Decryption failure recovery method, device, user terminal and network equipment
A recovery method and data frame technology, applied in the field of communication, can solve problems such as loss or disorder of data frames, failure of decryption at the receiving end, failure to recover, etc., and achieve the effect of reducing time and quickly restoring service use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
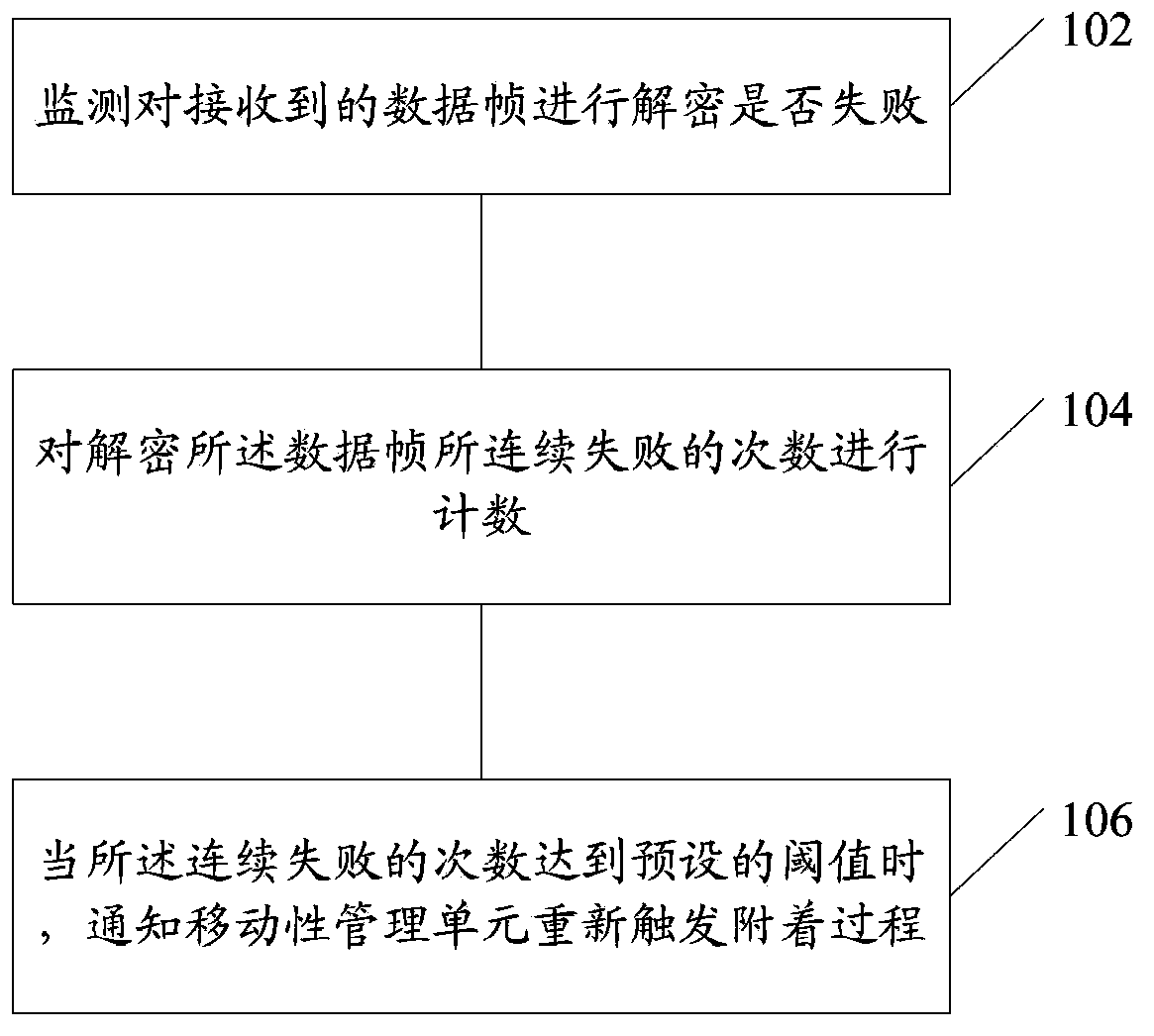
[0039] The recovery method of decryption failure described in this embodiment includes the following steps:
[0040] Step 102: monitoring whether the decryption of the received data frame fails;
[0041] Step 104: Count the number of consecutive failures to decrypt the data frame;
[0042] Step 106: When the number of consecutive failures reaches a preset threshold, notify the mobility management unit to re-trigger the attach process.
[0043] In a specific implementation, the execution subject of the method may be a user terminal or a network terminal. The user terminal may be a receiving end, and at this time, the network end is a sending end. When the user terminal is used as the receiving end, the method described in this embodiment is applied. Compared with the method of restarting the user terminal to restore the service, it does not require user participation, and only needs to re-trigger the attachment process of the user terminal, so it can be more convenient , Qui...
Embodiment 2
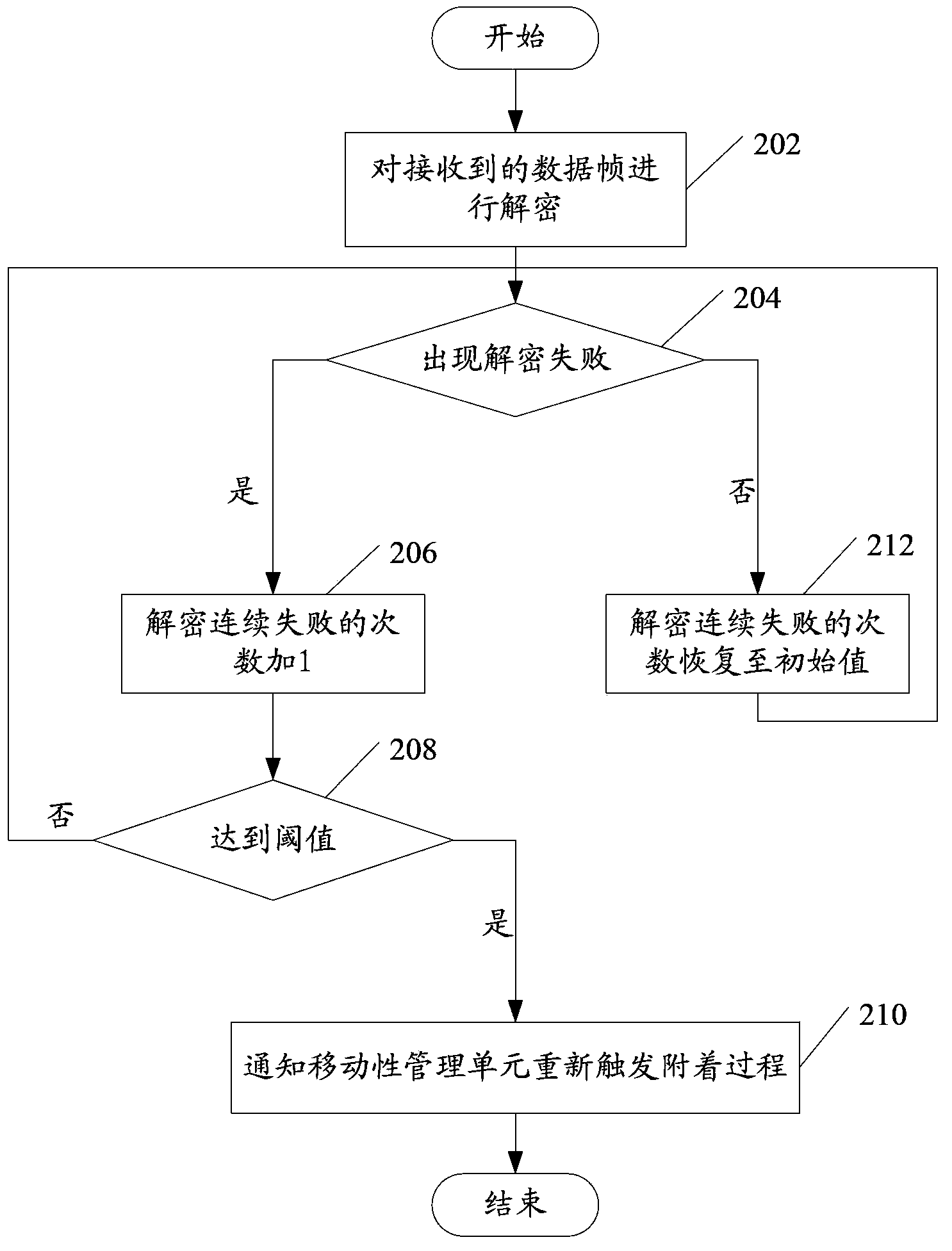
[0046] see figure 2 , the following are detailed steps through specific steps:
[0047] Step 202, decrypt the received data frame.
[0048] In a specific implementation, each time the sending end sends a data frame, the frame number of the next data frame to be sent will be correspondingly increased by 1. The value range of the frame number is between 0 and 511. When the frame number of the sent data frame is equal to 511, the frame number of the next data frame to be sent starts from 0 again, that is, the frame number of the data frame occurs reverse. When the frame number is reversed from 511 to 0, an operation of adding 512 to the OC value at the sending end is performed. When the receiving end finds that the received data frame is reversed, that is, when the data frame with frame number 511 is received, it is necessary to add 512 to the OC value of the receiving end to ensure that the OC values of the sending end and the receiving end are the same. match, so that ...
Embodiment 3
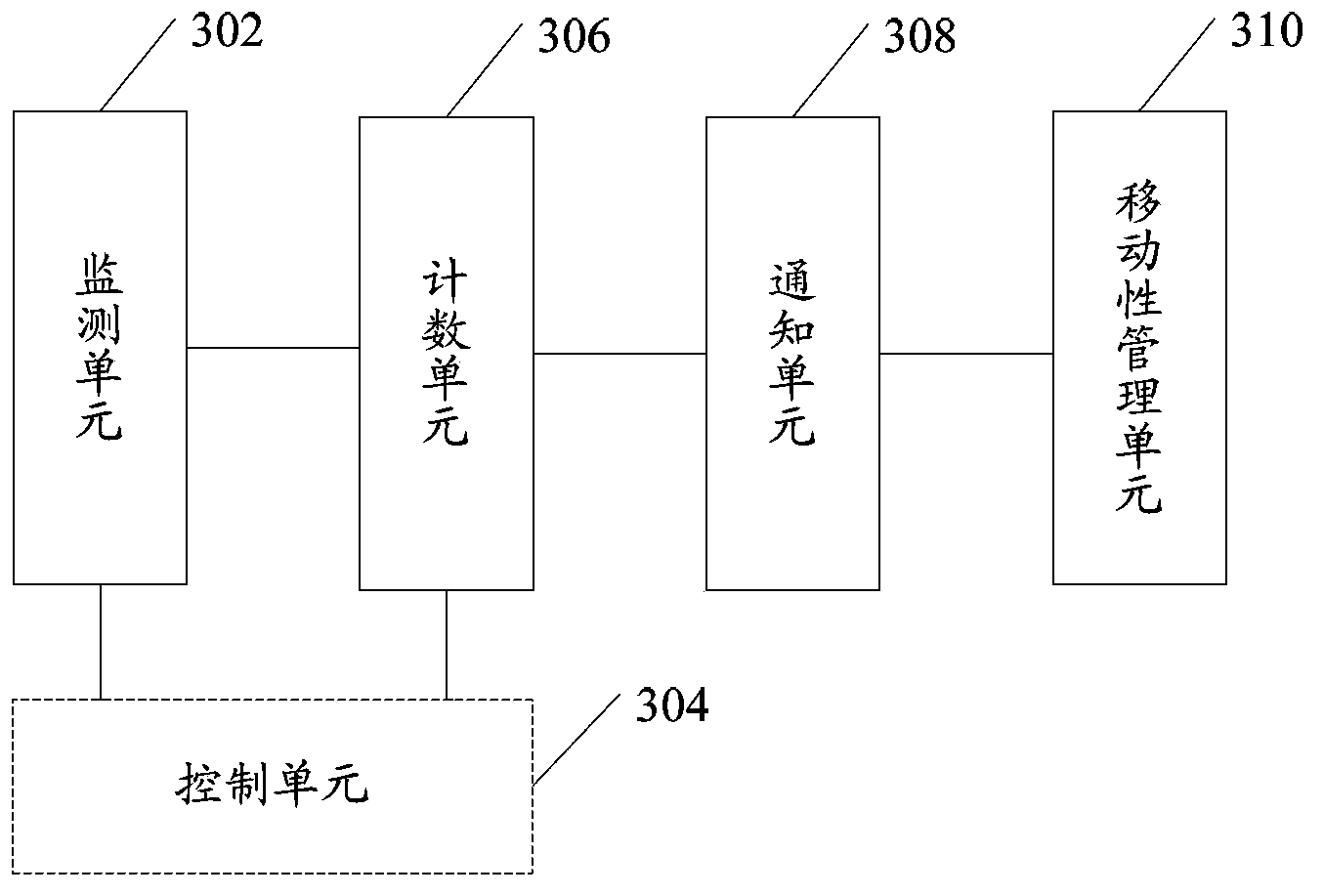
[0062] see image 3 , this embodiment provides a recovery device for decryption failure, the device includes;
[0063] A monitoring unit 302, configured to monitor whether the decryption of the received data frame fails;
[0064] A counting unit 306, configured to count the number of consecutive failures to decrypt the data frame;
[0065] A notification unit 308, configured to notify a mobility management unit when the number of consecutive failures reaches a preset threshold;
[0066] The mobility management unit 310 is configured to re-trigger an attach process when receiving the notification from the notification unit 308 .
[0067] In a specific implementation, the device may be set at a user terminal or at a network end. Wherein, the user terminal may be a receiving end, and at this time, the network end is a sending end. When the user terminal is used as the receiving end, the device described in this embodiment is applied. Compared with the method of restarting the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com