Data encryption based safety use method of configuration file
A configuration file and data encryption technology, applied in the field of application security, can solve the problems of configuration files being easily read and identified, sensitive information acquisition, etc., to achieve the effect of convenient modification and convenient next use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] In order to better understand the technical problems solved by the present invention and the technical solutions provided, the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments. The specific embodiments described here are only used to explain the implementation of the present invention, but not to limit the present invention.
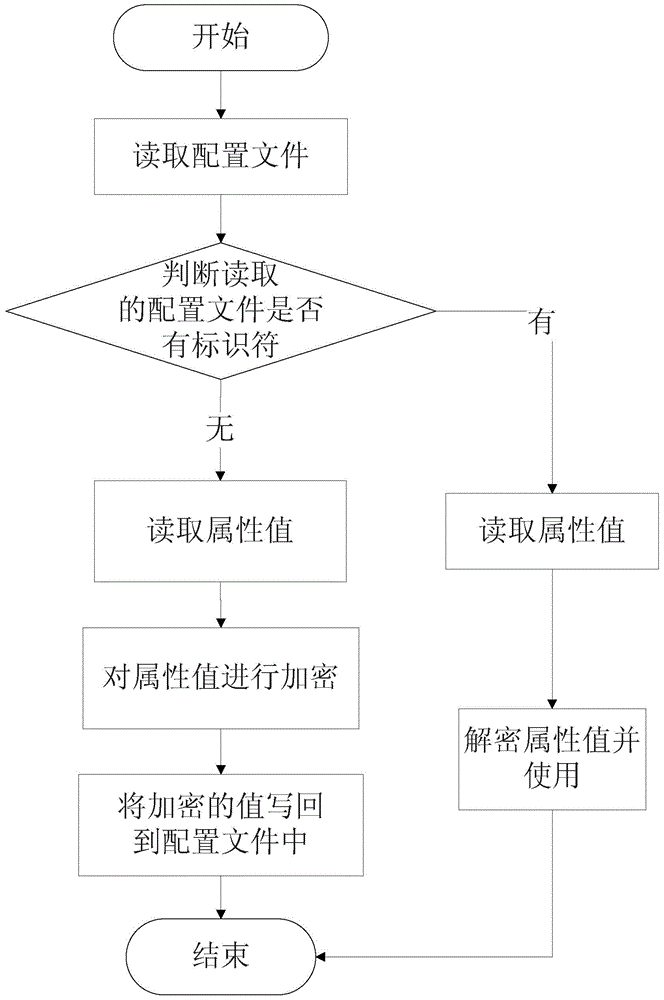
[0025] In a preferred embodiment, figure 1 It exemplarily shows a schematic flow chart of a method for safely using a configuration file based on data encryption; including;
[0026] Read the plaintext of the configuration file; determine whether the plaintext in the read configuration file contains an identifier item by item; if the identifier exists, perform the following steps a.1 and a.2; if not The identifier, then proceed to the following step b; a.1: read the attribute value of the configuration file, and use an asymmetric key, a symmetric key or a certificate to encr...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap