Method for detecting malicious application disclosing Android data
A data leakage and malicious application technology, applied in the direction of electronic digital data processing, computer security devices, instruments, etc., can solve the problems of large time consumption, inability to apply market-scale detection, and impractical use of mobile terminals, etc., to achieve the goal of shortening the time Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
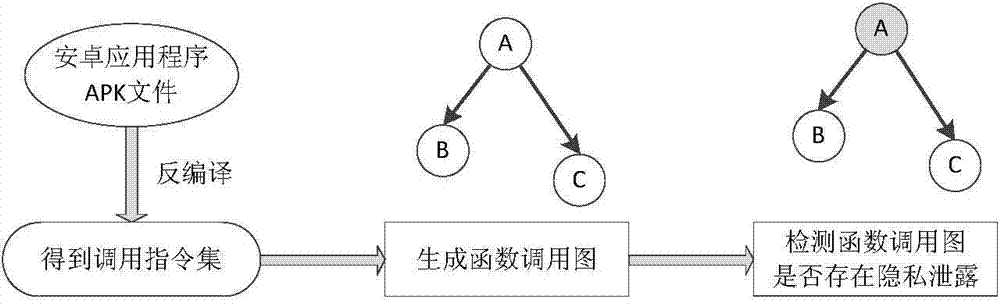
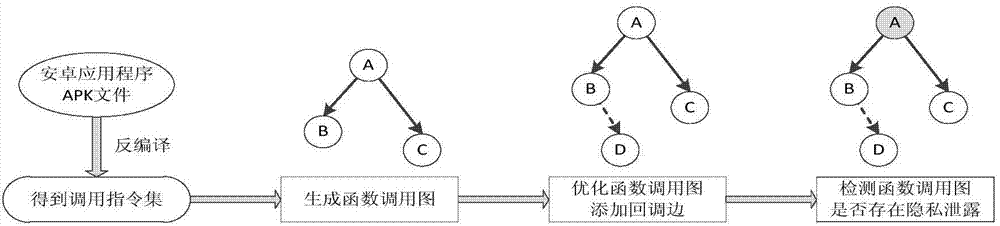
[0040] The following will combine an actual Android malicious application example, apply the system of the present invention to it, and elaborate on the core part, that is, the sensitive function screening part, including detailed implementation and specific operation process. The protection scope of the present invention includes but not limited to the following examples.
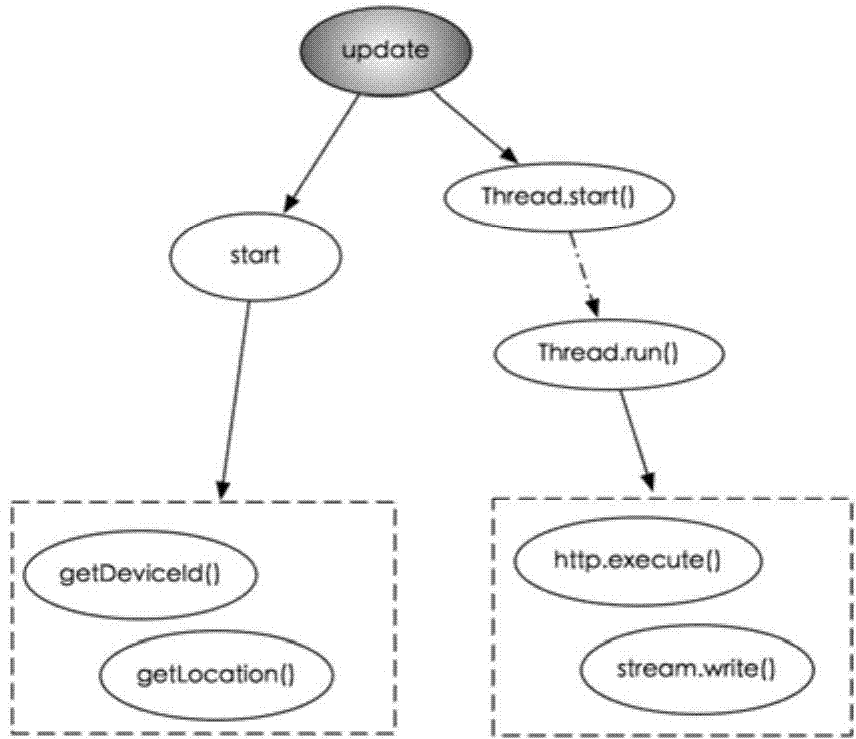
[0041] This embodiment is an example of an Android malicious application found in the market, and the application extension is DroidKungFu.apk. According to the detection of the market size, the app was determined to contain malicious software that illegally steals users' private information. After decompilation, we conducted a manual code review on it, which is shown under the core malicious code.
[0042]
[0043] Mainly, the variable mImei represents the string variable that the user stores the IMEI serial number of the mobile phone, and the doSearchReport() function calls two functions, updateInfo(...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap