Method for achieving cipher lock, cipher lock formed by the method, and annular lock
A combination lock and password information technology, applied to instruments, time registers, single input port/output port registers, etc., can solve the problems of not being able to use padlocks, low confidentiality, and inoperability, and achieve low cost , simple modification and safe use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
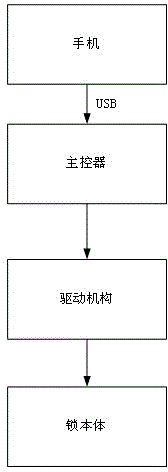
[0041] Such as figure 1 As shown, the present embodiment provides a combination lock based on a computer or a mobile phone, which mainly includes a lock body, a driving mechanism, and a main controller; the main controller is connected with a USB female interface, and the opening of the USB female interface is exposed to the lock. The outside of the main body is convenient for inserting data lines. Through the above settings, when in use, use the data cable to connect the mobile phone and the combination lock through the USB female interface, and the computer or mobile phone will send the password to the main controller in the combination lock. After the comparison is successful, the drive mechanism will be driven by the computer or mobile phone power supply. The driving mechanism drives the dead bolt to move to complete the unlocking.
[0042] Specifically, the main controller includes the following components:
[0043] USB control chip, responsible for the coordination and...
Embodiment 2
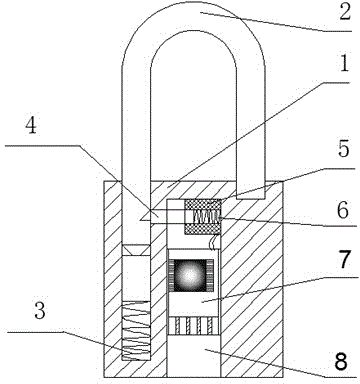
[0053] Such as figure 2As shown, the combination lock based on the mobile phone includes a lock body (1) and a lock ring (2). One end of the lock ring (2) is inserted into the lock body and a first spring (3) is arranged between the two. (1) There is an installation cavity inside, and the installation cavity is provided with a lock tongue (4) at one end for clamping the lock ring (2). The other end of the lock tongue (4) is sleeved with a second spring (6). The second spring (6) is covered with an electromagnet coil (5), the electromagnet coil (5) is connected to the main controller (7), the main controller (7) is connected to a USB female interface (8), and one end of the installation cavity extends to the outside of the lock and form an opening through which the USB female interface (8) is exposed. Through the above settings, the mobile phone is connected to the USB female interface (8) through the data line. After the password is successfully matched, the power supply of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com