Network abnormity detection method
A detection method and technology for network anomalies, applied in the field of network communication, can solve the problems of inability to obtain effective results, complex method models, and inability to detect abnormal behavior types, saving time, wide application, and improving detection efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] In order to make the content of the present invention more clear and understandable, the content of the present invention will be described in detail below in conjunction with specific embodiments and accompanying drawings.
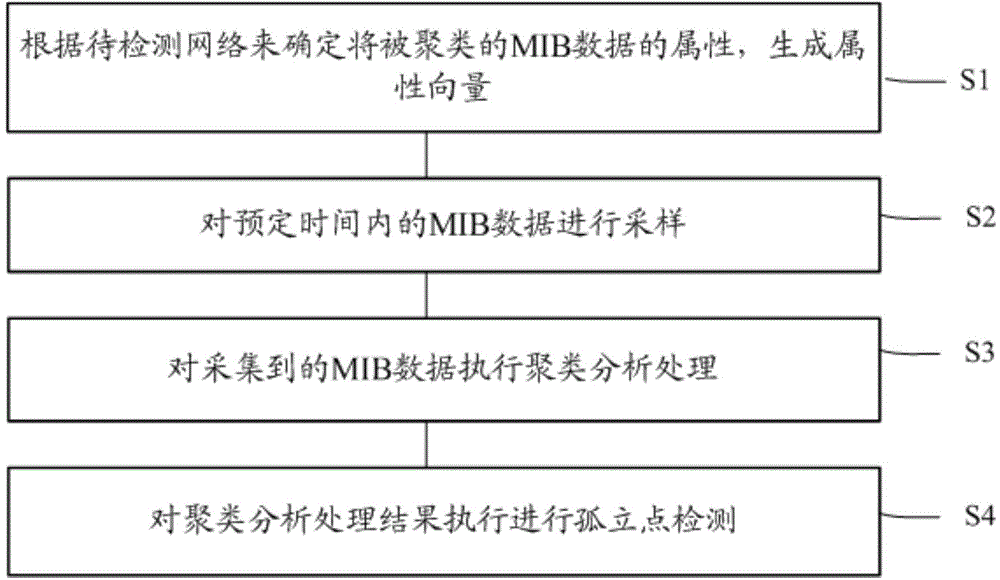
[0026] figure 1 A network anomaly detection method based on clustering and outlier detection according to a preferred embodiment of the present invention is schematically shown.
[0027] Specifically, as figure 1 As described, the network anomaly detection method based on clustering and outlier detection according to a preferred embodiment of the present invention includes:
[0028] The first step S1 is used to determine the attributes of the MIB (Management Information Base, Management Information Base) data to be clustered according to the network to be detected, and generate an attribute vector X; wherein, for example, each component of the attribute vector is each in the MIB attribute variable.
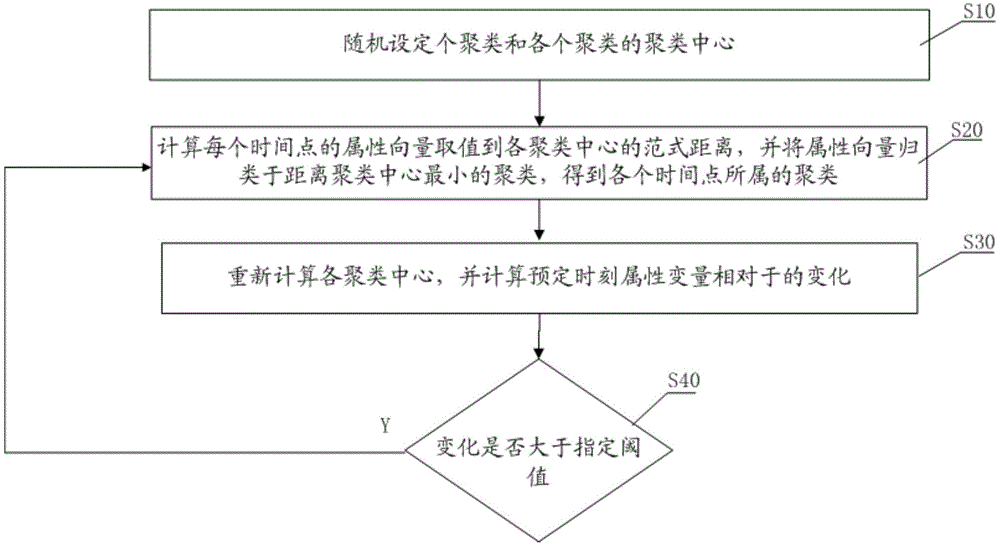
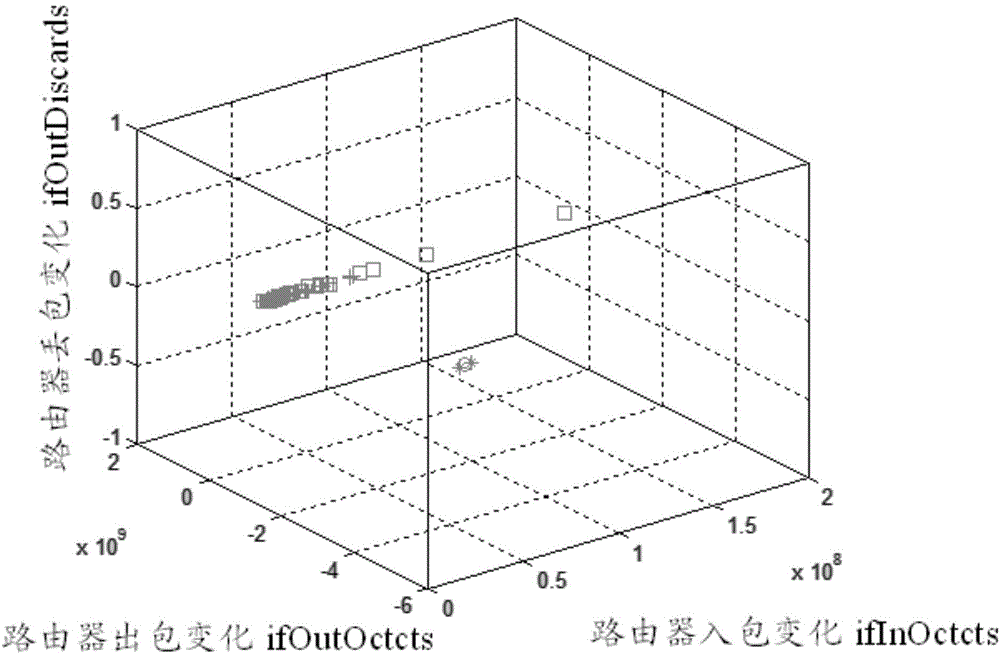
[0029] The second step S2 is to sample MIB da...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com