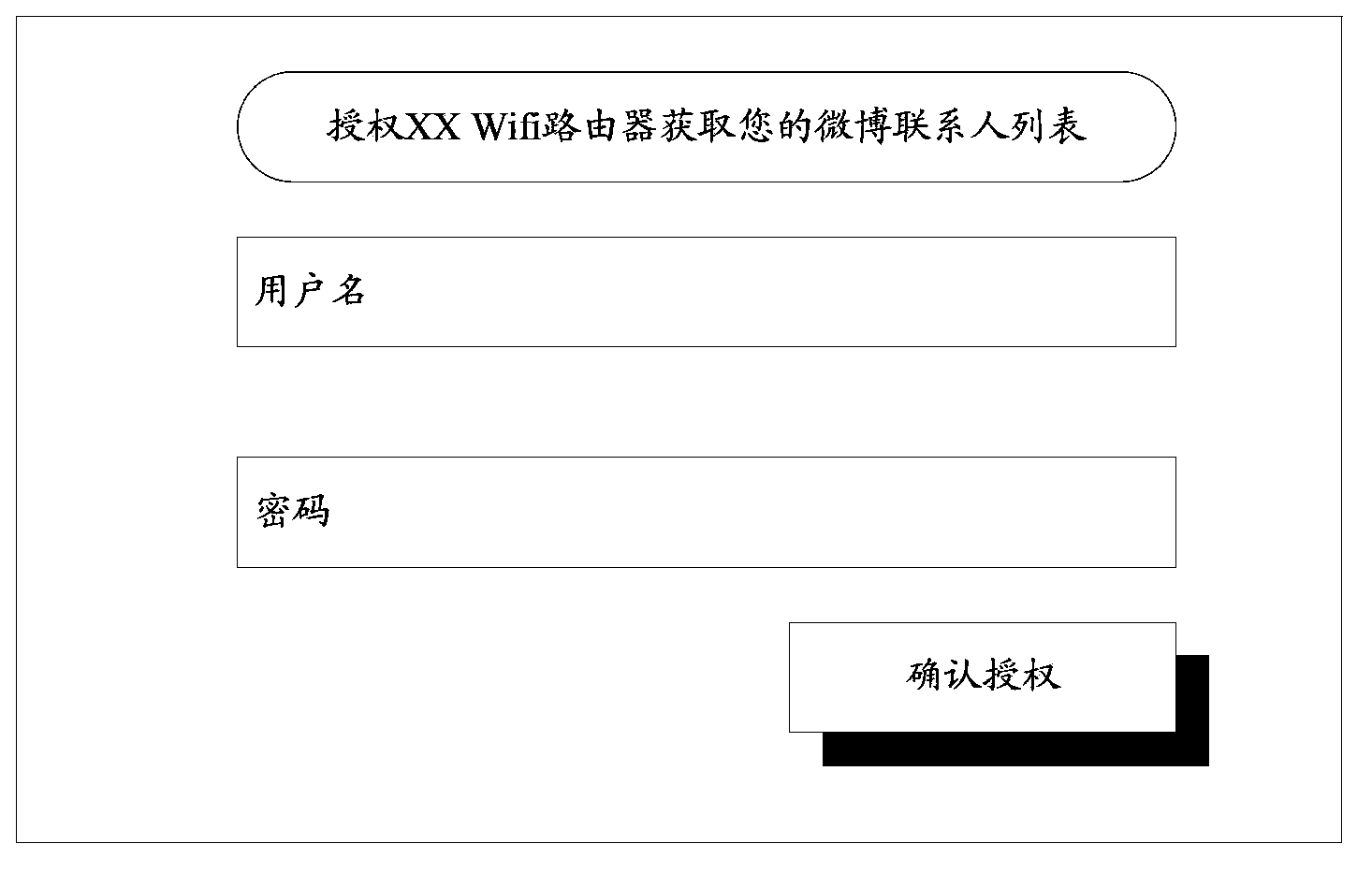
[0069] Step 101: The terminal initiates an authentication request to the Wifi router, and carries a username and password in the authentication request.
[0070] In this step 101, the terminal that initiates the authentication request is the terminal used by the Wifi resource owner. Therefore, the terminal can include the username and password input by the Wifi resource owner in the authentication request and send it to the Wifi router.
[0071] Step 102: The Wifi router uses the received user name and password to authenticate the terminal that initiated the authentication request, and if the authentication is passed, then return an authentication response message to the terminal, and jump to step 103; otherwise, return an authentication...
Embodiment 2
[0113] The solution of the second embodiment of the present application is based on the Wifi access authority set in the first embodiment to carry out the Wifi authentication scheme, such as Figure 6 As shown, it is a schematic diagram of the method steps for Wifi authentication, which mainly includes the following steps:
[0114] Step 201: The terminal initiates an authentication request to the Wifi router, and the authentication request includes a MAC (Media Access Control Address, Media Access Control) address of the terminal.
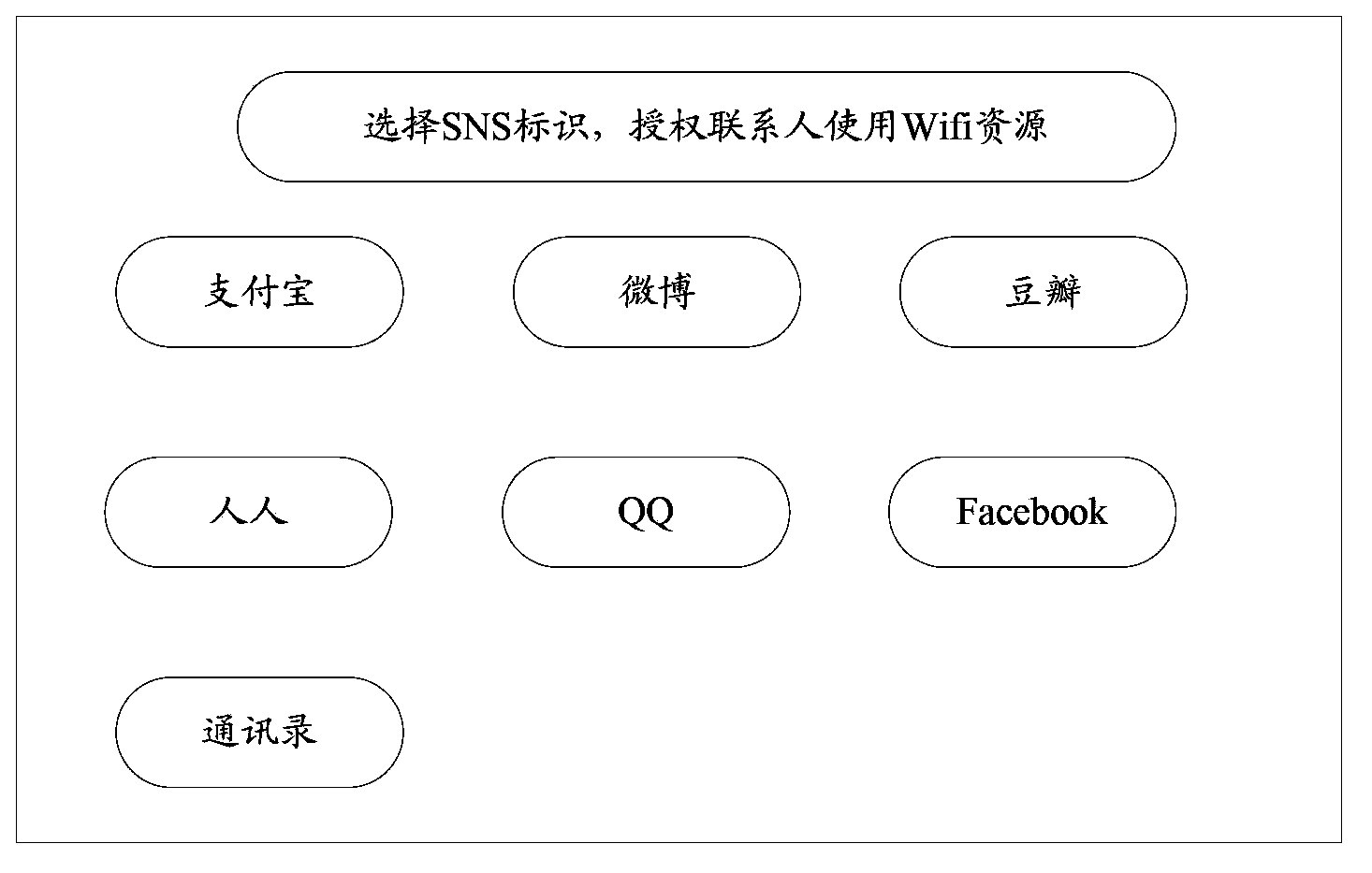
[0115] In the scheme of step 201, the Wifi router does not know whether the terminal currently initiating the authentication request is a terminal used by the Wifi resource owner or a terminal used by the Wifi resource user. After the request, first judge whether it contains the user name and password, if so, perform user name+password authentication on it, otherwise, identify the MAC address of the terminal from the authentication request.
[011...
Embodiment 3
[0130] The scheme of Embodiment 3 of the present application is also a scheme for performing Wifi authentication based on the Wifi access authority set in Embodiment 1, such as Figure 7 As shown, it is a schematic diagram of the method steps for Wifi authentication, which mainly includes the following steps:
[0131] Step 301: The terminal initiates an authentication request to the Wifi router, and the authentication request includes the MAC address of the terminal.
[0132] This step is the same as step 201 in the second embodiment.
[0133] Step 302: The Wifi router determines the user information corresponding to the MAC address included in the authentication request according to the stored correspondence between the user information and the MAC address.
[0134] In step 105 of the first embodiment, the Wifi router obtains from the server the user information of other user accounts that have a social association relationship with the user account used by the terminal that...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com