Cross-subnet access control method of electric power mobile terminal
A mobile terminal and access control technology, applied in the field of control, can solve problems such as inability to adapt to the system structure and inflexible terminal authorization management, and achieve the effect of taking into account the requirements of confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
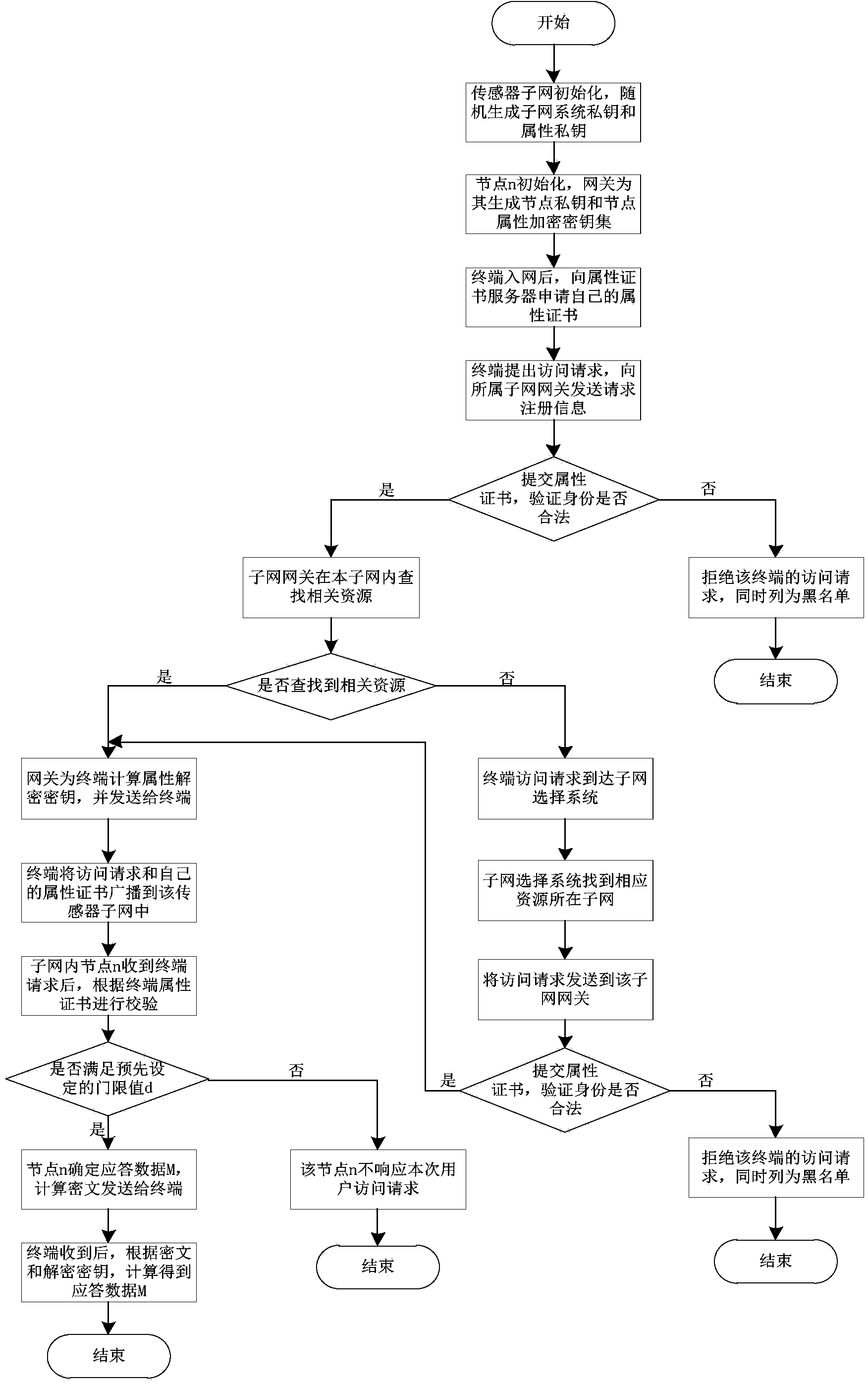
[0079] 1. Initialization of the sensor subnet
[0080] The gateway is denoted by W, first select the bilinear group G of order p 1 And the corresponding group G 2 , Use g for G 1 Generator of Is a bilinear mapping. W randomly generated subnet private key E k , Randomly generate the attribute private key I for each attribute i , I=A 1 , A 2 ...A N . For any sensor node in the subnet, the gateway W first generates the node private key for it And generate a node attribute encryption key for it according to the attribute set authorized to access the node data In the initialization phase of the sensor node, the node is preloaded with N sk And {P i }.
[0081] 2. Terminal registration stage
[0082] The terminal U enters the network range where the gateway W is located, and needs to register at the gateway W to access the node data in the network. The registration algorithm steps are as follows:
[0083] Step 1: Terminal U makes an access request to gateway W, sends registration infor...
Embodiment 2
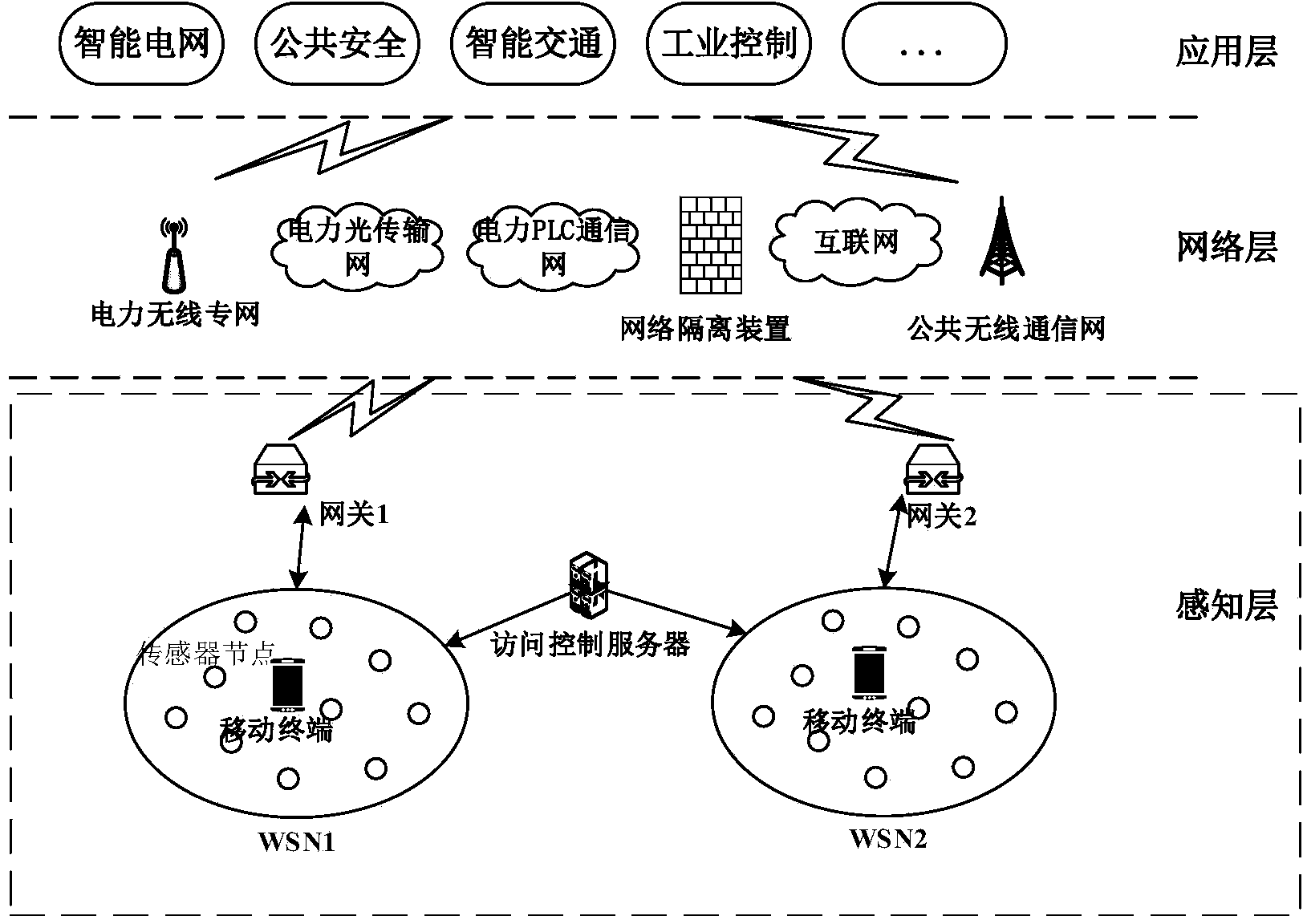
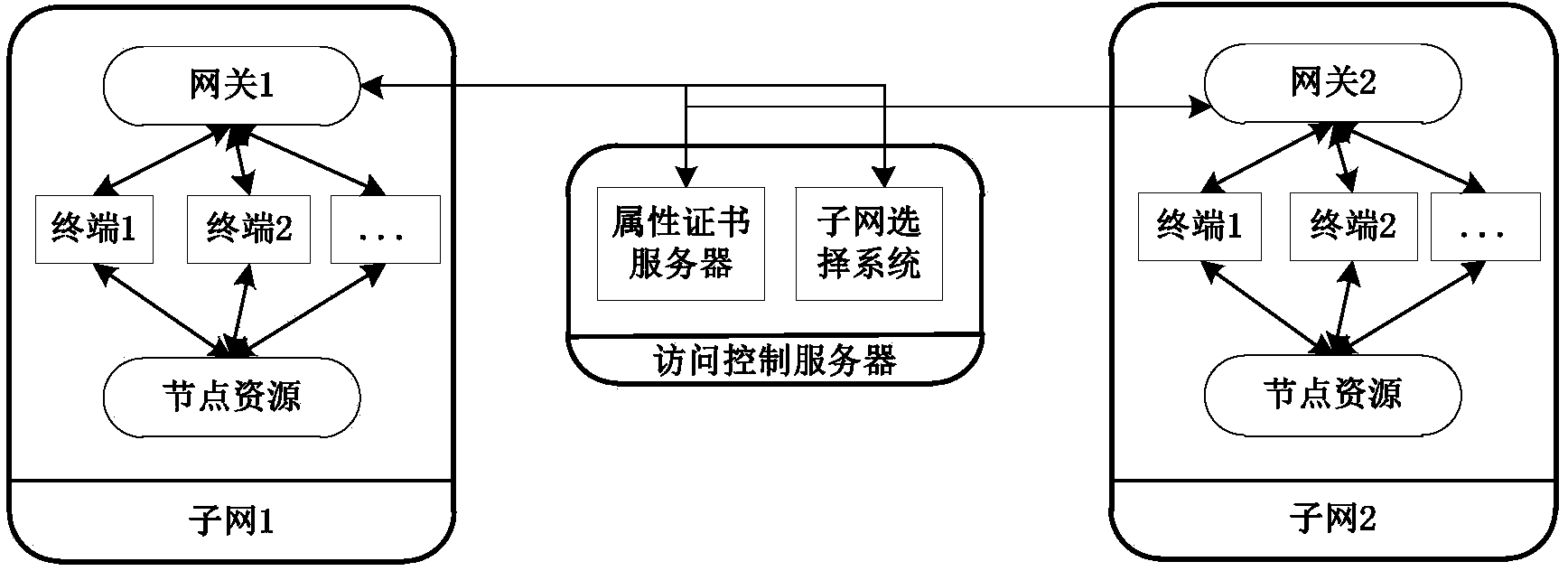
[0094] A certain electricity consumption information collection system is networked through the Internet of Things. According to the layout of residential quarters, the network is divided into different subnets according to buildings, units, floors and other units. The nodes in the subnet are responsible for data collection in a certain area, and the collection nodes Due to the power limitation, the collected information is usually transmitted to the subnet gateway, processed by the subnet gateway and uploaded to the power system electricity consumption information collection platform. After the mobile terminal enters the electricity consumption information collection system, if it needs to access the node data information, it needs to register. After the terminal successfully registers and possesses the decryption key, the attributes are checked according to the threshold structure to access the node information. Through the attribute-based cross-subnet access control method, t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com