Method for enhancing network communication security
A technology for communication security and network enhancement, applied in the field of enhanced communication security, can solve problems such as inability to guarantee security, difficulties, etc., and achieve the effects of improving security, preventing leakage, and preventing the execution of illegal configurations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0014] In order to enable those skilled in the art to better understand the technical solutions of the present invention, the technical solutions in the embodiments of the present invention will be clearly and completely described below in conjunction with the drawings and embodiments. Obviously, the described embodiments are only the present invention. Some embodiments of the invention are not all of the embodiments.
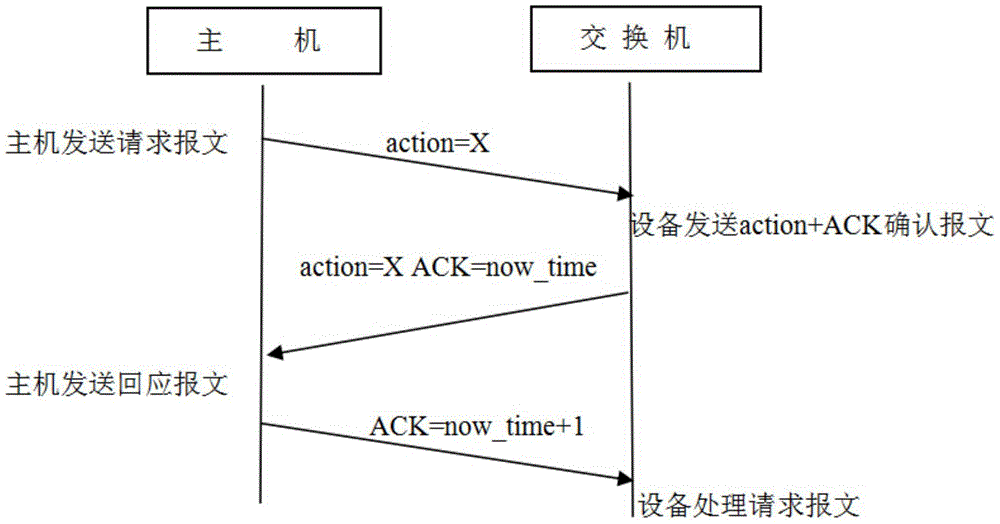
[0015] In the present invention, after the client (usually a host equipped with a web browser) logs in to the server with a correct user name and password, the server uses the user name, password, and client IP address as the identification of the connection between the client and the server, and records The absolute time the client logged in.
[0016] The present invention saves user names, passwords and client IP addresses for each legally connected client on the server. When the server receives the request message from the client, it checks whether the conn...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com