Network flow abnormity analysis method based on visualization clustering
A network traffic and clustering technology, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve the problems that users are difficult to understand and use, consume a lot of time, and cannot interact.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
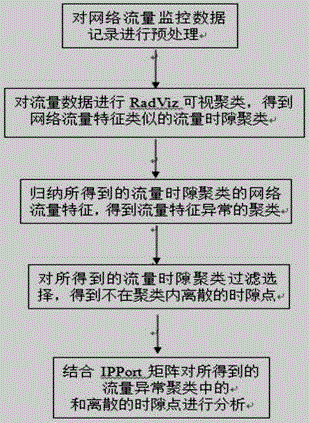
[0043] The invention discloses a method for abnormal analysis of network traffic based on visual clustering, see figure 1 , including five main steps: 1) Preprocessing the network traffic monitoring data records; 2) Carrying out RadViz visual clustering on the traffic data to obtain traffic time-slot clusters with similar network traffic characteristics; 3) Summarizing the results obtained in 2) The network traffic characteristics of the traffic time slot clustering, obtain the abnormal clustering of traffic characteristics; 4) to 2) the flow time slot clustering filter selection obtained, obtain the discrete time slot points not in the cluster; 5) combine IPPort The matrix analyzes the flow anomaly clusters and discrete time slot points obtained in 3) and 4). The present invention can quickly perform collaborative filtering on network traffic in combination with multiple angles, and efficiently analyze the abnormality of network traffic.
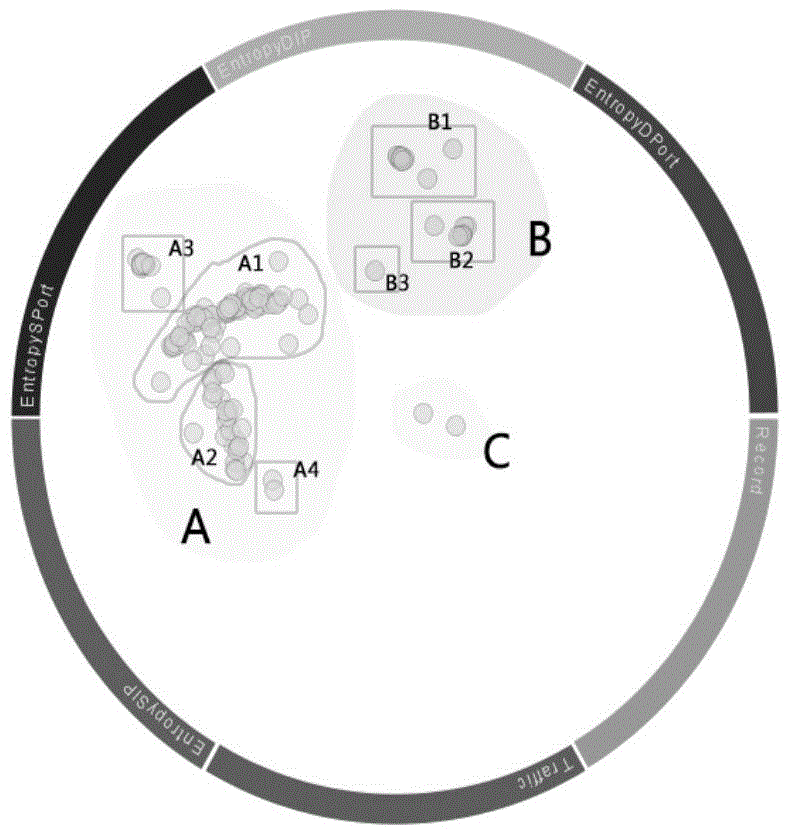
[0044] see figure 2 , utilize the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com